What are HAR files?
A HAR file is a recording of your current session & includes all web traffic including secrets & tokens.
Admins usually share these files with customer support when troubleshooting issues.
Here's a thread on how you can handle .har files safely.
🧵⬇️
A HAR file is a recording of your current session & includes all web traffic including secrets & tokens.
Admins usually share these files with customer support when troubleshooting issues.
Here's a thread on how you can handle .har files safely.
🧵⬇️
Exporting HAR files
There are a few ways to record your session to create HAR files. You might need to use different tools depending on what you are recording.
→ Browser
Every modern browser lets you export an HAR file of the current tab's session from the Network tab.
There are a few ways to record your session to create HAR files. You might need to use different tools depending on what you are recording.
→ Browser
Every modern browser lets you export an HAR file of the current tab's session from the Network tab.

→ Desktop
Sometimes you might need to troubleshoot a non-browser-based app, for example a desktop app like Outlook or a CLI or PowerShell script.
Your admins are usually asked to use an app like Fiddler that adds a system proxy to capture all the web traffic on the desktop.
Sometimes you might need to troubleshoot a non-browser-based app, for example a desktop app like Outlook or a CLI or PowerShell script.
Your admins are usually asked to use an app like Fiddler that adds a system proxy to capture all the web traffic on the desktop.

HAR files and session recordings are important tools to help troubleshoot issues, so they are not going away any time soon.
Here are a few practical tips you can take to reduce your risk when sharing session recordings.
Here are a few practical tips you can take to reduce your risk when sharing session recordings.
Tip #1: Capture non-production traffic
Try to repro the issue in a non-production environment. This way, even if the session tokens fall in the wrong hands, the impact will be limited to non-prod.
I've shared previously on how to set up a mature model.
Try to repro the issue in a non-production environment. This way, even if the session tokens fall in the wrong hands, the impact will be limited to non-prod.
I've shared previously on how to set up a mature model.
https://x.com/merill/status/1683783494324097025?s=20
Tip #2: Avoid using desktop session recording
Avoid recording with tools like Fiddler and ProxyMan that capture all the desktop traffic. Where possible use the browser session recording. This limits the scope to the active browser tab.
Avoid recording with tools like Fiddler and ProxyMan that capture all the desktop traffic. Where possible use the browser session recording. This limits the scope to the active browser tab.
The desktop capture tools on the other hand, capture the traffic and tokens of every single app you have open on your desktop.
If you do need to use them, make sure you filter and export just the selected sessions, instead of 'All Sessions'.
Alternatively use a remote session.
If you do need to use them, make sure you filter and export just the selected sessions, instead of 'All Sessions'.
Alternatively use a remote session.
Tip #3: Sanitize the session archive of all the secrets.
Most vendors ask you to review the trace and remove secrets.
This is easier said than done.
Here's none other than @ericlaw (who created Fiddler) answering a post asking how to remove passwords from a Fiddler trace.![Removing headers that might contain passwords is easy. Removing POST body data or URL QueryString data that might contain passwords is nearly impossible to do reliably, because there's no standard for how such data is encoded. public static ToolsAction("Remove PII") function doClean() { var arrSess: Session[] = FiddlerApplication.UI.GetAllSessions(); for (var i: int=0; i<arrSess.Length; i++) { arrSess[i].RequestHeaders.RemoveRange(["Cookie", "Authorization", "Proxy-Authorization"]); a...](/images/1px.png)
Most vendors ask you to review the trace and remove secrets.
This is easier said than done.
Here's none other than @ericlaw (who created Fiddler) answering a post asking how to remove passwords from a Fiddler trace.
![Removing headers that might contain passwords is easy. Removing POST body data or URL QueryString data that might contain passwords is nearly impossible to do reliably, because there's no standard for how such data is encoded. public static ToolsAction("Remove PII") function doClean() { var arrSess: Session[] = FiddlerApplication.UI.GetAllSessions(); for (var i: int=0; i<arrSess.Length; i++) { arrSess[i].RequestHeaders.RemoveRange(["Cookie", "Authorization", "Proxy-Authorization"]); a...](https://pbs.twimg.com/media/F9FGMYOaoAAf3tA.jpg)
Having said that Google does provide a HAR Analyzer to help remove some of the common types of secrets. 

Click the incognito icon to download a copy of the HAR file that has been stripped of tokens and other sensitive data.
Note: At the time of writing, the Google HAR Analyzer does all the processing locally in the browser and does not send the file to an external server.
Note: At the time of writing, the Google HAR Analyzer does all the processing locally in the browser and does not send the file to an external server.
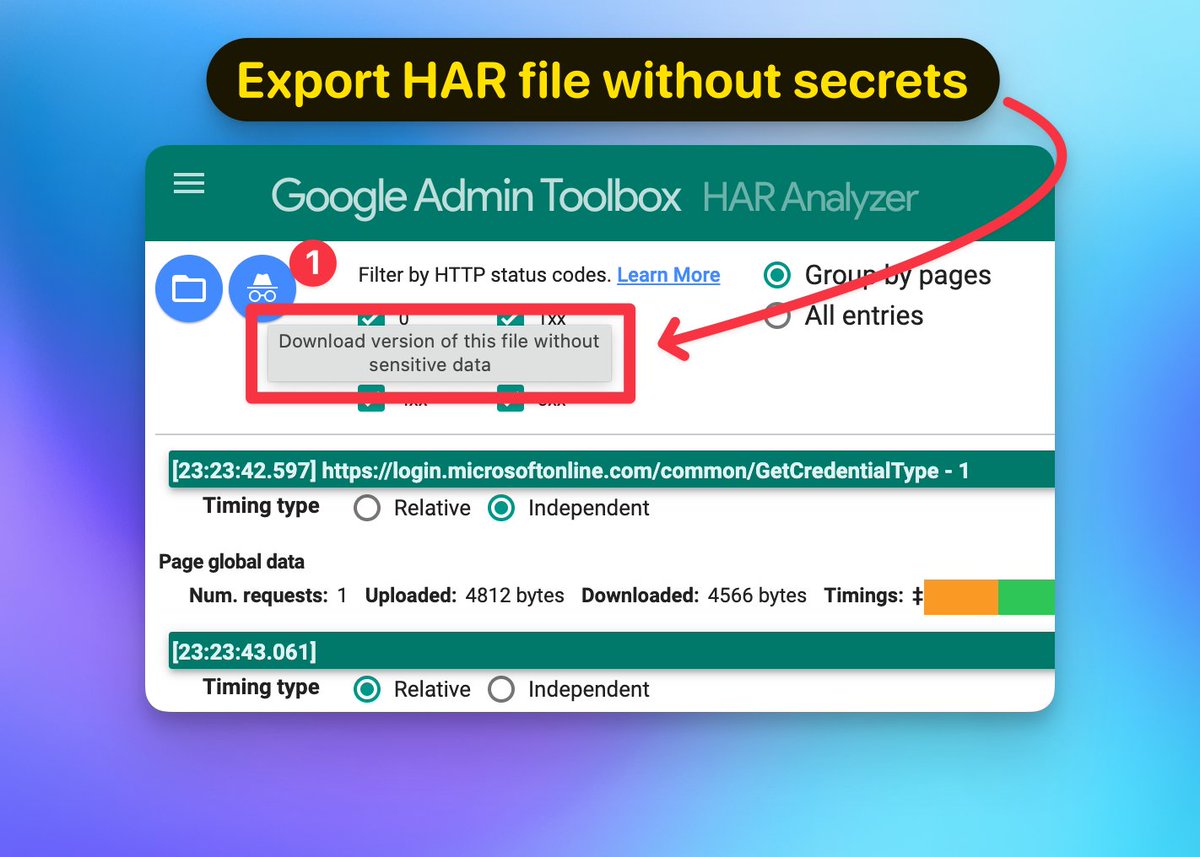
It's best to perform a manual review to make sure the HAR Analyzer did not miss any secrets.
-----
Note: The next few tips are specific to Microsoft Entra ID customers. I'll talk about what Microsoft admins can do to protect their tenant from token theft/replay.
-----
Note: The next few tips are specific to Microsoft Entra ID customers. I'll talk about what Microsoft admins can do to protect their tenant from token theft/replay.
Tip #4: In Microsoft Entra ID enable Privileged Identity Management (PIM) to ensure privileged sessions are short lived.
With PIM enabled and time-based, approval-based role activation, you reduce the surface area and effectives of stolen tokens.
With PIM enabled and time-based, approval-based role activation, you reduce the surface area and effectives of stolen tokens.

Tip #5: Limit admin session duration
NIST recommends a maximum 12-hour session lifetime for admins.
I shared recently on how you can do this with Entra ID.
NIST recommends a maximum 12-hour session lifetime for admins.
I shared recently on how you can do this with Entra ID.
https://x.com/merill/status/1714032178911433144?s=20
While the previous post was about the admin portal, it's better to apply these controls to All Cloud Apps accessed by admins. 
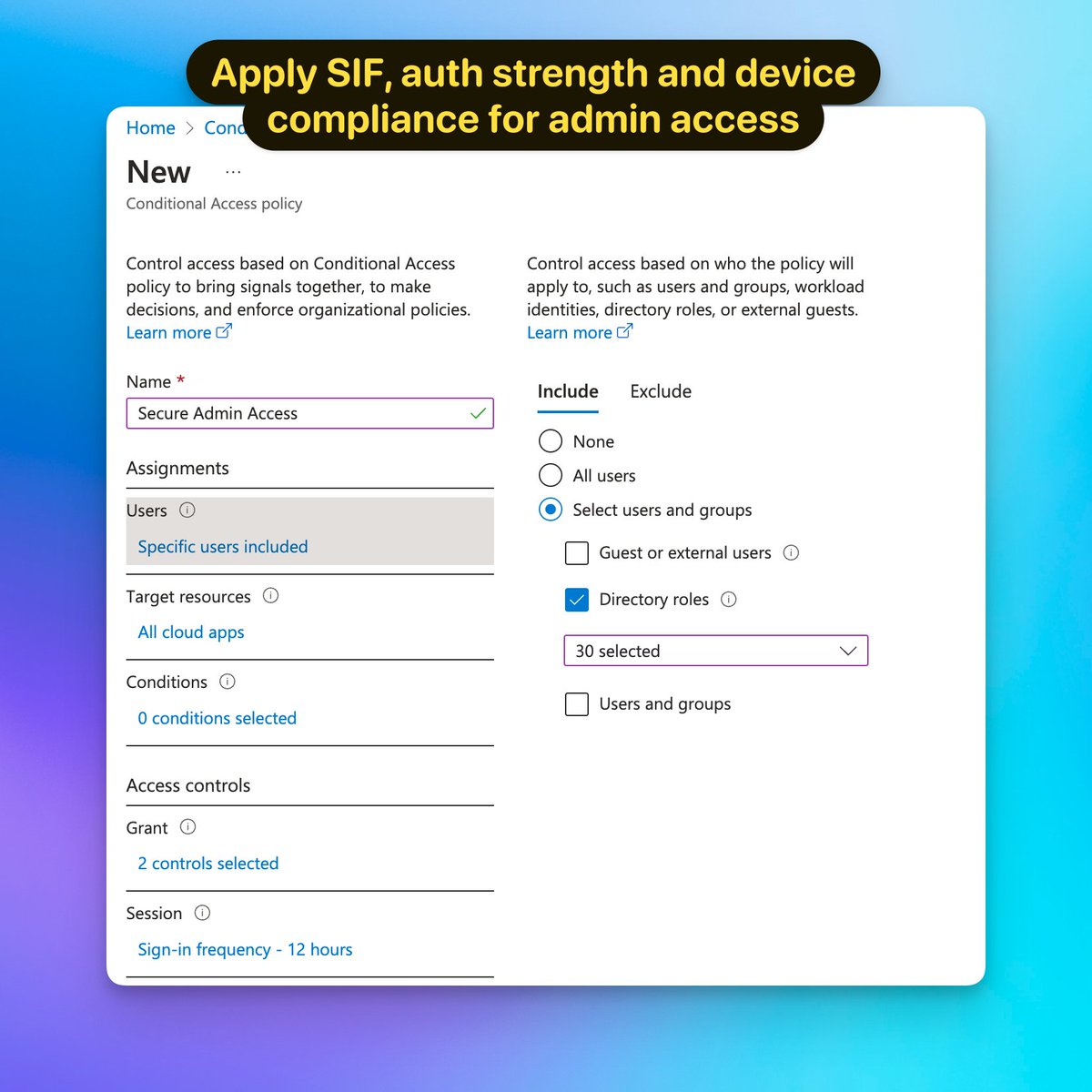
Tip #6: Apply Token Protection conditional access policy for admin access where possible.
Note: This feature is currently in preview and is limited to Exchange and SharePoint and currently blocks access from PowerShell, also requires P2.
Note: This feature is currently in preview and is limited to Exchange and SharePoint and currently blocks access from PowerShell, also requires P2.

Tip #7: Apply Risk based sign in conditional access policy
Entra ID Protection logs anomalous token usage to the logs and can also be used in CA policies to auto-remediate.
Entra ID Protection logs anomalous token usage to the logs and can also be used in CA policies to auto-remediate.

Tip #8: @reprise_99 shared an epic thread on everything tokens including posts from @JeffreyAppel7, @samilamppu, @Thomas_Live, @SantasaloJoosua, @fabian_bader, @_dirkjan, @DrAzureAD and @424f424f
Bookmark and read them all!
Bookmark and read them all!
https://x.com/reprise_99/status/1698607330513076674?s=20
Have I missed anything? Let me know.
A quick note. None of us are immune from token theft and there is a lot we need to do to raise awareness about the measures that can be taken to reduce the impact.
It is in this spirit that I'm sharing this thread.
A quick note. None of us are immune from token theft and there is a lot we need to do to raise awareness about the measures that can be taken to reduce the impact.
It is in this spirit that I'm sharing this thread.
• • •
Missing some Tweet in this thread? You can try to
force a refresh