
How to get URL link on X (Twitter) App

 1. Try other URL schemes:
1. Try other URL schemes:

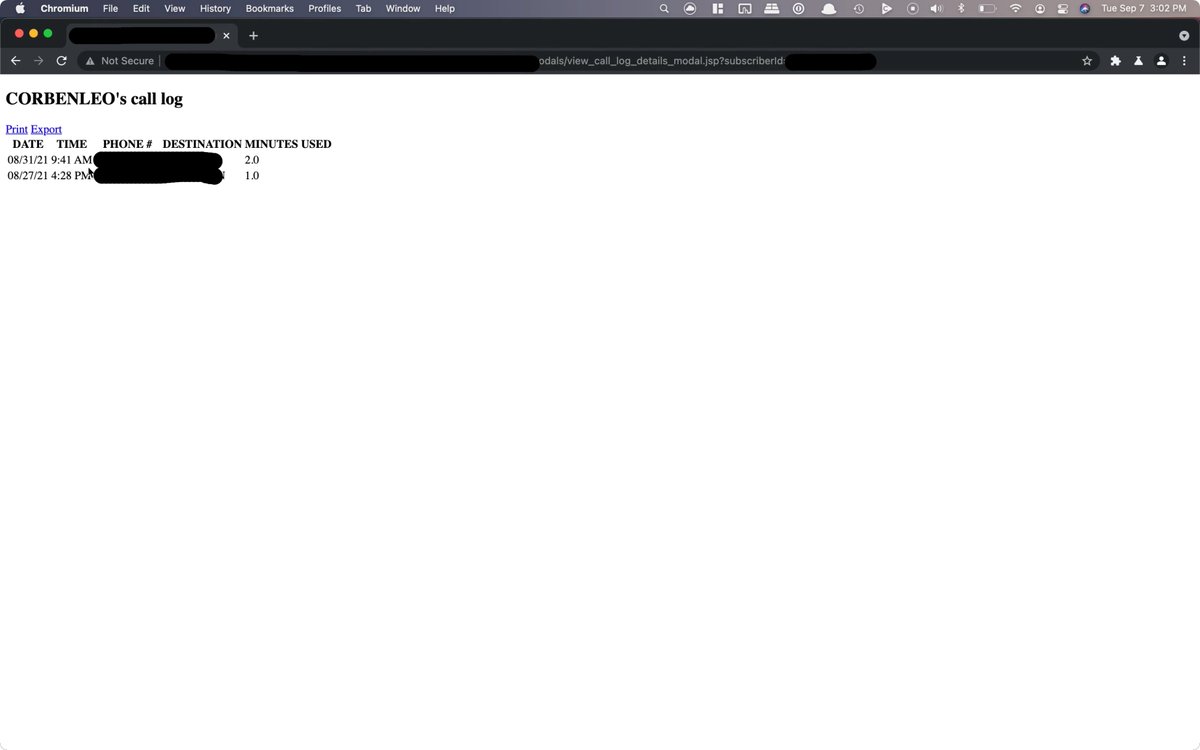
 1. I came across an Army server running ASP .NET
1. I came across an Army server running ASP .NET
 1. I started with reconnaisance:
1. I started with reconnaisance:
https://twitter.com/hacker_/status/1512552850831851531






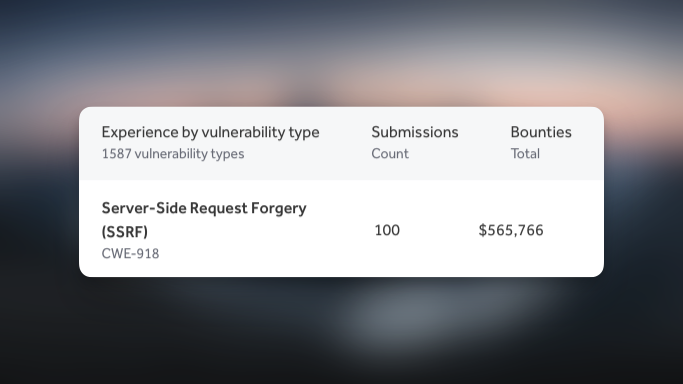
 1/ It began with a bug bounty program.
1/ It began with a bug bounty program.