Helping Secure the Internet | Long Island elder emo surviving in ATX | Expect: infosec current events, DFIR, appsec & cloudsec - and me!
11 subscribers
How to get URL link on X (Twitter) App


 The decision undoes a declaratory ruling that stated the 1994 Communications Assistance for Law Enforcement Act (CALEA) requires telecoms to secure networks from unlawful access and interception.
The decision undoes a declaratory ruling that stated the 1994 Communications Assistance for Law Enforcement Act (CALEA) requires telecoms to secure networks from unlawful access and interception.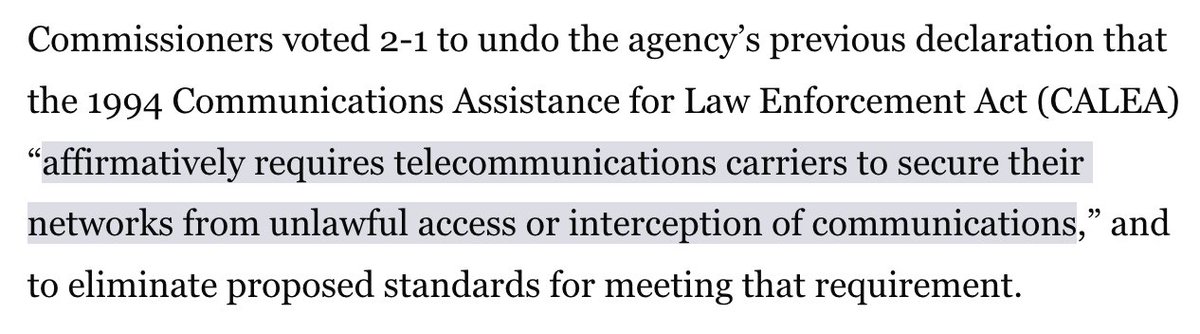


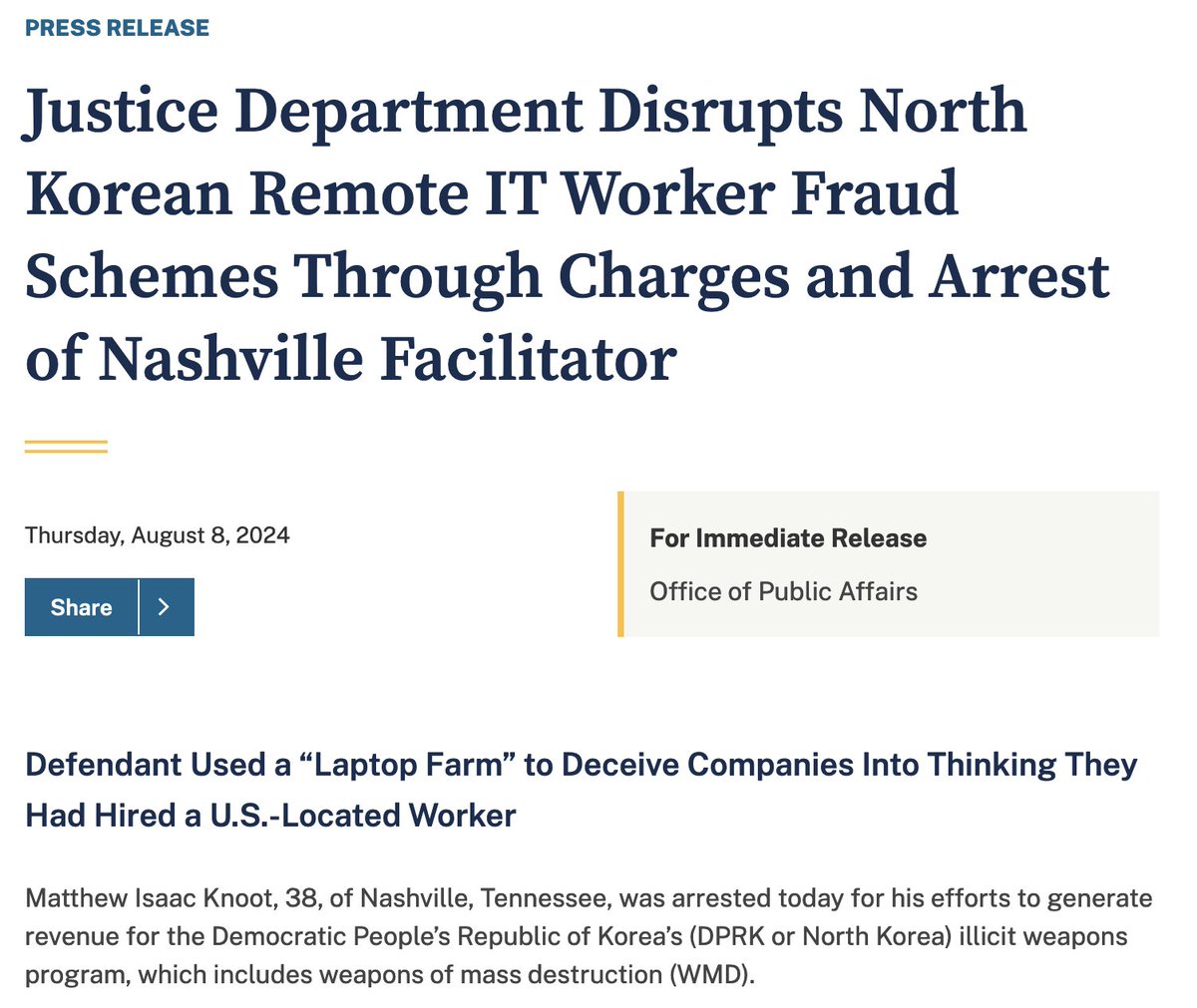
 Former L3Harris/Trenchant GM Peter Williams charged with stealing trade secrets. DOJ claims he made $1.3M from the sale.
Former L3Harris/Trenchant GM Peter Williams charged with stealing trade secrets. DOJ claims he made $1.3M from the sale. 

 Initial contact came to @JoeTidy via Signal from "Syndicate" offering 15% of potential ransom payment for access to BBC systems.
Initial contact came to @JoeTidy via Signal from "Syndicate" offering 15% of potential ransom payment for access to BBC systems.

 Key context: This follows whistleblower Daniel Berulis's disclosure about ~10GB of data exfiltrated from NLRB's NxGen system.
Key context: This follows whistleblower Daniel Berulis's disclosure about ~10GB of data exfiltrated from NLRB's NxGen system.

 Inverters already need remote access for firmware updates, so utilities put them behind firewalls.
Inverters already need remote access for firmware updates, so utilities put them behind firewalls.
 TeleMessage creates modified versions of Signal/WhatsApp/Telegram that archive messages for gov agencies.
TeleMessage creates modified versions of Signal/WhatsApp/Telegram that archive messages for gov agencies.

 Who’s the whistleblower?
Who’s the whistleblower?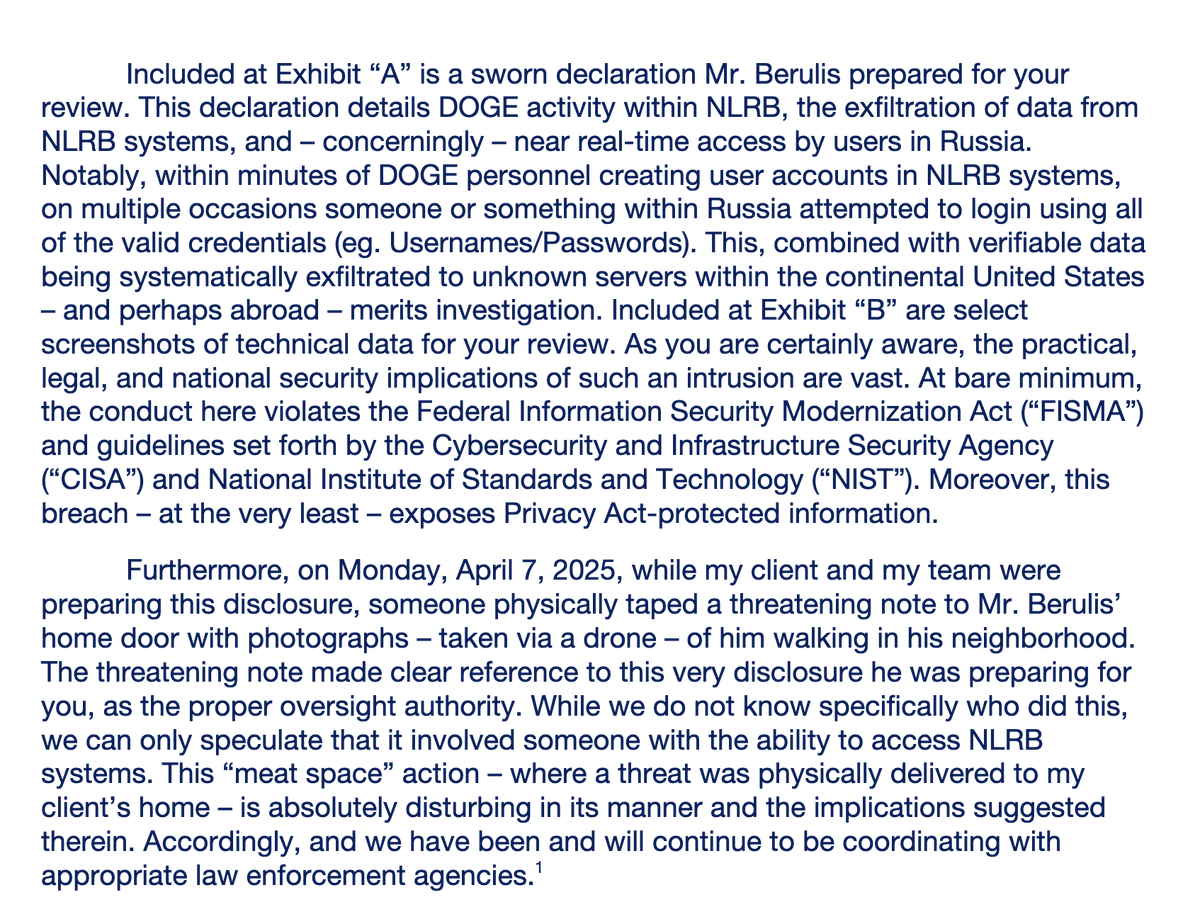









 First up -
First up - 

 The bug seems to impact all Kias right now and the researchers didn't disclose a PoC since it isn't fixed but it's been 90 days since disclosure so they're talking about it.
The bug seems to impact all Kias right now and the researchers didn't disclose a PoC since it isn't fixed but it's been 90 days since disclosure so they're talking about it.