Just getting into Web3 Security & don't know how to start?
Here's a complete 4 step process to become a pro Smart Contract Auditor as quickly as possible 🧵
1️⃣ Start Off By Building Something
2️⃣ Learn DeFi Primitives
3️⃣ Deep Dive Web3 Security
4️⃣ Build Your Personal Brand
Here's a complete 4 step process to become a pro Smart Contract Auditor as quickly as possible 🧵
1️⃣ Start Off By Building Something
2️⃣ Learn DeFi Primitives
3️⃣ Deep Dive Web3 Security
4️⃣ Build Your Personal Brand
🚨 Skip to the end for some high-impact resources on Web3 Security!
Let's explore each step in detail 👇
Let's explore each step in detail 👇
1️⃣ Start Off By Building Something
• If you're just getting started, read Mastering Ethereum to get familiar with the very basics
• After you’ve picked up some of the basics, build a simple faucet contract
• If you're just getting started, read Mastering Ethereum to get familiar with the very basics
• After you’ve picked up some of the basics, build a simple faucet contract
• After you’ve got that down, add meta transactions so users get native tokens without spending any gas
• Now that you’ve mastered the faucet, build something cool that you’re interested in
• Now that you’ve mastered the faucet, build something cool that you’re interested in
• Through doing this you’ll get comfortable with common design patterns & grow to understand the common vulnerabilities that we protect against
• After you’ve gotten a grasp on the basics of Solidity development you’re ready to learn more about DeFi
• After you’ve gotten a grasp on the basics of Solidity development you’re ready to learn more about DeFi
2️⃣ Get Familiar With Common DeFi Primitives
• Learn everything there is to know about Uniswap, Compound, Beefy Finance & more
• Go check out their apps, join the discord, read the docs, talk to the devs
• Learn everything there is to know about Uniswap, Compound, Beefy Finance & more
• Go check out their apps, join the discord, read the docs, talk to the devs
Pro-tip, ⚠️ Not Financial Advice:
• Use & invest in DeFi apps to get addicted to understanding how they work
• I did this & lost a decent amount of money but learned very quickly, up to you
• Use & invest in DeFi apps to get addicted to understanding how they work
• I did this & lost a decent amount of money but learned very quickly, up to you
• After you’ve gotten familiar with common DeFi primitives, it’s time to deep dive into web3 security
3️⃣ Deep Dive In Web3 Security
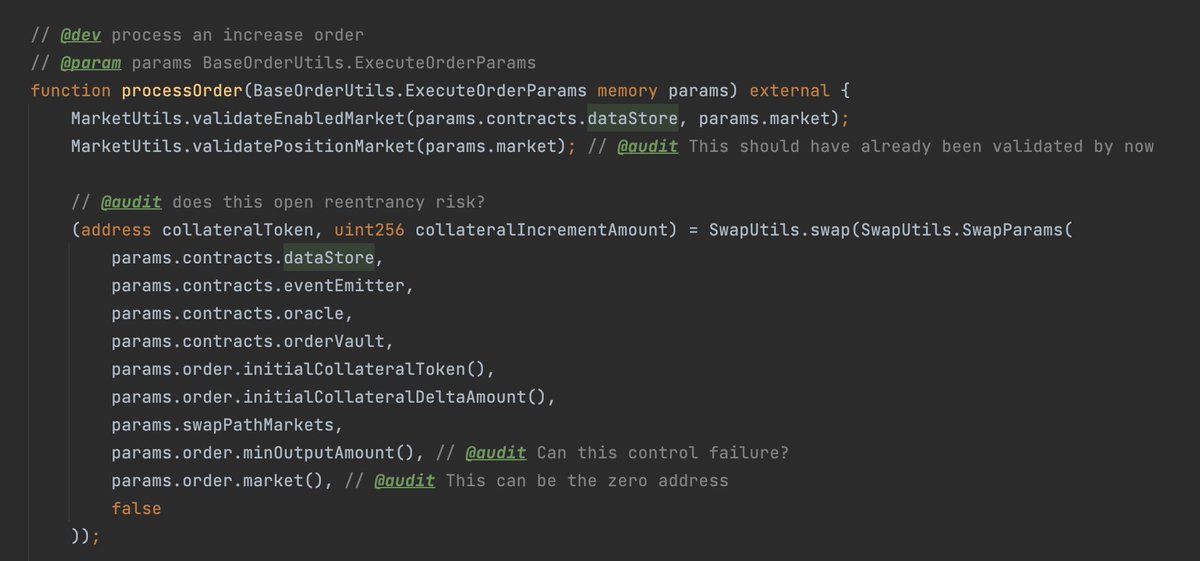
• Read over the corpus of Code4rena findings
• Read the public reports of great audit firms like Dedaub, OpenZeppelin, Guardian, and others
• Read over the corpus of Code4rena findings
• Read the public reports of great audit firms like Dedaub, OpenZeppelin, Guardian, and others
• Get on Twitter, it’s where all the latest alpha is.
• Follow top security researchers & Constantly be on the lookout for new exploits uncovered by the community
• Follow top security researchers & Constantly be on the lookout for new exploits uncovered by the community
• Finally, deep dive into the nitty gritty aspects of Ethereum.
• Learn stuff like the 63/64 rule & the intricacies & risks of delegatecall
• Learn stuff like the 63/64 rule & the intricacies & risks of delegatecall
This learning process never truly ends.
But once you put in a few dozen hours into strictly Web3 Security, it's time to start growing your personal brand for lasting success in the space.
But once you put in a few dozen hours into strictly Web3 Security, it's time to start growing your personal brand for lasting success in the space.
4️⃣ Build Your Personal Web3 Security Brand
• Your personal brand will allow you to work on cooler projects, connect with more like-minded individuals & make a larger impact on the space
• Your personal brand will allow you to work on cooler projects, connect with more like-minded individuals & make a larger impact on the space
• To build your personal brand, build up a portfolio of your reports & findings
• If you’re competing in an audit contest, wait until the report is released & release your own findings to show off your work
• If you’re competing in an audit contest, wait until the report is released & release your own findings to show off your work
Pro-tip:
• Share all of your learnings with the community, you’ll find that everything you give comes back in multiples over the long term
• Share all of your learnings with the community, you’ll find that everything you give comes back in multiples over the long term
Did this 4 step roadmap help you out?
Check out the full video here & share with other auditors so we can onboard more people into the space!
Check out the full video here & share with other auditors so we can onboard more people into the space!
• • •
Missing some Tweet in this thread? You can try to
force a refresh