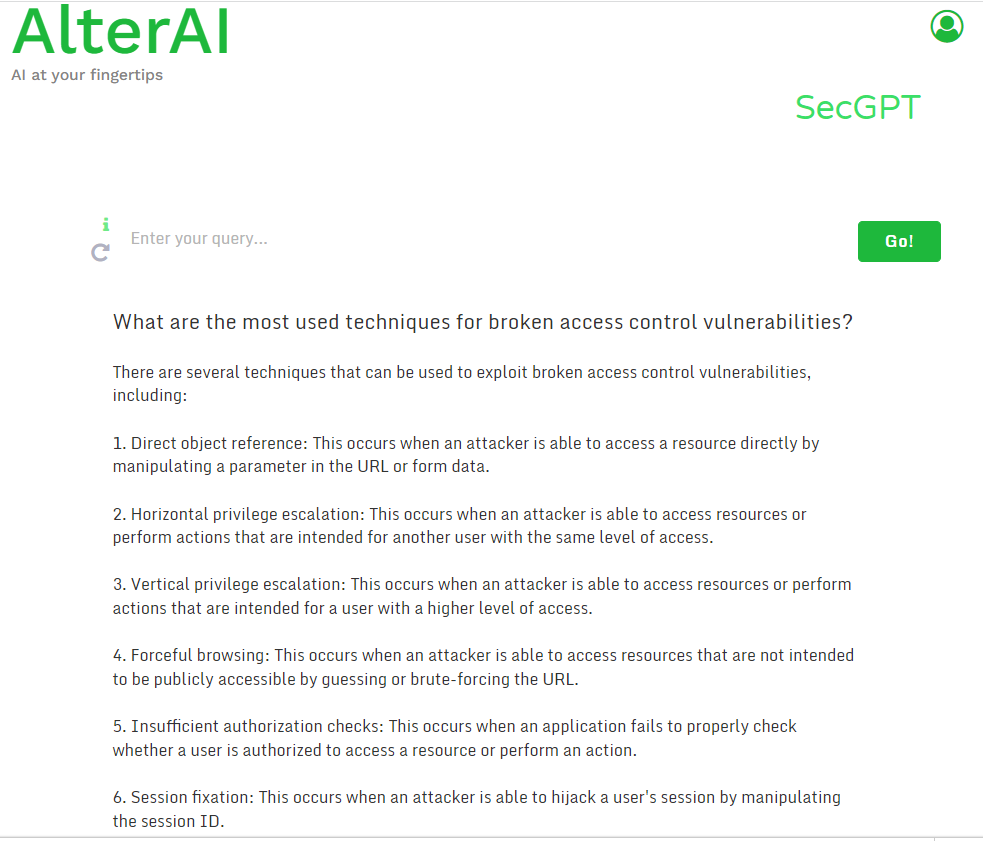
🚀🔒Exciting news! SecGPT is now LIVE!
Trained on thousands of cybersecurity reports, SecGPT revolutionizes cybersecurity with AI-driven insights.👇
Trained on thousands of cybersecurity reports, SecGPT revolutionizes cybersecurity with AI-driven insights.👇

1. Trained on an extensive collection of cybersecurity reports, @SecGPT provides you with a deeper understanding of vulnerabilities, exploitation techniques, and emerging trends in cybersecurity.
Its knowledge increases as more reports and writeups are published.
Its knowledge increases as more reports and writeups are published.
2. Explore SecGPT's capabilities and see how it can assist you in enhancing your cybersecurity expertise.
Try it out for free at alterai.me
#ai #cybersecurity #infosec #pentesting #ethicalhacking #bugbounty #bugbountytips #secgpt
Try it out for free at alterai.me
#ai #cybersecurity #infosec #pentesting #ethicalhacking #bugbounty #bugbountytips #secgpt
Tips to use:
Don't ask:
"top <SSRF> payloads" or something like that => It will throw you ethics reply.
Consider SecGPT as an AI trained on thousands of reports, It doesn't know everything, it knows only what's been trained on.
Ask, instead:
What is an interesting report on… twitter.com/i/web/status/1…
Don't ask:
"top <SSRF> payloads" or something like that => It will throw you ethics reply.
Consider SecGPT as an AI trained on thousands of reports, It doesn't know everything, it knows only what's been trained on.
Ask, instead:
What is an interesting report on… twitter.com/i/web/status/1…
Also, do not ask for:
Give me 10 <something>.
While still small, it may not find 10 exact relevant pieces to your query, therefore it will not respond.
Instead, ask specifically:
Is there a payload to bypass XSS filters when ">" is not allowed?
Be specific!
Give me 10 <something>.
While still small, it may not find 10 exact relevant pieces to your query, therefore it will not respond.
Instead, ask specifically:
Is there a payload to bypass XSS filters when ">" is not allowed?
Be specific!
Needles to say @LangChainAI and @hwchase17 FTW.
Some users had issues signing up. It's fixed now.
• • •
Missing some Tweet in this thread? You can try to
force a refresh