Here is an updated chart following further research into the attempts by Ilya Medvedovsky to obscure his attempts to avoid sanctions imposed by the US DOT on his companies Digital Security (DSEC), ERPScan and Embedi that we first highlighted in
🧵1/9

🧵1/9
https://twitter.com/cyber_watchers/status/1694670973960941739
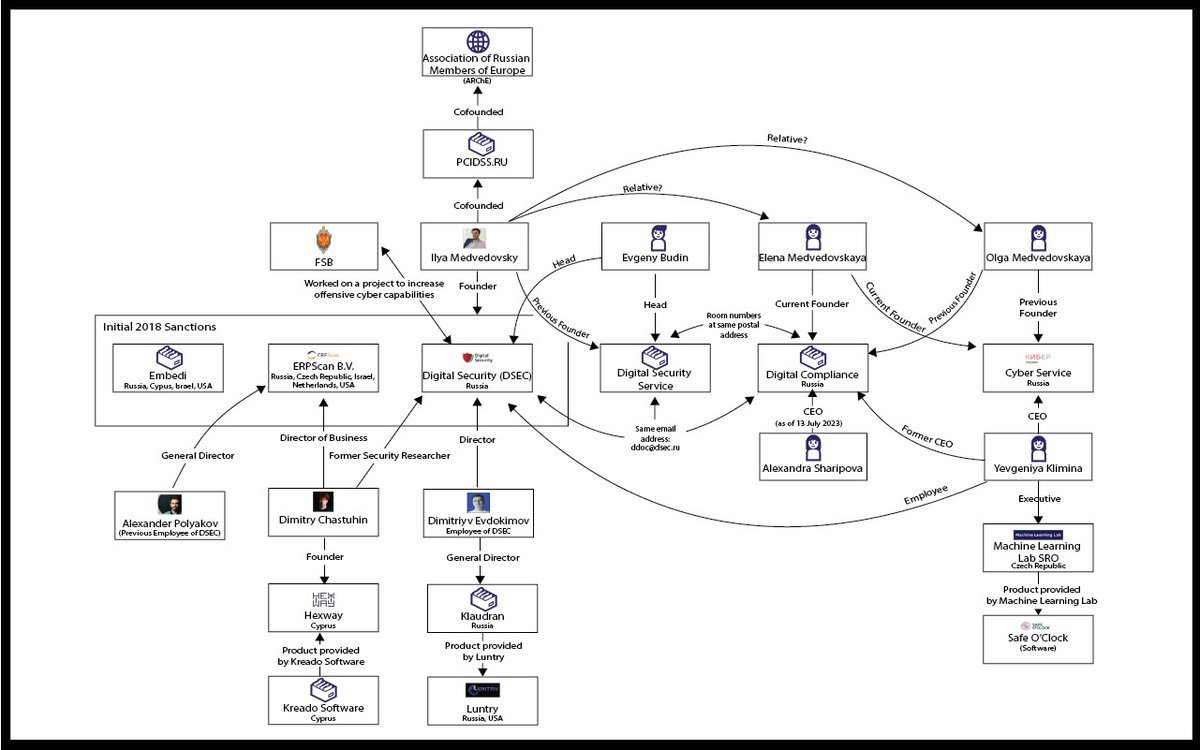
As you can see, we have a new individual that has links to the subject companies. Dmitriy Chastuhin is a security analyst specializing in SAP, who has appeared as a speaker at multiple conferences when Director of Business Application Pen testing at ERPScan. 2/9 

In 2011 he also attended the Zero Nights hacker conference as a security researcher from DSEC and in 2014 spoke at CONFIDENCE 2014 representing DSEC. In 2019 Chastuhin founded Hexway and is the self proclaimed CEO. 3/9
Hexway advertises products such as their Pentest as a Service (PTaas) platform, referred to as "Hive" and "Apiary" by the company, and ASOC solution, "Vampy", which is a "universal DevSecOps platform to simplify vulnerability management". 4/9
Previously on , Hexway was provided by Kreado Software Limited, a business entity registered in Cyprus. 5/9Hexway.io
This connection was very recently removed from the website following our last post. It appears that DSEC is further trying to obfuscate their reach by removing names from their products. 6/9




We have also discovered that the contact email address for Digital Compliance, Digital Security Services and DSEC is the same, ddoc@dsec.ru. Company records show that Digital Compliance and Cyber Service are "Related/Connected Persons". 7/9
Evgeny Budin is listed as the Head of both DSEC and Digital Security Services. DSEC and Digital Security Services are listed as "Related/Connected Persons". 8/9
Digital Compliance and Digital Security Services have room numbers located at the same postal address, suggesting a strong connection between the two companies. 9/9
@threadreaderapp unroll
• • •
Missing some Tweet in this thread? You can try to
force a refresh









