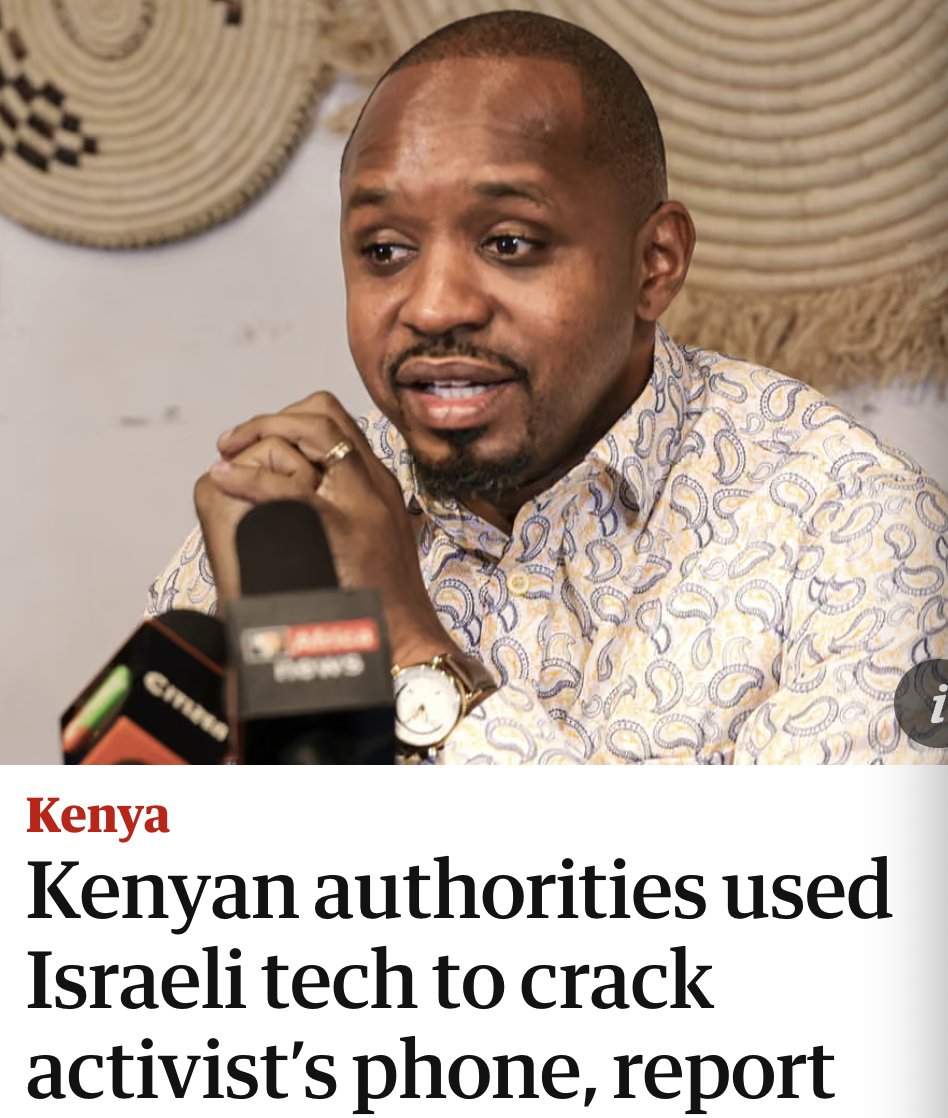
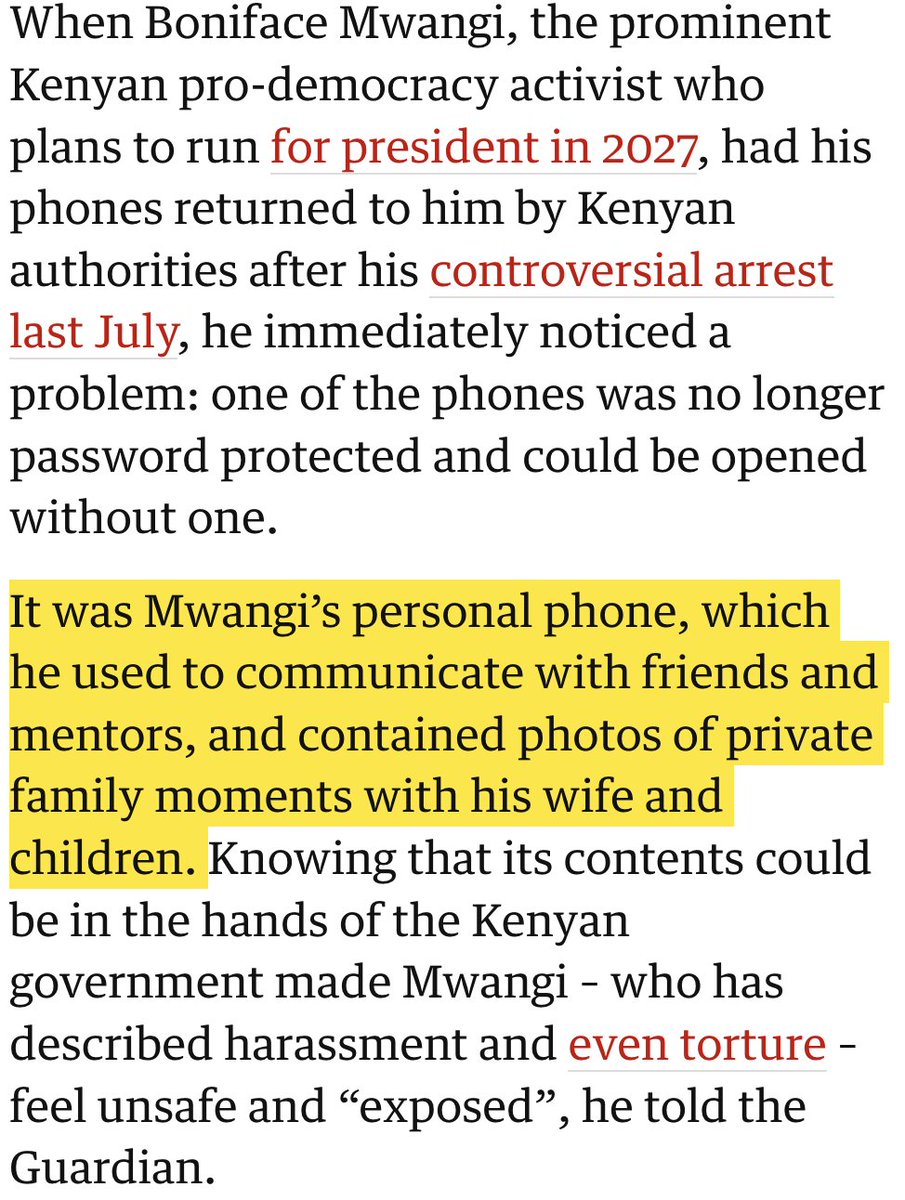
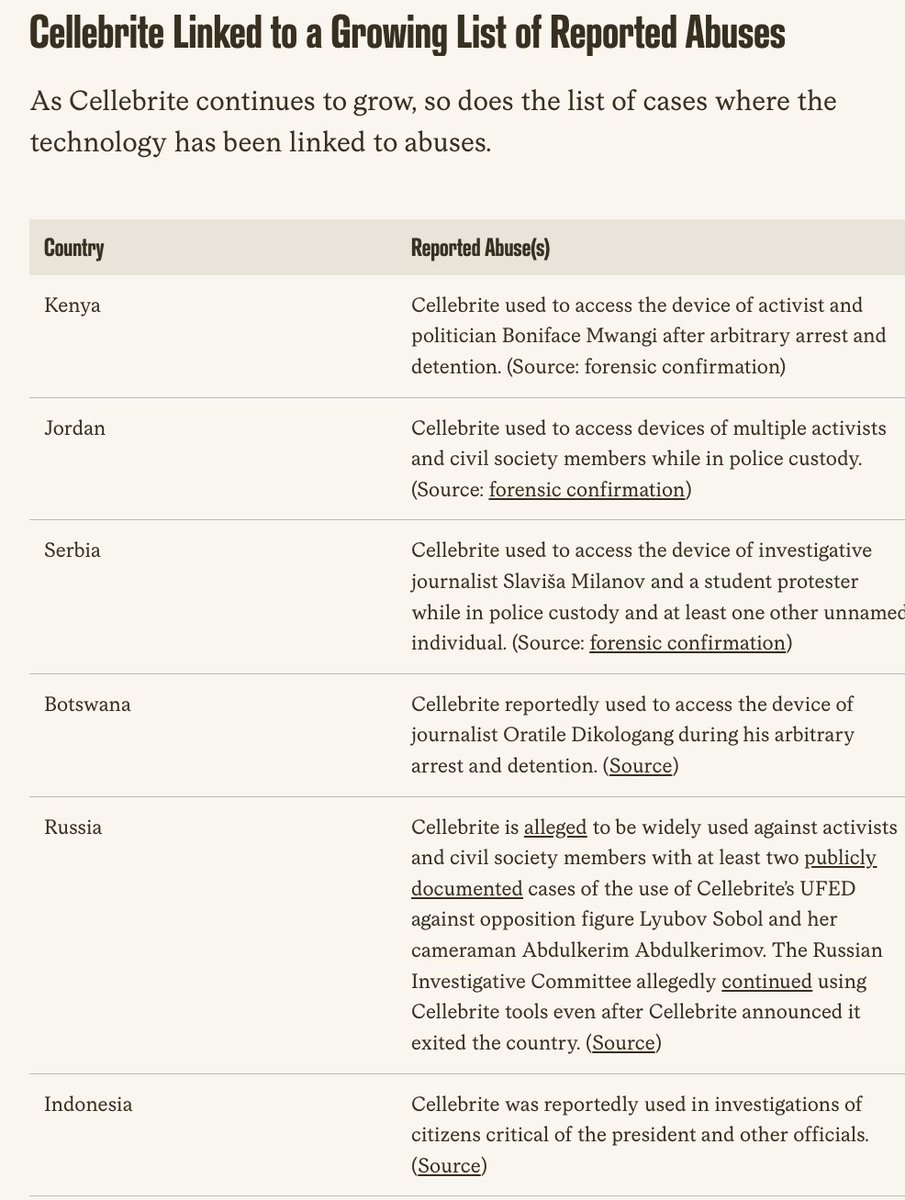
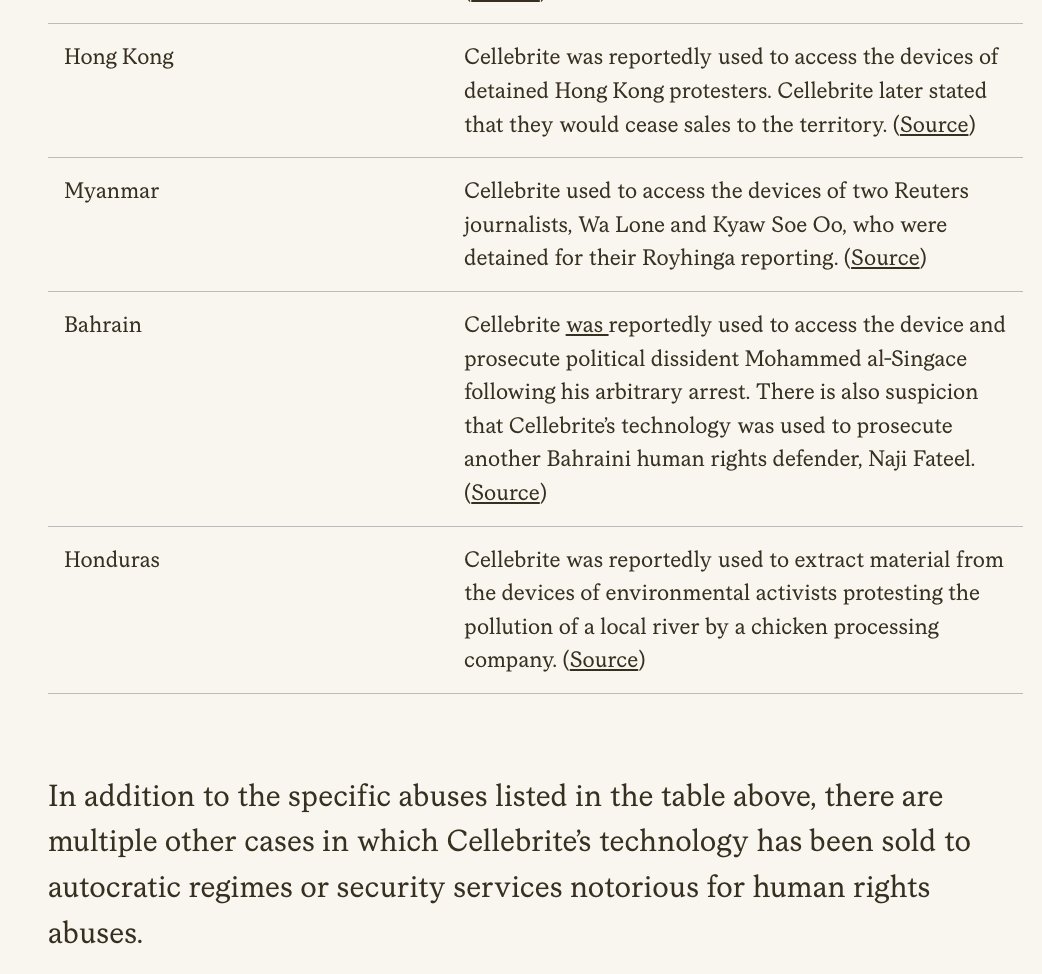
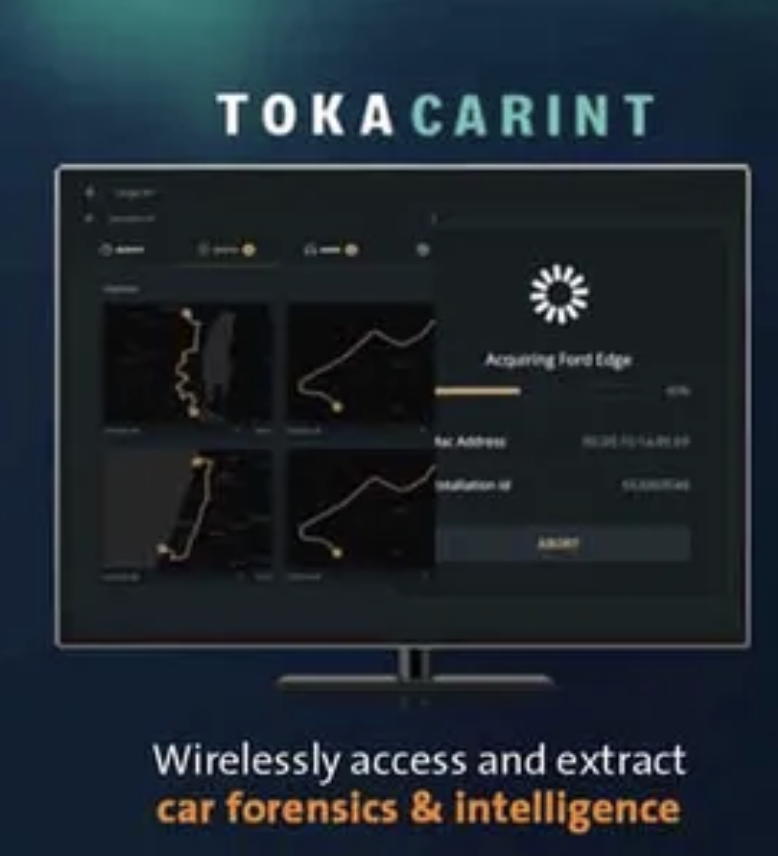
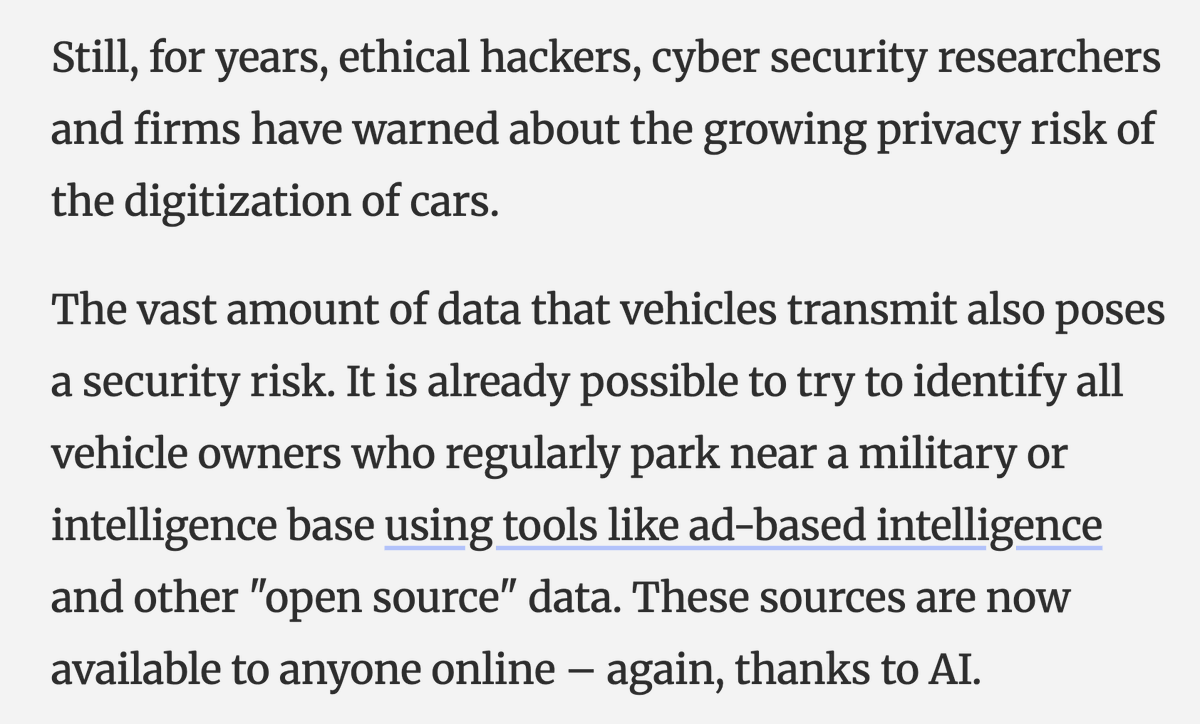
Want a window into Twitter's totally unsolved bot problem?
Search for "as an AI language model"
h/t @lcamtuf



Search for "as an AI language model"
h/t @lcamtuf




Using the "as an AI language model" search term it takes moments to spot repeat themes.
Hate speech.
Nationalism.
Religion.
Sexual content.
Efforts to artificially boost specific topics.
Hate speech.
Nationalism.
Religion.
Sexual content.
Efforts to artificially boost specific topics.
The wave of "as an AI language model" accounts are stupidly unsophisticated.
But legion.
So ask yourself: how likely is it that #Twitter is catching the more sophisticated entities doing AI based replies & content?
And manipulating the conversation.
But legion.
So ask yourself: how likely is it that #Twitter is catching the more sophisticated entities doing AI based replies & content?
And manipulating the conversation.

Finding bots tweeting & replying with AI right now is like shooting fish in a barrel.
Here are some more search terms:
"not a recognized word"
"cannot provide a phrase"
"with the given words"
"violates OpenAI's content policy."
There are many, many more.



Here are some more search terms:
"not a recognized word"
"cannot provide a phrase"
"with the given words"
"violates OpenAI's content policy."
There are many, many more.




Hard problem to reliably find text generated by an #LLM w/out false positives.
But what these accounts show is something different:
A glimpse of Twitter's overburden of bot accounts as operators experiment & make errors trying to integrate #ChatGPT & other AI.
But what these accounts show is something different:
A glimpse of Twitter's overburden of bot accounts as operators experiment & make errors trying to integrate #ChatGPT & other AI.

• • •
Missing some Tweet in this thread? You can try to
force a refresh