
Department of Cyber WAR.
Member of the Counter Spider Collective.
Wielder of AI to defend in Cyber Space.
Ralph Vibe Specialist.
Grey Teamer.
How to get URL link on X (Twitter) App



 ok so to explain the UNIFI setup a bit:
ok so to explain the UNIFI setup a bit:

 So let's look at the scenario:
So let's look at the scenario: 


 As you can see here there are not 30 device events
As you can see here there are not 30 device events

 looks similar as almost every org I've worked with (super broad generalisation)
looks similar as almost every org I've worked with (super broad generalisation)

 Now in this instance it’s not even spoofing (you would see an event)
Now in this instance it’s not even spoofing (you would see an event)

 Microsoft teams uses STUN
Microsoft teams uses STUN

 now it gets complicated in the details. If you do this with servers/storage and locations you own Plane 4 can litterally be physically isolated at it's management/access plane. Think of a hypervisor and where the networks are physically split (outside of the requirement to have… twitter.com/i/web/status/1…
now it gets complicated in the details. If you do this with servers/storage and locations you own Plane 4 can litterally be physically isolated at it's management/access plane. Think of a hypervisor and where the networks are physically split (outside of the requirement to have… twitter.com/i/web/status/1… 

 Now I’m gonna deploy a quick vm locally. Windows 11. Then deploy MDE.
Now I’m gonna deploy a quick vm locally. Windows 11. Then deploy MDE. 
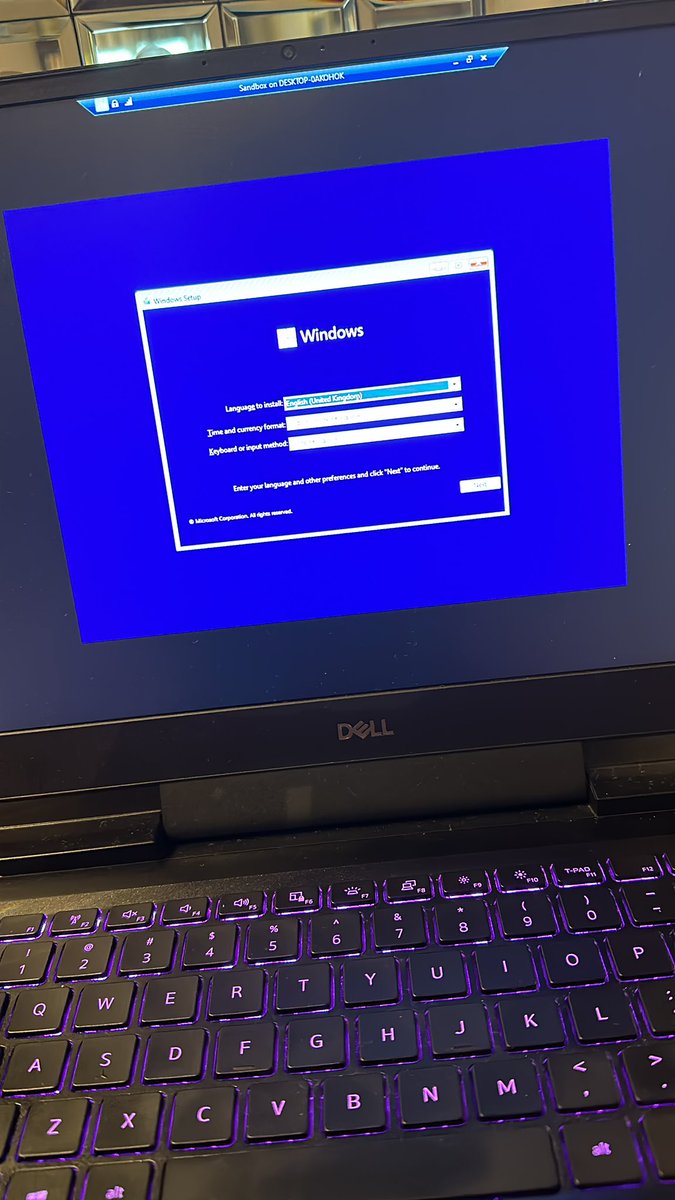





 I also promise I did not jack into their net ;) 😈
I also promise I did not jack into their net ;) 😈 




 Backup and Replication License Agreement goes brrr
Backup and Replication License Agreement goes brrr

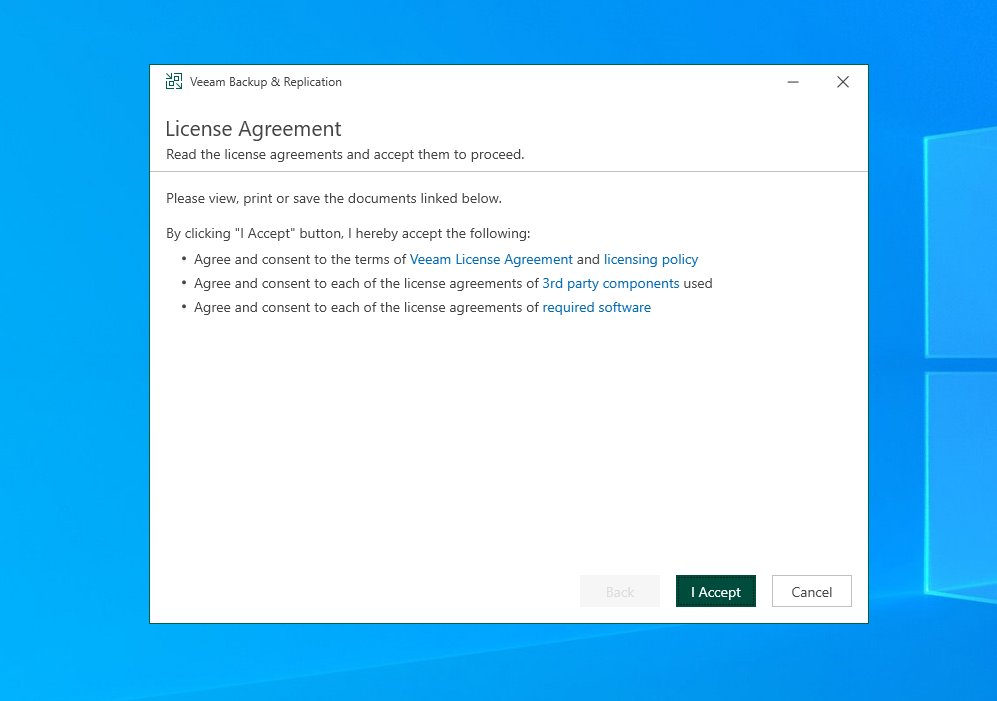

 to start with I'm going to just do some PREP. We are going to need to think about Initial Access then Escalation to Domain Admin and then RAMPAGE!
to start with I'm going to just do some PREP. We are going to need to think about Initial Access then Escalation to Domain Admin and then RAMPAGE! 

 "You do not understand the exposure of your essential function to publicly-known vulnerabilities."
"You do not understand the exposure of your essential function to publicly-known vulnerabilities."

