🧵NEW THREAD🧵
Here is how I was able to takeover the whole company's AWS infrastructure under 10 min after a new asset launch at @Hacker0x01 private program

Here is how I was able to takeover the whole company's AWS infrastructure under 10 min after a new asset launch at @Hacker0x01 private program
1. I was invited in the morning to a private program at H1 and the program updated the scope in the evening, So I decided to take a look to see if there is something to hack
2. I visited the main website in scope, to my surprise and thanks to @trufflesec Chrome extension Trufflehog which could be found here chrome.google.com/webstore/detai…
This extension is mandatory for every bug hunter, pentester .. , it works in the background and scans every JS file for every website you visit and alert you if there are any found credentials-- checkout more info at their website github.com/trufflesecurit… ...
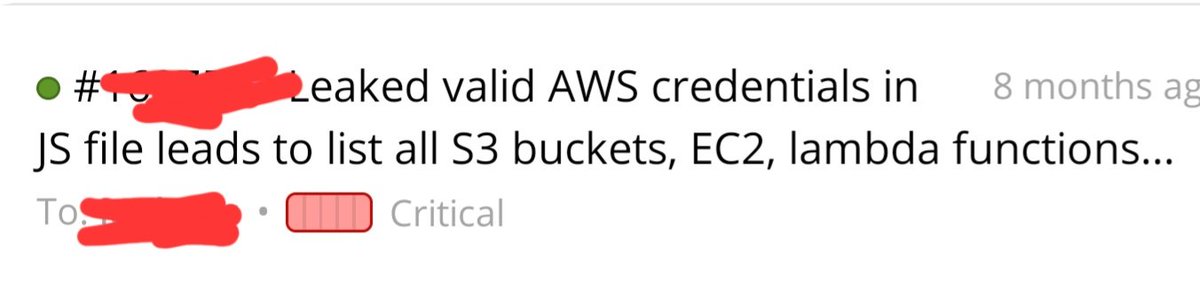
3. I got the popup that contains the AWS access and secret keys, and then used enumerate-iam.py found here github.com/andresriancho/… which will gives me all privileges related to the keys I found
4. The found keys have limited privileges such listing S3 buckets and lambda functions
5. I listed the lambda functions and while i was scrolling my terminal, I found another AWS keys that were used as Variable env creds
6. I then used enumerate-iam.py again, and this was the jackpot! The keys found have root privilege against the AWS account of the company running the BB program
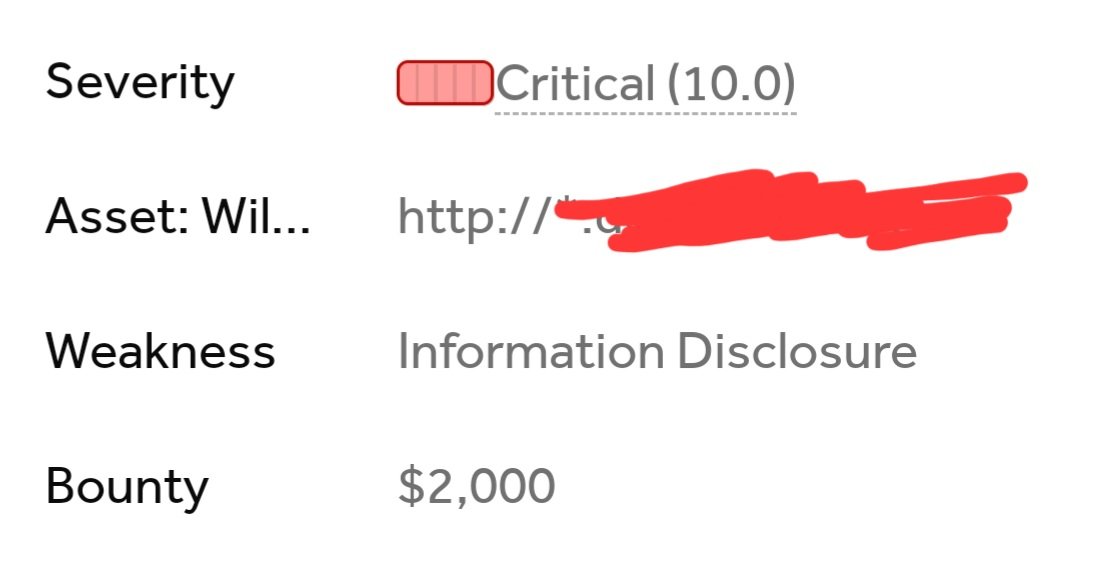
7. I added this finding as a comment to my first report and then in the same day my report was triaged and paid with $2000 as a maximum payout for a Critical finding in the program
Note: Install the Trufflehog browser extension that will helps you automatically scan an JS file even if your are not in the hacking mood!
Also read JS files manually if you are not willing to install the extension, because developers sometimes forget their variable env in JS...
Also read JS files manually if you are not willing to install the extension, because developers sometimes forget their variable env in JS...
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter









