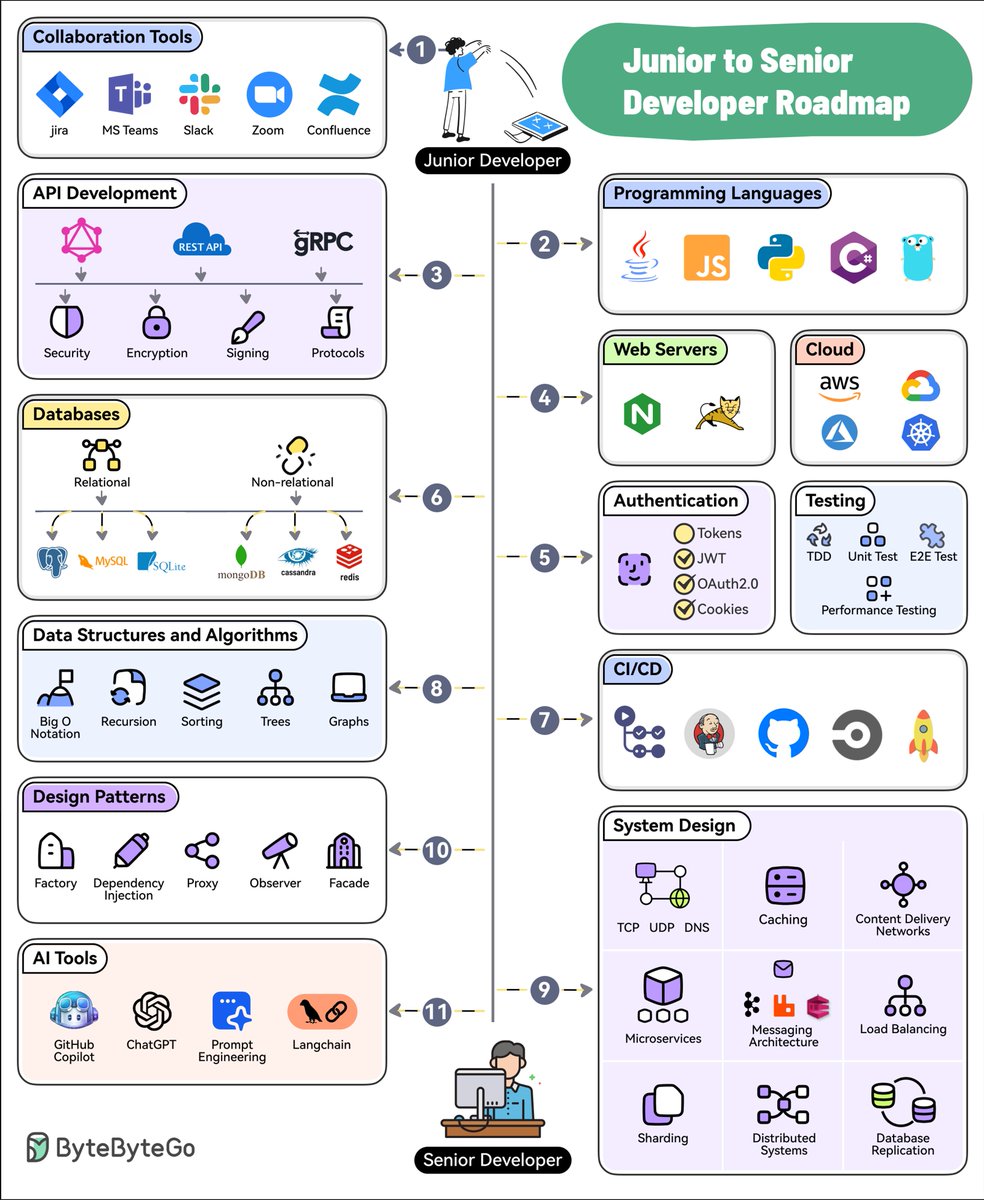
/1 What are the common load-balancing algorithms?
The diagram below shows 6 common algorithms.
🔹 Static Algorithms
1. Round robin
The client requests are sent to different service instances in sequential order. The services are usually required to be stateless.
The diagram below shows 6 common algorithms.
🔹 Static Algorithms
1. Round robin
The client requests are sent to different service instances in sequential order. The services are usually required to be stateless.

/2 2. Sticky round-robin
This is an improvement of the round-robin algorithm. If Alice’s first request goes to service A, the following requests go to service A as well.
This is an improvement of the round-robin algorithm. If Alice’s first request goes to service A, the following requests go to service A as well.

/3 3. Weighted round-robin
The admin can specify the weight for each service. The ones with a higher weight handle more requests than others.
4. Hash
This algorithm applies a hash function on the incoming requests’ IP or URL.
The admin can specify the weight for each service. The ones with a higher weight handle more requests than others.
4. Hash
This algorithm applies a hash function on the incoming requests’ IP or URL.

/4 🔹 Dynamic Algorithms
5. Least connections
A new request is sent to the service instance with the least concurrent connections.
6. Least response time
A new request is sent to the service instance with the fastest response time.
5. Least connections
A new request is sent to the service instance with the least concurrent connections.
6. Least response time
A new request is sent to the service instance with the fastest response time.

/5 👉 Over to you: We can use other attributes for hashing algorithms. For example, HTTP header, request type, client type, etc. What attributes have you used?
/6 Subscribe to our weekly free newsletter to learn something new every week: bit.ly/3FEGliw 

/7 I hope you've found this thread helpful.
Follow me @alexxubyte for more.
Like/Retweet the first tweet below if you can:
Follow me @alexxubyte for more.
Like/Retweet the first tweet below if you can:
https://twitter.com/alexxubyte/status/1625536625030885377
• • •
Missing some Tweet in this thread? You can try to
force a refresh