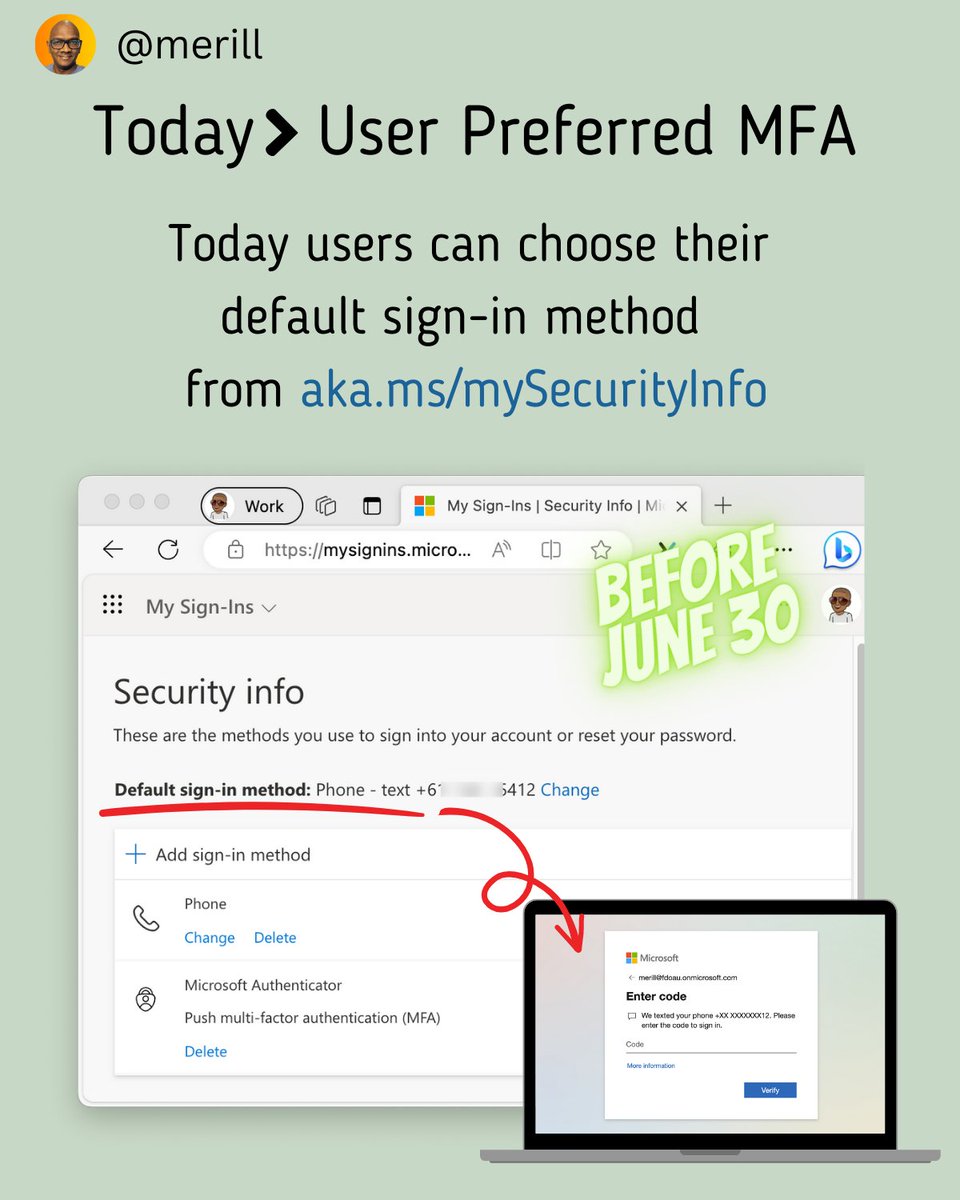
It's 2023 and your IT team is still forcing the entire company to change their passwords every few months 🤦
PS. I work at Microsoft, and we stopped doing this nearly four years ago.
Send the link below to your IT team 👇
PS. I work at Microsoft, and we stopped doing this nearly four years ago.
Send the link below to your IT team 👇

💠
The recommendation now is to only force a user to change their password if a compromise has been detected.
If your org is using Microsoft 365, you can set it up to force a password change when a user's password is compromised.
If you are not licensed… https://t.co/Ipo25zfUa9zdnet.com/article/micros…
twitter.com/i/web/status/1…
The recommendation now is to only force a user to change their password if a compromise has been detected.
If your org is using Microsoft 365, you can set it up to force a password change when a user's password is compromised.
If you are not licensed… https://t.co/Ipo25zfUa9zdnet.com/article/micros…
twitter.com/i/web/status/1…
To those asking about audits & PCI requirements.
How many of your users have access to your customer's credit card data❓️
Why not apply the forced expiry to the subset of users that actually handle credit card data?
📢 Plus, it's now 1 year expiry ⬇️
https://t.co/pWDAnMEiHKbleepingcomputer.com/news/security/…

How many of your users have access to your customer's credit card data❓️
Why not apply the forced expiry to the subset of users that actually handle credit card data?
📢 Plus, it's now 1 year expiry ⬇️
https://t.co/pWDAnMEiHKbleepingcomputer.com/news/security/…

If you like to be kept up to date on Microsoft Azure AD (Microsoft Entra) feel free to follow me.
You can also sign up for my weekly newsletter that helps you stay on top of all the latest Microsoft identity related news👇🏾
entra.news
You can also sign up for my weekly newsletter that helps you stay on top of all the latest Microsoft identity related news👇🏾
entra.news
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter