
🔎 @mapperplus
🥷 Cyber Security Engineer - Penetration Tester
🔴 Synack Red Team Member
💻 Coding enthusiast
...
---------------
OSCP-CRTO
How to get URL link on X (Twitter) App

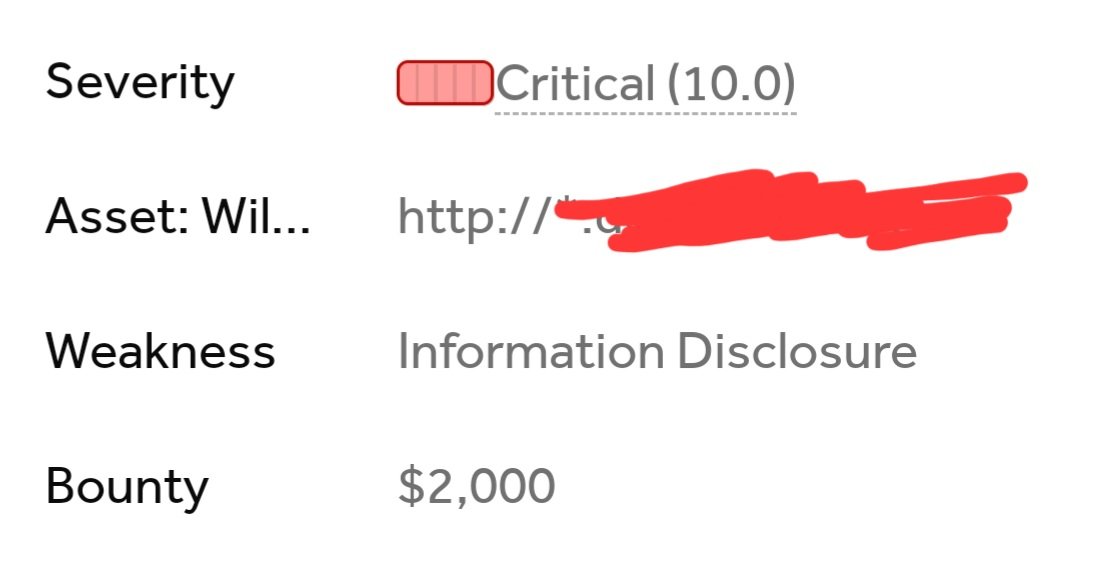

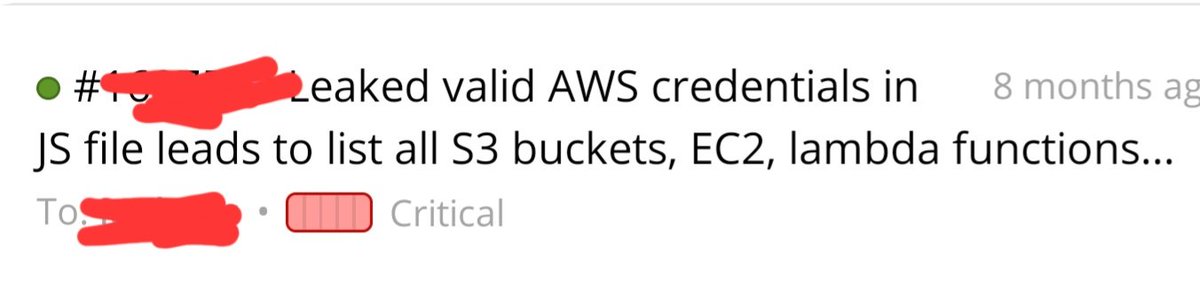 1. I was invited in the morning to a private program at H1 and the program updated the scope in the evening, So I decided to take a look to see if there is something to hack
1. I was invited in the morning to a private program at H1 and the program updated the scope in the evening, So I decided to take a look to see if there is something to hack


 2. Found that the program accepts all vulnerabilities related to their assets and of course third party assets are OOS
2. Found that the program accepts all vulnerabilities related to their assets and of course third party assets are OOS


 The second one is from the JS files.
The second one is from the JS files.

 3. I tried to find the executable for the In scope app just to understand what the app will looks like when installed in the machine
3. I tried to find the executable for the In scope app just to understand what the app will looks like when installed in the machine