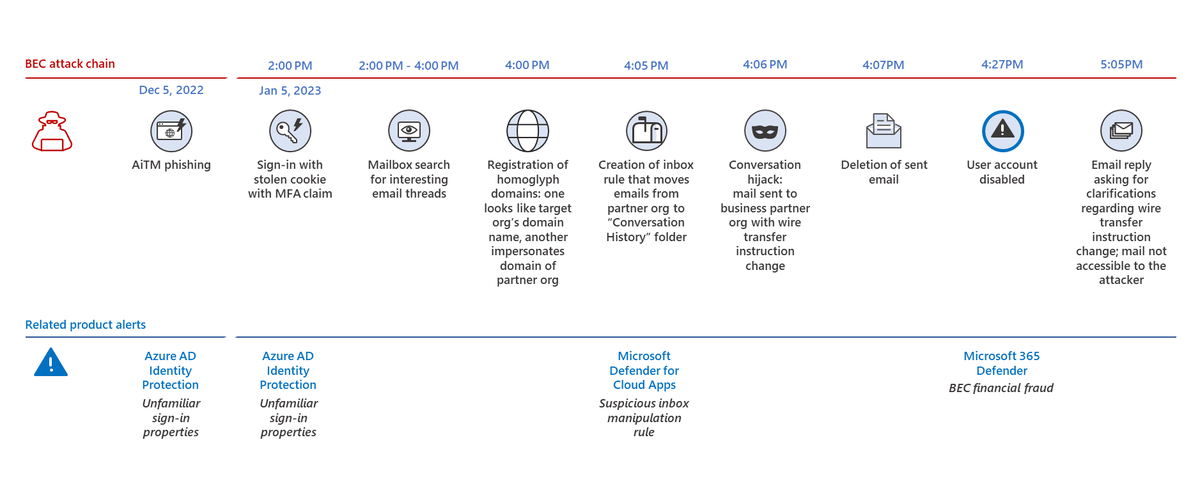
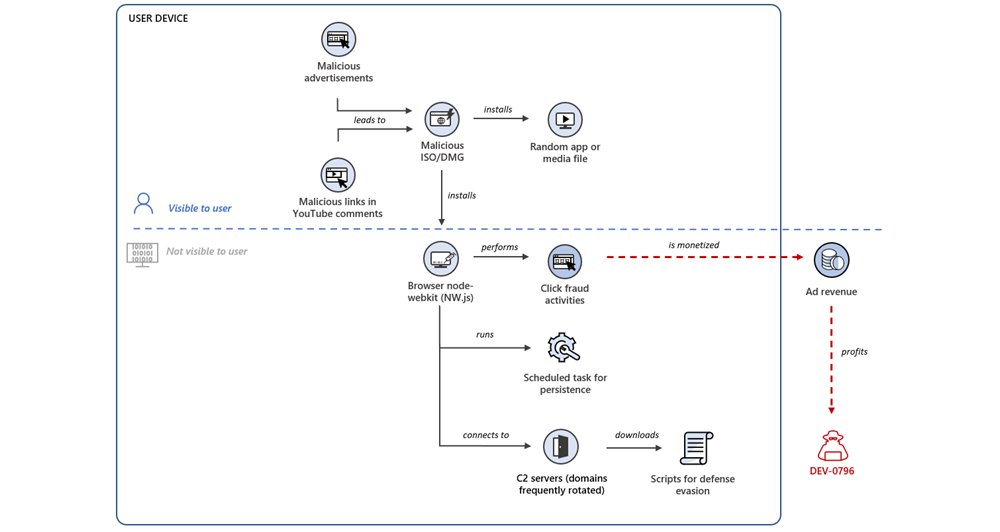
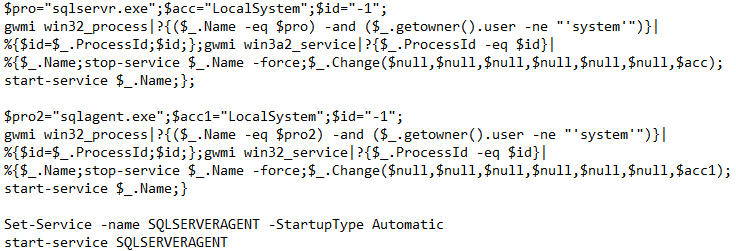
More actors are exploiting unpatched CVE-2023-27350 in print management software Papercut since we last reported on Lace Tempest. Microsoft has now observed Iranian state-sponsored threat actors Mint Sandstorm (PHOSPHORUS) & Mango Sandstorm (MERCURY) exploiting CVE-2023-27350.
After public POCs were published for CVE-2023-27350, Mint Sandstorm & Mango Sandstorm quickly adapted the exploit in their operations to achieve initial access. This activity shows Mint Sandstorm’s continued ability to rapidly incorporate POC exploits into their operations.
The PaperCut exploitation activity by Mint Sandstorm appears opportunistic, affecting organizations across sectors and geographies. We previously reported on other Mint Sandstorm TTPs: microsoft.com/en-us/security…
Observed CVE-2023-27350 exploitation activity by Mango Sandstorm remains low, with operators using tools from prior intrusions to connect to their C2 infrastructure: microsoft.com/en-us/security…
As more threat actors begin to use this vulnerability in their attacks, organizations are strongly urged to prioritize applying the updates provided by PaperCut to reduce their attack surface: msft.it/6018gPn92
Microsoft 365 Defender detects activity related to exploitation of the PaperCut vulnerabilities. Microsoft Defender Threat Intelligence also includes a report with additional details and recommendations to defend against this threat.
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter