Okta got hacked. Leading to impact for CloudFlare, 1Password, and BeyondTrust.
Here's everything we know about it:
Here's everything we know about it:
Okta’s support system was compromised, allowing unauthorized access to sensitive files uploaded by customers.
Notably, Okta did not discover the breach themselves; it was independently detected by BeyondTrust and Cloudflare.
Notably, Okta did not discover the breach themselves; it was independently detected by BeyondTrust and Cloudflare.

BeyondTrust detected an identity-centric attack on October 2, 2023, which led them to believe that Okta’s support system was compromised.
They alerted Okta, but it took until October 19 for Okta to confirm the breach.
They alerted Okta, but it took until October 19 for Okta to confirm the breach.

Cloudflare discovered attacks traced back to Okta on October 18, 2023. They were able to contain the attack, ensuring no customer information or systems were impacted.
Cloudflare contacted Okta about the breach before Okta had notified them.
Cloudflare contacted Okta about the breach before Okta had notified them.
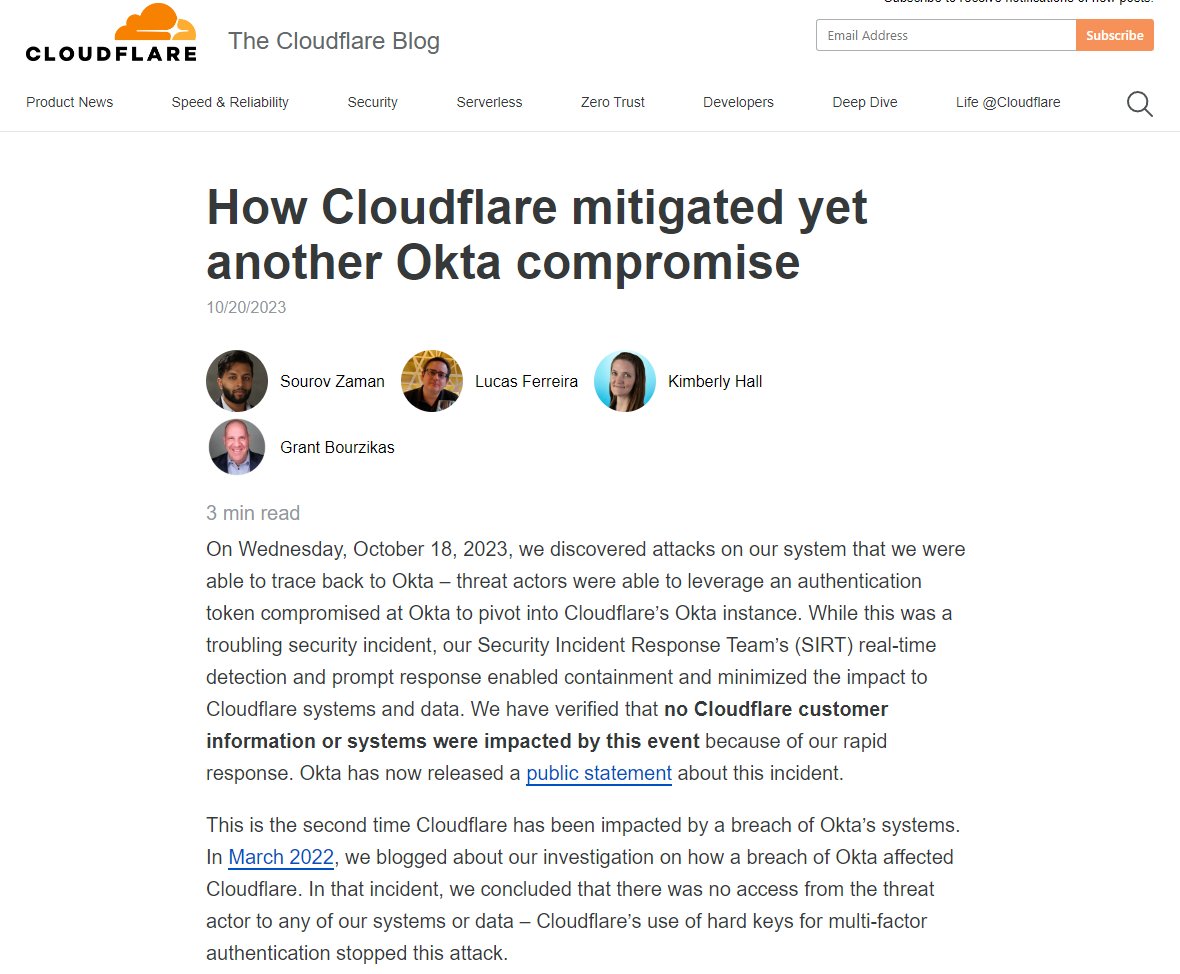
1Password has released an incident report that goes into a lot of detail about what they saw and how they responded. 

I'm a bit concerned that a privileged member of 1Password staff's endpoint didn't have Yubikey enforced until post this incident.
And free version of Malwarebytes also doesn't instill a ton of confidence.
And free version of Malwarebytes also doesn't instill a ton of confidence.

What led to the breach to begin with?
Speculation beyond "stolen credentials," but it all started on their support portal.
Okta support often requests customers to upload HTTP Archive (HAR) files for troubleshooting.
HAR files can contain sensitive info like session tokens.
Speculation beyond "stolen credentials," but it all started on their support portal.
Okta support often requests customers to upload HTTP Archive (HAR) files for troubleshooting.
HAR files can contain sensitive info like session tokens.

Upon being notified of the incident, Okta revoked any of the embedded session tokens.
Okta also advised users to sanitize HAR files by removing sensitive data before sharing.
Okta also advised users to sanitize HAR files by removing sensitive data before sharing.

My opinion: This HAR file sanitization is not the burden of the customer.
Okta needs to have a better process here.
Okta needs to have a better process here.

The breach primarily affected Okta’s support case management system.
Other systems, including the Okta service and the Auth0/CIC case management system, remain unaffected by this incident.
Other systems, including the Okta service and the Auth0/CIC case management system, remain unaffected by this incident.

It is reported that 170 of Okta's customers were impacted as a way to downplay the impact.
But we know about 3 of them and they are CloudFlare, BeyondTrust, and 1Password - not a small impact even if many Okta customers weren't involved.
But we know about 3 of them and they are CloudFlare, BeyondTrust, and 1Password - not a small impact even if many Okta customers weren't involved.

Okta has provided IoCs to help customers identify potential malicious activity.
This includes a list of IP addresses and user agents that might be associated with the malicious activities.
This includes a list of IP addresses and user agents that might be associated with the malicious activities.

Remaining Questions - Who are the other companies impacted?
Did they respond as well as CloudFlare, BeyondTrust, and 1Password?
Did they respond as well as CloudFlare, BeyondTrust, and 1Password?
Want to stay on top of news like this?
Join over 5k pros who trust me to give them what they need to know every week in cybersecurity:
vulnu.mattjay.com
Join over 5k pros who trust me to give them what they need to know every week in cybersecurity:
vulnu.mattjay.com
Sources: Beyond Trust Blog: beyondtrust.com/blog/entry/okt…
CloudFlare Blog - blog.cloudflare.com/how-cloudflare…
Okta announcement - sec.okta.com/harfiles
• • •
Missing some Tweet in this thread? You can try to
force a refresh