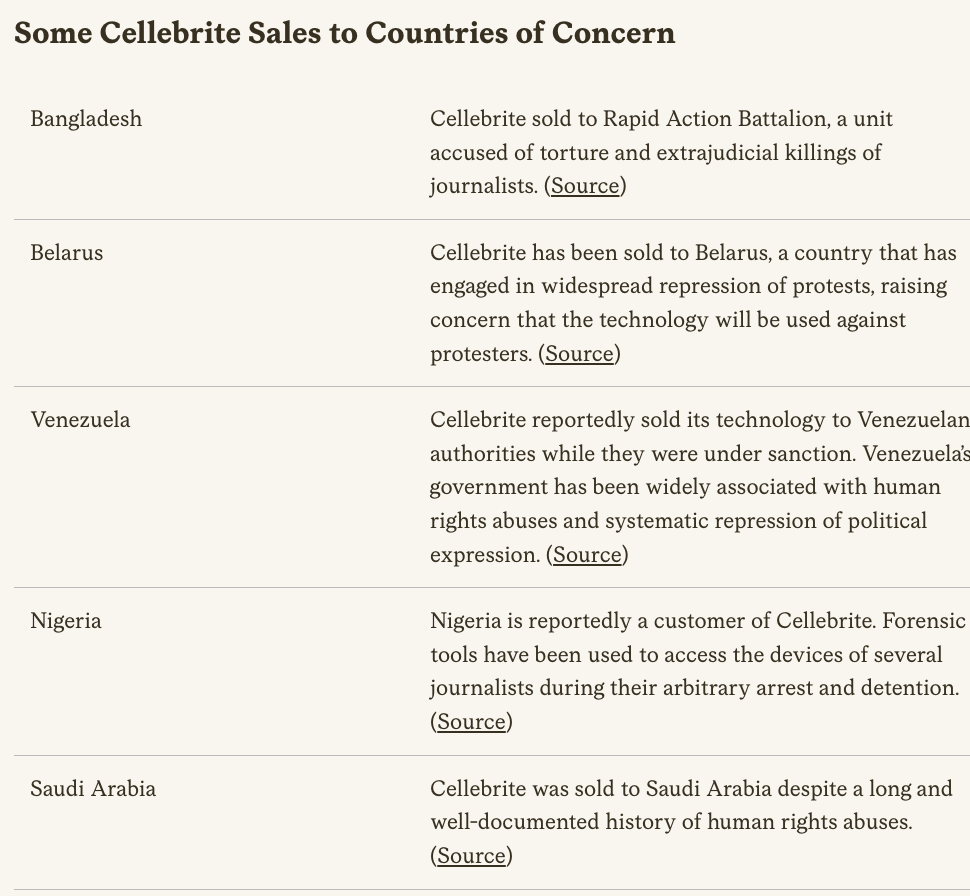
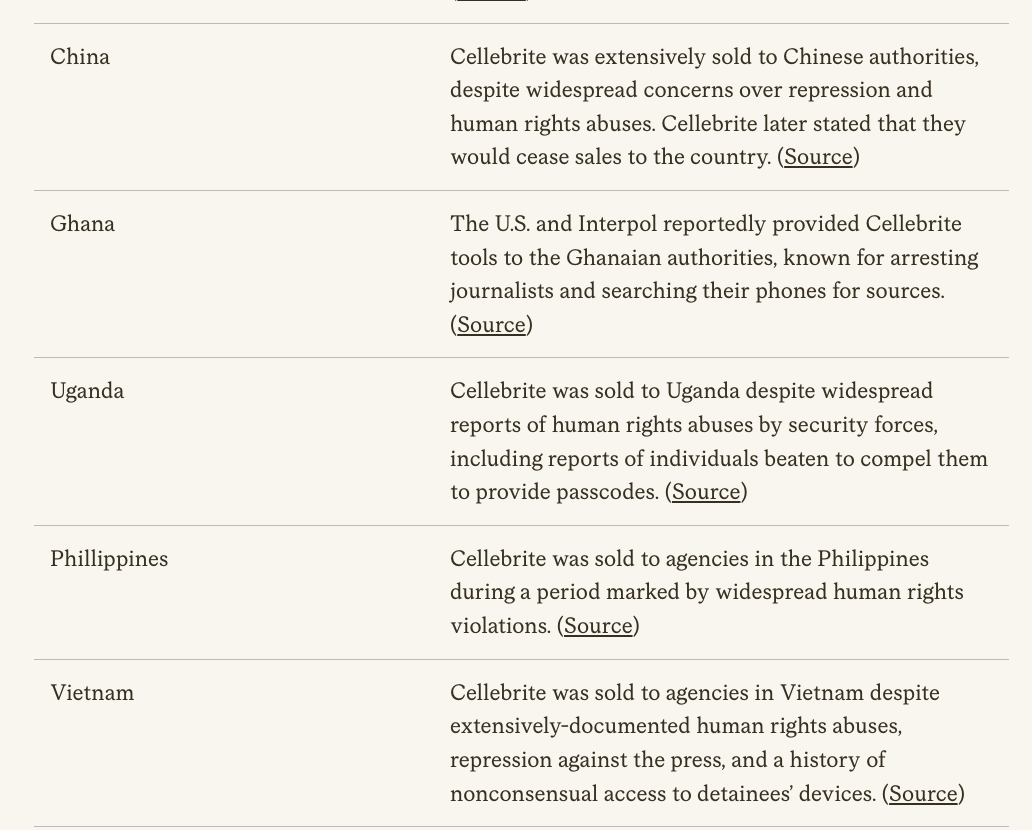
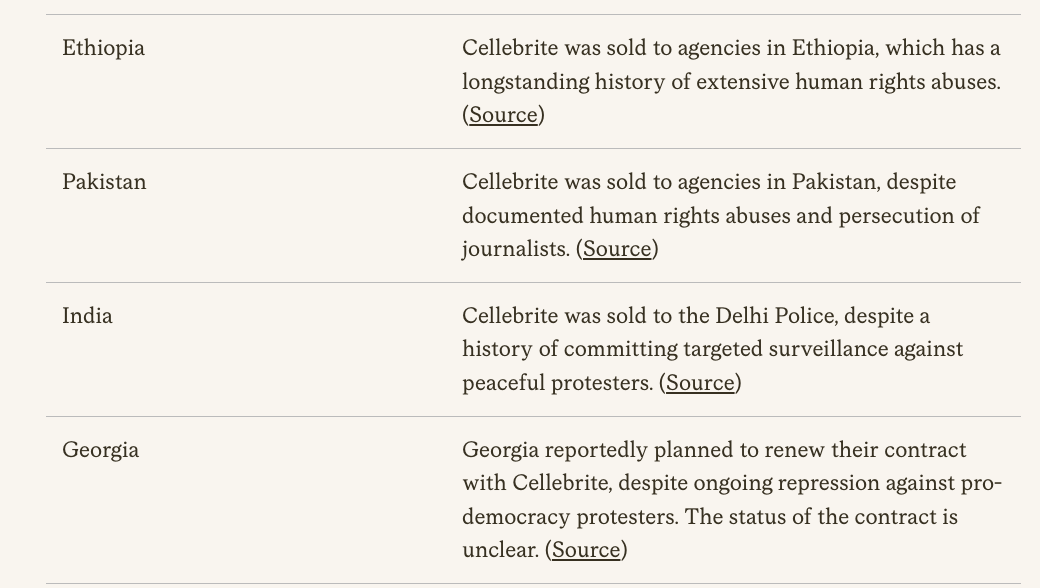
Not to mention the Emergency Management Agencies.
The sheer recklessness of what Musk has done boggles my mind.
The sheer recklessness of what Musk has done boggles my mind.

For every sector of officialdom, from federal all the way to towns Musk made a mess.
Replicated in every country around the world.
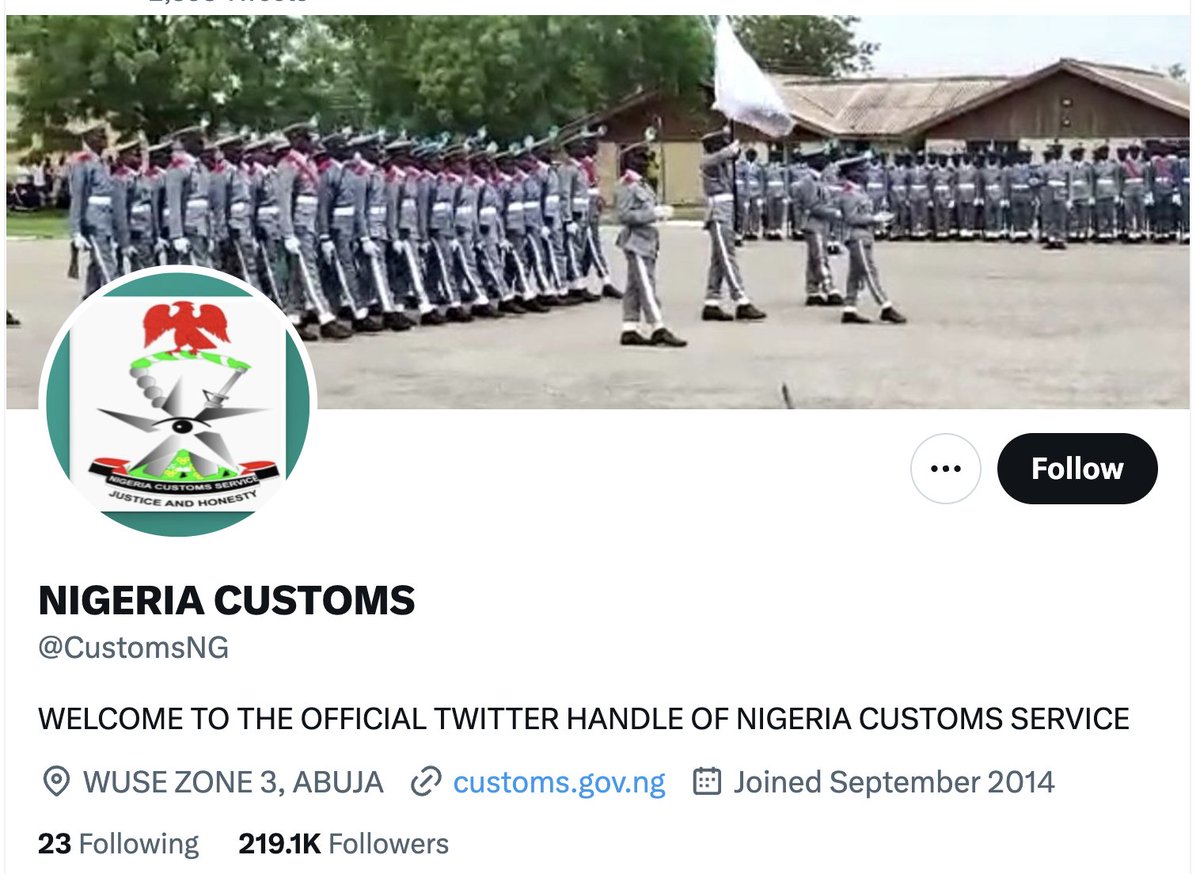
I'm picking national customs services at random to make the point.



Replicated in every country around the world.
I'm picking national customs services at random to make the point.



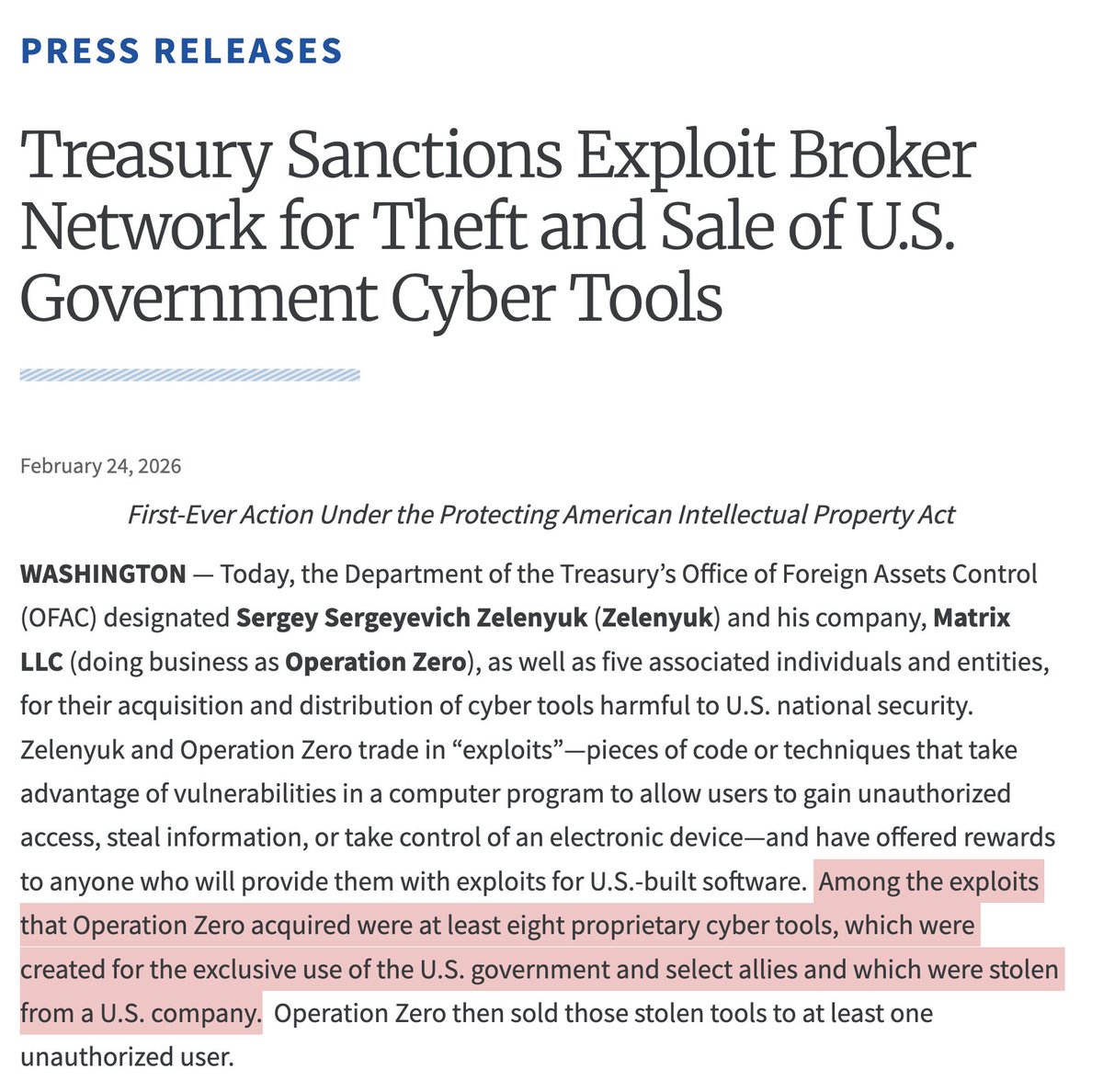
Richest man in the world: I'll create chaos.
Then they'll have to pay me.
Then they'll have to pay me.
US public safety agencies are all over the map,
A good # of the biggest federal ones have a grey badge.
But the lower you go into regional offices, state & local, the worse it looks.
And situation is even more dire internationally.

A good # of the biggest federal ones have a grey badge.
But the lower you go into regional offices, state & local, the worse it looks.
And situation is even more dire internationally.


Rich villain sowing global chaos to make everyone give them $$$ is the evil-scheme-that-always-splutters in so many great movies.
Because the near universal audience reaction is to want it to fail.
Epically.
Because the near universal audience reaction is to want it to fail.
Epically.
Given the scale of official accounts around the world stripped of verification today.
And those of elected & appointed officials.
And counting twitter's slashed global workforce.
It's safe to say that this totally avoidable chaos will be with us for a long time.
And those of elected & appointed officials.
And counting twitter's slashed global workforce.
It's safe to say that this totally avoidable chaos will be with us for a long time.
Ugh, the State Department's tipline, too.
Which offers rewards for tips about terror groups targeting the USA.
The stakes are not a joke.
Which offers rewards for tips about terror groups targeting the USA.
The stakes are not a joke.

Presidential administrations got stripped of verification too.
So did whole govs.
I picked Africa, and it was true for just about every country I checked.
Twitter's only effort seems to have been to grey badge heads of state.
That's it.
Like a sloppy highschool effort.



So did whole govs.
I picked Africa, and it was true for just about every country I checked.
Twitter's only effort seems to have been to grey badge heads of state.
That's it.
Like a sloppy highschool effort.




Got visa issues? Need to contact an embassy ?
Let's look just at embassies in the US.
Sure enough, stripped.
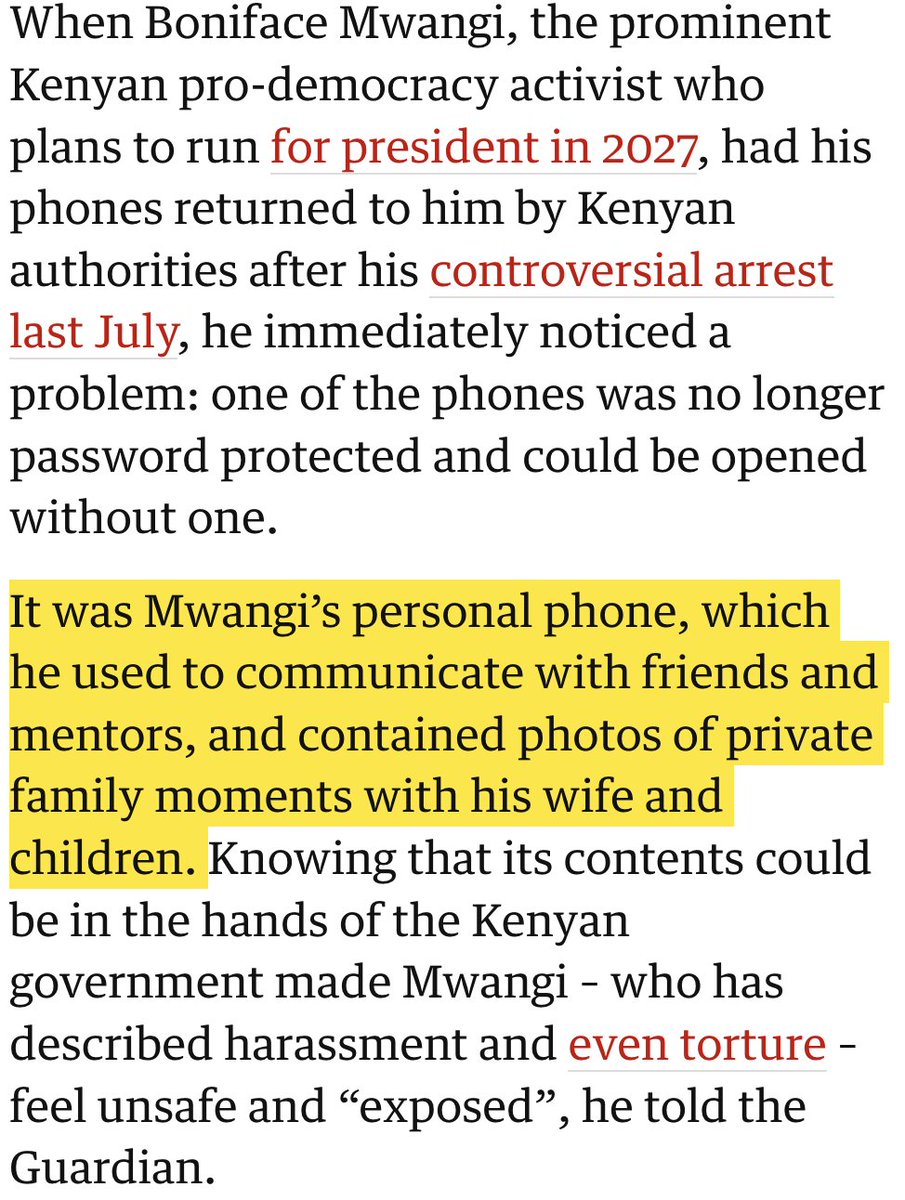
From Sweden to Kenya, Kazakhstan to Bahrain...
Good luck figuring out what's real.



Let's look just at embassies in the US.
Sure enough, stripped.
From Sweden to Kenya, Kazakhstan to Bahrain...
Good luck figuring out what's real.




Oh and how about Musk's other favorite thing?
Of the top 10 space agencies in the world, only @NASA is verified.
I checked.
Everybody else got stripped.



Of the top 10 space agencies in the world, only @NASA is verified.
I checked.
Everybody else got stripped.




One thing I'm confident about.
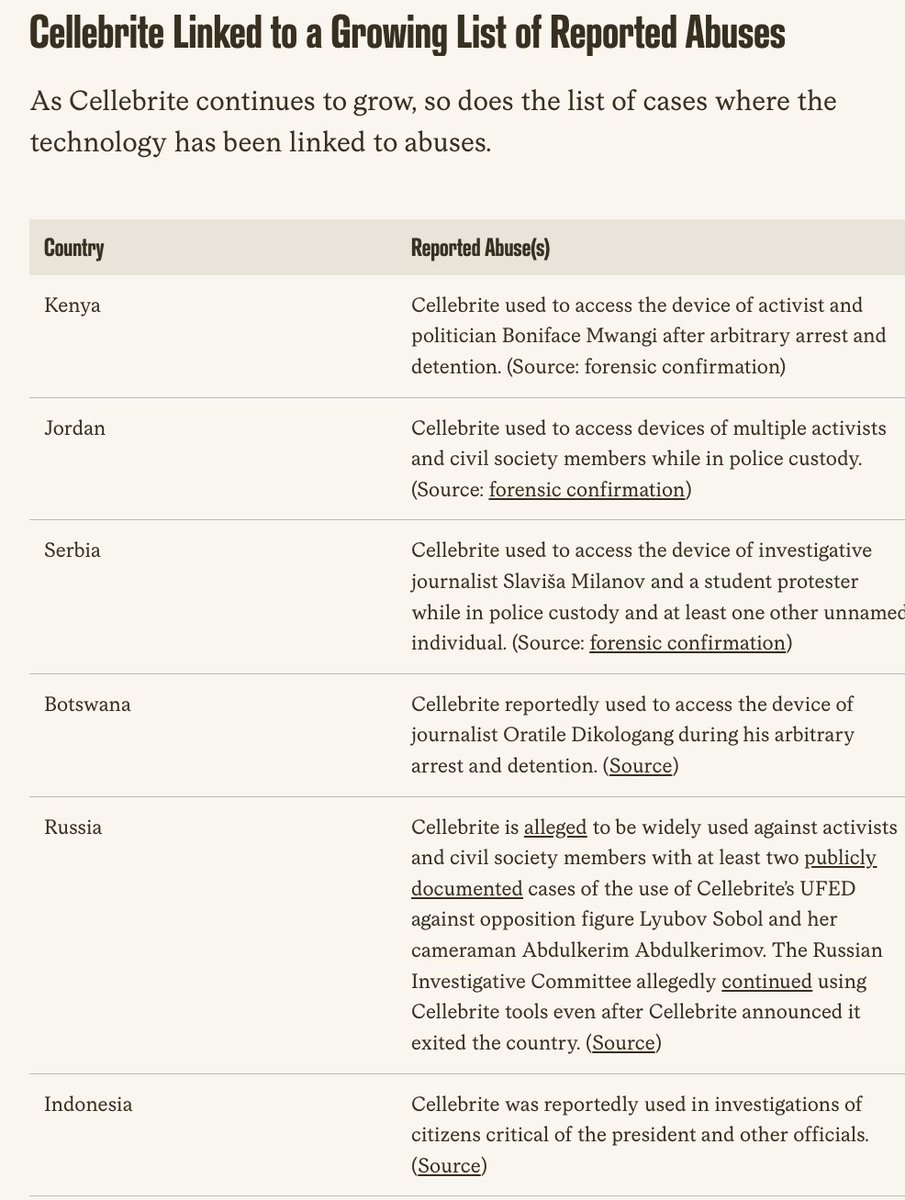
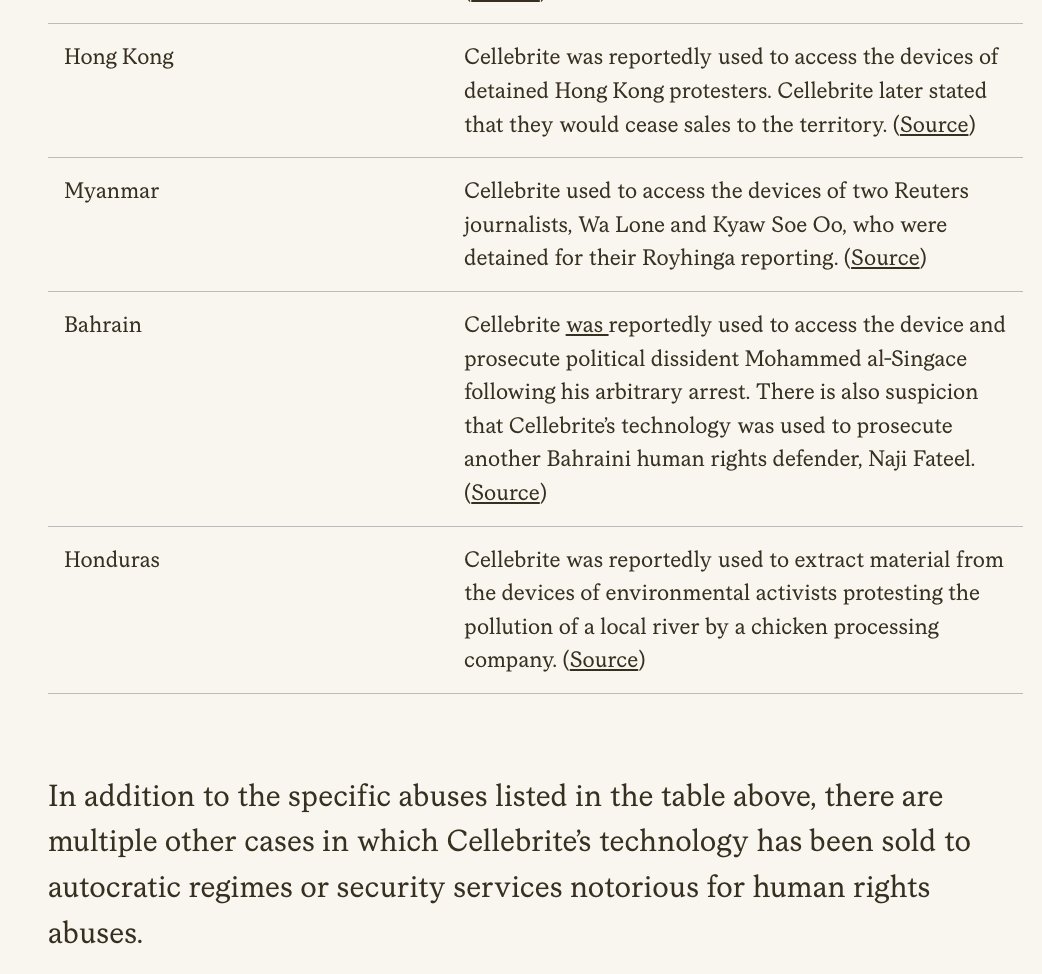
From scammers to coup plotters, terror groups to village trolls: today a lot of people are pondering if/how they might leverage Musk's nearly clean global sweep of verification of governments, agencies, militaries, etc.
From scammers to coup plotters, terror groups to village trolls: today a lot of people are pondering if/how they might leverage Musk's nearly clean global sweep of verification of governments, agencies, militaries, etc.
Musk just made a crystal clear case to governments & businesses that they should rethink whether & how much they use #twitter for official comms.
And instantly showed *everybody* that Twitter isn't the same place to find instantly-verified official statements that it once was.
And instantly showed *everybody* that Twitter isn't the same place to find instantly-verified official statements that it once was.
There are self owns.
And then there's whatever rapid unforced value destruction this is.
And then there's whatever rapid unforced value destruction this is.
But wait, there's more.
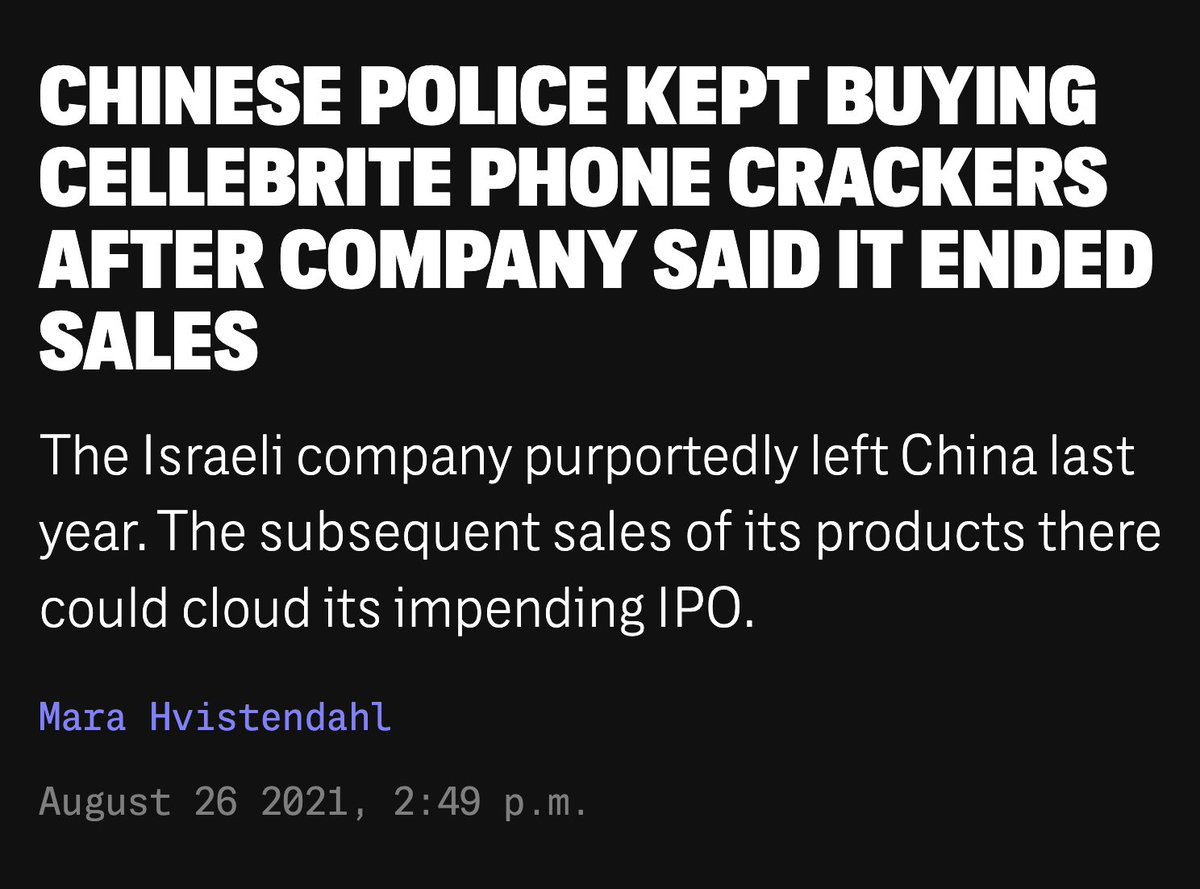
Twitter deleted "state-affiliated media" labels.
I'm sure Russia, China & Iran are tickled.



Twitter deleted "state-affiliated media" labels.
I'm sure Russia, China & Iran are tickled.




As we all know, fake lookalike accounts aren't new.
And even *when* official accounts had verification, you could find people mistakenly engaging the fake ones.
Here's an example.
Think of how much this problem is about to grow.
And even *when* official accounts had verification, you could find people mistakenly engaging the fake ones.
Here's an example.
Think of how much this problem is about to grow.
https://twitter.com/jsrailton/status/1649440909501648897
• • •
Missing some Tweet in this thread? You can try to
force a refresh