Founder, @guardianaudits. $10,000,000,000+ Protected. Host: Permissionless Podcast.
Book an audit → https://t.co/M4i98qF4Nv
How to get URL link on X (Twitter) App


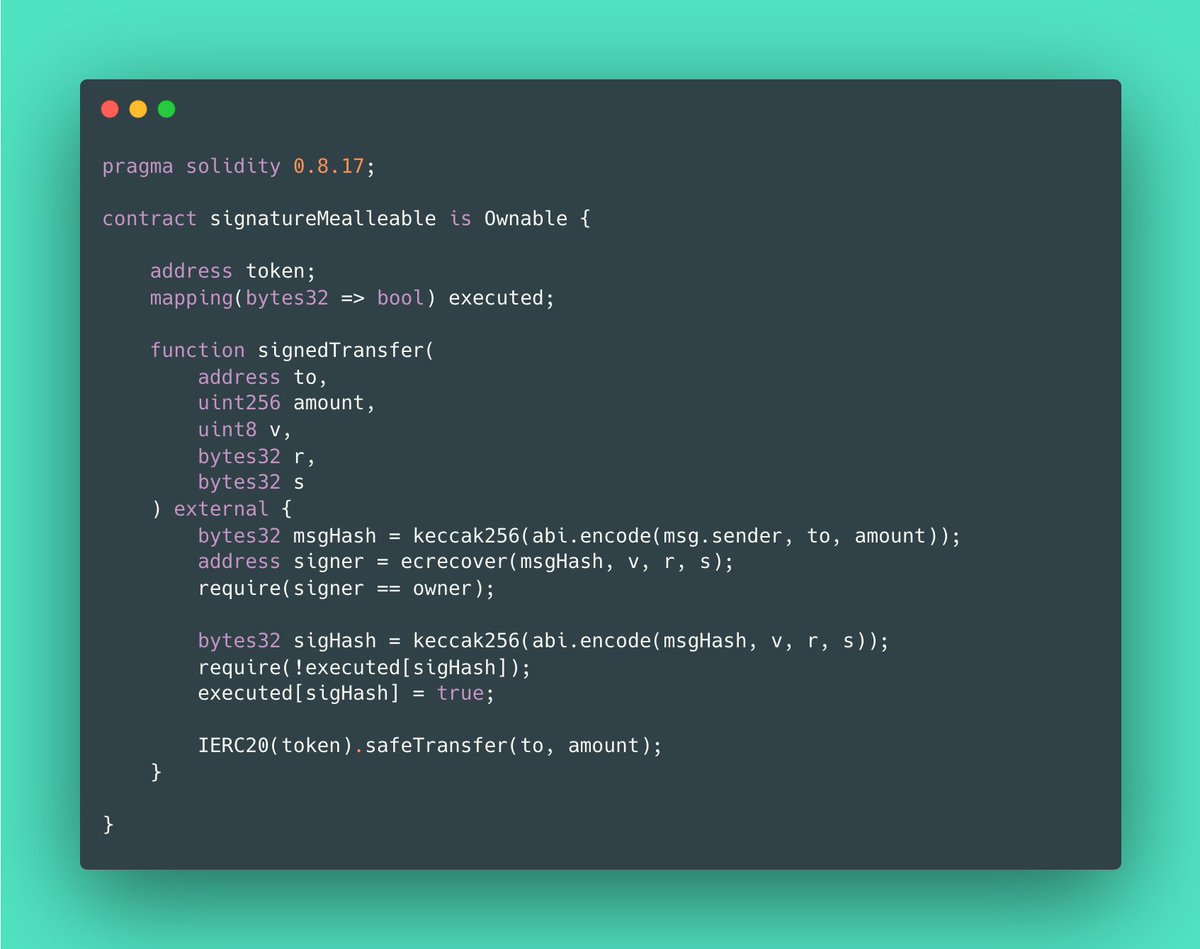
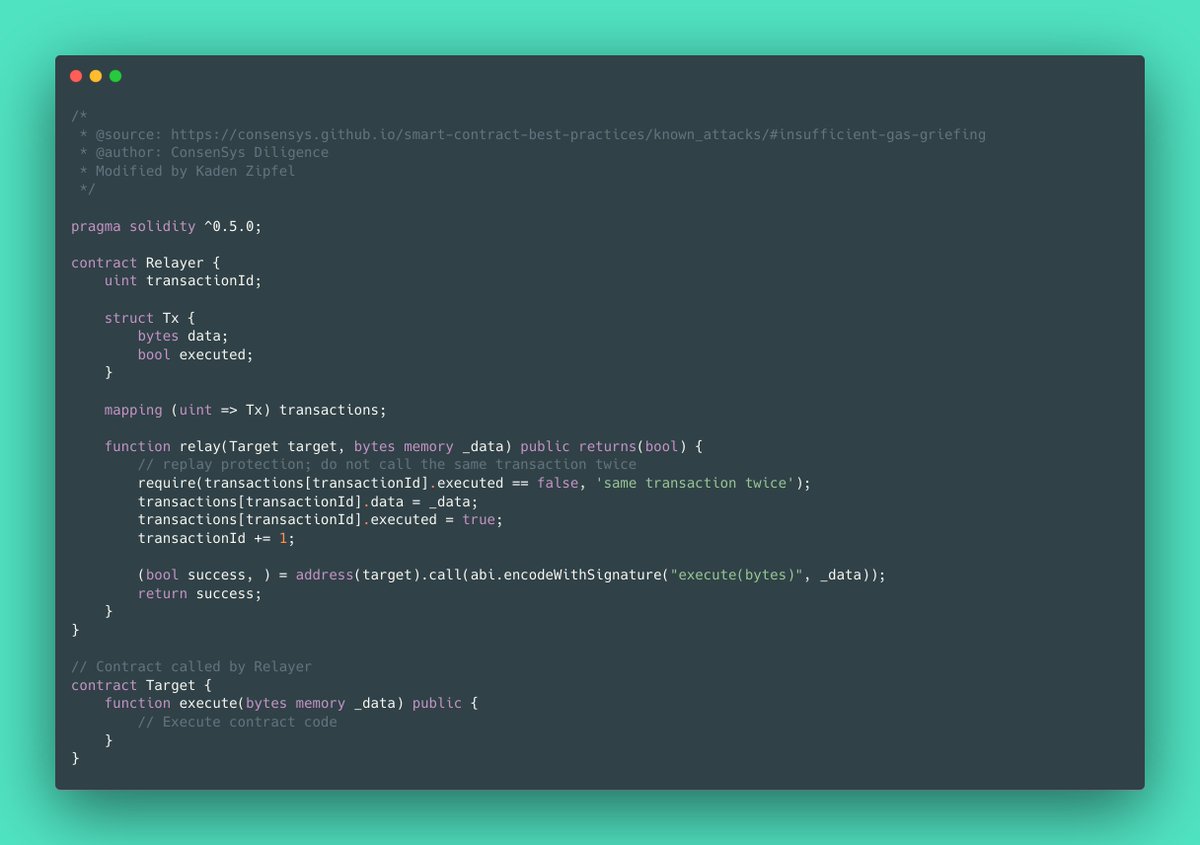

 TLDR:
TLDR: