🐀 AsyncRAT 🐀 - Defeating Obfuscation Using CyberChef
An overview of some advanced CyberChef tricks for decoding malware
[1/12] 🧵
#AsyncRAT #Decoding #CyberChef #Malware



An overview of some advanced CyberChef tricks for decoding malware
[1/12] 🧵
#AsyncRAT #Decoding #CyberChef #Malware

[2/] First, some links if you wish to follow along.
The Malware File: bazaar.abuse.ch/sample/26c9f29…
Links to CyberChef Recipes:
github.com/embee-research…
The Malware File: bazaar.abuse.ch/sample/26c9f29…
Links to CyberChef Recipes:
github.com/embee-research…
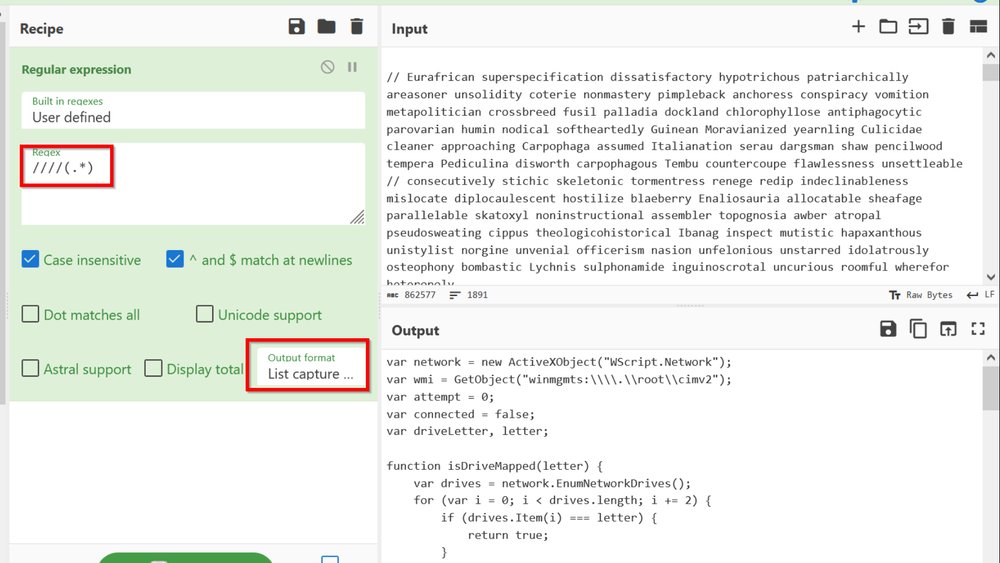
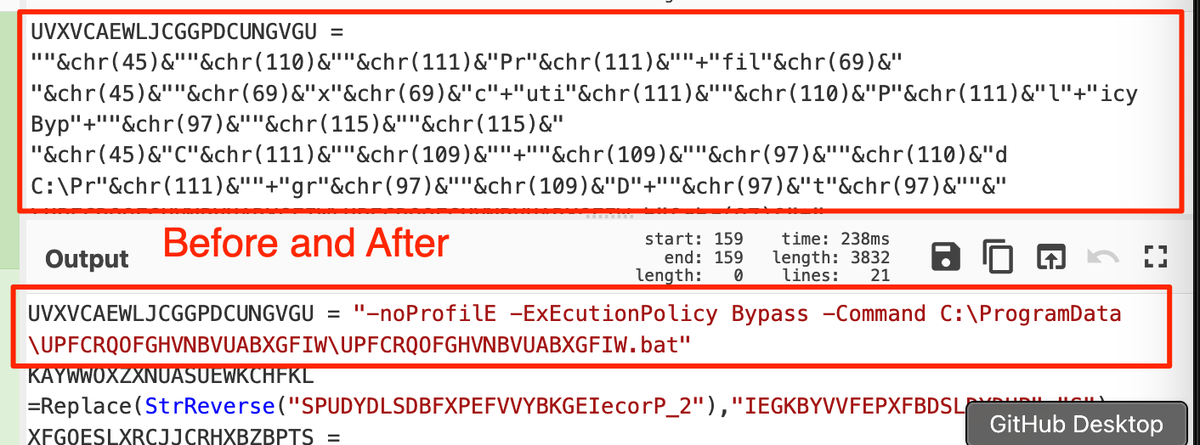
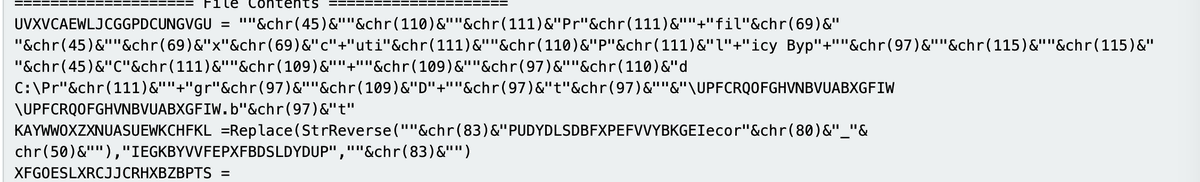
[3] Decimal Values:
Some text is converted to decimal to hinder simple text based analysis.
To defeat:
- Subsection - This grabs encoded data without removing the rest of the script
- Regex - Grab the decimal and ignore the "chr" junk
- From Decimal - Decode the decimal
Some text is converted to decimal to hinder simple text based analysis.
To defeat:
- Subsection - This grabs encoded data without removing the rest of the script
- Regex - Grab the decimal and ignore the "chr" junk
- From Decimal - Decode the decimal
[4] Decimal Values P2:
- Merge - Removes Subsection - Allowing future operations to apply to the entire script.
- Find/Replace - Remove remaining string concatenation ("+") etc
- Syntax Highlighter - Make the resulting script pretty


- Merge - Removes Subsection - Allowing future operations to apply to the entire script.
- Find/Replace - Remove remaining string concatenation ("+") etc
- Syntax Highlighter - Make the resulting script pretty



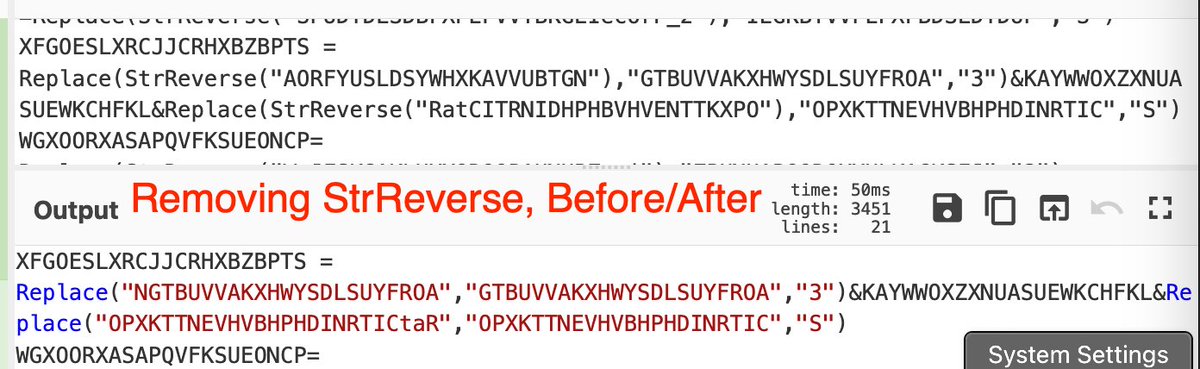
[5] Reversed Strings P1:
Reversed strings are used to further hinder analysis and evade simple text analysis.
To Defeat:
- Subsection - Grab only the reversed content, including references to the "StrReverse" function.
- Regex - Grab only content between quotes ".*" This...


Reversed strings are used to further hinder analysis and evade simple text analysis.
To Defeat:
- Subsection - Grab only the reversed content, including references to the "StrReverse" function.
- Regex - Grab only content between quotes ".*" This...

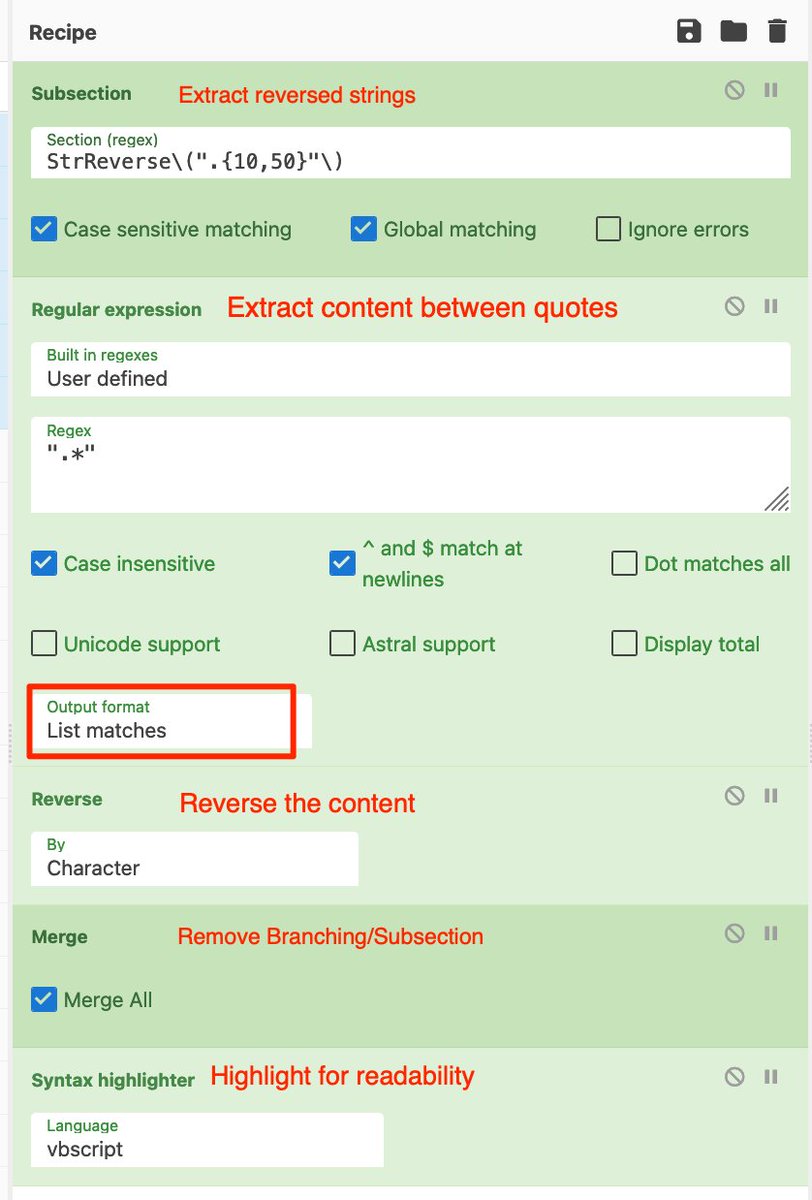
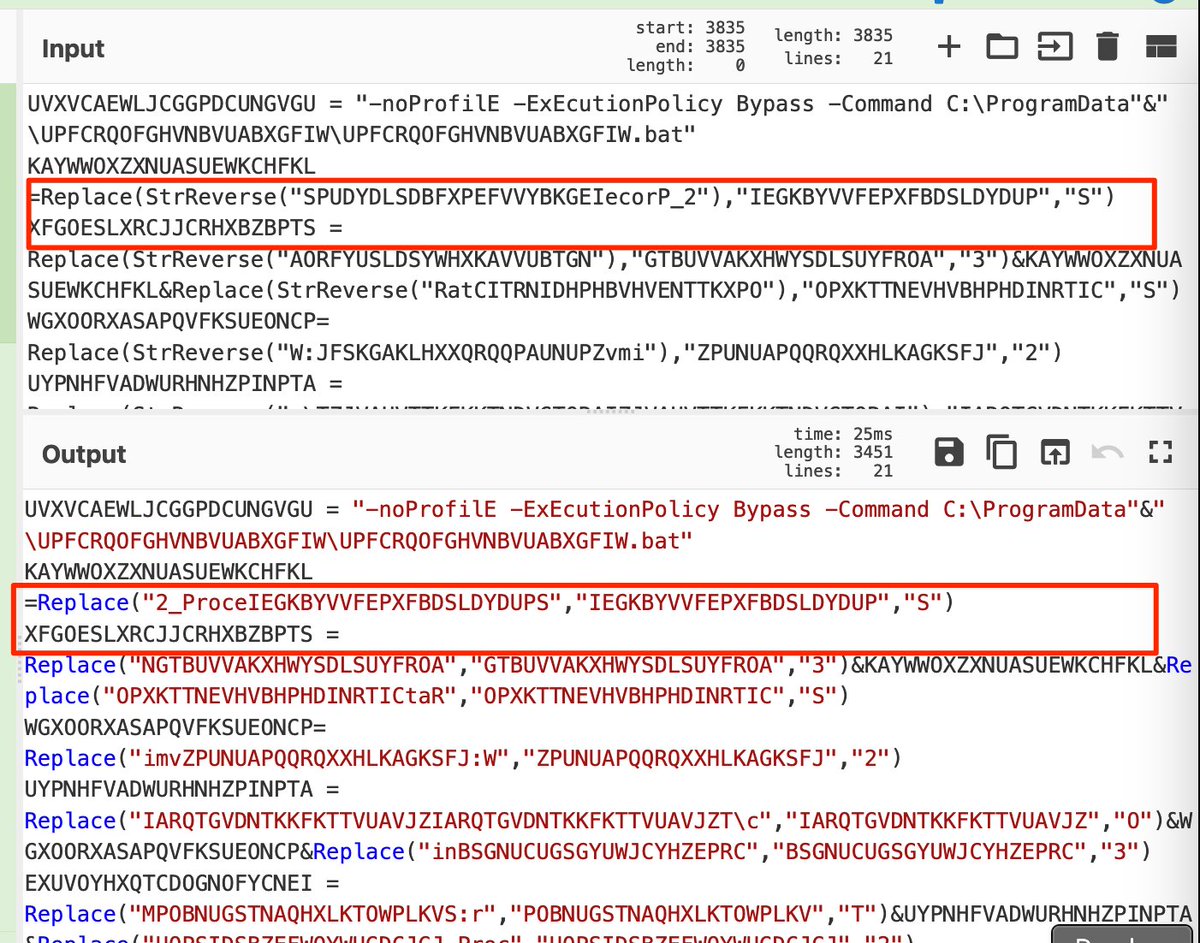
[6] .. gives us only the reversed string. Ignoring the "StrReverse" component.
- Reverse - Perform the string reverse operation
- Merge - Removes our subsection
- Syntax Highlighter - Make it all look pretty
- Reverse - Perform the string reverse operation
- Merge - Removes our subsection
- Syntax Highlighter - Make it all look pretty

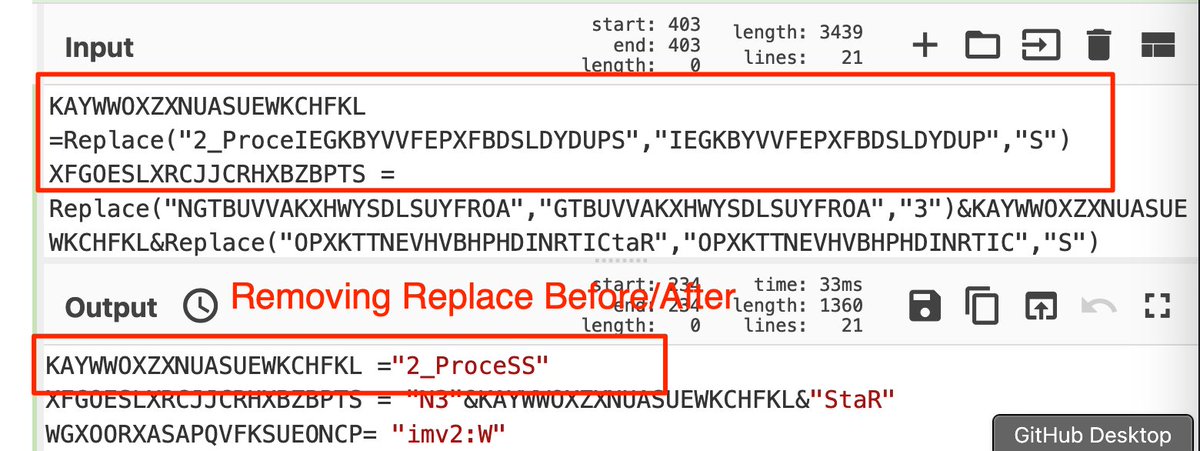
[7] String Replace:
Replace operations are used to further obfuscate text.
#Deobfuscation is similar to above
To Defeat:
- Subsection - To retrieve all content related to the replace operation.
- Register - Using the same regex as before, but adds capture groups to...

Replace operations are used to further obfuscate text.
#Deobfuscation is similar to above
To Defeat:
- Subsection - To retrieve all content related to the replace operation.
- Register - Using the same regex as before, but adds capture groups to...


[8] ... Adds capture groups so that we can group content and create variables for future operations. -
$R0 = Encoded String,$R1 = StringToRemove,$R2 = ReplaceValue) etc.
- Regular Expression - Now that our variables are made, we can use regex to show only the encoded value.
$R0 = Encoded String,$R1 = StringToRemove,$R2 = ReplaceValue) etc.
- Regular Expression - Now that our variables are made, we can use regex to show only the encoded value.
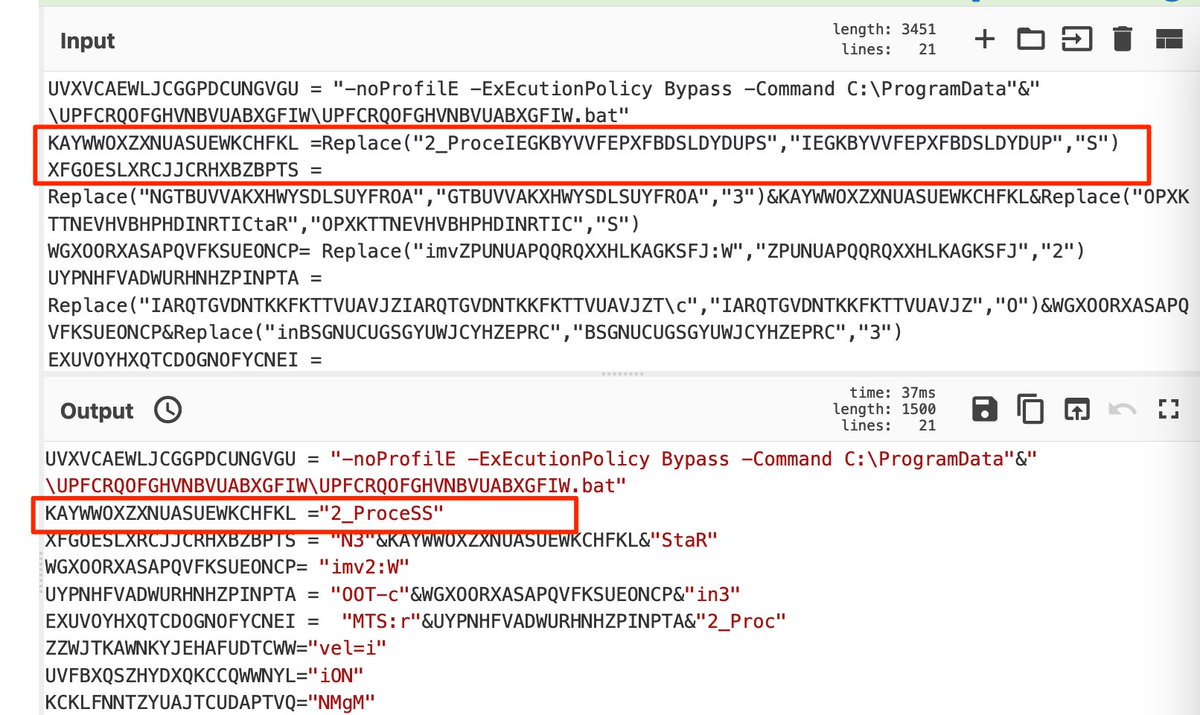
[9] Find/Replace - This allows us to perform the string replace using the previously created variables.
eg (From $R0; Remove all instances of $R1; Then Replace $R1 with the value $R2)
Merge - Remove the subsection
Syntax - Make it look pretty.
Before and After
eg (From $R0; Remove all instances of $R1; Then Replace $R1 with the value $R2)
Merge - Remove the subsection
Syntax - Make it look pretty.
Before and After
[10] More String Replace:
The last encoding is the most simple, and simply uses variables to store strings, which are then concatenated together.
I couldn't find a way to decode this part using only Cyberchef (so let me know if you have a way)
The last encoding is the most simple, and simply uses variables to store strings, which are then concatenated together.
I couldn't find a way to decode this part using only Cyberchef (so let me know if you have a way)

[11] Luckily, this task is well suited for a simple print statement.
This can be achieved in the browser (ideally in a safe VM) after replacing the (&) with a more #javascript friendly (+).
Then pasting the content into the browser console.


This can be achieved in the browser (ideally in a safe VM) after replacing the (&) with a more #javascript friendly (+).
Then pasting the content into the browser console.



[12] We now have the decoded values and can determine (mostly statically) what the malware is trying to achieve.
In this case, the malware script's ultimate goal is to execute a .bat script via #powershell.
Not the most exciting outcome but a cool study into #cyberchef :)

In this case, the malware script's ultimate goal is to execute a .bat script via #powershell.
Not the most exciting outcome but a cool study into #cyberchef :)


• • •
Missing some Tweet in this thread? You can try to
force a refresh