If you don’t want to Burp every time you look at a web application I have just the right free tool for you.
The ⚡️ZAP⚡️ Gang is coming together to hack some bug bounty programs and we are going to join them.
The ⚡️ZAP⚡️ Gang is coming together to hack some bug bounty programs and we are going to join them.
@zaproxy will help you hack websites quickly and in an automated fashion
Just the way we like it - and the best?!
It is open source and free.
WHOAAAA - but what is ZAP really?
Just the way we like it - and the best?!
It is open source and free.
WHOAAAA - but what is ZAP really?
It's a proxy. Plain and simple and not really descriptive.
Lets fix that.
A proxy is a piece of software that sits between you and the internet
Kinda like my dad when I was younger...
Lets fix that.
A proxy is a piece of software that sits between you and the internet
Kinda like my dad when I was younger...
Hackers use proxies to capture requests send to the internet and from the internet to them.
Why?
Why?
They manipulate the requests
- add some data
- remove some data
- change some data
and finally see how the application handles these situations 🦾🤖
- add some data
- remove some data
- change some data
and finally see how the application handles these situations 🦾🤖
Proxies help hackers to stop every request and response - it's like a bouncer for their club. 💪😤
Request 1: COOL😎 - you are a good request, I know you, no need to search you
Request 2: STOP🦋 - who are you?! Let me see if I can find something interesting in your head(ers) 🤕
Request 1: COOL😎 - you are a good request, I know you, no need to search you
Request 2: STOP🦋 - who are you?! Let me see if I can find something interesting in your head(ers) 🤕
Hacker also use proxies to spider / scrape applications which is what we will do today.
@zaproxy has a very neat function for that but first we need to install the software and a proxy switcher
I will guide you through the process
@zaproxy has a very neat function for that but first we need to install the software and a proxy switcher
I will guide you through the process
1. Go to
zaproxy.org/download/ and click on the “download” button for your operating system
2. open the downloaded file and install the software
3. start Zed Attack Proxy (ZAP)
zaproxy.org/download/ and click on the “download” button for your operating system
2. open the downloaded file and install the software
3. start Zed Attack Proxy (ZAP)
You could also run ZAP in a docker container 🐳 📦
if you would like to
hub.docker.com/r/owasp/zap2do…
if you would like to
hub.docker.com/r/owasp/zap2do…
ZAP will probably ask you to update plugins - go ahead and “Update all” of them and close the marketplace window
ps you dont have to wait until the update for all the plugins is done, it will continue the update in the background after you click “Close”
ps you dont have to wait until the update for all the plugins is done, it will continue the update in the background after you click “Close”

🎊 NICE 🎉
You just installed ZAP
Now you can either click on the small 🔥🦊 firefox in the top right
(or use a proxy-switcher - e.g. foxyproxy getfoxyproxy.org)
After you clicked the firefox icon - a browser will open - this one has ZAP integration already
umm?!
You just installed ZAP
Now you can either click on the small 🔥🦊 firefox in the top right
(or use a proxy-switcher - e.g. foxyproxy getfoxyproxy.org)
After you clicked the firefox icon - a browser will open - this one has ZAP integration already
umm?!

WHAT DOES THAT MEAN!?!?!
When you look at the address bar, something seems different compared to your normal browser, right?!
Those diagonal things are not there usually and the little robot face in front of the url is also new 🤖
Is this what Terminator warned us about?!
When you look at the address bar, something seems different compared to your normal browser, right?!
Those diagonal things are not there usually and the little robot face in front of the url is also new 🤖
Is this what Terminator warned us about?!

These are indicators that your current firefox window was modified by some tool (ZAP)
ah of course… wait WHAT?!
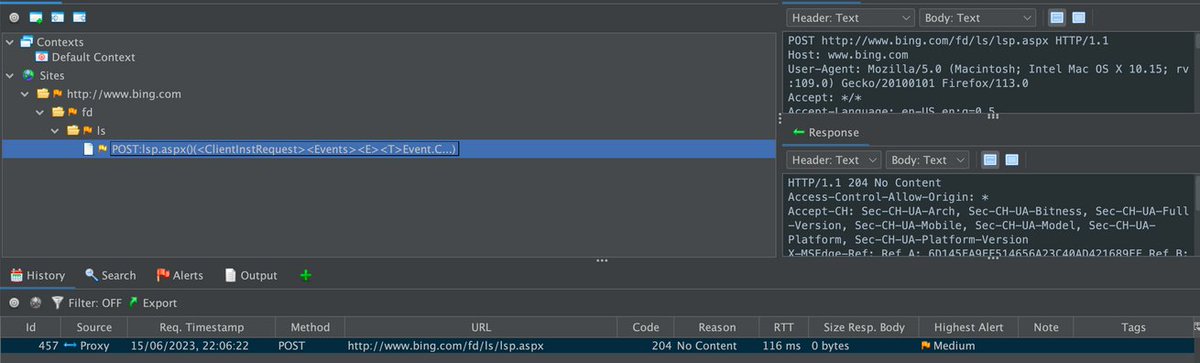
When you open a page in this browser - I chose bing because why not.
And look at ZAP next…
ah of course… wait WHAT?!
When you open a page in this browser - I chose bing because why not.
And look at ZAP next…
You will see that the website you visited now magically appeared in ZAP.
Any request / response coming through that browser can be modified with ZAP now
OHHHH - that is coool 😈
Any request / response coming through that browser can be modified with ZAP now
OHHHH - that is coool 😈
Now we come to the real wizard part
Hold your horses HARRY. 🪄🦄
We will use a spider to first find all the possible links we can click on
next we figure out how we can login and use the logged in session in ZAP
yes you read that right a 🕷️🕸️ - sorry arachnophobes.
Hold your horses HARRY. 🪄🦄
We will use a spider to first find all the possible links we can click on
next we figure out how we can login and use the logged in session in ZAP
yes you read that right a 🕷️🕸️ - sorry arachnophobes.
Open juice-shop.herokuapp.com/#/
in your browser
at the top right there is a “Account” button that you can click on and then hit that login button as well
in your browser
at the top right there is a “Account” button that you can click on and then hit that login button as well

Since we dont have an account yet we need to create one - use the green link at the bottom of the login portal - “Not yet a customer?”
hit that, enter your hacker persona details and click the “Register” button afterwards
hit that, enter your hacker persona details and click the “Register” button afterwards

You can now login and check out the internal part of the juice shop manually
OR
you let the robots do the work. 🤖🤖🤖
OR
you let the robots do the work. 🤖🤖🤖
I would recommend doing the following first
Inside ZAP you right click the juice shop url and then use “Include in Context” and “Default Context” to make sure you define your scope
You only want resources on your target - not some random facebook page.
Inside ZAP you right click the juice shop url and then use “Include in Context” and “Default Context” to make sure you define your scope
You only want resources on your target - not some random facebook page.

Now we spider - click on the url
and then use the “Attack” → “Spider” to crawl all urls on the target (use the default parameters)
and punch that “Start Scan” button
Spider go BRRRRRRRRR ⏩

and then use the “Attack” → “Spider” to crawl all urls on the target (use the default parameters)
and punch that “Start Scan” button
Spider go BRRRRRRRRR ⏩


at the bottom you can now see the urls popping up and either with a green or red light
green = processed
red = ignored (usually because of out of scope)
Search through the urls - you might find a diamond in the rough or some previously unknown resources that are juicy 🧃
green = processed
red = ignored (usually because of out of scope)
Search through the urls - you might find a diamond in the rough or some previously unknown resources that are juicy 🧃
Did you spot the one I am talking about?
That FTP link does look interesting, right?!
Shall we see whats behind it?
That FTP link does look interesting, right?!
Shall we see whats behind it?

Can you smell more vulnerabilities heading your way now?
There is a new book by packt publishing - the ZAP Cookbook - this one might have exactly the details you are looking for to get the most out of ZAP.
You can check it out here:
packtpub.com/product/zed-at…
#sponsored #ad
There is a new book by packt publishing - the ZAP Cookbook - this one might have exactly the details you are looking for to get the most out of ZAP.
You can check it out here:
packtpub.com/product/zed-at…
#sponsored #ad
@threadreaderapp unroll
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter