Recently, I faced numerous challenges where I needed to bypass limited SSRF or overcome regex mitigations to increase impact and make a case for a report.
Spinning up a server to host a redirection header is time consuming and not-so-fun to do.
There's an easy alternative 🧵
Spinning up a server to host a redirection header is time consuming and not-so-fun to do.
There's an easy alternative 🧵
While exploring some options online I've came across replit.com, their product offers a pretty easy way to just spin up a server with whatever technologies you'd like, and control the files and source code of your application.
#NotSponsored
#NotSponsored

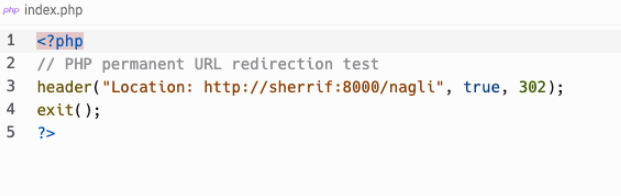
So, as easy as it gets - we will select a PHP Server to host our payload on, change the index.php file to have the following code snippet:
<?php
// PHP permanent URL redirection test
header("Location: http://internal.asset", true, 307);
exit();
?>
<?php
// PHP permanent URL redirection test
header("Location: http://internal.asset", true, 307);
exit();
?>

Then on the top right corner we'll have our constructed URL to test our payload on the target, should be something like *.repl.co
So in a matter of ~2 minutes - we have our own DNS name with a redirection payload that we can point directly to internal assets of our target, cool!
So in a matter of ~2 minutes - we have our own DNS name with a redirection payload that we can point directly to internal assets of our target, cool!

After testing our payload on our injection point,
We can observe the interactive console on the bottom right of the page, and debug the information to wether we managed to successfully increase our SSRF Impact and to determine that everything is set up correctly.
We can observe the interactive console on the bottom right of the page, and debug the information to wether we managed to successfully increase our SSRF Impact and to determine that everything is set up correctly.

This is mostly useful for SSRF endpoints with heavy whitelisting / regex mitigations, if the SSRF will follow redirects, that could open a whole new aspect for numerous of chains to bypass those.
It helped me to successfully hit internal assets at the H1-407 Live Hacking Event.
It helped me to successfully hit internal assets at the H1-407 Live Hacking Event.
TLDR:
Hosting a redirection machine for whitelisting bypass scenarios should take no longer than 2 minutes
1. Create repl.it server with any technology
2. Edit the source code
3. Use the constructed DNS Payload on your target
4. Debug
5. Win
#BugBountyTips
Hosting a redirection machine for whitelisting bypass scenarios should take no longer than 2 minutes
1. Create repl.it server with any technology
2. Edit the source code
3. Use the constructed DNS Payload on your target
4. Debug
5. Win
#BugBountyTips
• • •
Missing some Tweet in this thread? You can try to
force a refresh