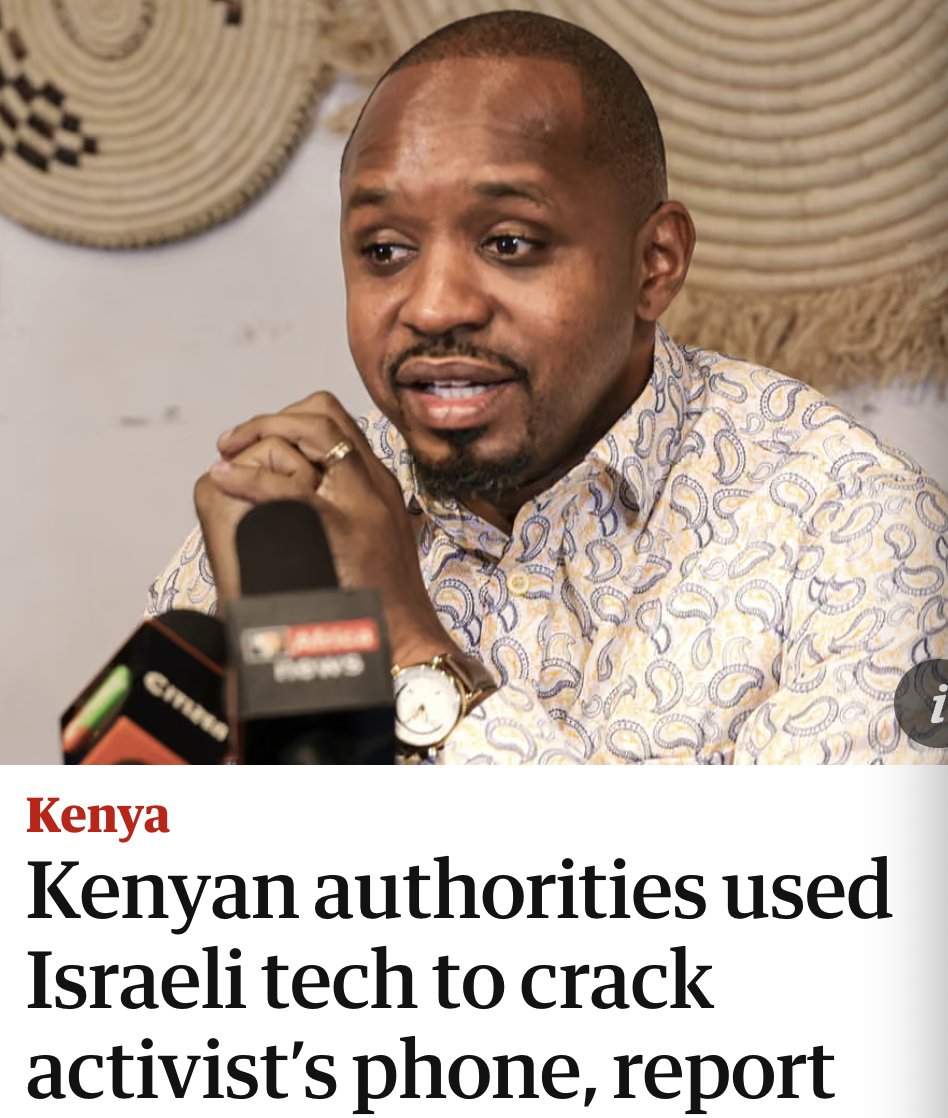
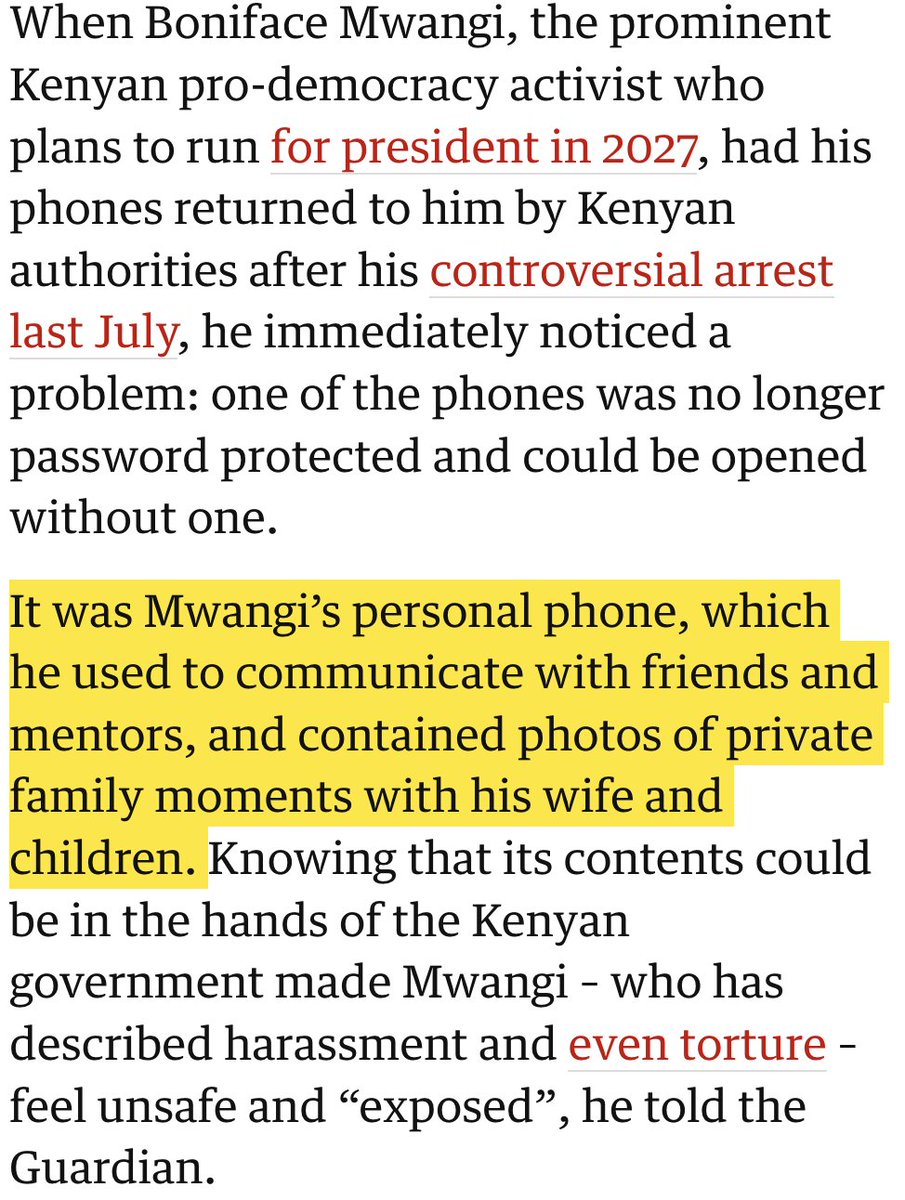
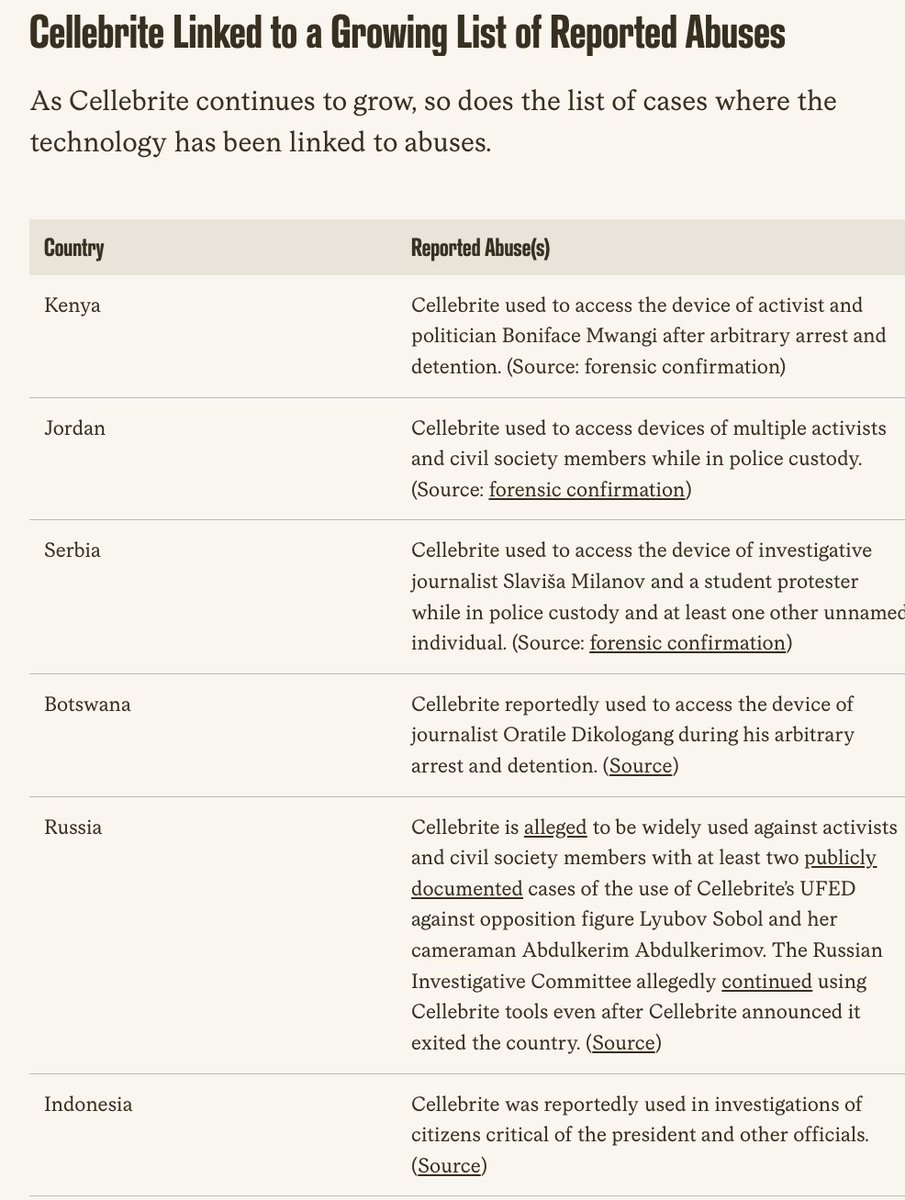
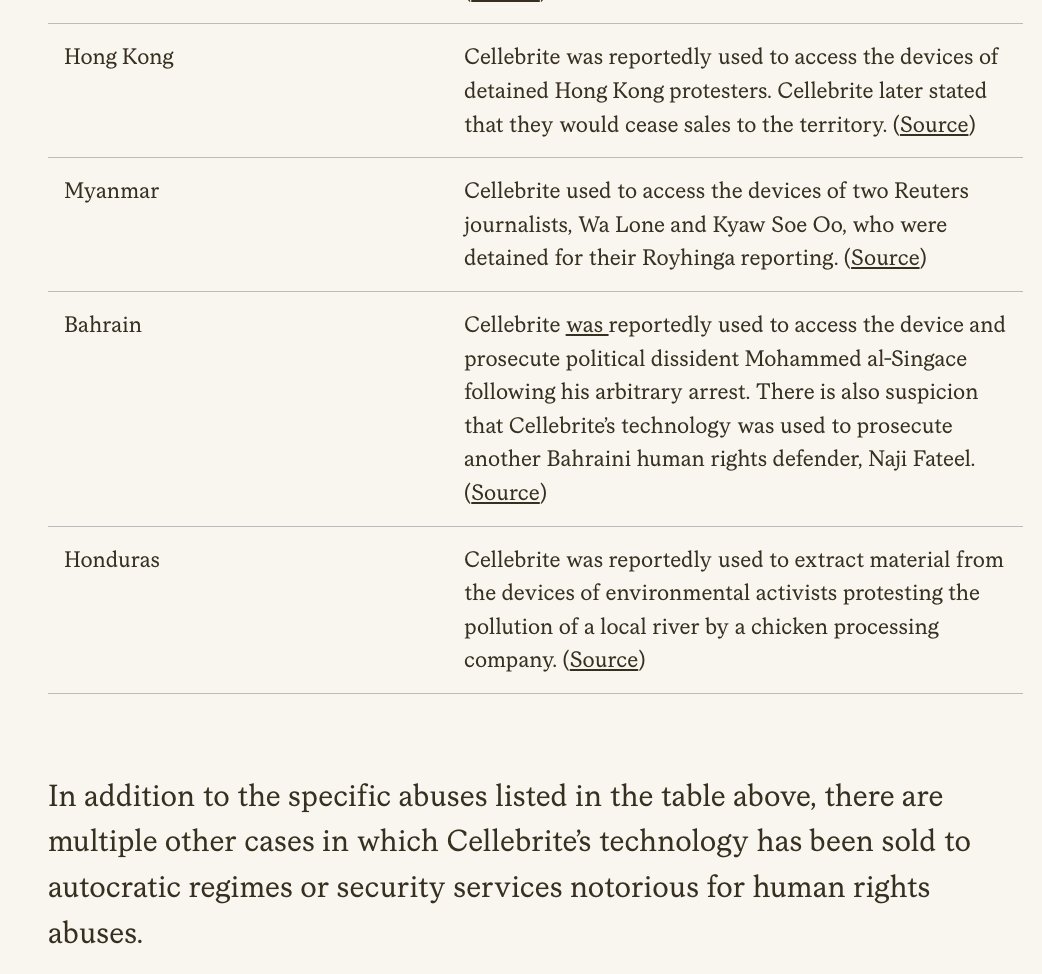
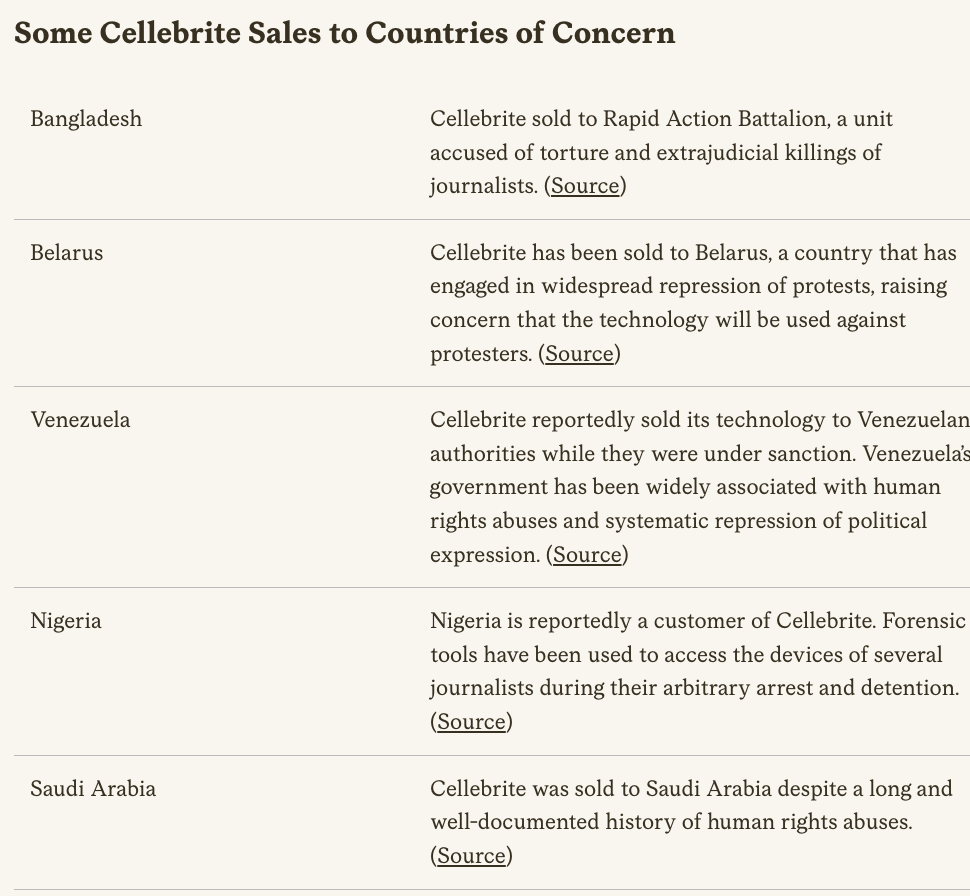
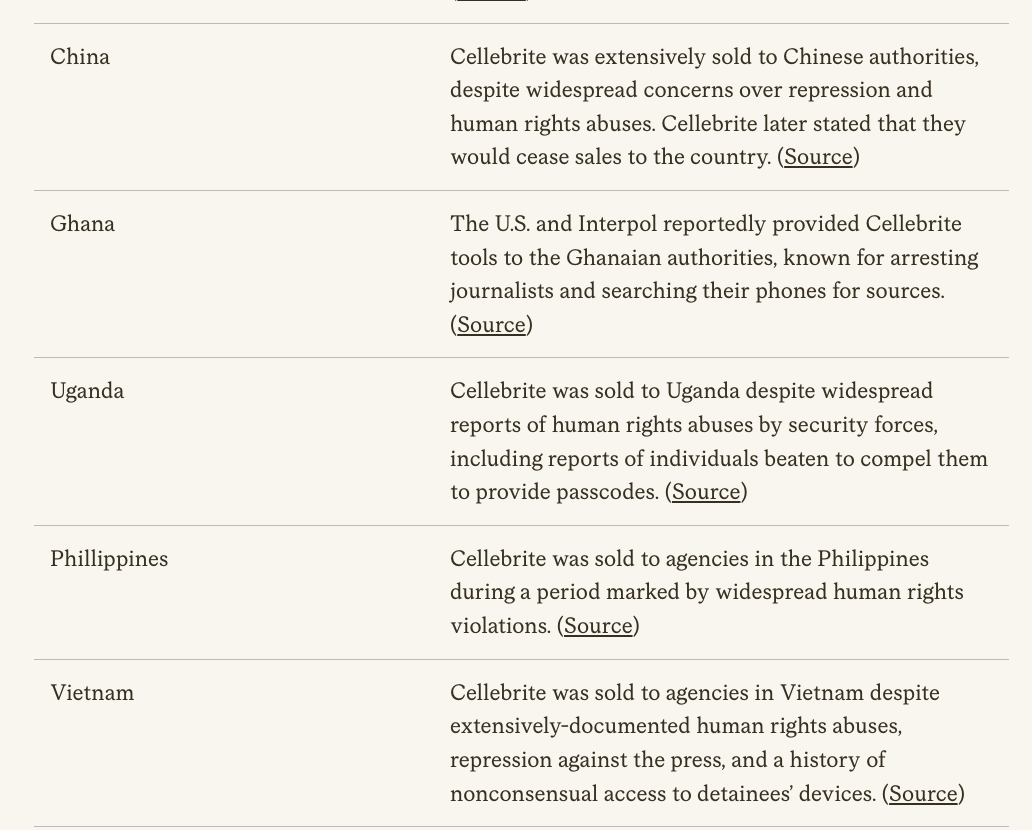
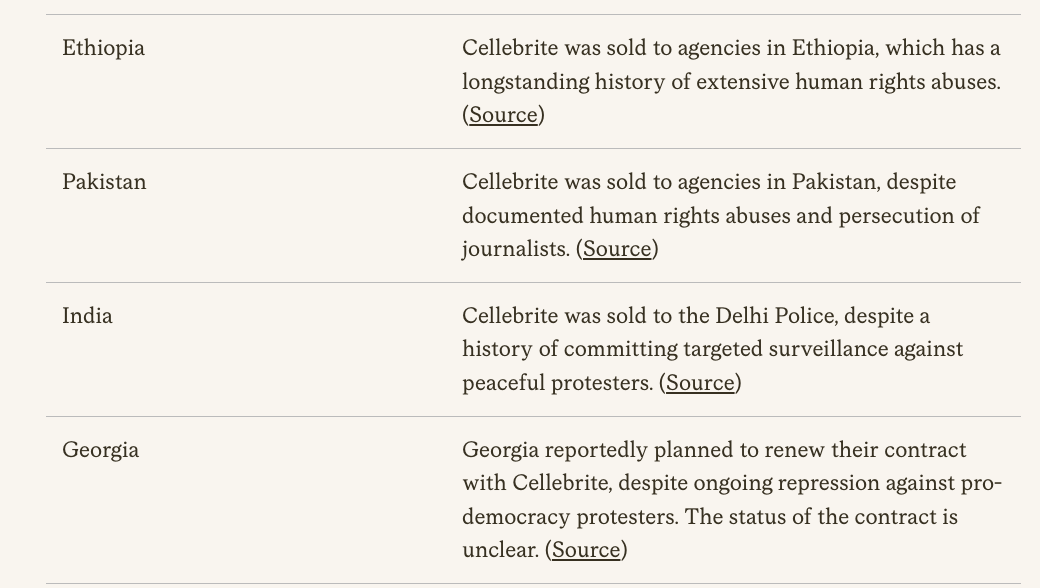
BREAKING: Biden White House issues executive order on commercial spyware.
Also confirms over 50+ USG personnel suspected targeted w/#Pegasus
Huge deal, let me break the new #SpywareEO down. 1/

Also confirms over 50+ USG personnel suspected targeted w/#Pegasus
Huge deal, let me break the new #SpywareEO down. 1/


2/ Investment fuels spyware proliferation. A lot of that is predicated on the juicy dream of the USG as the ultimate customer.
The new #SpywareEO says to mercenary spyware vendors & backers: decision time.
Either stop contributing to proliferation right now, or lose our number.
The new #SpywareEO says to mercenary spyware vendors & backers: decision time.
Either stop contributing to proliferation right now, or lose our number.
3/ Biden's #SpywareEO's closes door for vendors if their spyware has:
❌Been used against USG
❌Has counterintelligence / foreign intel risks
-or-
❌ Abused for repression
❌Used on 🇺🇸Americans
❌Sold to govs that systematically do political repression.

❌Been used against USG
❌Has counterintelligence / foreign intel risks
-or-
❌ Abused for repression
❌Used on 🇺🇸Americans
❌Sold to govs that systematically do political repression.


4/ For each component of the #SpywareEO I'm going to relate it to something concrete.
Let's call it the #Pegasus factor: would provision result in blocking USG from purchasing spyware from NSO for operational use?
Link to the full EO: whitehouse.gov/briefing-room/…
Let's call it the #Pegasus factor: would provision result in blocking USG from purchasing spyware from NSO for operational use?
Link to the full EO: whitehouse.gov/briefing-room/…
5/ First #SpywareEO component: national security, counterintelligence
Clearly derived from recent experiences with NSO.
#Pegasus factor? Yes, the EO would likely block NSO as a vendor.
Clearly derived from recent experiences with NSO.
#Pegasus factor? Yes, the EO would likely block NSO as a vendor.

6/Second #SpywareEO trigger: abuses.
Reflects the broad spectrum #spyware harms happen.
But *also* and critically, situations where vendors should expect that their product, once sold, will inevitably be abused.
#Pegasus factor: Ouch. NSO again would get dinged.
Reflects the broad spectrum #spyware harms happen.
But *also* and critically, situations where vendors should expect that their product, once sold, will inevitably be abused.
#Pegasus factor: Ouch. NSO again would get dinged.

7/ I initially expected #SpywareEO to look like a allow/deny aka "blacklist" of spyware sellers..
But the EO's conduct based definitions = constant shell game of vendors corporate identities is blunted.
Even applies to companies that haven't been formed yet.
Probably better.
But the EO's conduct based definitions = constant shell game of vendors corporate identities is blunted.
Even applies to companies that haven't been formed yet.
Probably better.
8/ Lots of spyware companies absolutely know what they are doing.
What's especially interesting is the term "remove" to describe risks.
Not the milquetoast & unverifiable "mitigate."
#SpywareEO is saying: cancel the contracts & more.
And you may still be toast. Do it now.
What's especially interesting is the term "remove" to describe risks.
Not the milquetoast & unverifiable "mitigate."
#SpywareEO is saying: cancel the contracts & more.
And you may still be toast. Do it now.

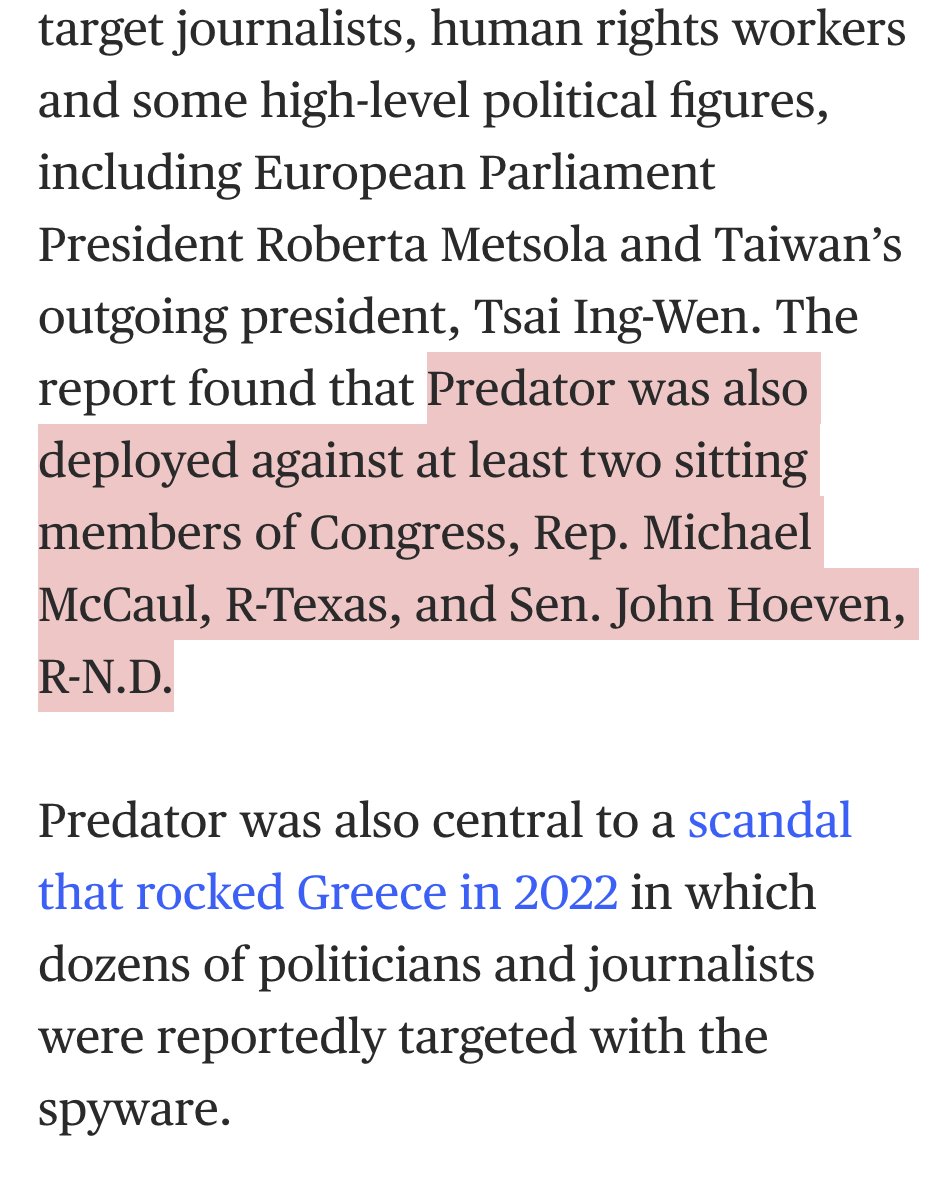
9/ Reports in the past that USG entities may have occasionally facilitated spyware purchases / acquisition by other governments.
If the #SpywareEO abuse/natsec/counterintelligence triggers are met... that door now closes.
If the #SpywareEO abuse/natsec/counterintelligence triggers are met... that door now closes.

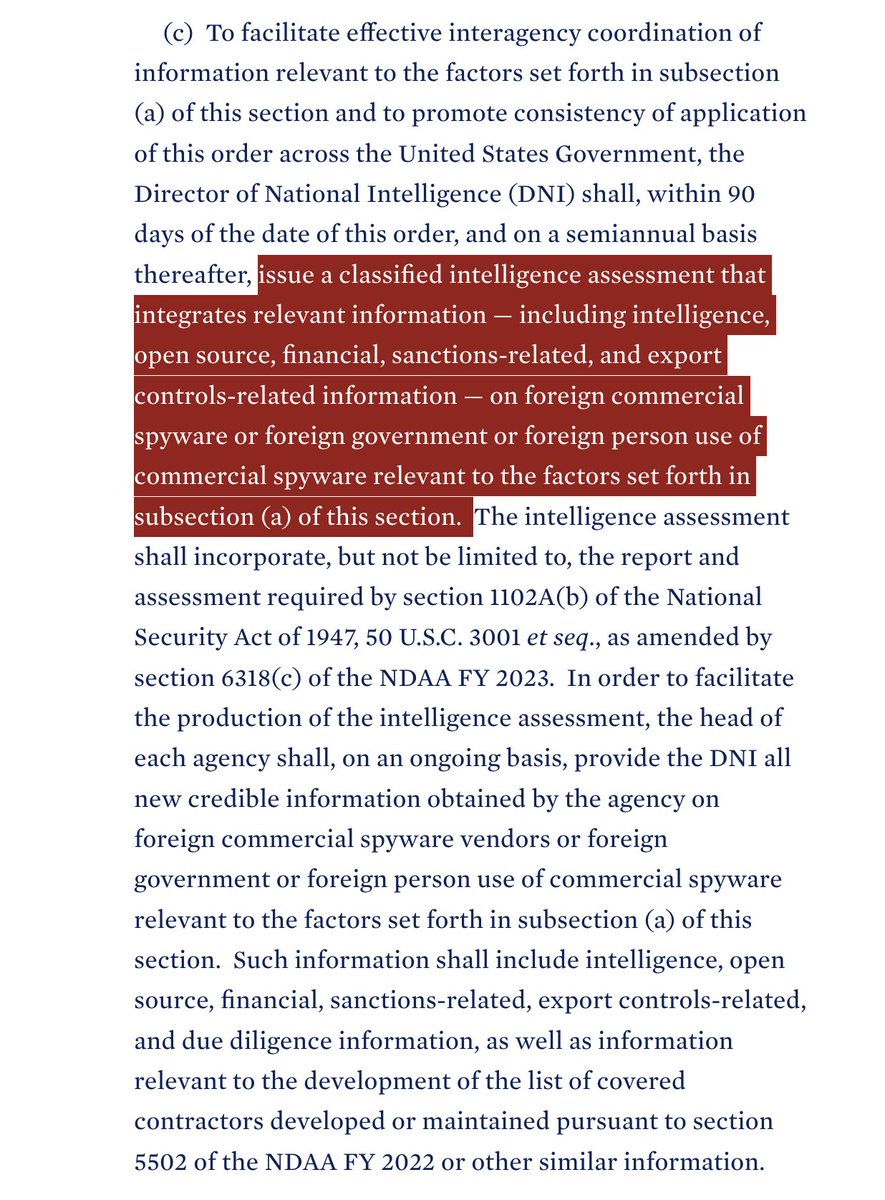
10/ How does the USG know if #spyware vendors hit the #SpywareEO's triggers?
The EO contains a robust set of reporting requirements around misuses from the Intel community & procurement reporting.
Seems intended to prevent vendors from slipping through the cracks.



The EO contains a robust set of reporting requirements around misuses from the Intel community & procurement reporting.
Seems intended to prevent vendors from slipping through the cracks.

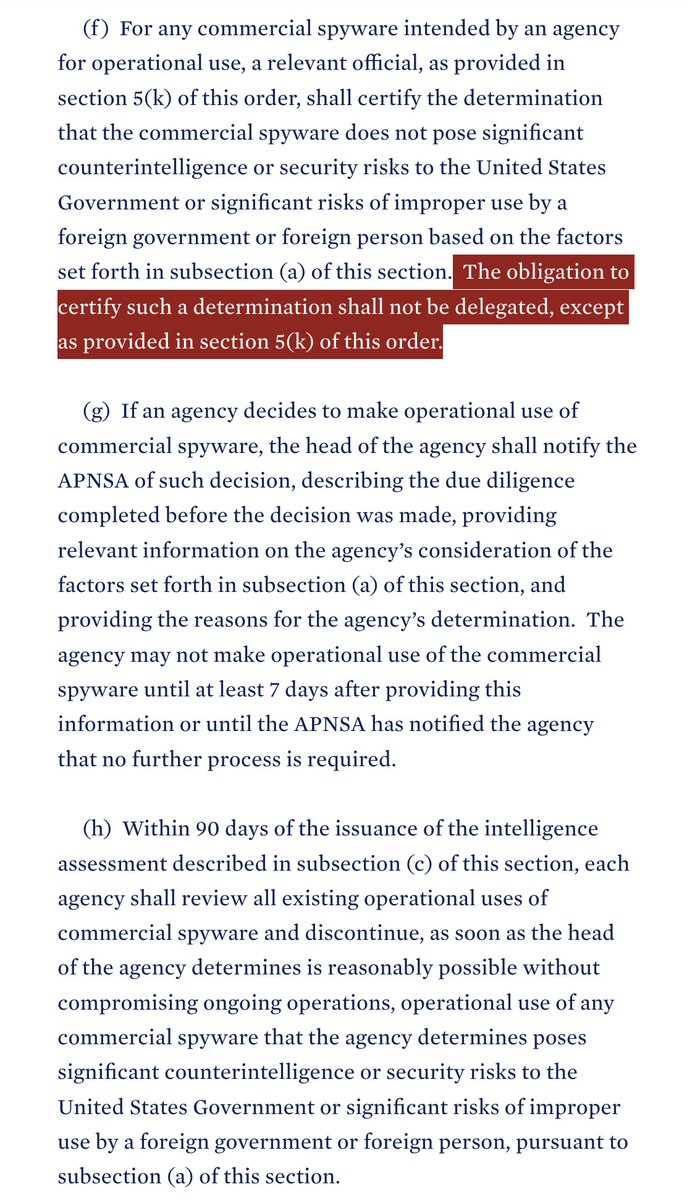

11/ Use of the "operational use" term is interesting.
And creates carve outs for things like testing & analysis.
Analogy: USG can buy an anti-tank missile from a shady entity to test it against armor, but can't reward the vendor by equipping the whole military with them.
And creates carve outs for things like testing & analysis.
Analogy: USG can buy an anti-tank missile from a shady entity to test it against armor, but can't reward the vendor by equipping the whole military with them.

12/ Takeaway: The #SpywareEO is the first comprehensive action by any government on #spyware.
It was clearly drafted to pump the breaks on proliferation & is written with a good understanding the slippery nature of the industry.
It closes many loopholes.
It was clearly drafted to pump the breaks on proliferation & is written with a good understanding the slippery nature of the industry.
It closes many loopholes.
13/ Whenever the USG regulates there's always temptation to speculate about protectionism for American companies.
But reading the #SpywareEO...these provisions hit US-based spyware companies just as hard if they meet the triggers / contribute to proliferation.
Good.
But reading the #SpywareEO...these provisions hit US-based spyware companies just as hard if they meet the triggers / contribute to proliferation.
Good.
14/ Every government wants to not tie their hands too tightly, so there is a waiver provision.
But what's interesting is how restricted this is. This is a very high bar.
The #SpywareEO is not designed to be easily circumvented by someone in a corner of the USG bureaucracy.
But what's interesting is how restricted this is. This is a very high bar.
The #SpywareEO is not designed to be easily circumvented by someone in a corner of the USG bureaucracy.

15/ I've spent over a decade researching commercial spyware.
The #spywareEO is one of the most consequential actions to blunt proliferation that I've seen a government take.
So, where do we go from here?
The #spywareEO is one of the most consequential actions to blunt proliferation that I've seen a government take.
So, where do we go from here?
16/ While the #SpywareEO addresses federal procurement, it doesn't hit state & local agencies.
And we know these are targets for sales by NSO Group & others.
This is going to be a really important area in coming years.
By: @josephfcox
vice.com/en/article/m7v…
And we know these are targets for sales by NSO Group & others.
This is going to be a really important area in coming years.
By: @josephfcox
vice.com/en/article/m7v…
17/ Second, while USG is a big & juicy prize, European governments are another core vendor target.
And #Germany is an example of a country on the wrong side of history on this.
Hopefully the #spywareEO provides a better model for how to not reward the worst of the worst.
And #Germany is an example of a country on the wrong side of history on this.
Hopefully the #spywareEO provides a better model for how to not reward the worst of the worst.

18/ I expect the #SpywareEO to immediately chill investor comfort with reckless spyware vendors...
Some prospectuses are probably hitting the shredder right now.
But also need to see other direct disincentives for US-based investors that fuel harmful spyware proliferation.
Some prospectuses are probably hitting the shredder right now.
But also need to see other direct disincentives for US-based investors that fuel harmful spyware proliferation.
19/ Remarkable to see @POTUS and the White House leaning this hard into the issue.
This is what global leadership looks like.
It also would not have happened without tremendous work from civil society and many brave #spyware victims coming forward year. after. year.
This is what global leadership looks like.
It also would not have happened without tremendous work from civil society and many brave #spyware victims coming forward year. after. year.
• • •
Missing some Tweet in this thread? You can try to
force a refresh