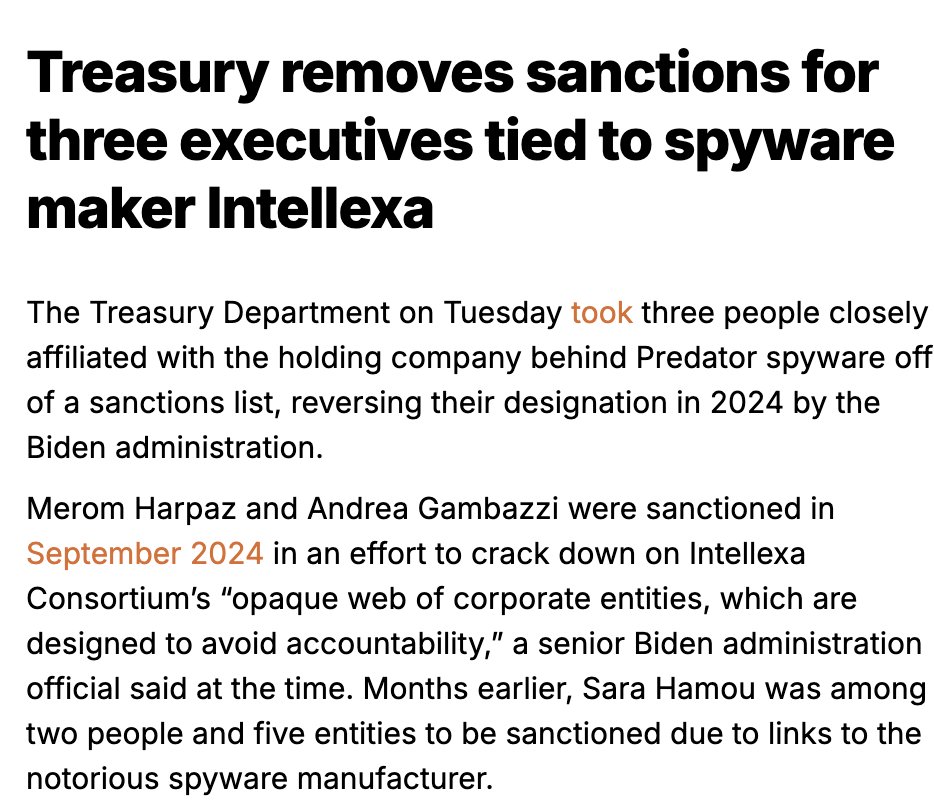
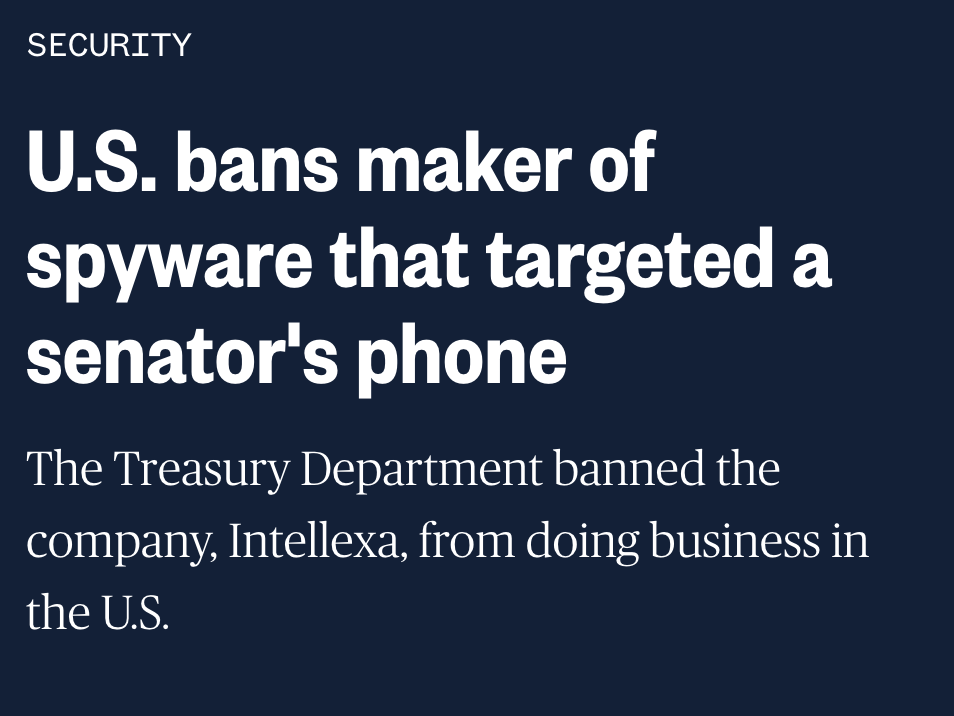
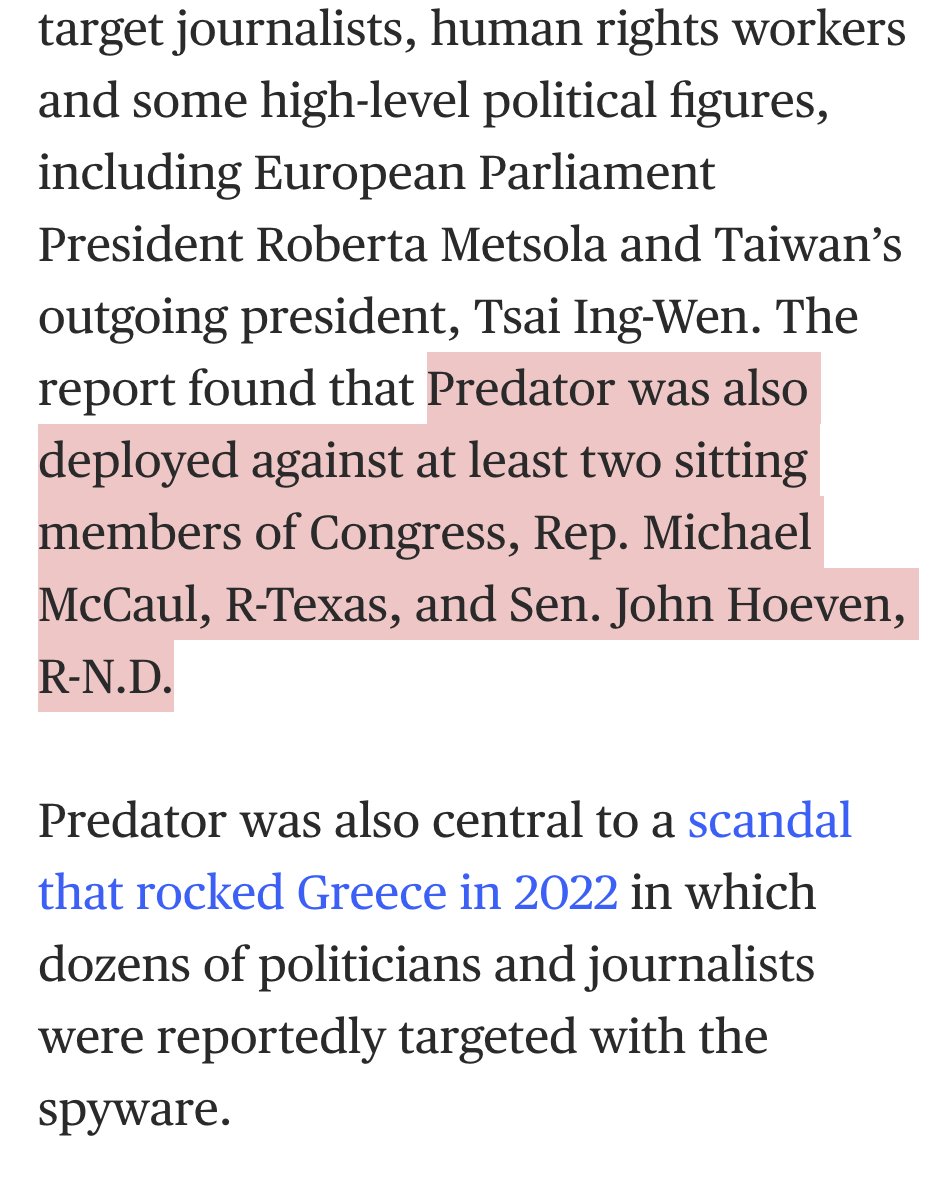
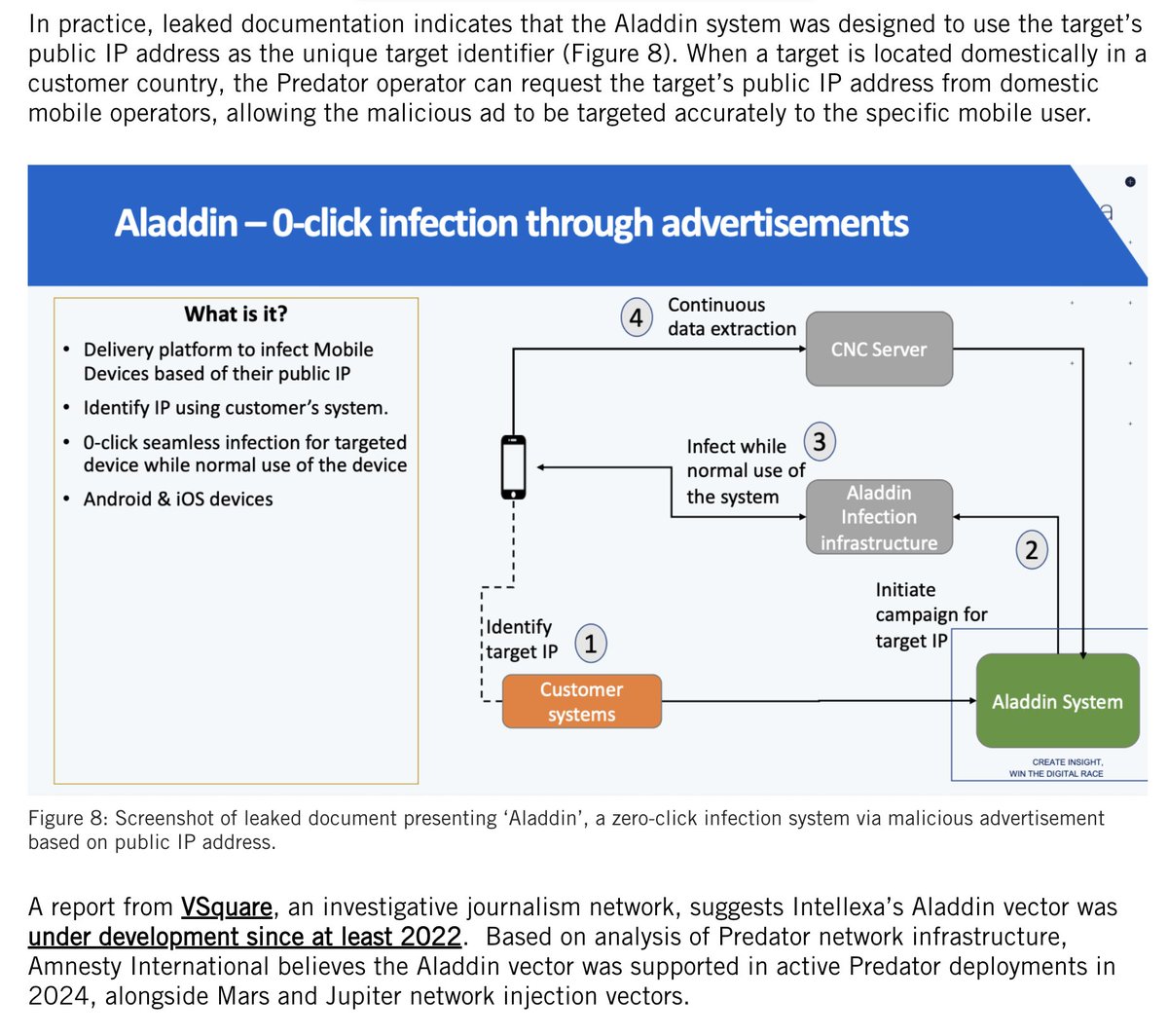
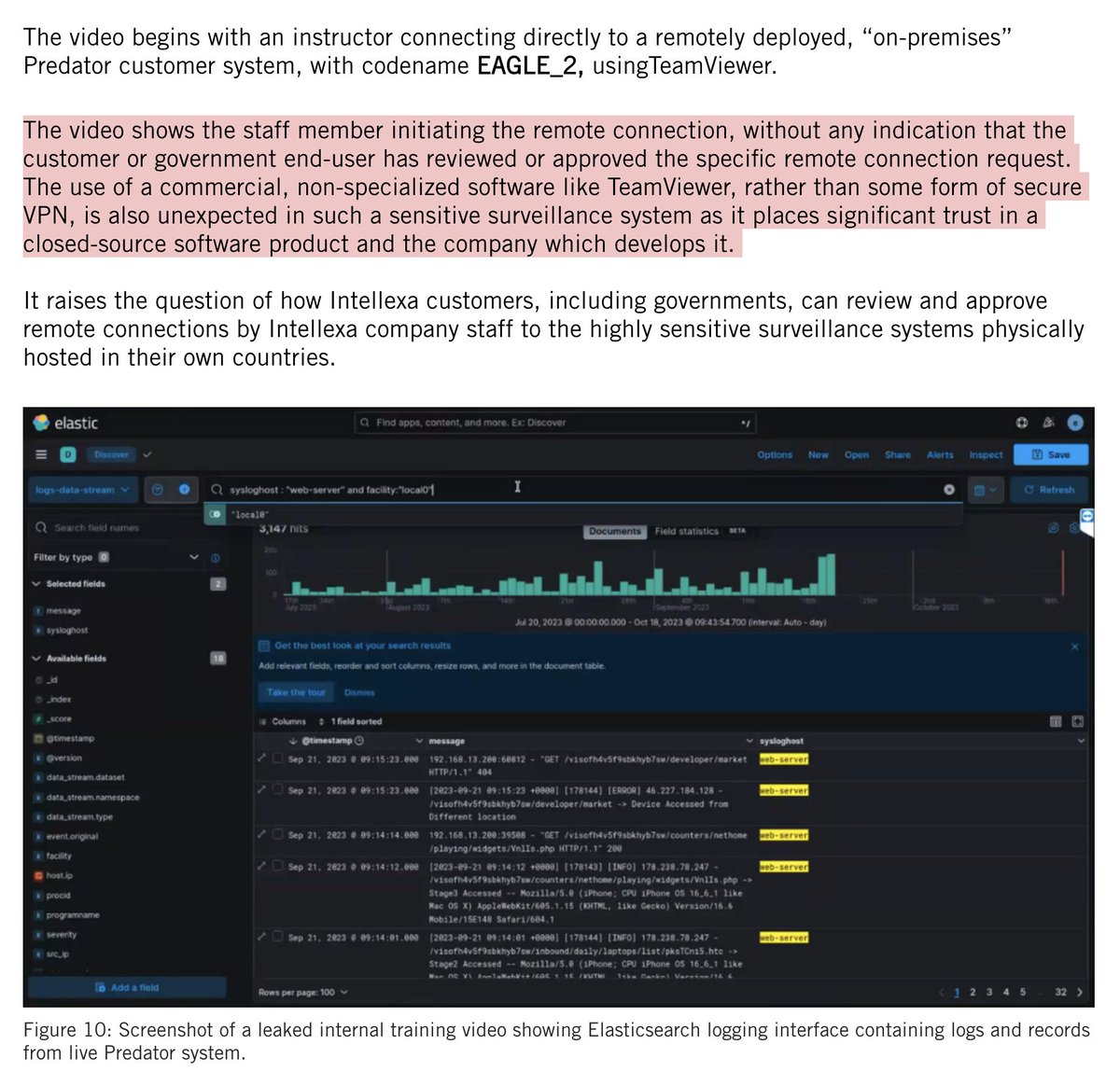
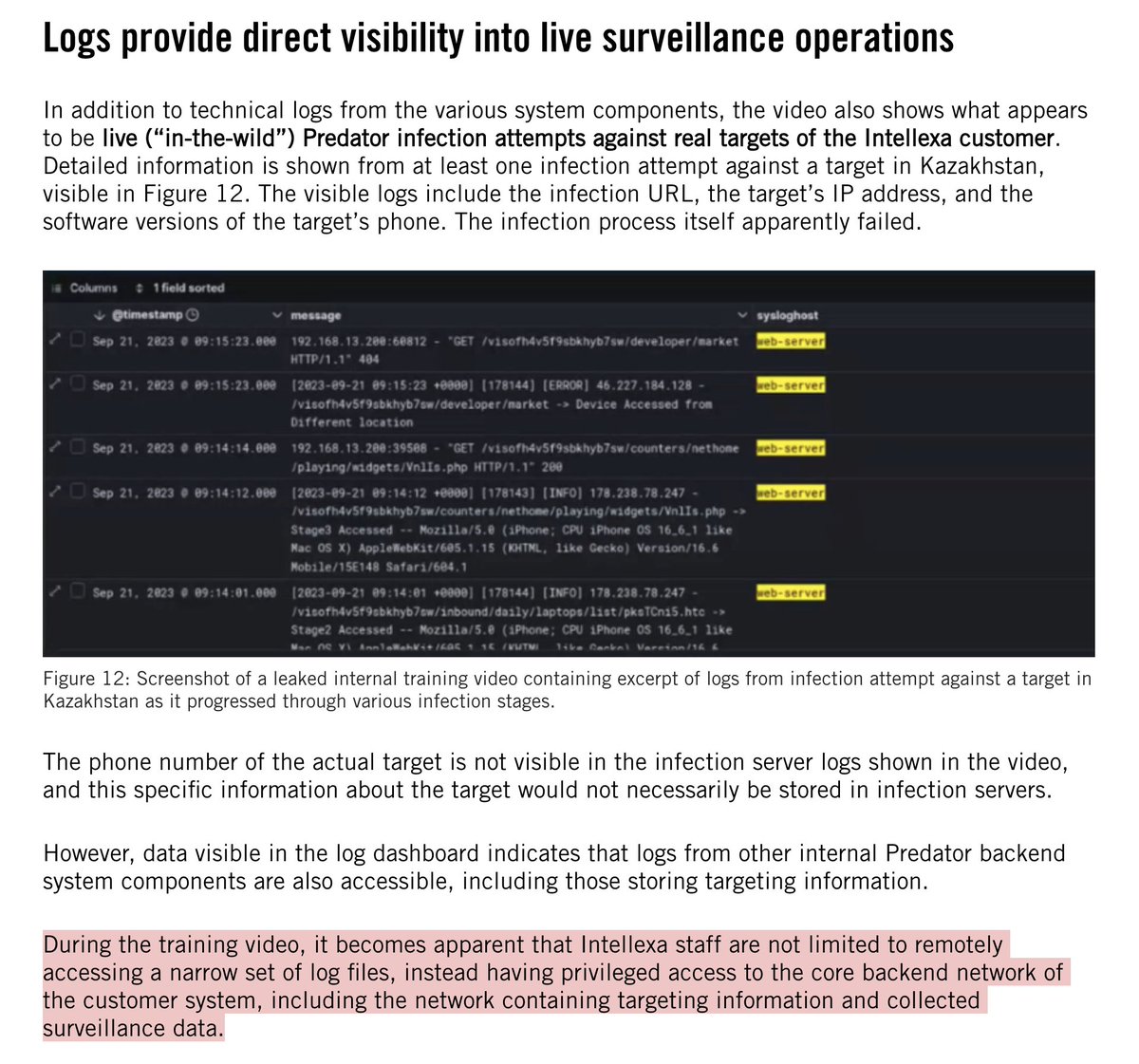
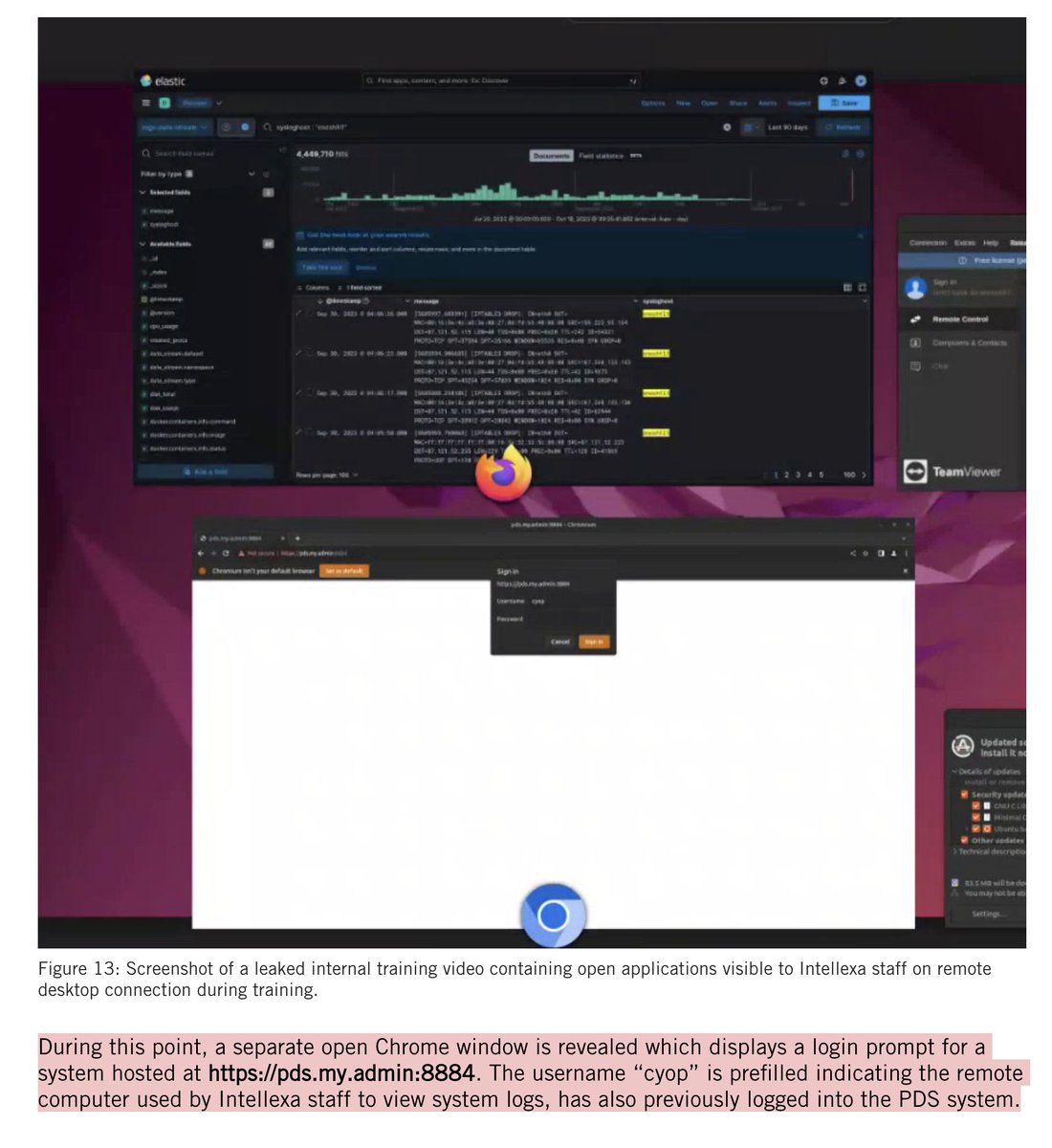
Been seeing these replies everywhere?
It's happening because Musk can't stop bots.
Let me break it down what's going on with this spam. 1./
It's happening because Musk can't stop bots.
Let me break it down what's going on with this spam. 1./

2/ Reply spammers fight a cat & mouse games with platforms like #Twitter.
One way they get spotted is by the platforms examining links.
If spammers hammer a platform by sending the same link in a thousands replies to the same scam site, it's not hard to spot & scale blocking.
One way they get spotted is by the platforms examining links.
If spammers hammer a platform by sending the same link in a thousands replies to the same scam site, it's not hard to spot & scale blocking.

3/ Remember spam emails w/misspellings, weird names, blocks of garbage text, mixtures of words & numbers etc?
These were all tactics to avoid spam filtering done by looking at each of these things for patterns.
Each new filtering strategy = new workarounds.


These were all tactics to avoid spam filtering done by looking at each of these things for patterns.
Each new filtering strategy = new workarounds.



4/ These incessant Twitter replies are doing the equivalent of old school email scammers.
They want targets to get curious & greedy like "oh cool look here's a website with an account that already has a balance...let me just log in & get rich!"
Who falls for this? Well...
They want targets to get curious & greedy like "oh cool look here's a website with an account that already has a balance...let me just log in & get rich!"
Who falls for this? Well...

5/ People greedily typing in the site URL & "logging in" see a big account balance!
1.5 million dollars in USDT
They are instantly rich!
But to get it out? Well looks like you'll need to talk to the scammers.
& maybe sign up for the "VIP plan"


1.5 million dollars in USDT
They are instantly rich!
But to get it out? Well looks like you'll need to talk to the scammers.
& maybe sign up for the "VIP plan"



6/ Here's the thing. Platforms don't just look at the text & links of posts for evidence of spamming.
(Reports help too)
They scrutinize things like IP addresses & tech used for account creation & posting.
Enough signals of badness & you can scale up blocking.
(Reports help too)
They scrutinize things like IP addresses & tech used for account creation & posting.
Enough signals of badness & you can scale up blocking.
7/ Speculation: anti-bot filtering that should happen before anyone can create an account or post... is failing.
So spam accounts are posting like crazy.
Then avoiding #Twitter's secondary defenses (e.g. text & URL filters) by mucking up their URLs to be less blatant.


So spam accounts are posting like crazy.
Then avoiding #Twitter's secondary defenses (e.g. text & URL filters) by mucking up their URLs to be less blatant.



8./ Reply spam is a numbers game.
Hope some users see a reply. (e.g. 14 views on a 60k tweet ain't great but...)
Eventually you get one user ready to go the whole way & get conned.
Even if 99.99999999% of us don't, there's still potential for ROI.
Hope some users see a reply. (e.g. 14 views on a 60k tweet ain't great but...)
Eventually you get one user ready to go the whole way & get conned.
Even if 99.99999999% of us don't, there's still potential for ROI.

9/ Now, here's the thing. You have seen this reply spam for a while because the network has been up before.
Then #Twitter did some mass suspensions.
But the spammers figured out how to circumvent #Twitter.
Great thread on the last go-round👇👇
Then #Twitter did some mass suspensions.
But the spammers figured out how to circumvent #Twitter.
Great thread on the last go-round👇👇
https://twitter.com/conspirator0/status/1657519601448517633
10/ Still with me this far down the reply #spam rabbit hole?
Here's an interview with a crypto spam scammer by @briankrebs.
Thanks @oxleyio for flagging!
krebsonsecurity.com/2023/05/interv…
Here's an interview with a crypto spam scammer by @briankrebs.
Thanks @oxleyio for flagging!
krebsonsecurity.com/2023/05/interv…
11/ Reply scam is like opportunistic infections.
They proliferate when an immune system isn't working.
Just like #Twitter's anti-bot tech.
They proliferate when an immune system isn't working.
Just like #Twitter's anti-bot tech.
12/ Just *so many signals* #Twitter could use to stomp reply spam bot accounts.
Them just constantly showing up in our replies is the daily reminder of just how bad things are.
Them just constantly showing up in our replies is the daily reminder of just how bad things are.

• • •
Missing some Tweet in this thread? You can try to
force a refresh