I spoke at @MSFTBlueHat last week.
➡️
I will follow up with a link to the recording when it is posted.
Some highlights from my talk below👇👇👇github.com/JohnLaTwC/Shar…
➡️
I will follow up with a link to the recording when it is posted.
Some highlights from my talk below👇👇👇github.com/JohnLaTwC/Shar…
I talked about while it is often romanced that offense has a richer toolset compared to the singular metaphor for defense ("the shield"). Defense has many creative ideas within it as well.




Some foundational concepts for defenders include:
1. Every contact leaves a trace...in a log
2. Defense involves the process of mapping attacker activity to its traces in logs
3. Attacks can take place on many logical layers
4. How essential pivoting is to navigating your data




1. Every contact leaves a trace...in a log
2. Defense involves the process of mapping attacker activity to its traces in logs
3. Attacks can take place on many logical layers
4. How essential pivoting is to navigating your data




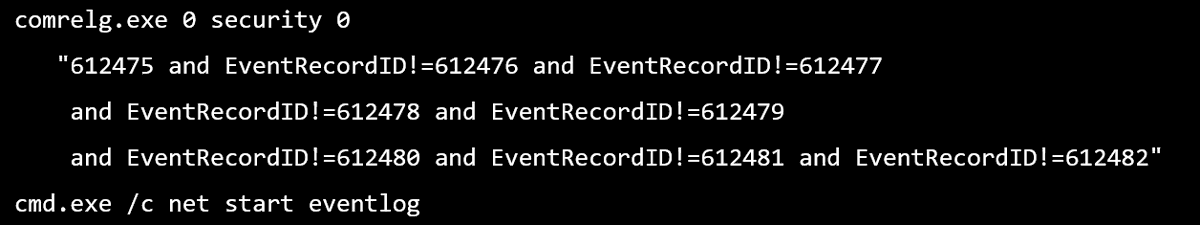
I talked about the ability to find breaches by time-traveling through logs. Some attacker techniques may have fewer methods of expression (e.g. credential dumping, privileged group enumeration) and these serve as important detection "bottlenecks" in the kill chain. 

I also talked about the importance of building trust as defenders and how it can be the fastest way to accomplish things. 

Often our toughest problems at work are not technical, but rather inter-team issues. I gave some tips on dealing with these. 

Finally, I talked about the importance of staying sane, focusing on your health, and having good work/life boundaries. 

When the video for the talk is posted, I will link it here.
Thx to @ItsReallyNick for the concept of bottlenecks
Thx to @MSwannMSFT for discussion of many of these topics on our PCT hike.
The audio 🎙️of this talk can be found at the @bluehat podcast: podcasts.apple.com/us/podcast/blu…
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter