ok let's #ransomware some servers! (in a lab of mine not for real coz it's NASTY!)
VMs go BRRRRR
But wait... we are gonna look at how we can PROTECT, RESPOND and RECOVER! I'm going to deploy @Veeam to help me (coz I like the product, it rocks!)
VMs go BRRRRR
But wait... we are gonna look at how we can PROTECT, RESPOND and RECOVER! I'm going to deploy @Veeam to help me (coz I like the product, it rocks!)

to start with I'm going to just do some PREP. We are going to need to think about Initial Access then Escalation to Domain Admin and then RAMPAGE! 
I'm gonna thread some stuff whilst I build.. I'm going to start with using @VMware workstation PRO. I might do some stuff with the RACK mounted servers but let's see. 

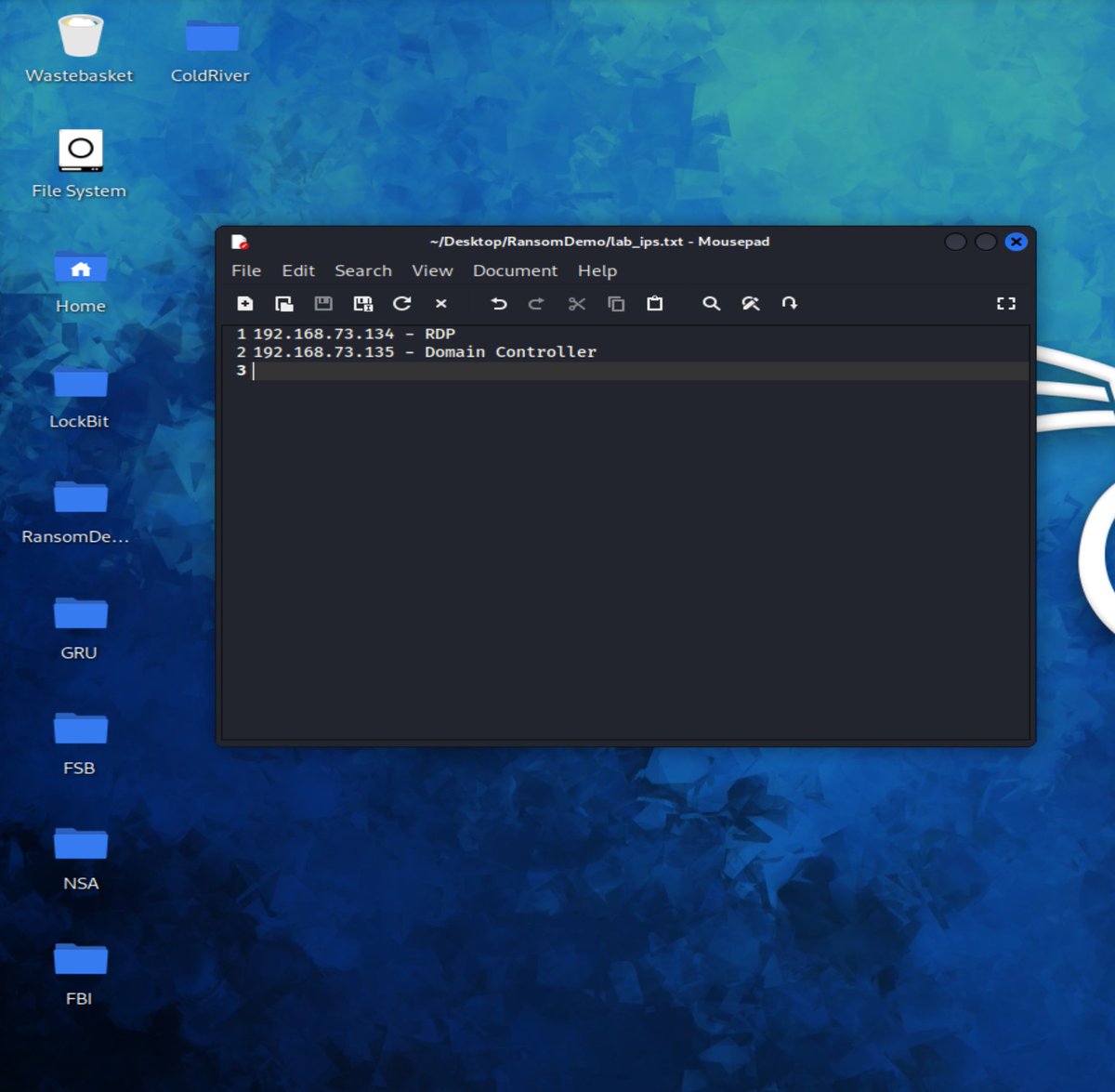
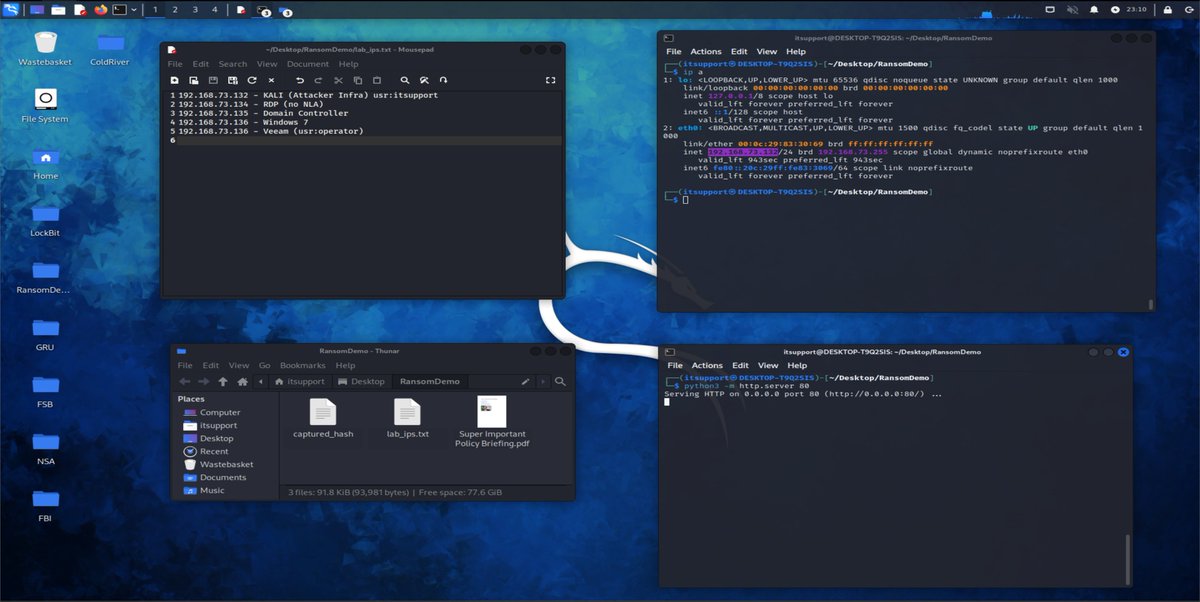
ok we are gonna simulate a DMZ RDP exposure (I'm not making a FULL lab for this) and I'm building a quick domain controller! 

also to note, WINRM (WSMAN) on TCP 5985 was open by DEFAULT, RDP I configured to be OPEN manually.
WINRM is only available on the LOCAL SUBNET by default, some NAT configs in hosting providers means that's exposed by DEFAULT as well... (the the whole internet)
WINRM is only available on the LOCAL SUBNET by default, some NAT configs in hosting providers means that's exposed by DEFAULT as well... (the the whole internet)

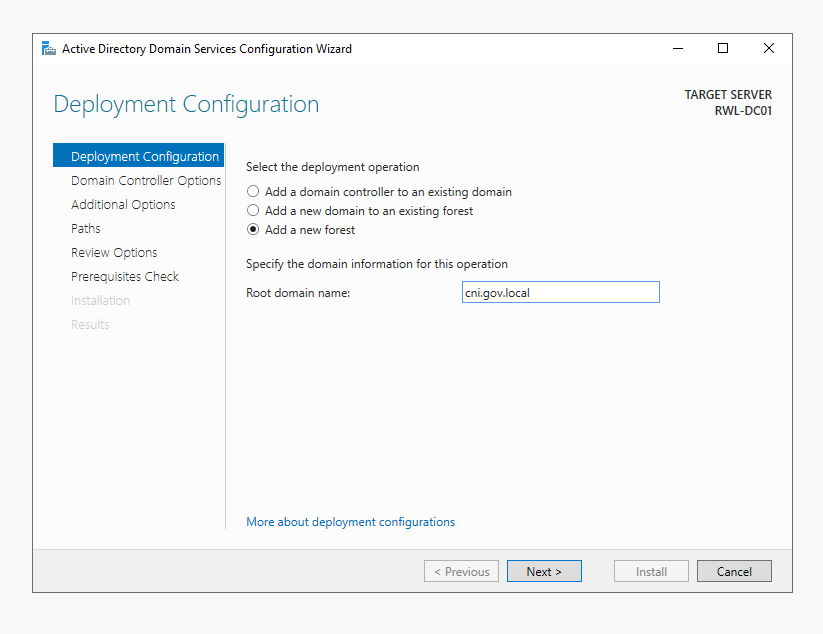
ok now we have our Initial Access route sorted, let's get a domain controller (active directory domain/forest) deployed! 

ok i'm using 2022 OS's so for CNI that's LAUGHABLE .. i should have deployed 2008 R2, I'll set the functional level down low in symbolic reference to REALITY. 

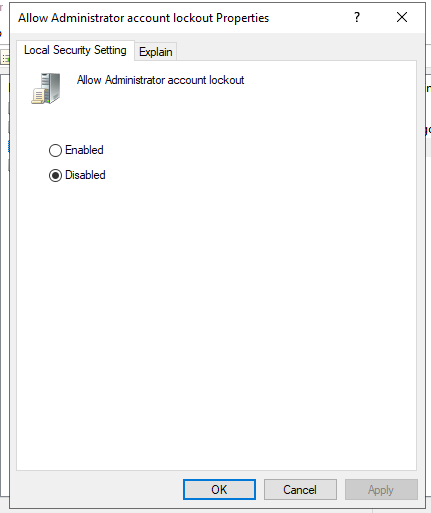
i need to do a quick cofig change but whilst I'm here on Server 2022 (this build) local administrator account lockout is ENABLED by DEFAULT! here's the config for default account lockout times! 



ok cool as always even in demo labs we need a MVP for docs. I'm gonna quickly demo the account lockout using HYDRA to attack RDP on the domain controler! 
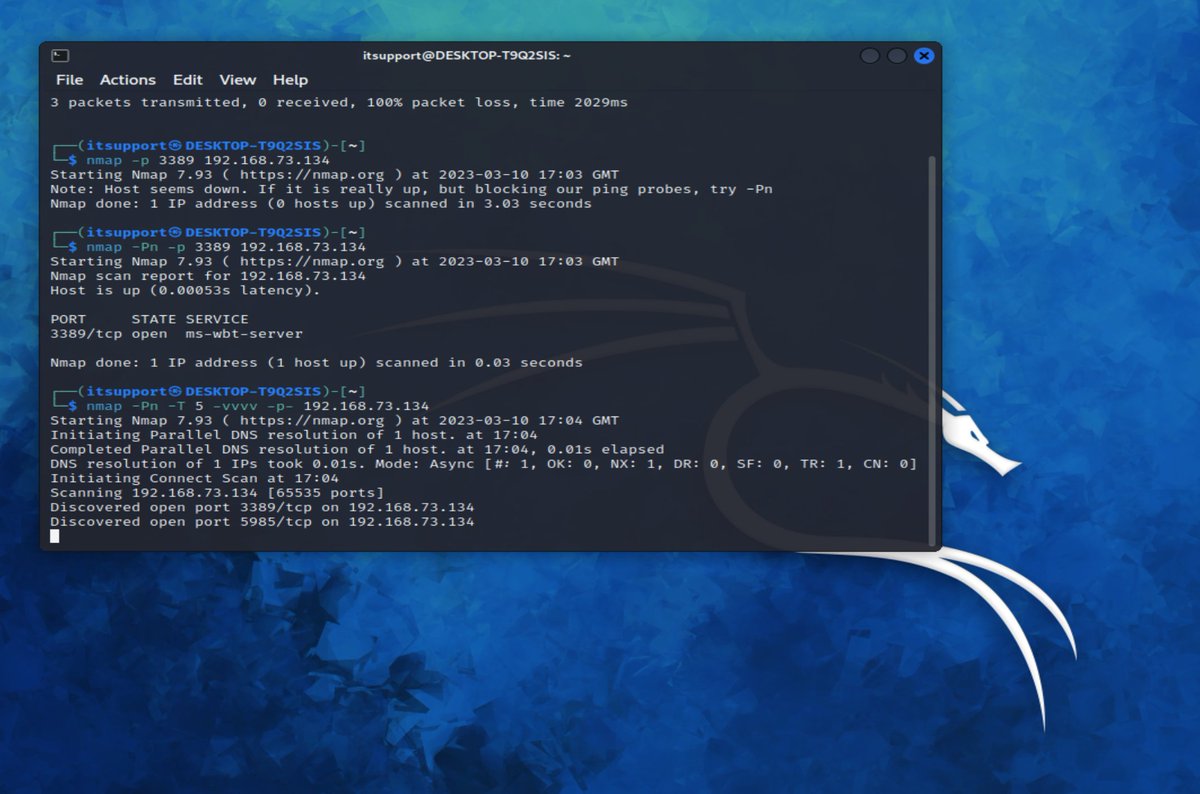
ok just a quick TCP port scan (remember DNS clients use UDP 53) TCP 53 is used for zone transfers!
445 - SMB/CIFS (File shares, WMI, RPC)
135,139 - MSRPC, NETBIOS etc.
389 = LDAP
636 = LDAPS
3268 = GLOBAL CAT (the all partitions in the directory!)
3268 - GCAT SSL/TLS
5985 = WINRM… twitter.com/i/web/status/1…
445 - SMB/CIFS (File shares, WMI, RPC)
135,139 - MSRPC, NETBIOS etc.
389 = LDAP
636 = LDAPS
3268 = GLOBAL CAT (the all partitions in the directory!)
3268 - GCAT SSL/TLS
5985 = WINRM… twitter.com/i/web/status/1…

right ok let's fire some PEWS! I've turned on RDP and re-scnaned TCP 3389 (RDP)
now it's sensible to look at the client/server handshake with RDP, there's metadata in there you might want to know about ;)
now it's sensible to look at the client/server handshake with RDP, there's metadata in there you might want to know about ;)

ok we need a username (administrator) and then a password list -P (capital for LIST -p lowercase for a single password string) (same as -u vs -U for username)
rockyou coz i'm lazy then service://IP
hydra -l administrator -P /usr/share/wordlists/rockyou.txt rdp://192.168.73.135 -d
rockyou coz i'm lazy then service://IP
hydra -l administrator -P /usr/share/wordlists/rockyou.txt rdp://192.168.73.135 -d
an old blog from 2018 on RDP brute force by me
pwndefend.com/2018/07/24/hai…
pwndefend.com/2018/07/24/hai…
ok PEW PEW!!
Fire the lasers! etc. etc. this is now attacking the domain controller (which has LOCKOUT local administrator enabled!)
Fire the lasers! etc. etc. this is now attacking the domain controller (which has LOCKOUT local administrator enabled!)

ahh ok tweeps look! when we promoted this to a domain controller the policy WAS changed to this! so that's good to know, if you use BRAND NEW 2022 Media and you make a new domain, local administrator lockout is enabled on OS install, BUT disabled if you promote to a domain… twitter.com/i/web/status/1… 

ok so let's leave the defaults on! but we DO need to configure some bits on the domain or it's not gonna be realistic! Let's make some common misconfigurations and vulns!
ok let's fire some pews at the RDP server....
the creds are: administrator:Pa55w0rd1!
but look... no dice... let's go check out the logs!
the creds are: administrator:Pa55w0rd1!
but look... no dice... let's go check out the logs!
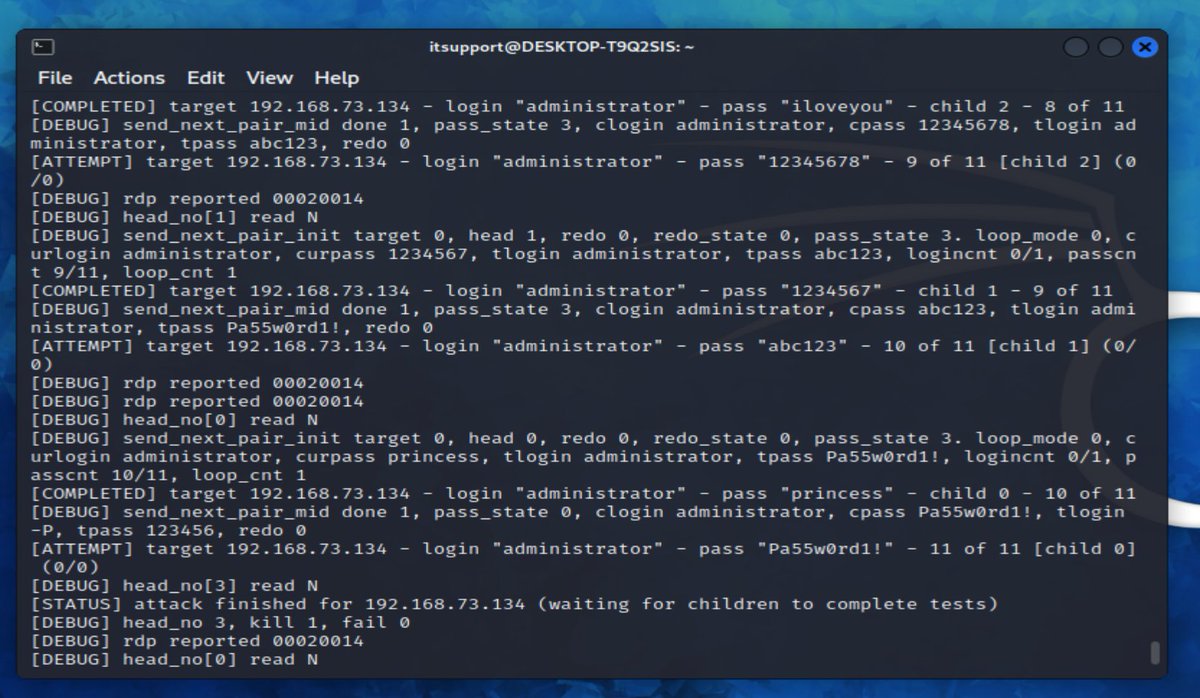
ok pews detected! we can see the logs here... we fire another round of PEWS! and LOCKED OUT! nice one @Microsoft @Windows @MsftSecIntel :) 



for the sake of the DEMO we are going to simulate older Windows servers/clients. so I'm disabling this! it might take years for orgs to roll this feature out.. 
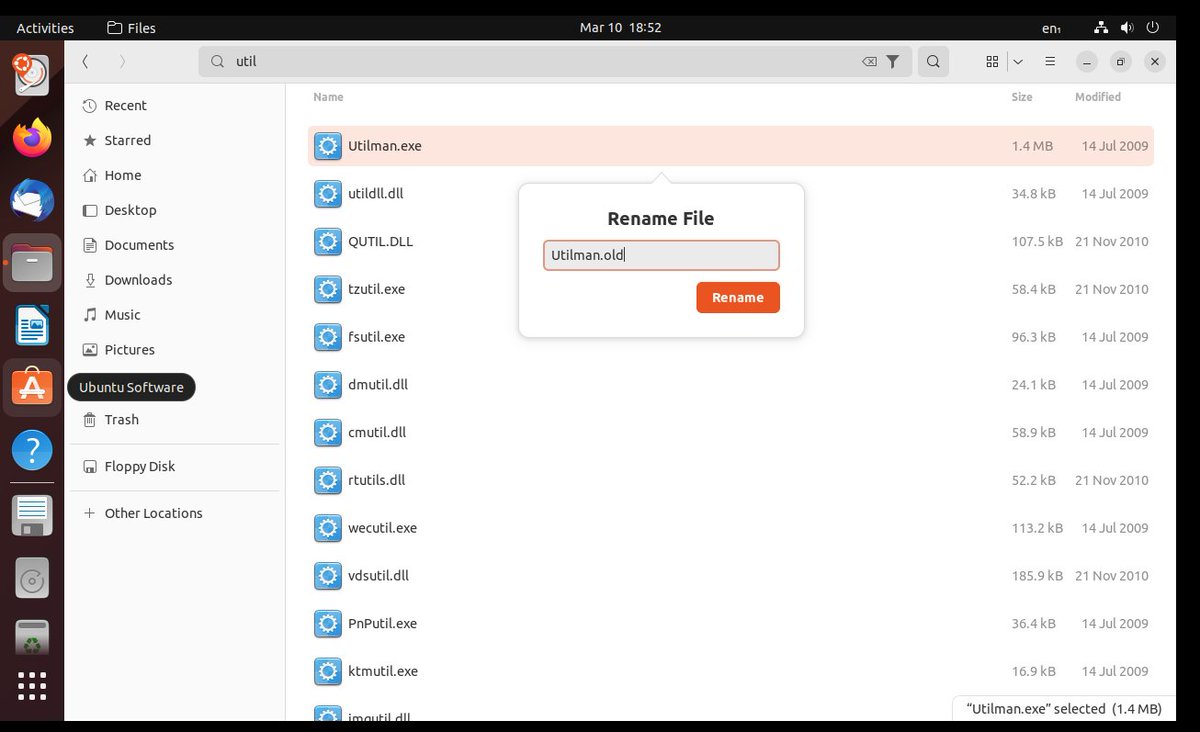
let's backdoor this because... my creds aren't working LOL rename utilman.exe to whatever, then copy cmd.exe to utilman.exe 


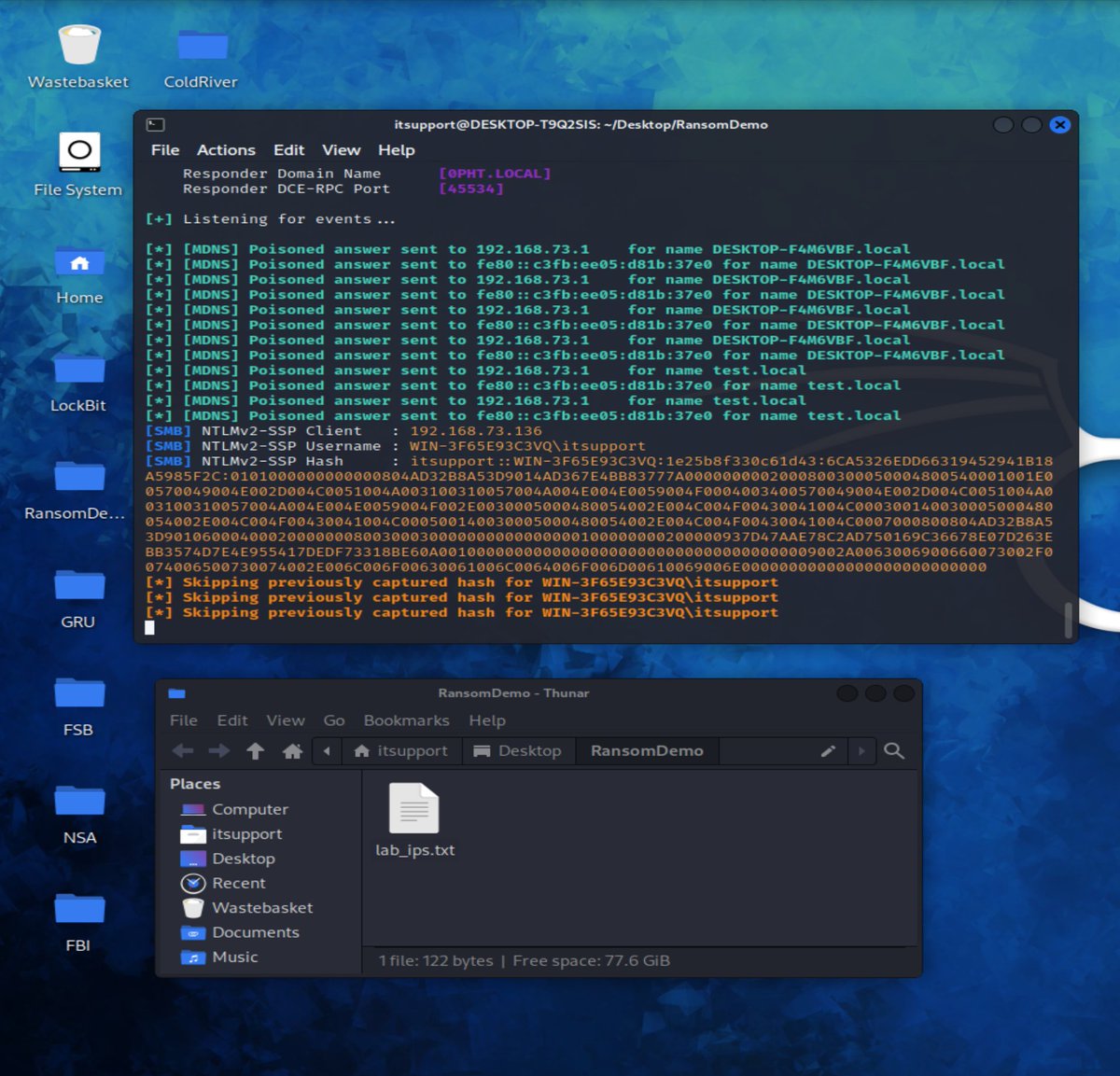
ok now from the RDP (NO NLA ENABLED) screen of console session we can click in the bottom left and we get a SYSTEM level CMD (pwn3d!) 

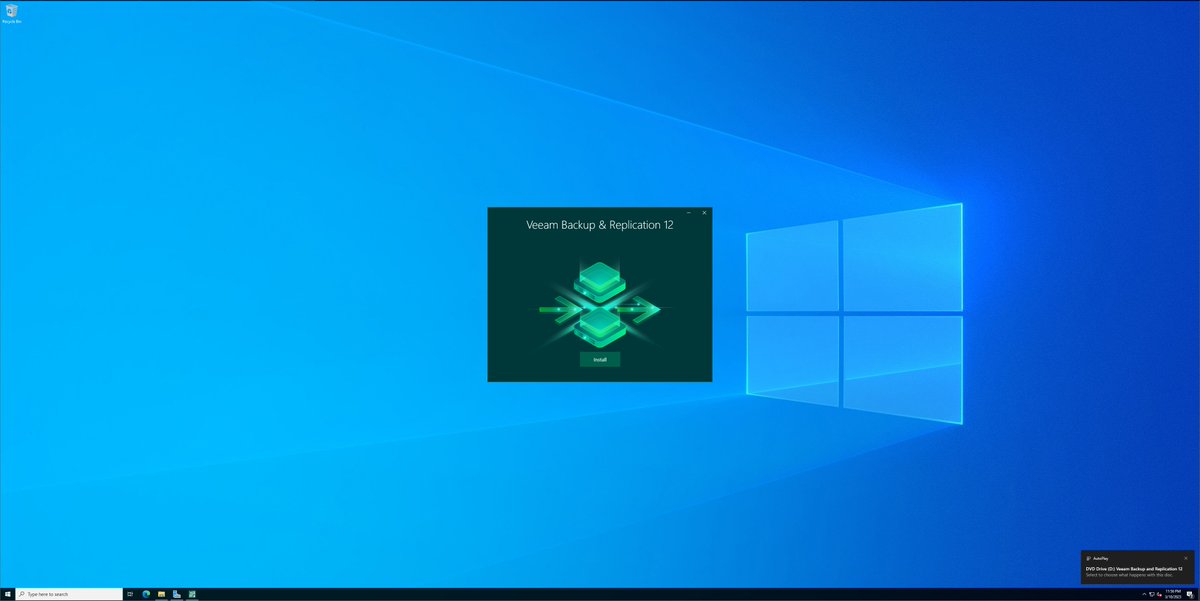
ok so whilst that builds... we need to think about some backup infra....
we are going to deploy @Veeam
we are going to deploy @Veeam
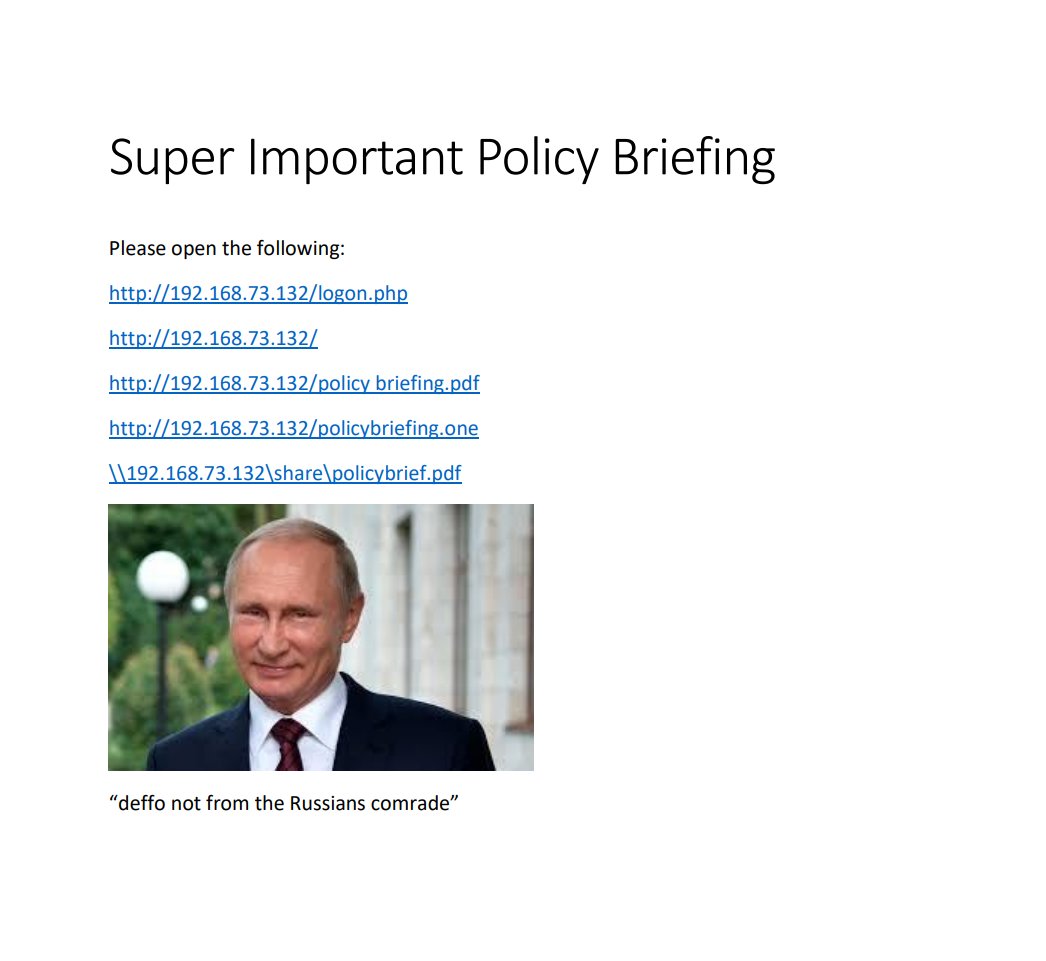
ok cool we have a few VMs to play with. Ideally we would have loads more like app servers, web servers, DMZs etc. but i'm tired and this will do 

Whilst we wait for installs, updates... let's make some LURES!
This one is TOP CLASS ATP MATERIAL based off REAL LIFE THREAT ACTORS!
I'm putting a few different types of link, I mean hell let's throw in a onenote document as well!
This one is TOP CLASS ATP MATERIAL based off REAL LIFE THREAT ACTORS!
I'm putting a few different types of link, I mean hell let's throw in a onenote document as well!
you can also use WINPEAS you can either just disable all the defences when you get on a box and find creds (hahaha no shit that is so common) or you can obfuscate some of it to not trigger the signatures
ok our attacker is here, i'm being well lazy but we have a simple HTTP server for hosting our LURE. now we could attack in a few ways:
Phish + maldoc
Phish + Web Inra + Maldoc
Phish + cred harvester
etc.
We could also attack supply chain, web apps, internet infra (e.g. VPNS) or… twitter.com/i/web/status/1…

Phish + maldoc
Phish + Web Inra + Maldoc
Phish + cred harvester
etc.
We could also attack supply chain, web apps, internet infra (e.g. VPNS) or… twitter.com/i/web/status/1…
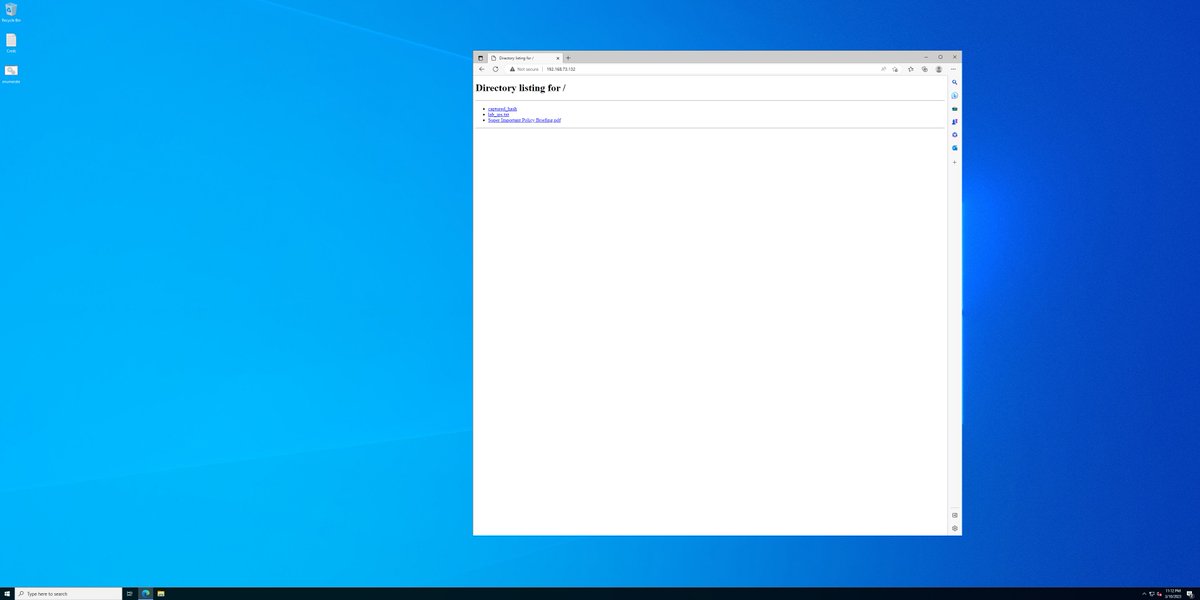
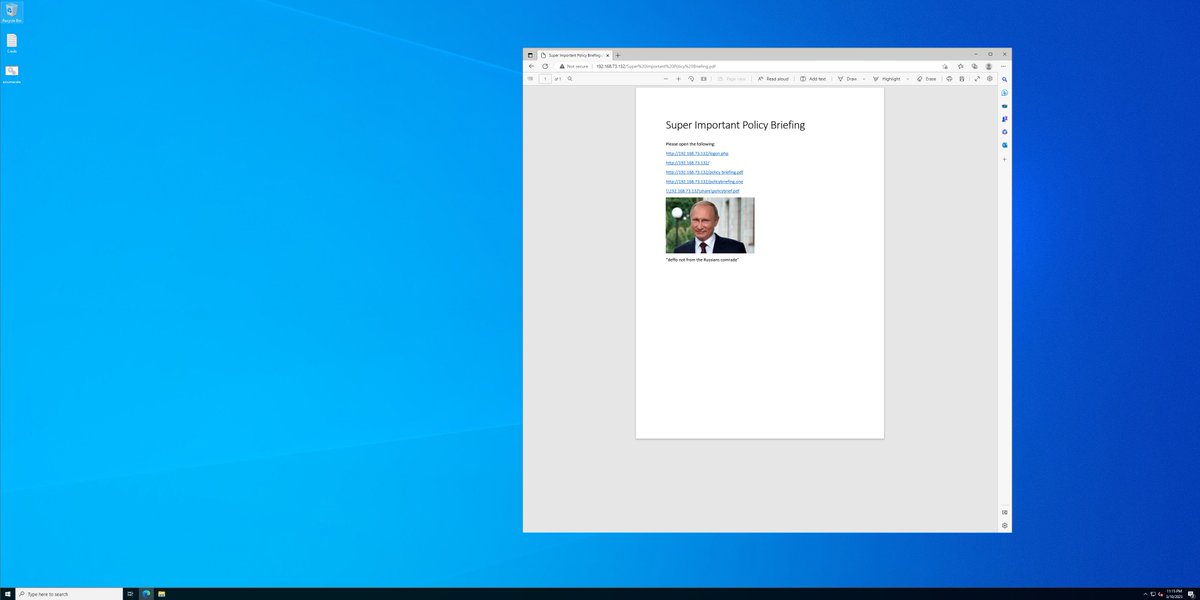
also i mean we could find a really expensive browser ZERO Day .. or let's just do the LIKELY thing and send someone a link to CLICK.
oh HAI A PDF!
oh HAI A PDF!
now coz i'm lazy i've just killed the HTTP server and then run responder and simulated clicking a link to wpad.. oh look a prompt... let's enter my creds! 

oh no, our IT administrator has been duped! VLAD the fuckwit criminal now has a username and a hash! 

ok we have now cracked the hash for our victim IT admin.
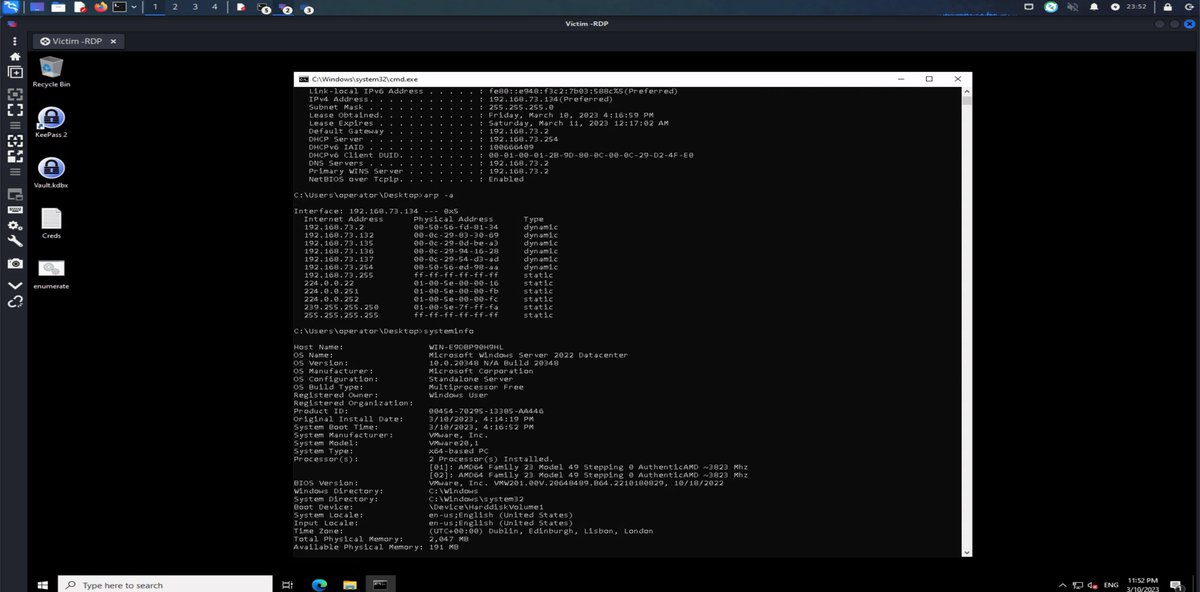
Now we can remote in via RDP. We shall wait and do this at night when they have gone home/stopped work.
Now we can remote in via RDP. We shall wait and do this at night when they have gone home/stopped work.

ok now our RANSOMWARE CRIMINAL has access as OPERATOR to the "REMOTE ADMIN WORKSTATION"
(this isn't fake, this occurs LOADS!)
(this isn't fake, this occurs LOADS!)

and now our attacker can now work through the victim operators machine. This might have:
> Windows Credential Manager Creds🔥
> Browser Credentials Stored🔥
> Creds in Memory (LSASS)🔥
> Creds in the registry🔥
> Creds in files🔥
> Creds in password managers 🔥
also we can do… twitter.com/i/web/status/1…
> Windows Credential Manager Creds🔥
> Browser Credentials Stored🔥
> Creds in Memory (LSASS)🔥
> Creds in the registry🔥
> Creds in files🔥
> Creds in password managers 🔥
also we can do… twitter.com/i/web/status/1…

oh and also FML also the SAM/SYSTEM files (the SYSTEM file is a registry file but the SAM is a local file)
anyway you get the picture.
We also need to hunt for documents, files, network metadata... anything that will let us think about how we can ESCLATE/PIVOT....
anyway you get the picture.
We also need to hunt for documents, files, network metadata... anything that will let us think about how we can ESCLATE/PIVOT....
as we can see there's LOTS that has already gone wrong... gonna pause on our ATTACKER journey as we need to deploy VEEAM and backup the stuff etc. also it's getting late! hopefully this is useful to people. it's a very rough version but this is how lots of people get ransomed (or… twitter.com/i/web/status/1… 
PART 2 VEEAM INSTALL
https://twitter.com/UK_Daniel_Card/status/1634434820804624384?s=20
• • •
Missing some Tweet in this thread? You can try to
force a refresh