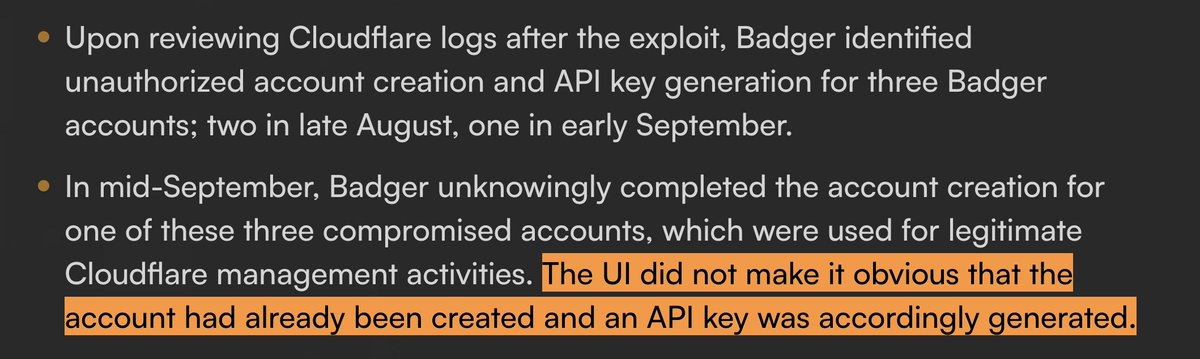
⚠️ Heads up y'all—we're seen a huge increase in the # of ultra-targeted spearphishes lately.
The most deadly one? A Google Doc share that appears to come from *someone you know* about *something you're interested in*
It won’t be flagged and looks super legit.
DO NOT CLICK! 🙏
The most deadly one? A Google Doc share that appears to come from *someone you know* about *something you're interested in*
It won’t be flagged and looks super legit.
DO NOT CLICK! 🙏

This campaign is the work of #Lazarus / #APT38 / #DangerousPassword / #T444
aka the same crew that compromised Ronin, Harmony, bZx, Bondly, EasyFi, mngr, Arthur0x, Hugh Karp, etc. etc. etc.
Their spear-phishing methods are diverse, targetted, and hard-to-detect.
aka the same crew that compromised Ronin, Harmony, bZx, Bondly, EasyFi, mngr, Arthur0x, Hugh Karp, etc. etc. etc.
Their spear-phishing methods are diverse, targetted, and hard-to-detect.

Recent subject lines / filenames:
Fast Changes in NFT Price (Protected)
Investor Demo Day-Animoca Brands (Protected)
Jump Crypto Investment Agreement
New Credit Investment Opportunity
Spirit Blockchain Capital 2023 - Pitch Deck
Opening the file *may* result in something like:


Fast Changes in NFT Price (Protected)
Investor Demo Day-Animoca Brands (Protected)
Jump Crypto Investment Agreement
New Credit Investment Opportunity
Spirit Blockchain Capital 2023 - Pitch Deck
Opening the file *may* result in something like:



If you think you’re too smart to get phished, think again.
They don't spam some airdrop bs, they capitalize on the fact you’re back-to-back all day.
They get you to do what you already do all the time: click a "Google" link from a "colleague."
proofpoint.com/us/blog/threat…
They don't spam some airdrop bs, they capitalize on the fact you’re back-to-back all day.
They get you to do what you already do all the time: click a "Google" link from a "colleague."
proofpoint.com/us/blog/threat…

And if you accidentally give them a sliver of access, they will silently drop malware made just for you.
Mac, Windows, Linux, anti-virus software, malware scans—it doesn't matter.
They have some new-fangled Mac malware written in Rust:
jamf.com/blog/bluenorof…
Mac, Windows, Linux, anti-virus software, malware scans—it doesn't matter.
They have some new-fangled Mac malware written in Rust:
jamf.com/blog/bluenorof…
And here's some of their latest Windows shit. They always seem to be iterating and experimenting in order to evade detection:
securelist.com/bluenoroff-met…
securelist.com/bluenoroff-met…
Think you're safe because you're a hardcore Linux-only person?
lol rip
welivesecurity.com/2023/04/20/lin…
lol rip
welivesecurity.com/2023/04/20/lin…
In the past they've dropped a *custom-built MM🦊* that stole funds from a founder's *secured* hardware wallet.
They literally rewrote chunks of MM in order to hide the theft txn behind the legitimate txn he intended to sign. 😱
securelist.com/the-bluenoroff…
They literally rewrote chunks of MM in order to hide the theft txn behind the legitimate txn he intended to sign. 😱
securelist.com/the-bluenoroff…
Don't get cocky.
I've got countless stories this month from founders and funds seeing these hit their inboxes.
You need to stop clicking links and downloading files—whether they come via email, Telegram, WhatsApp, Linkedin, whatever.

I've got countless stories this month from founders and funds seeing these hit their inboxes.
You need to stop clicking links and downloading files—whether they come via email, Telegram, WhatsApp, Linkedin, whatever.


If you clicked / downloaded anything that looks like the above, you need to sound the alarm *now.*
- Consider your shit completely compromised
- Get help from experts
- Rotate all keys & pws
- Secure any servers, infra, smart contracts you have access/admin to
PLZ STAY SAFE! 💖



- Consider your shit completely compromised
- Get help from experts
- Rotate all keys & pws
- Secure any servers, infra, smart contracts you have access/admin to
PLZ STAY SAFE! 💖




• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter