Today, we will cover how you can successfully exploit XXE vulnerabilities
If you aren't familiar with the concepts of XXE yet...
This thread is made just for you! 👇️
If you aren't familiar with the concepts of XXE yet...
This thread is made just for you! 👇️
https://twitter.com/intigriti/status/1684887385715376128
1⃣ Basic exploitation via XML Entities
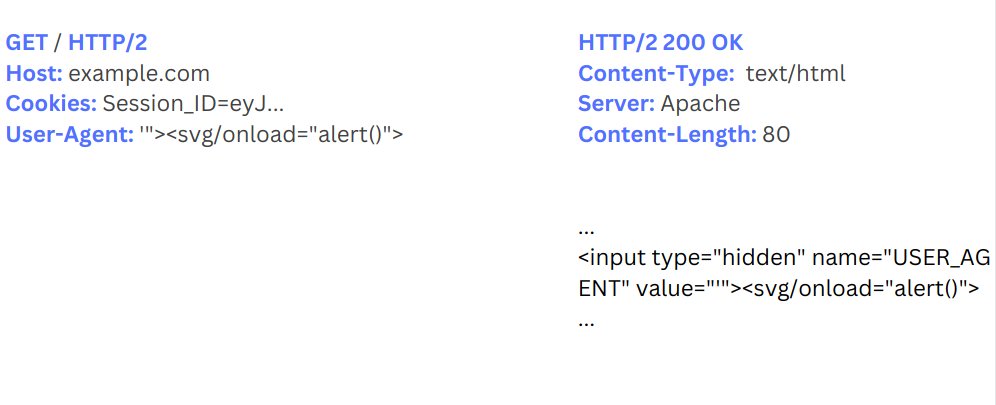
Let's start off with the most basic example
A web app that queries the backend to retrieve your previously sent messages
Let's start off with the most basic example
A web app that queries the backend to retrieve your previously sent messages

To test if this feature is vulnerable to XXE, we could try and retrieve a local file
To do so, we'd have to add the XML entity definition ourselves:
To do so, we'd have to add the XML entity definition ourselves:

Afterwards, include your entity in the field and send the request
The response should contain the contents of the local file "/etc/passwd"
The response should contain the contents of the local file "/etc/passwd"

But we can also take the same approach to request an internal or external resource and escalate this into an SSRF vulnerability! 

2⃣ Exploitation via OOB technique
This exploitation technique involves us hosting a DTD file and referencing it in our payload
The XML parser will then parse our malicious XML data and retrieve the external DTD
This exploitation technique involves us hosting a DTD file and referencing it in our payload
The XML parser will then parse our malicious XML data and retrieve the external DTD
That DTD file contains our payload
And just as before, we can send our request and retrieve the contents of a local file for example!


And just as before, we can send our request and retrieve the contents of a local file for example!


We hope you've learned something new from this thread on XXE exploitation:
If you have enjoyed this thread:
1. Follow us @INTIGRITI for more of these threads 🐛️
2. Retweet the first Tweet to share it with your friends 💙️
If you have enjoyed this thread:
1. Follow us @INTIGRITI for more of these threads 🐛️
2. Retweet the first Tweet to share it with your friends 💙️
https://twitter.com/intigriti/status/1689937316276535296
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter