Another @ethereum #ACDE today! We covered SELFDESTRUCT removal, 4844 spec changes, opcode management and potential final Cancun additions 🏖️
Agenda: github.com/ethereum/pm/is…
Stream:
Recap below 😄
Agenda: github.com/ethereum/pm/is…
Stream:
Recap below 😄
https://twitter.com/TimBeiko/status/1656703312543252481
@ethereum First on the call, we had the @dedaub team share the impact analysis they did around SELFDESTRUCT removal: docs.google.com/document/d/1HD…
Their presentation was thorough and accessible - recommend the livestream if you want to get the full picture 😄
Their presentation was thorough and accessible - recommend the livestream if you want to get the full picture 😄
@ethereum @dedaub At a high level, they were tasked with determining what would break if SELFDESTRUCT semantics changed, and whether trying to accommodate certain breaking cases would be worthwhile. 

@ethereum @dedaub First, they clearly explained how SELFDESTRUCT works today, and then contrasted this with what EIPs 4758 and 6780 propose. 





@ethereum @dedaub TL;DR SELFDESTRUCT currently sends ETH in a contract to the beneficiary address, then clears the runtime bytecode, nonce and storage of the contract where it is called.
@ethereum @dedaub As previously discussed, the problems with this are (1) unbounded execution time (SELFDESTRUCTING a big contract requires much more computation than a small ones (2) the incompatibility with Verkle Tries & stateless and (3) whether we want mutable contracts at all 😅
@ethereum @dedaub EIP-4758 proposes to aggressively remove SELFDESTRUCT, converting it to SENDALL, and having it only send funds back to the beneficiary address, but not clear any bytecode/storage/nonce.
@ethereum @dedaub EIP-6780 does the same, with an exception: contracts which are created and destroyed within a single transaction. This was previously identified as a large usage pattern for the opcode. The Dedaub analysis looked at the "reduced + remaining breakage" from this.
@ethereum @dedaub Assuming we went the more aggressive way of 4758, here's the projects which would be affected. 

@ethereum @dedaub But, if we do 6780, we greatly reduce the impact: we go from 400k transactions over the past 2.5m blocks that would have been impacted to ~700! 

@ethereum @dedaub @willmorriss4 felt the report understated the impact in that last line about MEV bots, and shared a statement about why + how to mitigate it: docs.google.com/document/d/16G…
@ethereum @dedaub @willmorriss4 In short, his proposal is to add another opcode, SETCODE, alongside the removal of SELFDESTRUCT to allow for programmatic accounts to still be updated: 

@ethereum @dedaub @willmorriss4 Yoav Weiss discussed this with him async over the past day, and shared some of his concerns with SETCODE: notes.ethereum.org/@yoav/SETCODE-…
In short, it introduces some new mutability risks related to DELEGATECALL.
In short, it introduces some new mutability risks related to DELEGATECALL.
@ethereum @dedaub @willmorriss4 There were some more questions about SETCODE on the call, and some concerns about the implications of the feature. After some back and forth, client teams agreed to still move forward with EIP-6780, independently of making a decision on SETCODE.
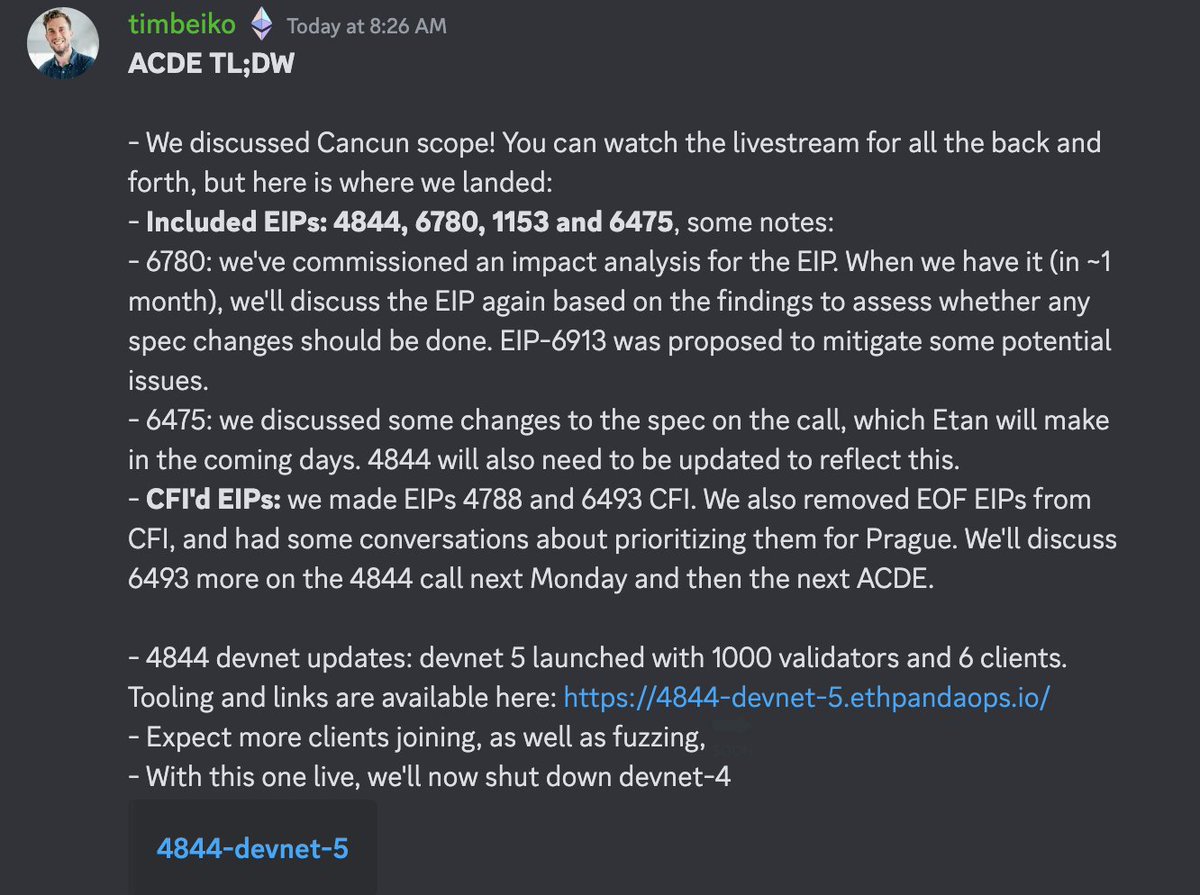
@ethereum @dedaub @willmorriss4 Next up, we discussed EIP-4844! There were a bunch of spec issues on the agenda. I won't go over all of them here - you can watch the livestream for the full overview, or wait for @terencechain's recap of Monday's 4844 call 😄
@ethereum @dedaub @willmorriss4 @terencechain The one we spent the most time on is a proposal from the geth team to change how blob gas usage is tracked: github.com/ethereum/EIPs/…
The PR would align 4844 with 1559 in terms of what information is needed to derive a block's excess_data_gas
The PR would align 4844 with 1559 in terms of what information is needed to derive a block's excess_data_gas

@ethereum @dedaub @willmorriss4 @terencechain Aside from this, we reviewed PRs confirming two changes we had agreed to: moving the precompile to use big endian (like the rest of the EL), and removing SSZ from 4844.
@ethereum @dedaub @willmorriss4 @terencechain The SSZ -> RLP change also implied that the two SSZ EIPs for Cancun are no longer required: EIPs 6475 and 6493 are therefore being respectively removed from the Included & CFI lists
github.com/ethereum/execu…
github.com/ethereum/execu…
@ethereum @dedaub @willmorriss4 @terencechain Then, @BarnabasBusa gave an update on 4844 devnet-5: in the past two weeks, we had a non-finalization event on it which forcefully exited 900 validation. The devnet then finalized, and new validators are being activated. New nodes can sync to it successfully!
@ethereum @dedaub @willmorriss4 @terencechain @BarnabasBusa He also started drafting a spec for devnet 6, which will be the main topic for our 4844 call Monday: notes.ethereum.org/@bbusa/dencun-…
@ethereum @dedaub @willmorriss4 @terencechain @BarnabasBusa With Dencun shaping up, it's likely devnet-6 will be the last 4844-exclusive devnet, and that after that, we'll start pulling in other EIPs to test as well!
@ethereum @dedaub @willmorriss4 @terencechain @BarnabasBusa After this, @shemnon came on to help us try and make sense of all the proposed opcodes for Cancun, Prague and more. He shared this doc which makes suggestions for opcode usage based on a holistic view of all proposed EVM changes: hackmd.io/@shemnon/Cancu…
@ethereum @dedaub @willmorriss4 @terencechain @BarnabasBusa @shemnon Everyone agreed this was very useful to have! We'll be merging it into the execution specs repo, similarly to how there's a list of transaction types: github.com/ethereum/execu…
@ethereum @dedaub @willmorriss4 @terencechain @BarnabasBusa @shemnon Most directly relevant to Cancun, the opcodes allocated for EIP-1153 were changed: 

@ethereum @dedaub @willmorriss4 @terencechain @BarnabasBusa @shemnon Lastly, we briefly discussed a set of proposed Cancun EIPs. @ralexstokes shared some updates on the 4788 design, modifying it to use a stateful precompile over an opcode, and we briefly discussed the MCOPY, PAY and "revamped CALL" opcode proposals
@ethereum @dedaub @willmorriss4 @terencechain @BarnabasBusa @shemnon @ralexstokes While we didn't make final decisions about inclusion, we agreed that these proposals should be the final ones formally considered for the upgrade.... with perhaps SETCODE as an exception?
The spec has been updated to reflect this: github.com/ethereum/execu…
The spec has been updated to reflect this: github.com/ethereum/execu…

@ethereum @dedaub @willmorriss4 @terencechain @BarnabasBusa @shemnon @ralexstokes And that was it! SELFDESTRUCT is being deactivated, 4844 is chugging along, and we should finalize the full scope for Dencun in the next few weeks 😄
Next ACDE is scheduled for June 8 - see you then!
Next ACDE is scheduled for June 8 - see you then!
@ethereum @dedaub @willmorriss4 @terencechain @BarnabasBusa @shemnon @ralexstokes Oh, and here are the full slides presented by @dedaub on the call 😄 docs.google.com/presentation/d…
@ethereum @dedaub @willmorriss4 @terencechain @BarnabasBusa @shemnon @ralexstokes And a note by William about how the SETCODE spec has been updated to address the DELEGATECALL concerns:
https://twitter.com/willmorriss4/status/1661834065832452108
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter