
How to get URL link on X (Twitter) App



 According to Treasury press release sm0401 at the time this was in response to Russian state sponsored cyber-attacks alleged to have been targeting critical infrastructure.
According to Treasury press release sm0401 at the time this was in response to Russian state sponsored cyber-attacks alleged to have been targeting critical infrastructure.

 The Kvant Scientific Research Institute was founded in 1978 and though officially civilian was under
The Kvant Scientific Research Institute was founded in 1978 and though officially civilian was under

 InfoTeks has been sanctioned by the Council of the European Union for its work in creating systems and tools for Russian Security Services. In addition, the company has also been indicted by the US for enabling the malicious activity of Russian Cyber actors.
InfoTeks has been sanctioned by the Council of the European Union for its work in creating systems and tools for Russian Security Services. In addition, the company has also been indicted by the US for enabling the malicious activity of Russian Cyber actors.

 In 2021 the US indicted an employee of the institute, Evgeny Gladkikh, for installing TRITON malware on a safety system of global energy facilities and using techniques designed to enable future damage with potentially catastrophic effects on a Shneider Electric safety system.
In 2021 the US indicted an employee of the institute, Evgeny Gladkikh, for installing TRITON malware on a safety system of global energy facilities and using techniques designed to enable future damage with potentially catastrophic effects on a Shneider Electric safety system.

 Between 2005 and 2007 the company was called FSUE Atlas of the Federal State Security Service and, according to Government documentation, under the supervision of the FSB.
Between 2005 and 2007 the company was called FSUE Atlas of the Federal State Security Service and, according to Government documentation, under the supervision of the FSB.

 According to freely available Federal Tax Service information the company was founded on 17 July 2003 by the Foreign Intelligence Service of the Russian Federation, better known as the SVR.
According to freely available Federal Tax Service information the company was founded on 17 July 2003 by the Foreign Intelligence Service of the Russian Federation, better known as the SVR. 
https://twitter.com/cyber_watchers/status/1694670973960941739
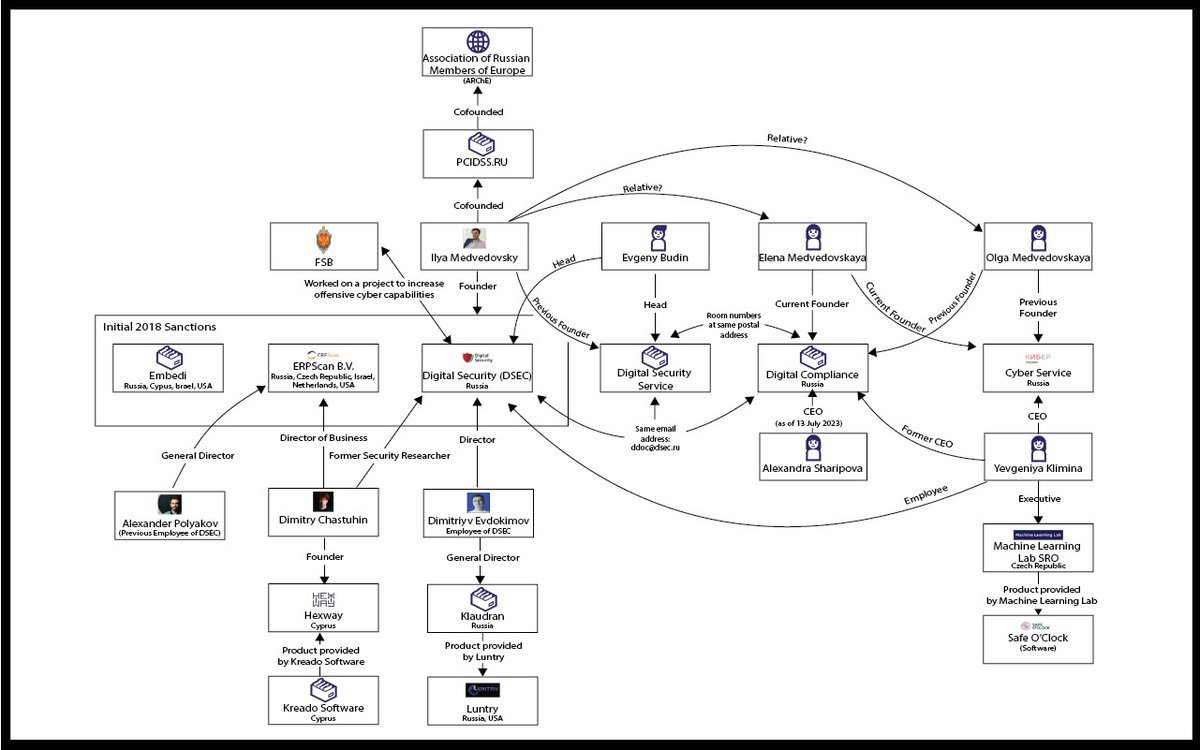
 As you can see, we have a new individual that has links to the subject companies. Dmitriy Chastuhin is a security analyst specializing in SAP, who has appeared as a speaker at multiple conferences when Director of Business Application Pen testing at ERPScan. 2/9
As you can see, we have a new individual that has links to the subject companies. Dmitriy Chastuhin is a security analyst specializing in SAP, who has appeared as a speaker at multiple conferences when Director of Business Application Pen testing at ERPScan. 2/9 

 Sanctions were imposded on DSEC because of work conducted on a project that would increase Russia's
Sanctions were imposded on DSEC because of work conducted on a project that would increase Russia's 
https://twitter.com/cyber_watchers/status/1646847570726080514
 From what we have heard he was head of his Department with some extra responsibilities supporting the Head of his section within the 85th GTsSS. Not the Deputy Head of the entire unit, as Cyber Resistance had stated.
From what we have heard he was head of his Department with some extra responsibilities supporting the Head of his section within the 85th GTsSS. Not the Deputy Head of the entire unit, as Cyber Resistance had stated.
https://twitter.com/cyber_watchers/status/1653763061189148677Despite the mistakes made it may surprise you that Morenets still has a job in the #85thGTsSS, also known as #APT28 or Fancy Bear. It is our understanding that he is in charge of a Directorate involved in Cyber espionage.

 He may look familiar to you? Here he is in our tweet of congratulations to Yevgeny Serebryakov, on GRU day, for his part in the failed attempted hack of the OPCW HQ in The Hague.
He may look familiar to you? Here he is in our tweet of congratulations to Yevgeny Serebryakov, on GRU day, for his part in the failed attempted hack of the OPCW HQ in The Hague.https://twitter.com/cyber_watchers/status/1588786233525739520
https://twitter.com/cyber_watchers/status/1547561370899558400?s=20&t=wsxe2Z21g7Pw9Cr0MMnTAgDrovorub-A1 was originally developed for the GRU 85th Main Special Service Center (85th GTsSS, в/ч 26165) and dubbed the 'Swiss Army Knife' for hacking Linux.