The selling of this bitcoin is, by far, the least interesting part of the saga.
The govt's seizure, the dude who had his bitcoin seized, and why it even got seized in the first place is full of so many amazing, hysterical, enraging gems.
Heads up...not a short story. Buckle up.
The govt's seizure, the dude who had his bitcoin seized, and why it even got seized in the first place is full of so many amazing, hysterical, enraging gems.
Heads up...not a short story. Buckle up.
https://twitter.com/tier10k/status/1641821284341280768
To set the stage, dude w/ the bitcoin is a super OG bitcoiner living in Gainesville, Georgia.
In Sept 2012 he executed a very basic "hack" on the Silk Road and withdrew the coins.
Not a bad dude. Not a huge hack either. Way less than a mil at the time.
justice.gov/usao-sdny/pr/u…
In Sept 2012 he executed a very basic "hack" on the Silk Road and withdrew the coins.
Not a bad dude. Not a huge hack either. Way less than a mil at the time.
justice.gov/usao-sdny/pr/u…

After collecting up all these coins (~60k BTC) this dude, from at least 2012 thru at least 2021, fucking *lived* life. 

Like, seriously, #bitcoinsquadgoals 

what could ever be better than getting hammered and trolling roger and jihan with your stash of 60k btc + btc-fork coins?? 😂 

Keep in mind, this entire time, dude has a fucking stash of BTC thats growing from ~$150k to ~$3.36 billion dollars!!!!!
😳
where do you even keep ~$3.36 billion dollars????!!?
😳
where do you even keep ~$3.36 billion dollars????!!?
Turns out, he had a "state-of-the-art computer setup" protecting his coins.
Well, he had a "state-of-the-art computer setup" at least.
Well, he had a "state-of-the-art computer setup" at least.

He kept his $3+ billy bitcoin in an underground floor safe.
And on a raspberry pi under blankets in a popcorn tin in his bathroom closet.
And on a raspberry pi under blankets in a popcorn tin in his bathroom closet.

Now obviously youre wondering, "damn. how'd he get caught?"
And, well, considering he signed a message using his 60k BTC key and posted it to bitcointalk... 🙈
A better question though is *why* did he get caught? Like, who cares that someone hacked Silk Road back in 2012????
And, well, considering he signed a message using his 60k BTC key and posted it to bitcointalk... 🙈
A better question though is *why* did he get caught? Like, who cares that someone hacked Silk Road back in 2012????
Turns out the govt cares. They *really* care. But not about lil Jimmy. Nope.
Govt cares bc it would look *really* bad if corrupt federal agents who were investigating Silk Road in 2013 still had a $3b stash of BTC that the (less corrupt) investigation in 2015 missed. 😬
Govt cares bc it would look *really* bad if corrupt federal agents who were investigating Silk Road in 2013 still had a $3b stash of BTC that the (less corrupt) investigation in 2015 missed. 😬
I know—that last tweet was a doozy. Let's back up. You need some more context so you can appreciate what's happening here.
If we rewind even further back to 2011, Adrian Chen of Gawker infamy discovered the Silk Road and wrote about it.
gawker.com/the-undergroun…—
If we rewind even further back to 2011, Adrian Chen of Gawker infamy discovered the Silk Road and wrote about it.
gawker.com/the-undergroun…—
In response, Sens. Charles Schumer of New York and Joe Manchin of West Virginia stood up on their high horses and demanded, loudly, that the DOJ and DEA 'shut down this shit down immediately!!!!!'
archive.sltrib.com/article.php?id…
archive.sltrib.com/article.php?id…

And in response to that every possible agency jumped up and started trying to take down Silk Road.
Like, literally, all of them.
FBI, USSS, ICE, HSI, DEA, IRS-CI, USPS and random ass local agencies / individual agents, too.
h/t @lamoustache antilop.cc/sr/#timeline
Like, literally, all of them.
FBI, USSS, ICE, HSI, DEA, IRS-CI, USPS and random ass local agencies / individual agents, too.
h/t @lamoustache antilop.cc/sr/#timeline

Naturally, due to the huge number of federal cooks in the kitchen + the newness of Bitcoin + the fact being a federal law enforcement agent does preclude you from being a lying, stealing, scheming, greedy bastard...it didnt go super well.
h/t @a_greenberg amazon.com/Tracers-Dark-G…
h/t @a_greenberg amazon.com/Tracers-Dark-G…

Notably, they didn't end up finding the 20-something year old kid living in SF until late-2013.
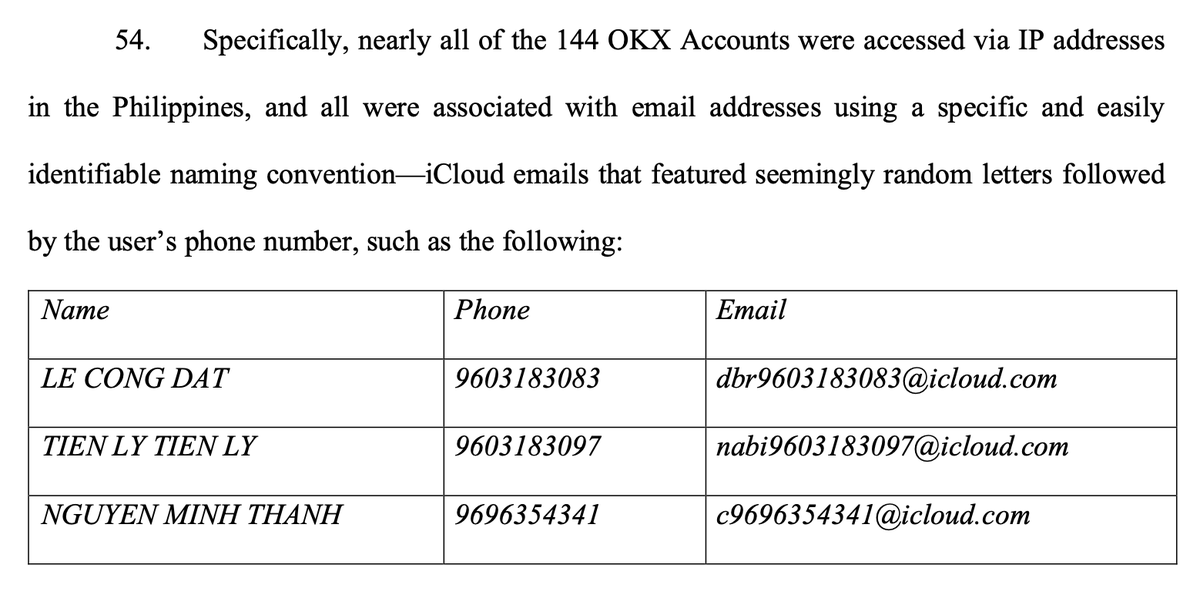
2+ full years later.
He was in SF.
😐
And remember how I told you earlier that James hacked the Silk Road in late-2012 via a super basic race condition?
2+ full years later.
He was in SF.
😐
https://twitter.com/EileenOrmsby/status/385537258939748352
And remember how I told you earlier that James hacked the Silk Road in late-2012 via a super basic race condition?
Silk Road was also hacked in *early*-2012 by a still unidentified " Individual X " using the exact same method. (That ~$1 billion worth of BTC was similarly seized in November 2020.)
news.bitcoin.com/a-look-at-indi…

news.bitcoin.com/a-look-at-indi…


There were a ton of incidents like this. Silk Road was not a state-of-the-art platform. It was basically duct-taped together.
How tf did it take so long for the govt to actually track down the servers and identity of Ross and other admins??????
antilop.cc/sr/#timeline
How tf did it take so long for the govt to actually track down the servers and identity of Ross and other admins??????
antilop.cc/sr/#timeline

Oh right, they were too busy being corrupt as all fuck.
e.g. In Jan 2013 the dedicated Silk Road unit did a sting on one of the mods of SR.
Then they took over his account and......stole all the BTC they could from Silk Road users and vendors. 😬
arstechnica.com/tech-policy/20…
e.g. In Jan 2013 the dedicated Silk Road unit did a sting on one of the mods of SR.
Then they took over his account and......stole all the BTC they could from Silk Road users and vendors. 😬
arstechnica.com/tech-policy/20…
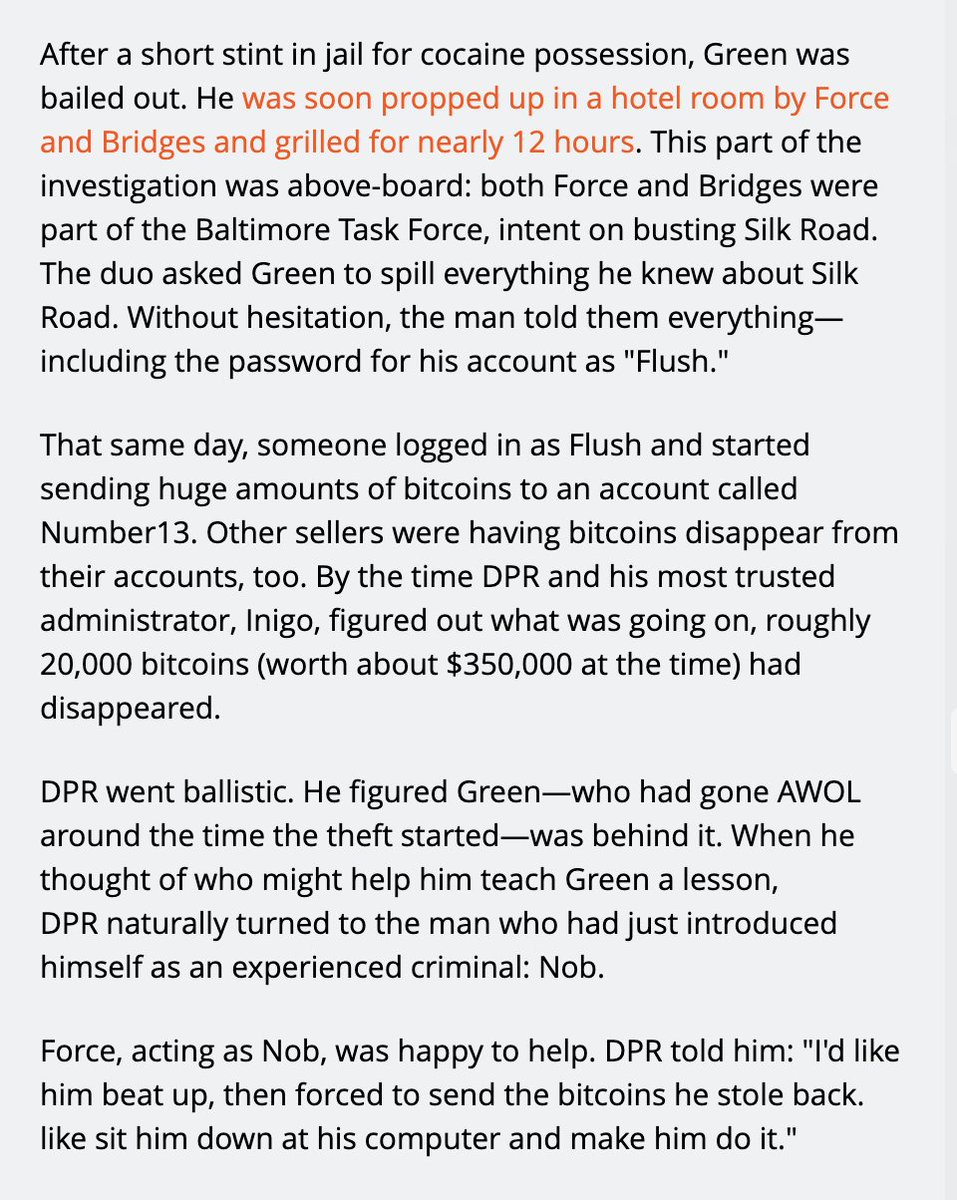
This isnt a conspiracy theory. These feds—Shaun Bridges and Carl Mark Force IV—were both busted after Katie Haun (then prosecutor @ NDCA) + Tigran Gambaryan (then investigator @ IRS-CI) got a tip from....Bitstamp. 🤡
arstechnica.com/tech-policy/20…
@a_greenberg amazon.com/Tracers-Dark-G…



arstechnica.com/tech-policy/20…
@a_greenberg amazon.com/Tracers-Dark-G…




The depth of fraud is really something else. The various filings are worth reading in full. These guys—who were not working together—were so fucking independently disgustingly dirty.
e.g. Corrupt US Secret Service Agent Bridges:
antilop.cc/sr/files/2015_…
+
s3.documentcloud.org/documents/2642…

e.g. Corrupt US Secret Service Agent Bridges:
antilop.cc/sr/files/2015_…
+
s3.documentcloud.org/documents/2642…


And corrupt DEA agent Carl Force
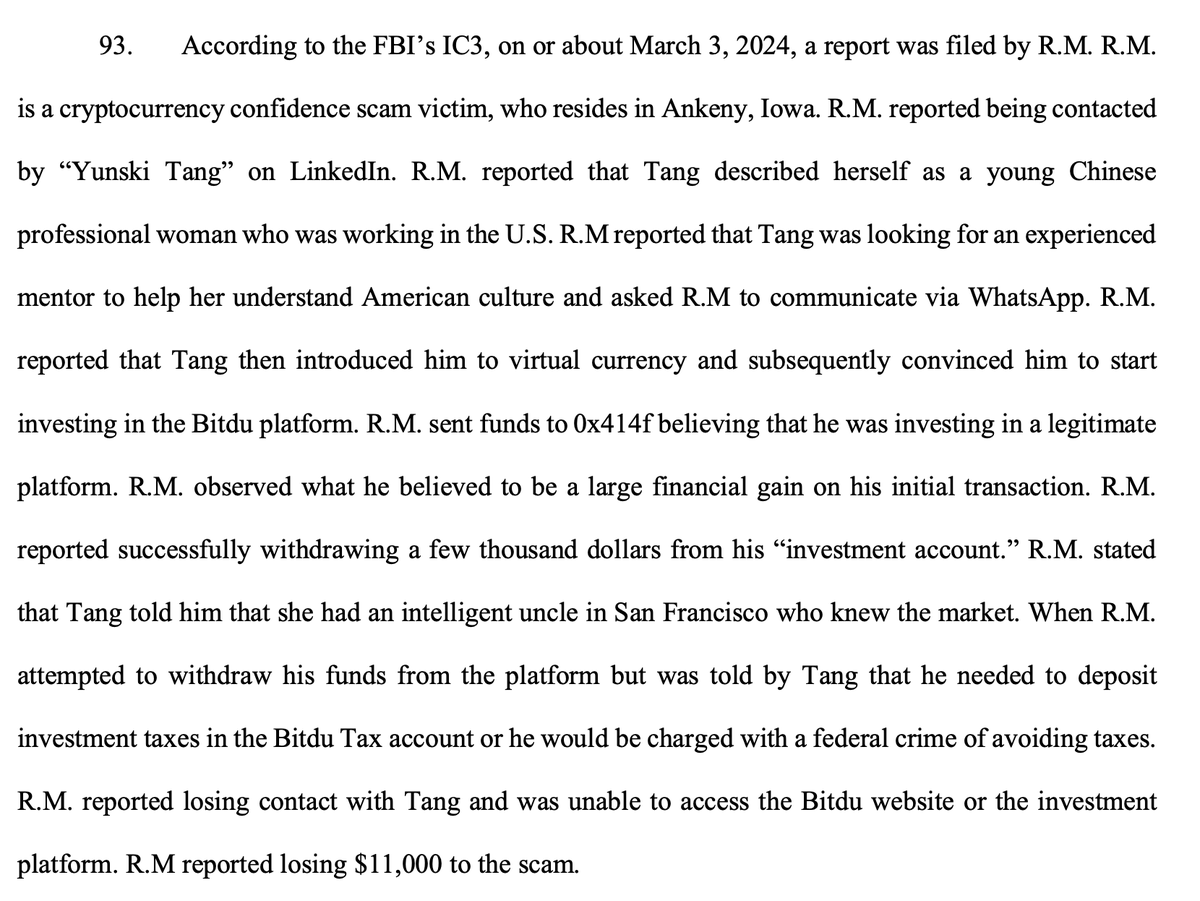
Extortion, theft, lies, and then more thefts.
antilop.cc/sr/files/2015_…
arstechnica.com/tech-policy/20…

Extortion, theft, lies, and then more thefts.
antilop.cc/sr/files/2015_…
arstechnica.com/tech-policy/20…


And even more theft, more lies, more fraud, more extortion by Corrupt DEA agent Carl Force
antilop.cc/sr/files/2015_…
+
antilop.cc/sr/files/2015_…

antilop.cc/sr/files/2015_…
+
antilop.cc/sr/files/2015_…


And Corrupt Bro #1, Bridges, *after* being arrested and pleading, RE-STOLE THE FUNDS THAT HAD TECHNICALLY (but not literally) SEIZED **TWICE** by then.
And then tried to run!!!
Cannot make this shit up. 🤣
Arrest #2:
antilop.cc/sr/files/2016_…
+
antilop.cc/sr/files/2016_…


And then tried to run!!!
Cannot make this shit up. 🤣
Arrest #2:
antilop.cc/sr/files/2016_…
+
antilop.cc/sr/files/2016_…



Anyways.
Obvs these 2 lying, murder-plotting, bitcoin-stealing and re-stealing asswipes were both eventually thrown in prison.
Carl Force got 78 months in October 2015.
oig.justice.gov/press/2015/201…
Shaun Bridges got 71+24 months consecutive in November 2017.
justice.gov/opa/pr/former-…
Obvs these 2 lying, murder-plotting, bitcoin-stealing and re-stealing asswipes were both eventually thrown in prison.
Carl Force got 78 months in October 2015.
oig.justice.gov/press/2015/201…
Shaun Bridges got 71+24 months consecutive in November 2017.
justice.gov/opa/pr/former-…

And then they were released from prison. Bc they are not evil like Ross Ulbricht is. Or something. 😒
Name: CARL MARK FORCE
Register Number: 58633-037
Released On: 10/09/2020
Name: SHAUN W BRIDGES
Register Number: 20436-111
Released On: 10/19/2021
bop.gov/mobile/find_in…
Name: CARL MARK FORCE
Register Number: 58633-037
Released On: 10/09/2020
Name: SHAUN W BRIDGES
Register Number: 20436-111
Released On: 10/19/2021
bop.gov/mobile/find_in…
Sidenote: It is truly appalling that Ross got the literal book thrown at him, will never be released, and these guys got half a slap on the wrist.
Especially considering not one word of this corrupt shitshow was allowed in Ross's trial. 😨 #freeross


Especially considering not one word of this corrupt shitshow was allowed in Ross's trial. 😨 #freeross



And that's the story of how the govt came to be in a position to dump piles of BTC via Coinbase today.
They knew there was unaccounted for BTC that had been stolen from SR.
They knew who stole repeatedly from SR before.
And those agents were about to be released.
🤡
They knew there was unaccounted for BTC that had been stolen from SR.
They knew who stole repeatedly from SR before.
And those agents were about to be released.
🤡
But more importantly, its why the small handful of folks in the govt who actually know Bitcoin—the same ones who took down the corrupt agents, Alpha Bay, BTC-E, Welcome 2 Video, etc.—went from working those cases to working random, long-forgotten-about Silk Road hacks and stuff. 

• • •
Missing some Tweet in this thread? You can try to
force a refresh