I hacked a car company.
Here's how I gained access to hundreds of their codebases.
Here's how I gained access to hundreds of their codebases.
1. This company ran a bug bounty program.
I came across a web server that responded with:
> 404 Not Found: Requested route ('example.apps.███.com')
I came across a web server that responded with:
> 404 Not Found: Requested route ('example.apps.███.com')
2. This is likely an ingress controller.
Seeing "404 Not Found" and
• the Host header reflected in the response
• The word "route" in the response
Made me believe it was.
What's an ingress controller?
Seeing "404 Not Found" and
• the Host header reflected in the response
• The word "route" in the response
Made me believe it was.
What's an ingress controller?
3. TL;DR: They route HTTP requests to different services.
Typically using the Host header and/or a path.
So, I started brute-forcing the host headers:
I got a hit:
> configurator-prod.apps.███.com
Typically using the Host header and/or a path.
So, I started brute-forcing the host headers:
I got a hit:
> configurator-prod.apps.███.com

4. I wasn't sure what this was.
So, I brute-forced paths on the host:
$ ffuf -u ██/FUZZ -H "Host: configurator-prod.apps.███.com" -mc all
> /env – "200 OK"
> /heapdump – "200 OK"
It was running Spring Boot Actuator & it was misconfigured.
So, I brute-forced paths on the host:
$ ffuf -u ██/FUZZ -H "Host: configurator-prod.apps.███.com" -mc all
> /env – "200 OK"
> /heapdump – "200 OK"
It was running Spring Boot Actuator & it was misconfigured.
5. The /env endpoint didn't contain much.
I also couldn't POST to it to achieve RCE.
It did contain:
• A "config server" URL (config-server-UUID.apps.███)
• And an oauth2 endpoint + credentials (to authenticate to the referenced server)
But, the password was redacted.
I also couldn't POST to it to achieve RCE.
It did contain:
• A "config server" URL (config-server-UUID.apps.███)
• And an oauth2 endpoint + credentials (to authenticate to the referenced server)
But, the password was redacted.

6. Remember the "/heapdump" endpoint?
Heap dumps are a snapshot of objects in memory for an application.
That includes the credentials...
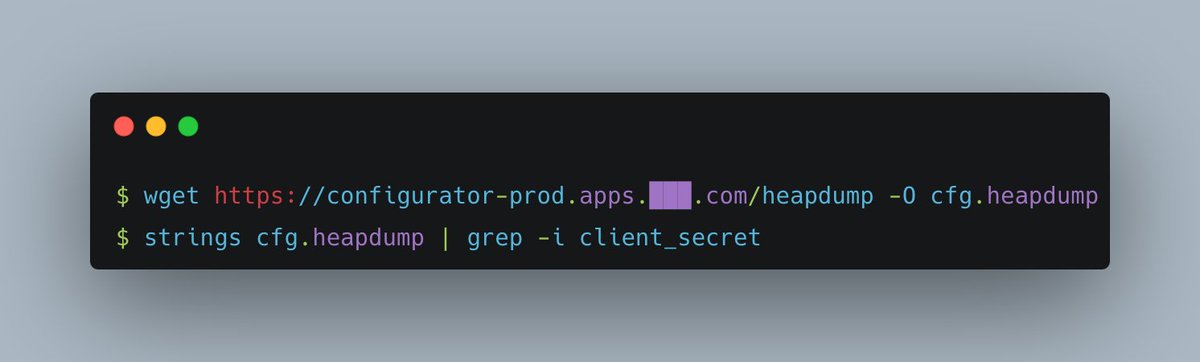
So, I grabbed the credentials by:
• Downloading the heap dump using wget.
• Running strings & grepping for the client secret
Got 'em.
Heap dumps are a snapshot of objects in memory for an application.
That includes the credentials...
So, I grabbed the credentials by:
• Downloading the heap dump using wget.
• Running strings & grepping for the client secret
Got 'em.
7. Now, I wanted to:
• Use these oauth2 credentials
• Hit the newly found config server for "configurator-prod"
• Fuzz it for endpoints
So, I used the oauth2 endpoint (leaked in the accessTokenURI)
+ the leaked credentials and got an access token:
• Use these oauth2 credentials
• Hit the newly found config server for "configurator-prod"
• Fuzz it for endpoints
So, I used the oauth2 endpoint (leaked in the accessTokenURI)
+ the leaked credentials and got an access token:

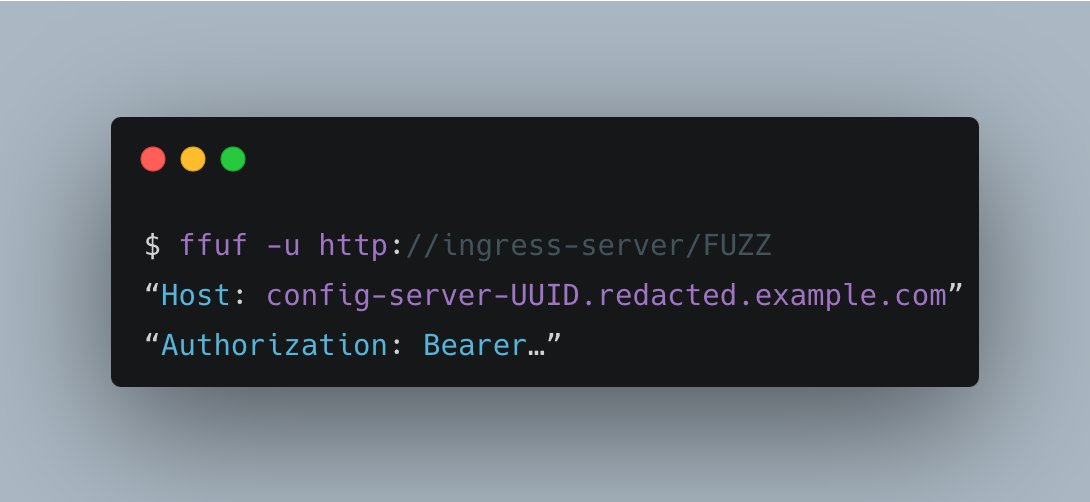
8. Then, I used it to access the config-server and fuzzed for endpoints.
Turns out, it was Spring Boot Actuator…
and misconfigured…again.
The /env & /heapdump endpoints were exposed.
Turns out, it was Spring Boot Actuator…
and misconfigured…again.
The /env & /heapdump endpoints were exposed.
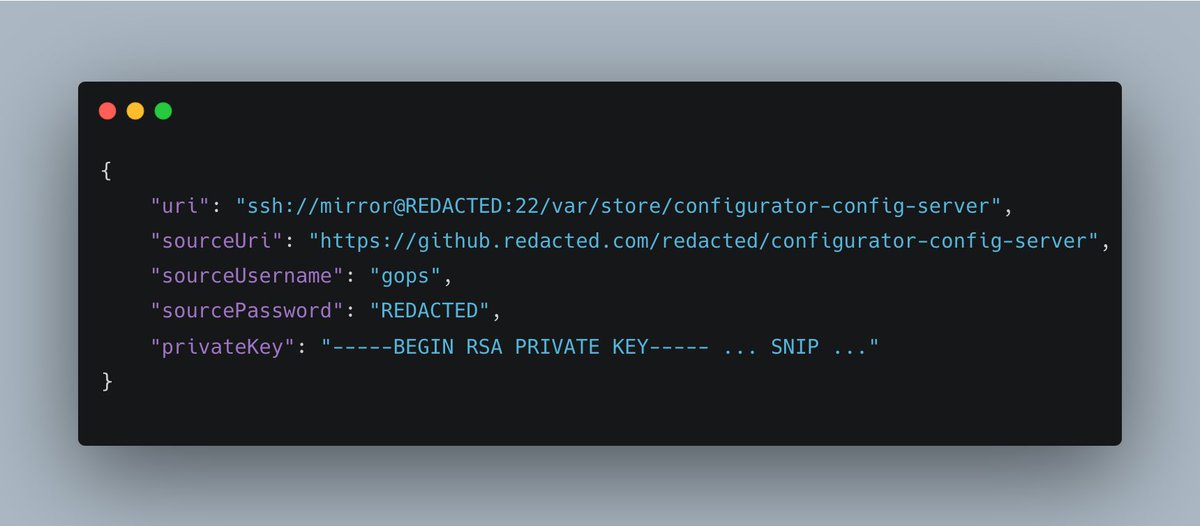
9. In the /env response was Github credentials...
And the private key for the user.
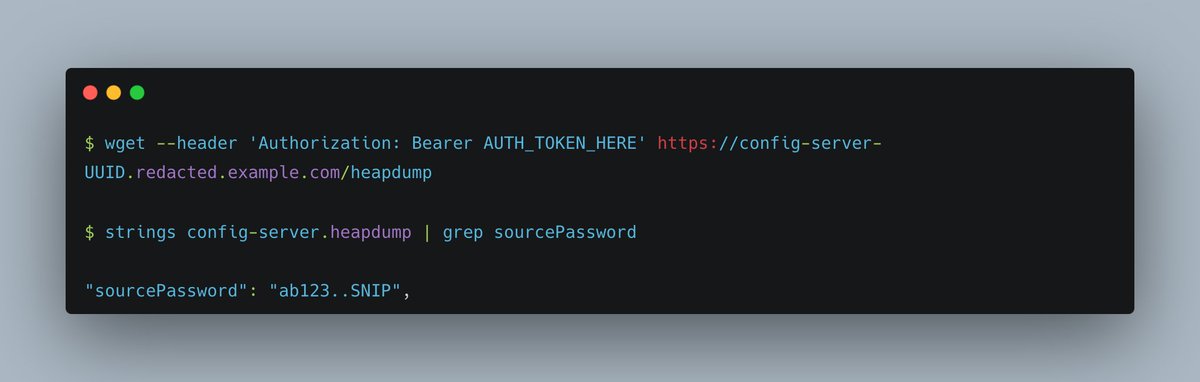
I grabbed the password using the /heapdump endpoint:


And the private key for the user.
I grabbed the password using the /heapdump endpoint:
10. I checked if the credentials were valid:
$ curl -u gops:abc123...
They were.
I could now access 30+ Github Orgs.
And I had read/write access to hundreds of repositories. github.example.com/api/v3/user

$ curl -u gops:abc123...
They were.
I could now access 30+ Github Orgs.
And I had read/write access to hundreds of repositories. github.example.com/api/v3/user

11. I reported it to their bug bounty program.
Unfortunately didn't get a cool new car 😢
But I guess $5,000 wasn't too bad.
Unfortunately didn't get a cool new car 😢
But I guess $5,000 wasn't too bad.
• • •
Missing some Tweet in this thread? You can try to
force a refresh