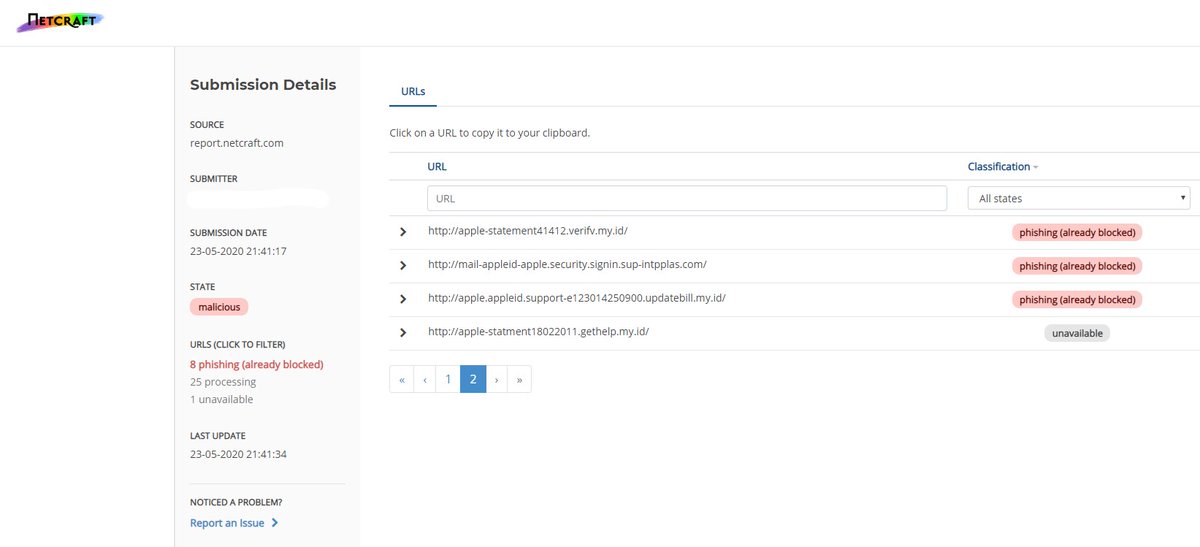
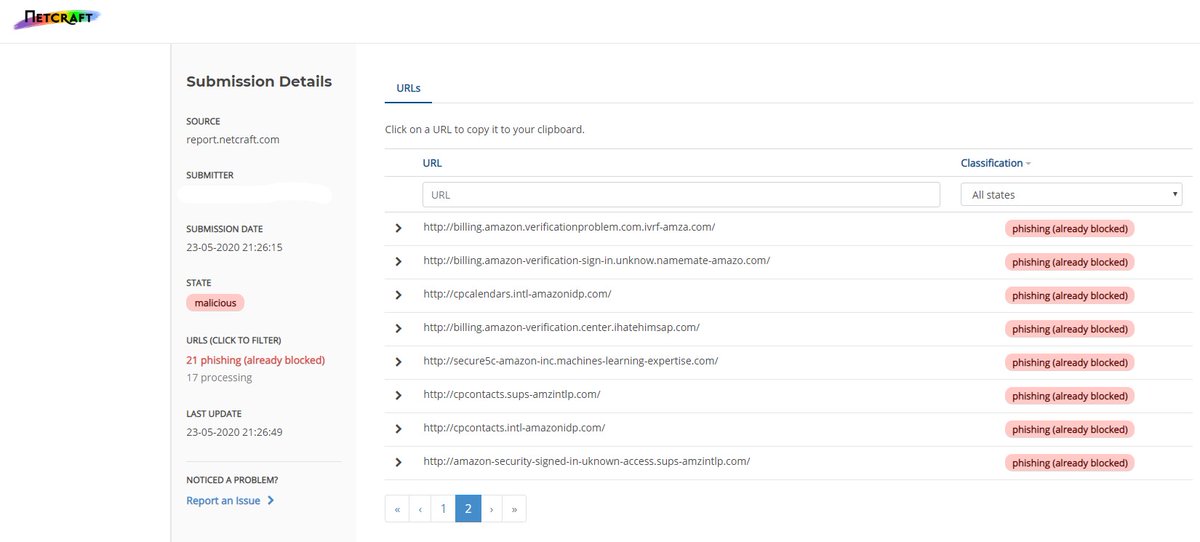
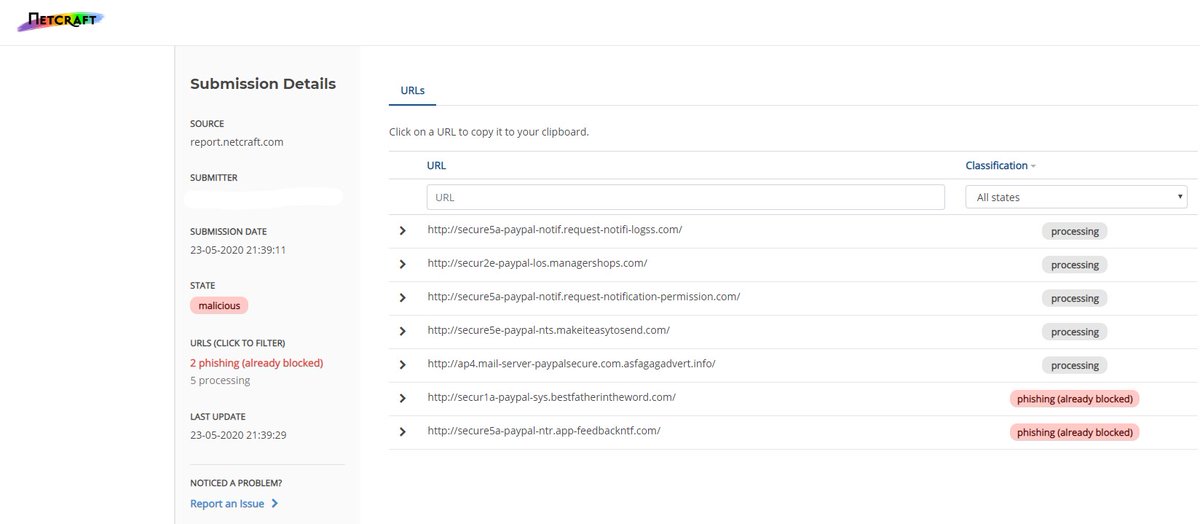
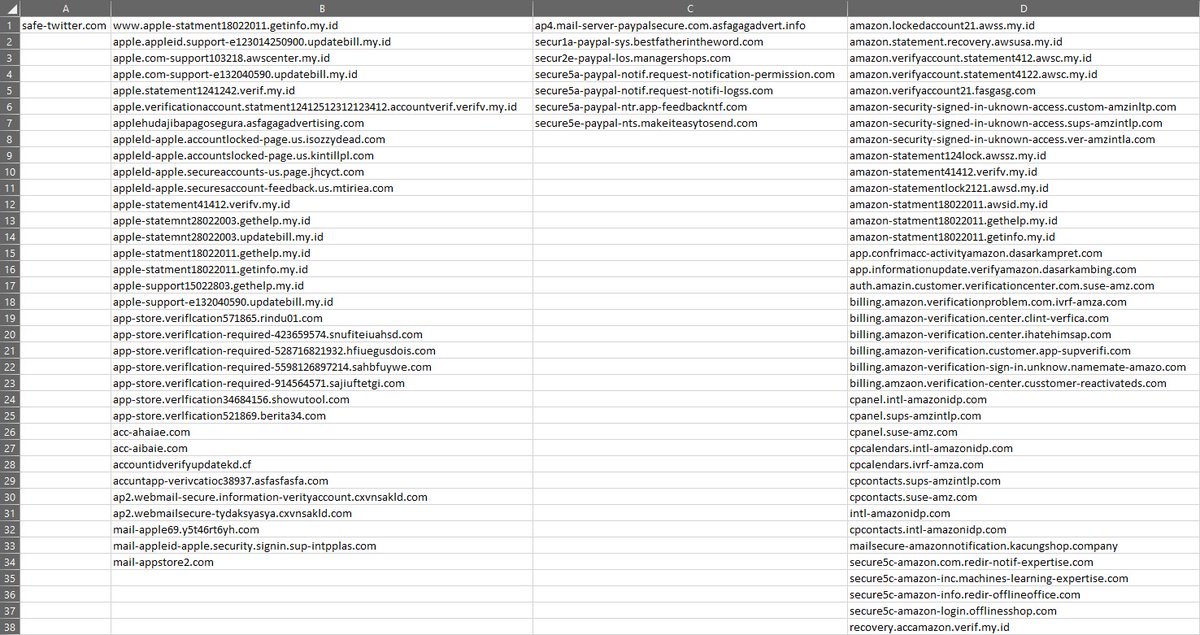
🧵#MustangPanda 🐼 (& other #APT groups) use DLL side-loading/search-order hijacking (see ATT&CK).
It's a pain for #CTI analysts who manually vet IOCs -> as this TTP involves delivering a valid vulnerable application, Bring-Your-Own-Vulnerable-App (BYOVA), if you will... 1/3
It's a pain for #CTI analysts who manually vet IOCs -> as this TTP involves delivering a valid vulnerable application, Bring-Your-Own-Vulnerable-App (BYOVA), if you will... 1/3
For example, take this Symantec.exe binary, it's a valid, signed file 🔍 but it's used by #MustangPanda 🐼 for dll side-loading!
Should you pre-emptively block it? Maybe. But first, be sure to check 📝 for its presence in the org -> before causing lots of alerts or worse ⚠️ 2/3

Should you pre-emptively block it? Maybe. But first, be sure to check 📝 for its presence in the org -> before causing lots of alerts or worse ⚠️ 2/3


OR you should give warnings ⚠️ before sharing these BYOVA bins as IOCs!
🥲The CTI analyst struggle to vet IOCs is real... but this may help!
I created a Gist & VT Collection for triage:
1.🔗gist.github.com/BushidoUK/181d…
2. 🔗 virustotal.com/gui/collection…
Hopefully this is useful! 2/2
🥲The CTI analyst struggle to vet IOCs is real... but this may help!
I created a Gist & VT Collection for triage:
1.🔗gist.github.com/BushidoUK/181d…
2. 🔗 virustotal.com/gui/collection…
Hopefully this is useful! 2/2
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter