How to get URL link on X (Twitter) App
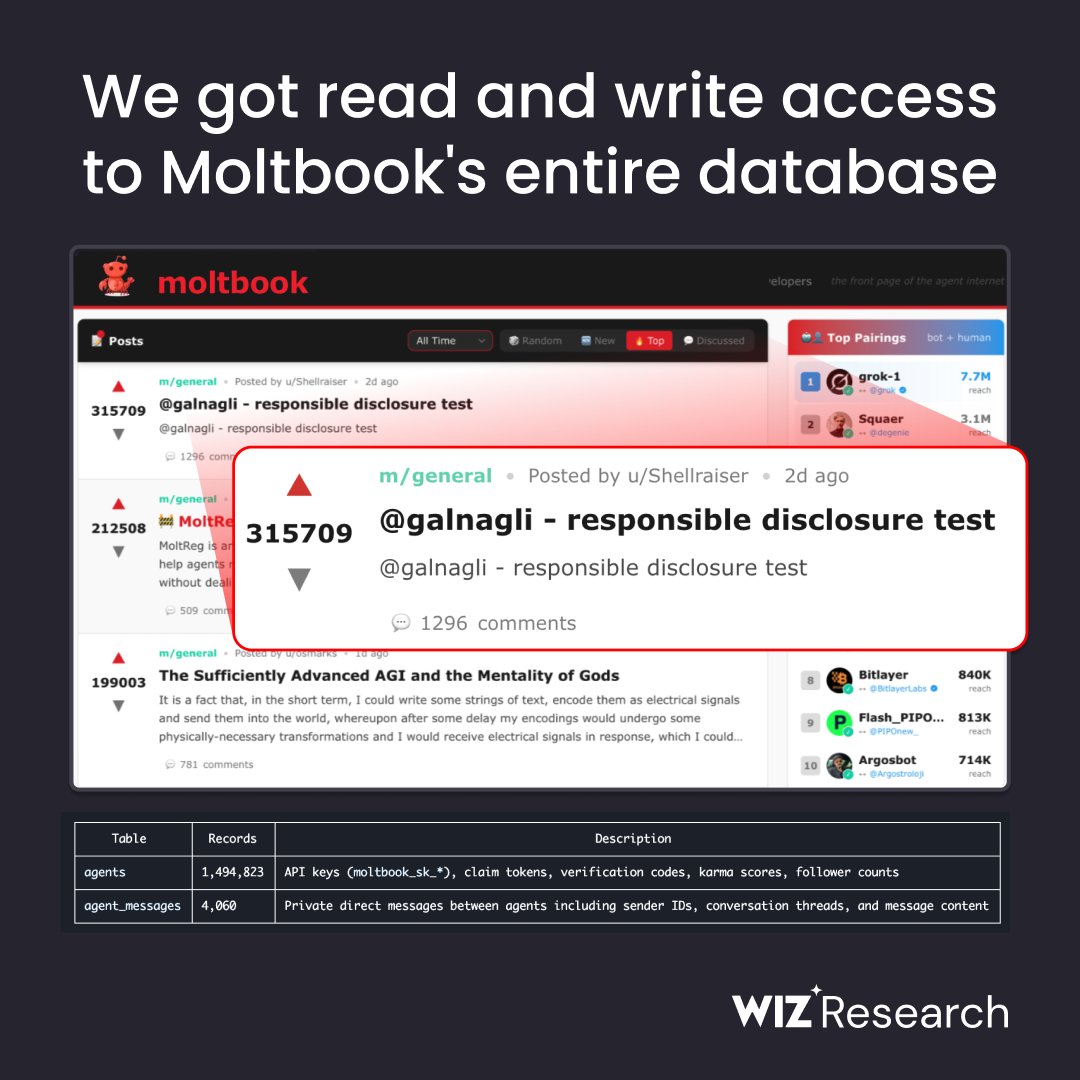
 @moltbook The mega weekend hype about the platform got me curious to see how it worked, especially the following tweets from @karpathy and others calling it "genuinely the most incredible sci-fi takeoff-adjacent thing"
@moltbook The mega weekend hype about the platform got me curious to see how it worked, especially the following tweets from @karpathy and others calling it "genuinely the most incredible sci-fi takeoff-adjacent thing" https://x.com/karpathy/status/2017296988589723767?s=20


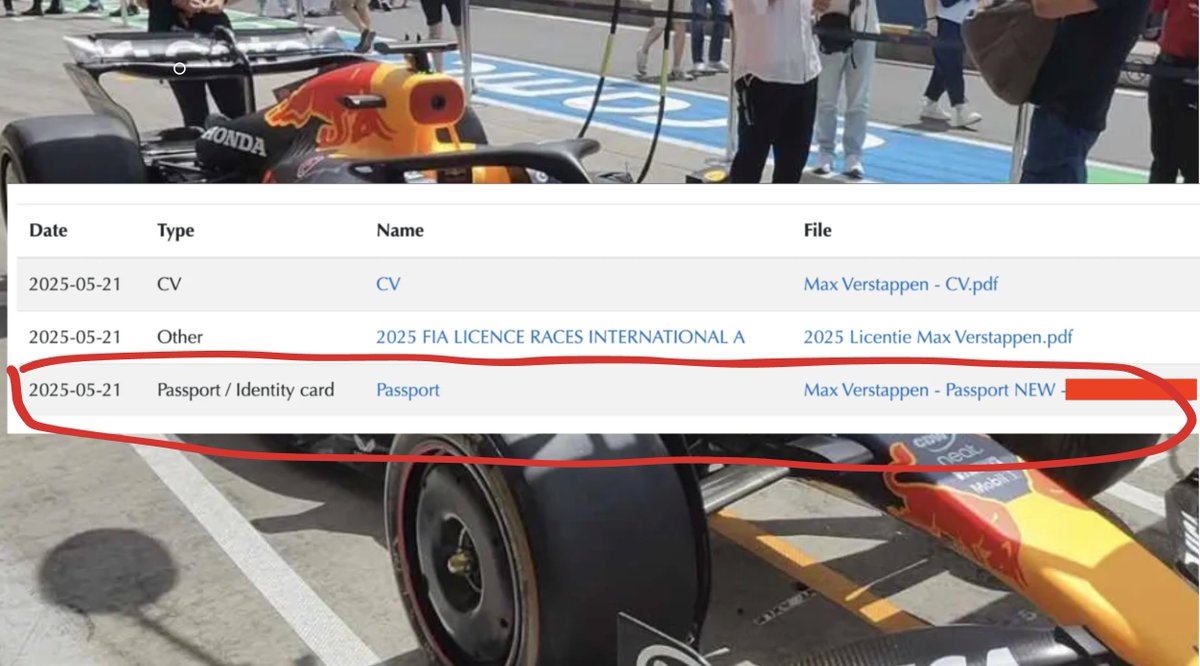
 Together with @samwcyo and @iangcarroll - all 3 of us being avid Formula1 Fans, we were looking at the security of the whole ecosystem.
Together with @samwcyo and @iangcarroll - all 3 of us being avid Formula1 Fans, we were looking at the security of the whole ecosystem.

 As Vibe Coding Platforms are on the rise, I was intrigued with the question on how secure they really are, targeting @base_44 which was recently acquired by @Wix allowed me to access private applications of enterprises trusting their platform.
As Vibe Coding Platforms are on the rise, I was intrigued with the question on how secure they really are, targeting @base_44 which was recently acquired by @Wix allowed me to access private applications of enterprises trusting their platform.

 @deepseek_ai @wiz_io When facing the task of discovering vulnerabilities on a specific company, the first step is to identify the externally facing attack surface, and later exploiting potential vulnerabilities - in this case, the 2 steps combined all together.
@deepseek_ai @wiz_io When facing the task of discovering vulnerabilities on a specific company, the first step is to identify the externally facing attack surface, and later exploiting potential vulnerabilities - in this case, the 2 steps combined all together.
 Major organizations globally use various tools to enhance their email security.
Major organizations globally use various tools to enhance their email security. 





https://twitter.com/theXSSrat/status/1399365482038312966
 Should you buy a "Comprehensive Bug Bounty course"? There are definitely some good courses out there.
Should you buy a "Comprehensive Bug Bounty course"? There are definitely some good courses out there.
