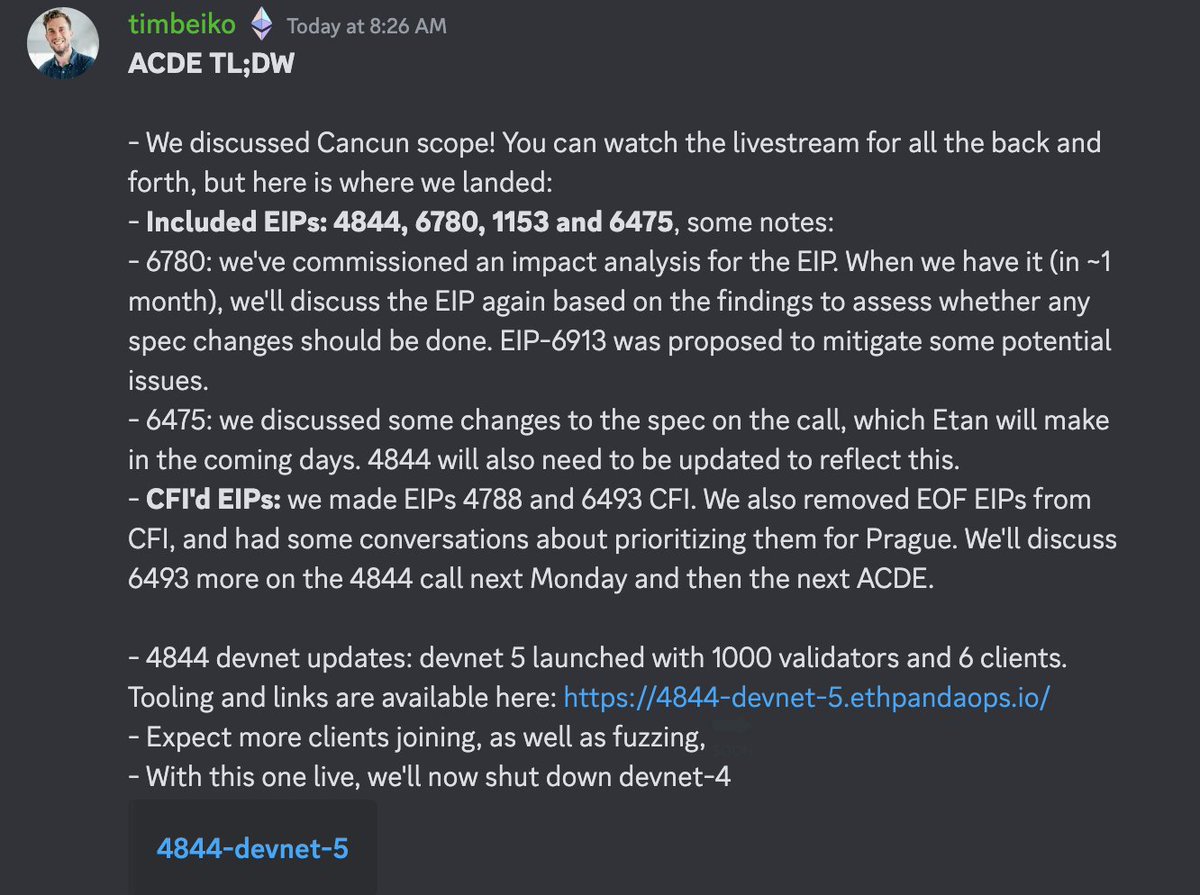
Had another @ethereum #ACDE earlier today: we finalized the Cancun EIP list, and discussed possible 4844, Engine API and validator spec changes 🏝️
Agenda: github.com/ethereum/pm/is…
Recording: youtube.com/live/LqaR-kdnO…
Recap below 👇
Agenda: github.com/ethereum/pm/is…
Recording: youtube.com/live/LqaR-kdnO…
Recap below 👇
https://twitter.com/TimBeiko/status/1661837625408487424
@ethereum We began the call with @dankrad making the case for changing the 4844 blob target & limit from 2/4 to 3/6.
To justify this, tests have been run on testnet + mainnet sending large blocks and analyzing the impact on the network.
To justify this, tests have been run on testnet + mainnet sending large blocks and analyzing the impact on the network.
@ethereum @dankrad Here's @christine_dkim's recap of the discussion on ACDC last week 👇
https://twitter.com/christine_dkim/status/1664645304296013826
@ethereum @dankrad @christine_dkim Early in the call, we reached consensus to move forward with this change. That said, the proposition later faced some opposition from the Geth team, which had concerns about the impact of the change on network stability.
@ethereum @dankrad @christine_dkim There was a lot of back and forth, but the crux of the debate is around how conservative we should be when introducing blobs to the network.
@ethereum @dankrad @christine_dkim On one hand, blobs are already a significant increase in gossiped data that will be introduced all at once. OTOH, providing L2 users with cheaper transaction fees is extremely important, and we can only increase blobs during hard forks, which are infrequent.
@ethereum @dankrad @christine_dkim After some more back and forth between @vdWijden and @dankrad at the end of the call, we agreed to keep the 3/6 target/limit combo for the next devnet and continue discussions around whether this is the right value for mainnet!
@ethereum @dankrad @christine_dkim @vdWijden On that note, @BarnabasBusa gave an update on the state of 4844 devnets: a first version of devnet-6 was launched this week with Lodestar, Teku, Nethermind and EthereumJS. With this blob count change, and other clients being ready to join soon, we'll do a full restart next week!
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa Here's the tracker we are using to determine the scope of the devnet: notes.ethereum.org/@bbusa/dencun-…
We discussed the last open PRs around JSON RPC on the call and agreed to keep those out of scope for devnet 6, but include full RPC support in devnet 7!
We discussed the last open PRs around JSON RPC on the call and agreed to keep those out of scope for devnet 6, but include full RPC support in devnet 7!
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa Then, we discussed a proposed change to EIP-4788, which exposes the Beacon block root in the EVM. The proposal was to limit the number of block roots stored on the EL to cap state growth. This would require more disk writes from EL clients, but everyone agreed with the change!
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa Next up, we discussed what to include alongside the previously chosen Cancun EIPs 🏝️
So far, Cancun had EIPs 1153 (Transient Storage), 4844 (ProtoDanksharding) and 6780 (SELFDESTRUCT removal). On the last ACDE, we finalized the list of EIP candidates:
So far, Cancun had EIPs 1153 (Transient Storage), 4844 (ProtoDanksharding) and 6780 (SELFDESTRUCT removal). On the last ACDE, we finalized the list of EIP candidates:
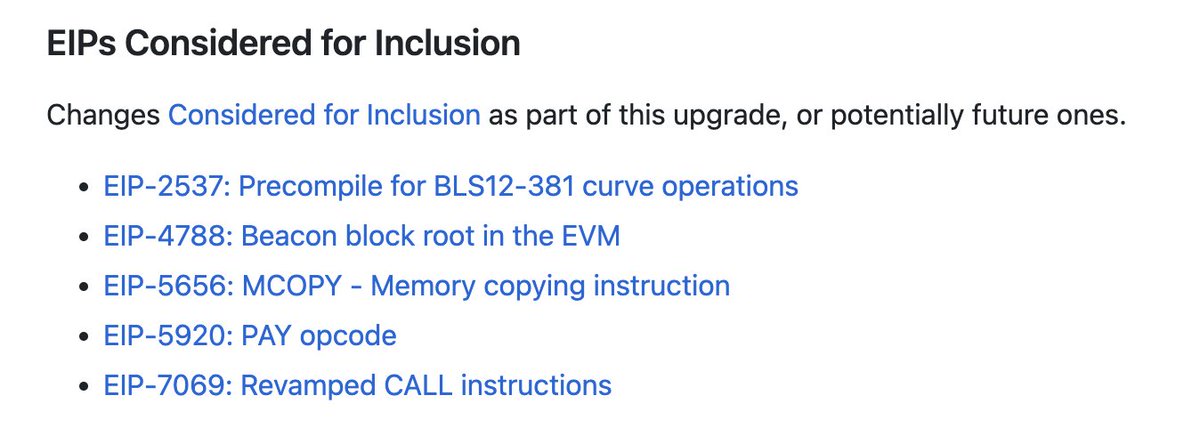
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa Client teams rapidly agreed to include EIP-4788!
Then, there were proposals for both EIPs 5656 (MCOPY) and 5920 (PAY)
https://twitter.com/ralexstokes/status/1666825863856545793
Then, there were proposals for both EIPs 5656 (MCOPY) and 5920 (PAY)
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa Due to some concerns about the potential side effects of including another way to transfer ETH, and the testing + security work required to reason through them, PAY was rejected for this upgrade.
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa Teams were initially split about MCOPY: while security concerns were addressed, there was concern about the implementation + testing bandwidth required to add this to the upgrade.
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa After some back and forth, we agreed to include the EIP, and that if we run into capacity issues on either the testing or client side, we'll consider removing it. So, MCOPY is (tentatively) included as well 🎉
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa So, TL;DR Cancun🏝️ will include:
EIP-1153: Transient storage opcodes
EIP-4788: Beacon block root in the EVM
EIP-4844: Shard Blob Transactions
EIP-5656: MCOPY - Memory copying instruction
EIP-6780: SELFDESTRUCT only in same transaction
Here's the PR: github.com/ethereum/execu… 😄
EIP-1153: Transient storage opcodes
EIP-4788: Beacon block root in the EVM
EIP-4844: Shard Blob Transactions
EIP-5656: MCOPY - Memory copying instruction
EIP-6780: SELFDESTRUCT only in same transaction
Here's the PR: github.com/ethereum/execu… 😄
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa After we briefly discussed and agreed to a proposed change to the Engine API versioning scheme, which would remove old ExecutionPayload versions and add a timestamp check to ensure V3 payloads are only sent after the next fork activates
github.com/ethereum/execu…
github.com/ethereum/execu…
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa Then, @tbenr had some questions about the validator specs. Specifically, he was wondering whether nodes should process all blobs on the network prior to sending attestations or not.
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa @tbenr Not having to do so could provide some UX benefits if a CL is swapped out on a synced EL (e.g. when changing CL client). That said, this does go against the implied semantics of the spec. @dannyryan will put up a PR to clarify & we'll discuss further on the ACDC call next week.
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa @tbenr @dannyryan And, lastly... well, aside from the blob limit debate pt II which I summarized earlier!, @BarnabasBusa announced a first coordination call around the launch of a new testnet: Holesky
github.com/ethereum/pm/is…
github.com/ethereum/pm/is…
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa @tbenr @dannyryan Holesky aims to run more validators than are currently on mainnet, to allow us to stress test Beacon chain-related changes. Rough ETA for the launch is Merge Day (Sept 15) - if you're into testnets, you should show up 😄!
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa @tbenr @dannyryan And that was it! Next ACDE is scheduled for June 22, 14:00 UTC. Until then, see you at the 4844, EOF, Holesky and ACDC calls 🙃
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa @tbenr @dannyryan Oh and one more thing: we'll be hosting an Ethereum Protocol Fellowship Town Hall next Monday at 16:30 UTC. If you're potentially interested in going down the protocol development rabbit hole, you should show up 😄
Info here: blog.ethereum.org/2023/06/01/eth…
Info here: blog.ethereum.org/2023/06/01/eth…
@ethereum @dankrad @christine_dkim @vdWijden @BarnabasBusa @tbenr @dannyryan 1153: store data, delete at end of txn -> cheaper
4788: add data beacon data chain in EVM, less trust assumption for staking pools
4844: store data, delete after 3 weeks, cheaper rollup txns
5656: cool new opcode
6780: remove SELFDESTRUCT, reduce breakage
4788: add data beacon data chain in EVM, less trust assumption for staking pools
4844: store data, delete after 3 weeks, cheaper rollup txns
5656: cool new opcode
6780: remove SELFDESTRUCT, reduce breakage
https://twitter.com/ArminJaeger4/status/1666914280237613066
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter