1/ 🚨 A recent surge in phishing scams via Google search ads has led to users losing approximately $4 million.
ScamSniffer has investigated multiple cases where users clicked on malicious ads and were directed to fraudulent websites.
#PhishingScams #GoogleAds
ScamSniffer has investigated multiple cases where users clicked on malicious ads and were directed to fraudulent websites.
#PhishingScams #GoogleAds
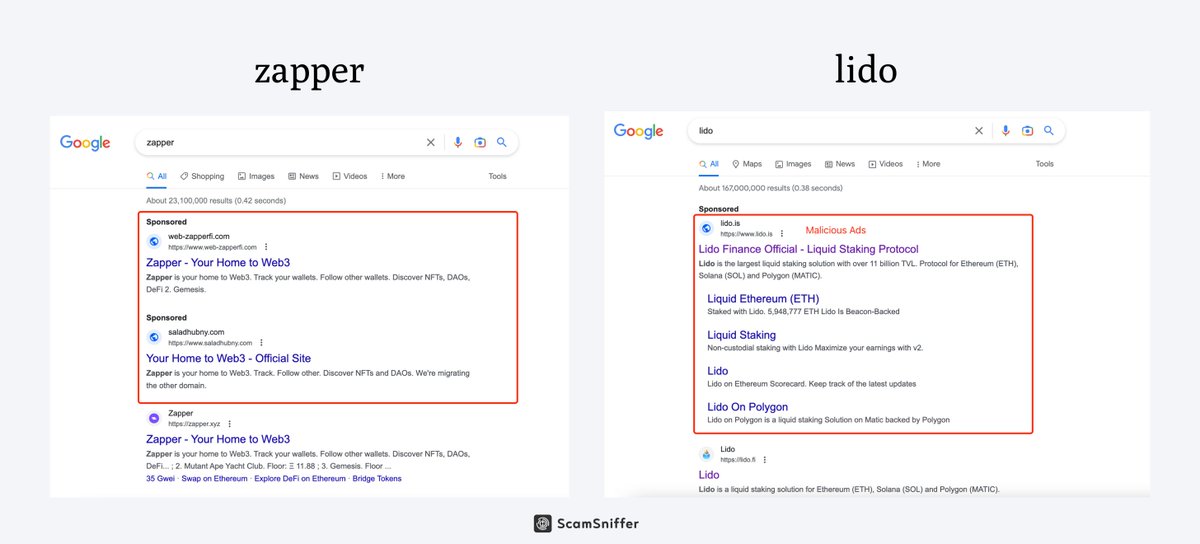
2/ 🕵️♂️ Investigation into the keywords used by victims has uncovered numerous malicious ads at the forefront of search results.
Most users, unaware of the deceptive nature of search ads, click on the first available option, leading them to malicious websites.
#Cybersecurity
Most users, unaware of the deceptive nature of search ads, click on the first available option, leading them to malicious websites.
#Cybersecurity

3/ 🎯 Some of the malicious ads and websites target brands such as @zapper_fi , @LidoFinance , @StargateFinance and @DefiLlama.
These advertisers have been identified as placing these malicious ads:
ТОВАРИСТВО З ОБМЕЖЕНОЮ ВІДПОВІДАЛЬНІСТЮ «РОМУС-ПОЛІГРАФ»
TRACY ANN MCLEISH.

These advertisers have been identified as placing these malicious ads:
ТОВАРИСТВО З ОБМЕЖЕНОЮ ВІДПОВІДАЛЬНІСТЮ «РОМУС-ПОЛІГРАФ»
TRACY ANN MCLEISH.


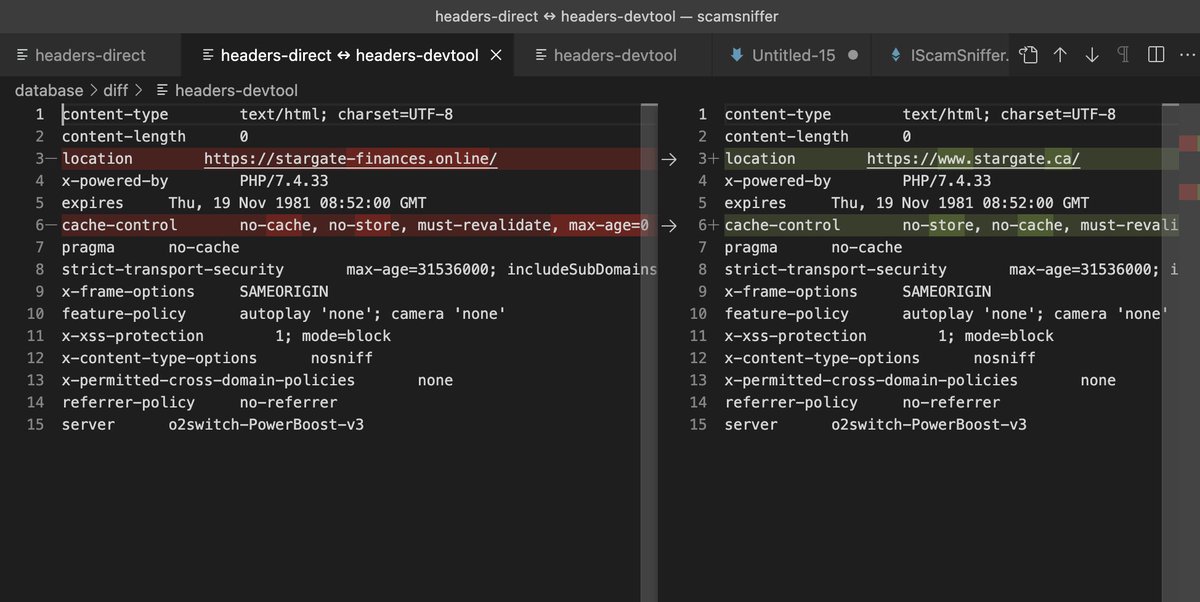
4/ 🛡️ Malicious ads employ several techniques to bypass Google's ad review process, including parameter distinction and debugging prevention.
These tactics allow them to deceive Google's ad review process and cause significant harm to users. #AdReview #Bypass


These tactics allow them to deceive Google's ad review process and cause significant harm to users. #AdReview #Bypass


5/ 🔧 Recommended improvements for @GoogleAds include the integration of a Web3-focused malicious website detection engine (e.g., ScamSniffer) and continuous monitoring of landing pages throughout the ad placement lifecycle.
#GoogleAds #Security
#GoogleAds #Security
6/ 💰 Analysis of on-chain data from addresses associated with the malicious ad websites reveals that approximately $4.16 million has been stolen from around 3,000 victims.
Details: dune.com/scamsniffer/go…
#CryptoTheft #OnChainData
Details: dune.com/scamsniffer/go…
#CryptoTheft #OnChainData

7/ 🌐 By analyzing several larger fund collection addresses, it was found that some funds were deposited into @SimpleSwap_io , Tornado.Cash, @kucoincom , and @BinanceUS. 

8/ 📈 Ad analysis platforms suggest that the average cost per click for these keywords is around $1-$2. Based on an estimated conversion rate of 40% and 7,500 users clicking on the ads, the advertising cost is approximately $15K.
Estimated ROI of about 276%.
#ROI #PhishingScams
Estimated ROI of about 276%.
#ROI #PhishingScams

9/ 🚀 You should exercise caution when using search engines and actively block content in the advertising area.
Furthermore, it's crucial for @GoogleAds to strengthen its review process for Web3 malicious ads to better protect users.
#CybersecurityAwareness #GoogleAdsProtection
Furthermore, it's crucial for @GoogleAds to strengthen its review process for Web3 malicious ads to better protect users.
#CybersecurityAwareness #GoogleAdsProtection
10/ 🙏 Thanks to @IM_23pds from @SlowMist_Team , @tayvano_ , @bax1337 from @convex_labs, @1nf0s3cpt, @zachxbt and @DeFiTeddy2020 for reviewing the data and content!
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter




