As part of our new report on RTB as a security threat and previously unreported, we reveal 'Patternz', a private mass surveillance system that harvests digital advertising data on behalf of 'national security agencies'.
5 billion user profiles, data from 87 adtech firms. Thread:
5 billion user profiles, data from 87 adtech firms. Thread:

'Patternz' in the report by @johnnyryan and me published today:
Patternz is operated by a company based in Israel and/or Singapore. I came across it some time ago, received internal docs. Two docs are available online.
Some more details in this thread. iccl.ie/wp-content/upl…

Patternz is operated by a company based in Israel and/or Singapore. I came across it some time ago, received internal docs. Two docs are available online.
Some more details in this thread. iccl.ie/wp-content/upl…

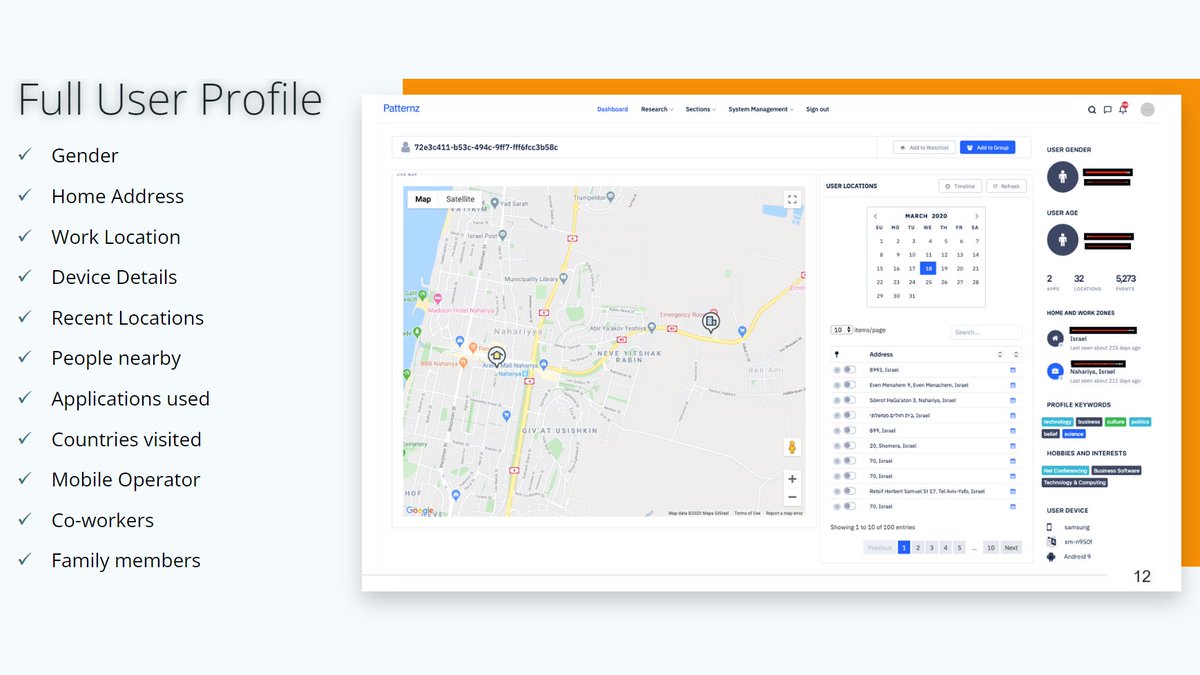
Here's how Patternz can be used to track and profile individuals, their location history, home address, interests, information about 'people nearby', 'co-workers' and even 'family members', according to information available online:
isasecurity.org/patternz
web.archive.org/web/2021062210…

isasecurity.org/patternz
web.archive.org/web/2021062210…
Most of today's digital advertising is based on real-time bidding (RTB) which involves uncontrolled data flows to many entities who bid on user profiles.
Patternz states its system is "built on the extensive knowhow of operating a Realtime bidding platform for the last 5 years".
Patternz states its system is "built on the extensive knowhow of operating a Realtime bidding platform for the last 5 years".

Patternz claims to operate a "fully commercial and operational AdTech arm that actually trades in media" to obtain RTB data from 87 ad exchanges and SSPs.
An earlier version of its website named Google, Yahoo and adtech firms like MoPub, AdColony and OpenX as data sources.
An earlier version of its website named Google, Yahoo and adtech firms like MoPub, AdColony and OpenX as data sources.

According to the source linked above, the Patternz system is sold by ISA Security, an Israeli firm.
Here's another publicly available doc from Sovereign Systems, a Singapore-based firm with offices in UAE, New Zealand and Ireland:
sovsys.co/wp-content/upl…
web.archive.org/web/2023100318…

Here's another publicly available doc from Sovereign Systems, a Singapore-based firm with offices in UAE, New Zealand and Ireland:
sovsys.co/wp-content/upl…
web.archive.org/web/2023100318…

Patternz claims to operate "6 data centers around the world" for real-time data collection.
I've seen internal Patternz docs which describe the IAB's OpenRTB protocol in digital advertising in detail. They also explain that the smartphone became a 'de-facto tracking bracelet'.
I've seen internal Patternz docs which describe the IAB's OpenRTB protocol in digital advertising in detail. They also explain that the smartphone became a 'de-facto tracking bracelet'.

Although we cannot verify the claims, the documents suggest that Patternz turns the intrusive global surveillance infrastructure that has been built to serve digital advertising into a system for mass+targeted surveillance for national security agencies and perhaps other actors.
I think it's the best-documented example of how personal data that is routinely processed to provide consumer services and enable digital advertising is exploited for completely unrelated purposes at scale.
The commercial data industry, publishers and advertisers are complicit.
The commercial data industry, publishers and advertisers are complicit.
Whenever someone visits a website or uses a mobile app that displays digital ads, profile data is broadcasted to dozens or hundreds of companies and other entities.
This occurs billions and billions of times a day. Billions of people are affected, hundreds of millions in Europe.
This occurs billions and billions of times a day. Billions of people are affected, hundreds of millions in Europe.

It was a deliberate decision to create the RTB system in this way, and even worse, to delay GDPR enforcement and lobby hard against criticism for years.
Thousands of adtech firms and myriads of publishers and advertisers have no control over who they share personal data with.
Thousands of adtech firms and myriads of publishers and advertisers have no control over who they share personal data with.
As such, the digital advertising industry, and specifically Google and the IAB, enable the worst possible kind of decontextualized misuse of everyone's personal information.
Of course, it's ridiculous to believe that only 'Western' state actors would access RTB bidstream data.
Of course, it's ridiculous to believe that only 'Western' state actors would access RTB bidstream data.

When they have no control over who they share data with they cannot have a legal basis to do so under the GDPR.
GDPR enforcement is broken. Otherwise, uncontrolled personal data sharing via the RTB bidstream would have been shut down years ago. Regulators must take action now.
GDPR enforcement is broken. Otherwise, uncontrolled personal data sharing via the RTB bidstream would have been shut down years ago. Regulators must take action now.
RTB does not only undermine the rights of hundreds of millions of Europeans and trust into digital tech at large, but is also a national security threat.
In our report published today we call for the European Commission, ENISA and EEAS to take action:
iccl.ie/wp-content/upl…


In our report published today we call for the European Commission, ENISA and EEAS to take action:
iccl.ie/wp-content/upl…


To my knowledge, this 2020 Forbes article provided evidence for the first time that a firm who sells surveillance tech to governments was running its own DSP to harvest personal data from RTB bid requests in digital advertising. Not much detail, though:
https://twitter.com/WolfieChristl/status/1337409116470472704
This recent Bloomberg article provided more detail about Rayzone, a shady surveillance vendor that reportedly acquired data from the RTB bidstream by operating a DSP and directly owns two adtech firms (, ):
impulsedsp.com
oxillon.com
bloomberg.com/news/articles/…
impulsedsp.com
oxillon.com
bloomberg.com/news/articles/…
This recent WSJ article by @ByronTau found that a shady consumer data broker accessed bidstream data via SSPs and ad exchanges like OpenX, AdColony and Smaato and sold it to surveillance contractors who sold it to US defense/intel agencies:
https://twitter.com/WolfieChristl/status/1712955510536696158
This Haaretz investigation addresses a number of firms that exploit advertising data for surveillance purposes and for targeted attacks on devices.
The article states that some surveillance firms are 'connected to ad firms' or even 'operate an ad firm':
haaretz.com/israel-news/20…
The article states that some surveillance firms are 'connected to ad firms' or even 'operate an ad firm':
haaretz.com/israel-news/20…
Ok, received a tip. It appears that 'Patternz' is closely affiliated or even identical to NUVIAD, an adtech firm, DSP and consumer data broker based in Israel.
Not only because of the apparent similarity of their promotional materials:
web.archive.org/web/2020051101…

Not only because of the apparent similarity of their promotional materials:
web.archive.org/web/2020051101…

Firms listed as Nuviad's data sources in 2020:
Google, MobPub (back then: Twitter), AOL/Yahoo, Smaato, OpenX, Amobee, Pulsepoint, Rubicon, Inneractive/Fyber (Digital Turbine), Avocarrot/MobFox (Glipsa, Germany), Axonix, Altitude Digital, Opera Mediaworks.
web.archive.org/web/2020051101…
Google, MobPub (back then: Twitter), AOL/Yahoo, Smaato, OpenX, Amobee, Pulsepoint, Rubicon, Inneractive/Fyber (Digital Turbine), Avocarrot/MobFox (Glipsa, Germany), Axonix, Altitude Digital, Opera Mediaworks.
web.archive.org/web/2020051101…
As of today, Google lists Nuviad as a vendor "eligible to receive bid requests compliant with US states privacy laws":
support.google.com/adsense/answer…
support.google.com/adsense/answer…
Btw. Patternz does not only offer monitoring based on advertising data, but also targeted attacks by sending "targeted messages, ads or trojans directly through the AdTech stack".
And, these 'profile keywords' and 'hobbies and interests' sections may refer to RTB segment info.


And, these 'profile keywords' and 'hobbies and interests' sections may refer to RTB segment info.


Some more pointers.
In 2017, the president of NUVIAD joined the board of Ability Inc. (), a spytech/surveillance firm specializing in tapping phones via SS7 (), which soon went down (employee arrests, NASDAQ delisting) /cc @iblametomsec.gov/Archives/edgar…
forbes.com/sites/thomasbr…
In 2017, the president of NUVIAD joined the board of Ability Inc. (), a spytech/surveillance firm specializing in tapping phones via SS7 (), which soon went down (employee arrests, NASDAQ delisting) /cc @iblametomsec.gov/Archives/edgar…
forbes.com/sites/thomasbr…
@iblametom The CEO of the Singapore-based firm Sovereign Systems, who sells Patternz according to its website, is quoted to have said that Sovereign Systems was a "front" for PICSIX (), an Israeli firm that sells all kinds of surveillance tech.
haaretz.com/world-news/asi…
pic-six.com




haaretz.com/world-news/asi…
pic-six.com




Xandr/Microsoft also lists Nuviad as a "partner which may receive Platform Data":
Here's Nuviad boasting about '2.5 billion user profiles' and 'analyzing over 700k ad opportunities every second'. From an Amazon AWS event in 2018:
docs.xandr.com/bundle/service…
de.slideshare.net/AmazonWebServi…

Here's Nuviad boasting about '2.5 billion user profiles' and 'analyzing over 700k ad opportunities every second'. From an Amazon AWS event in 2018:
docs.xandr.com/bundle/service…
de.slideshare.net/AmazonWebServi…

Investigative journalist? Would be great to get more solid evidence on who operates Patternz, links to other firms (spytech/adtech/Nuviad), resellers, clients.
You have insights into Nuviad or other firms (adtech, 'adint')? Reach out to trustworthy journalists, e.g. @josephfcox
You have insights into Nuviad or other firms (adtech, 'adint')? Reach out to trustworthy journalists, e.g. @josephfcox
Another public source confirms that Nuviad, the digital advertising firm, and Patternz, the secretive global mass surveillance tool, are identical.
In this video, Rafi Ton, the CEO of the adtech firm Nuviad, introduces himself as the 'CEO of Patternz':

In this video, Rafi Ton, the CEO of the adtech firm Nuviad, introduces himself as the 'CEO of Patternz':

The video includes a Patternz demo. An archived version should be soon available here:
It seems to be a sales pitch to a Peruvian firm and the government for covid tracking but it also addresses 'homeland security'.
Weird that this is publicly available.

It seems to be a sales pitch to a Peruvian firm and the government for covid tracking but it also addresses 'homeland security'.
Weird that this is publicly available.

There's talk about Peru's 'state of emergency' (2020/21/22?) and its military as a potential client.
The Patternz/Nuviad CEO also states that the Israeli 'security forces' were 'running' the platform, and an 'East European' country even linked Patternz with mobile operator data.
The Patternz/Nuviad CEO also states that the Israeli 'security forces' were 'running' the platform, and an 'East European' country even linked Patternz with mobile operator data.
According to the video, Patternz was originally 'designed and built' as a 'homeland security platform', for 'anti-riot and protesting'.
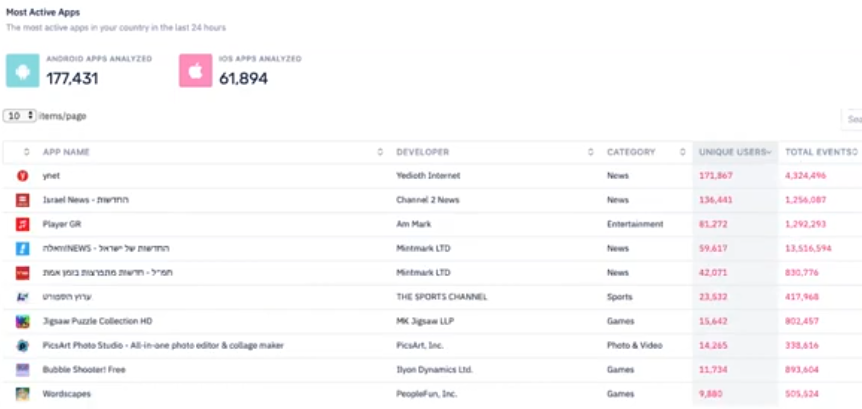
The system also shows apps which the location/profile data comes from. As behaviors from >100k apps are analyzed, it cannot be mobile SDK data.




The system also shows apps which the location/profile data comes from. As behaviors from >100k apps are analyzed, it cannot be mobile SDK data.



• • •
Missing some Tweet in this thread? You can try to
force a refresh