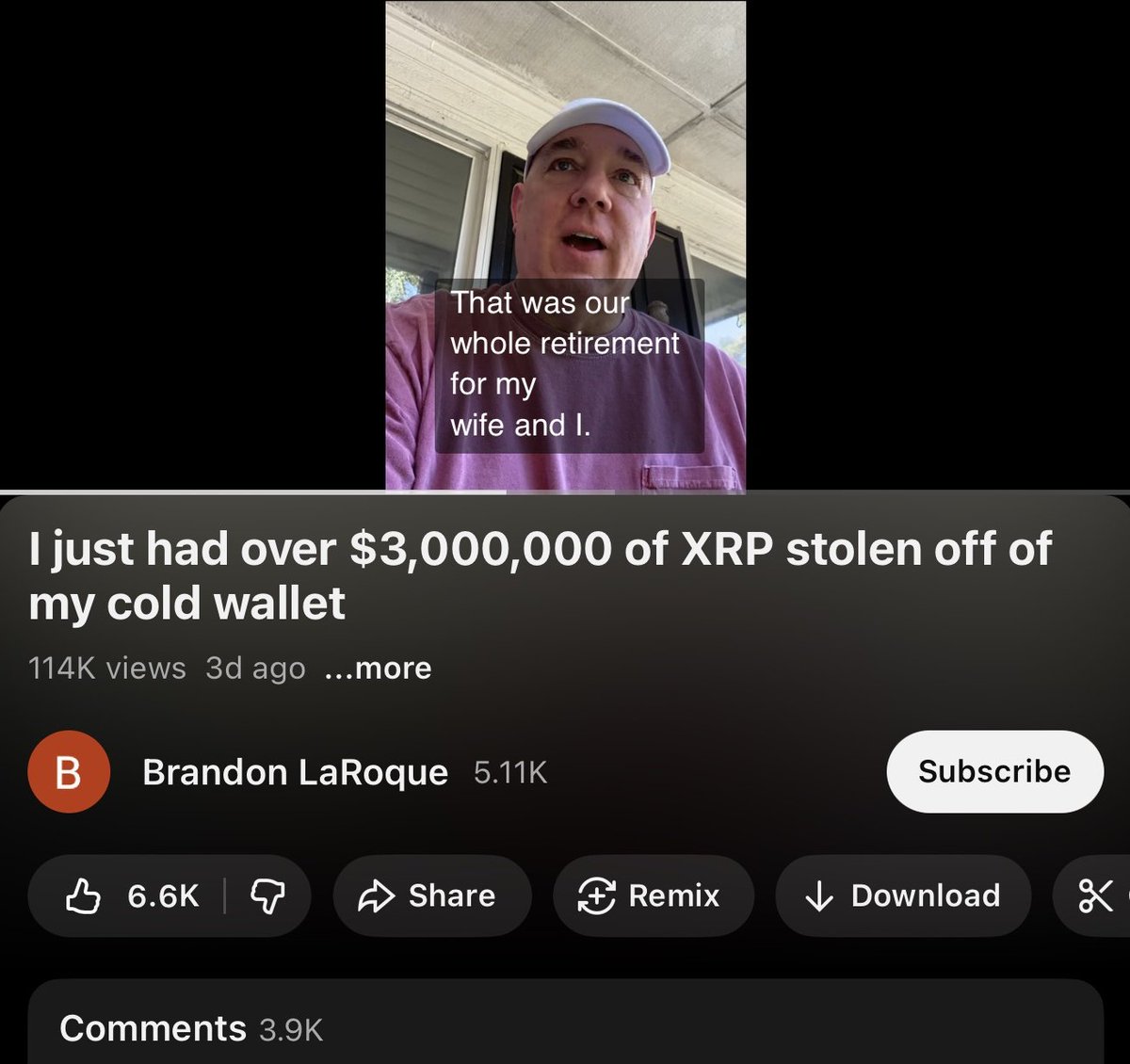
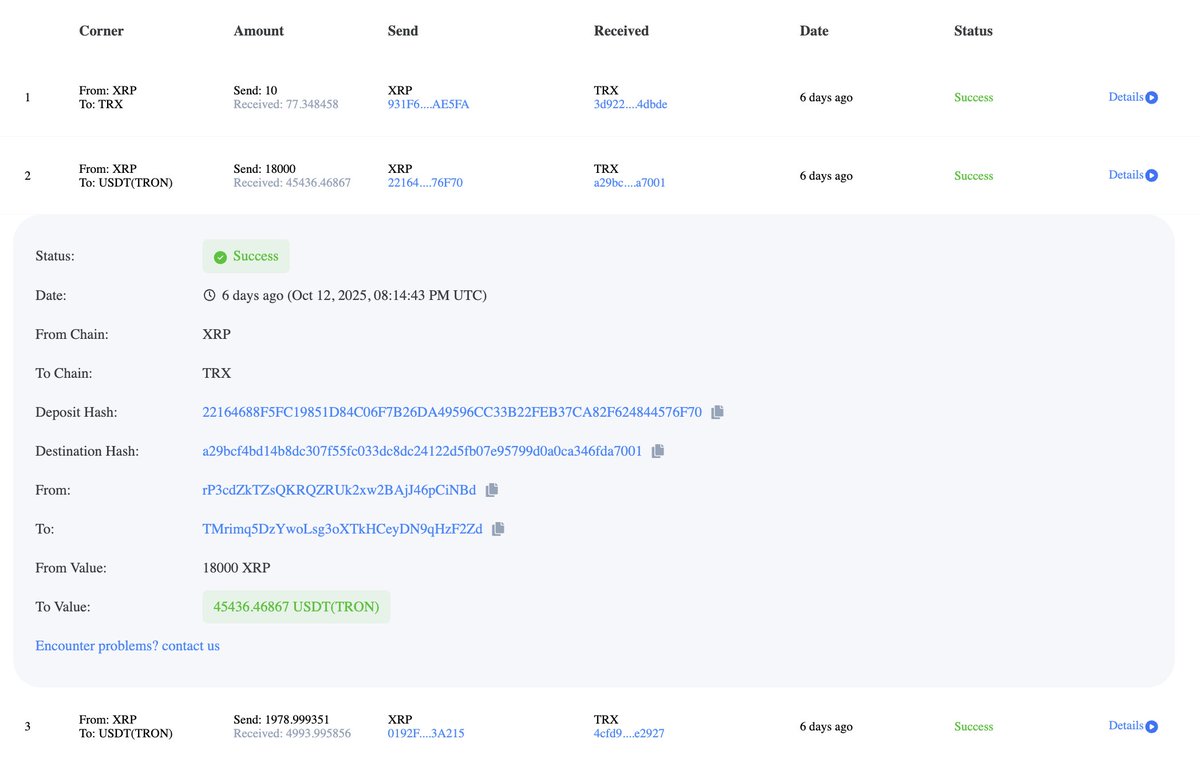
1/ Throughout this year I have been monitoring someone who has withdrawn 11,200+ ETH ($25M) from Tornado Cash and spent the majority of it on Magic The Gathering (MTG) trading cards.
Here’s my analysis of where the funds went and what the potential source of funds could be.
Here’s my analysis of where the funds went and what the potential source of funds could be.
2/ This person has withdrawn 110 X 100 ETH from Tornado to 11 addresses.
After they would:
1) Wrap the ETH
2) Transfer WETH to new address
3) Unwrap the WETH
4) Transfer USDC to MTG broker
(this is a strategy used to trick KYT at exchanges)
After they would:
1) Wrap the ETH
2) Transfer WETH to new address
3) Unwrap the WETH
4) Transfer USDC to MTG broker
(this is a strategy used to trick KYT at exchanges)

3/ After USDC was sent to a MTG US based broker that accepts crypto
How did I find the broker used?
1) Instagram username was same as on OpenSea
2) Directly contacted a few MTG sellers the broker interacted w/ on-chain
Broker address
0x80462101b56cb4125c645ff299d3e20c1d908c02


How did I find the broker used?
1) Instagram username was same as on OpenSea
2) Directly contacted a few MTG sellers the broker interacted w/ on-chain
Broker address
0x80462101b56cb4125c645ff299d3e20c1d908c02


4/ After contacting MTG sellers were where things became interesting.
-buyer was spending millions on starter decks, alpha sets, sealed boxes
-buyer seemed to be overpaying by 5-10%
-buyer sent crypto up front and broker met up IRL with seller
-buyer was unknown to seller
-said the broker has limited crypto knowledge (likely does not know about Tornado)
*seller names will be kept private for their safety*

-buyer was spending millions on starter decks, alpha sets, sealed boxes
-buyer seemed to be overpaying by 5-10%
-buyer sent crypto up front and broker met up IRL with seller
-buyer was unknown to seller
-said the broker has limited crypto knowledge (likely does not know about Tornado)
*seller names will be kept private for their safety*

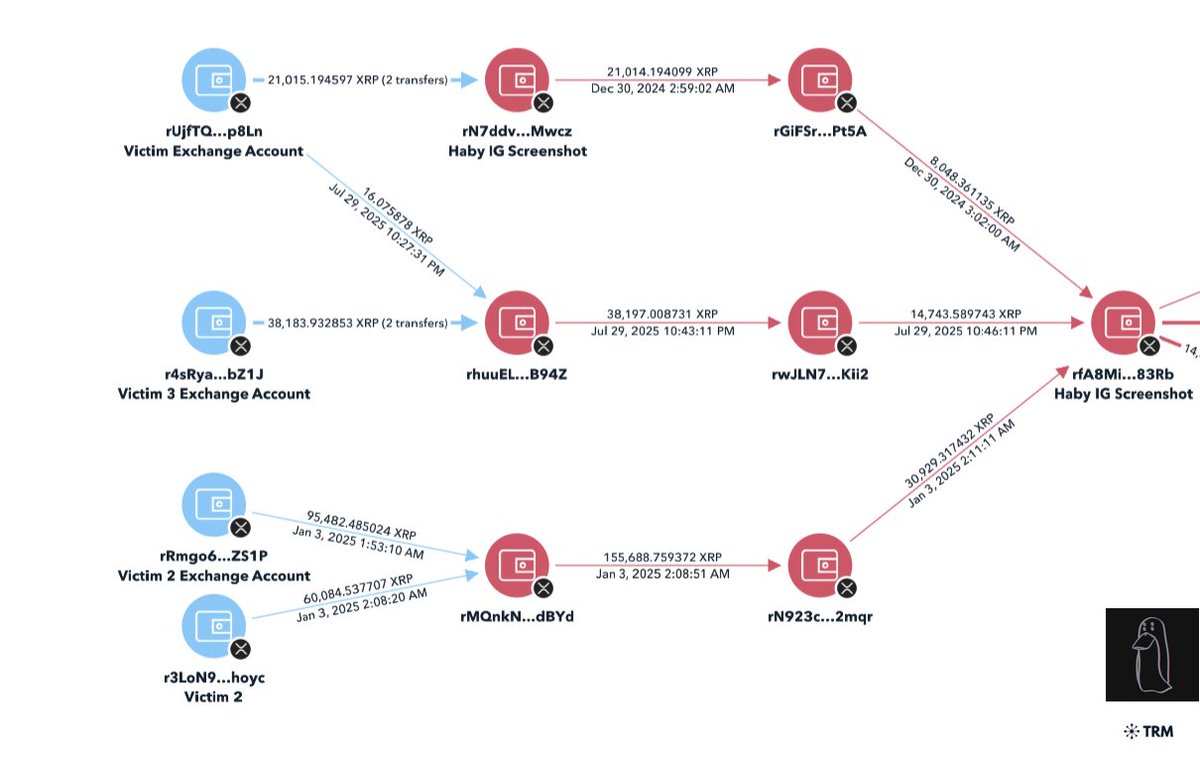
5/ The funds also go to various deposit addresses at Kraken, Bitpay, and Coinbase.
0x34e158883efc81c5d92fde785fba48db738711ee
0x3a43ac6baf1fa6bdbc966dbdfe26cf545131898e
0x85cb90db50608a950858e023509d6a7fa289e212
0xbfe6def287c402114d39d0156e17fda79efff4d2
0x34e158883efc81c5d92fde785fba48db738711ee
0x3a43ac6baf1fa6bdbc966dbdfe26cf545131898e
0x85cb90db50608a950858e023509d6a7fa289e212
0xbfe6def287c402114d39d0156e17fda79efff4d2
6/ Where do I think these funds could have originated from?
To start I began looking at the top Tornado depositors who were active throughout the past year using a Dune query created by @bax1337
-Anubis (12400 ETH)
-Cashio (11500 ETH)
-Uranium (11303 ETH)
Using timing and multi denomination reveal heuristics I arrived at the thesis that the funds potentially originated from the $50M Uranium Finance hack that occurred in April 2021.
Anubis had previously potentially been solved however and Casino did not deposit enough ETH earlier in the year to match the withdrawals of this person.


To start I began looking at the top Tornado depositors who were active throughout the past year using a Dune query created by @bax1337
-Anubis (12400 ETH)
-Cashio (11500 ETH)
-Uranium (11303 ETH)
Using timing and multi denomination reveal heuristics I arrived at the thesis that the funds potentially originated from the $50M Uranium Finance hack that occurred in April 2021.
Anubis had previously potentially been solved however and Casino did not deposit enough ETH earlier in the year to match the withdrawals of this person.


7/ Here’s some of my rationale behind it being the Uranium hacker:
Oct 4, 2022 the Uranium hacker deposited 5.01 ETH total to Aztec (privacy tool) at 22:03 UTC
0xd332be2c39de1f4ecd4ef6ce23ae826906a8a144ebbfefb9cf2a74c7d320f563
Just 2 hours later at 00:15 UTC on Oct 5 this person received 2.7 ETH from Aztec
0x2b8745157bd13cb7aa76444af67e7de0bf0b288bff50886b599942a17e0e298c

Oct 4, 2022 the Uranium hacker deposited 5.01 ETH total to Aztec (privacy tool) at 22:03 UTC
0xd332be2c39de1f4ecd4ef6ce23ae826906a8a144ebbfefb9cf2a74c7d320f563
Just 2 hours later at 00:15 UTC on Oct 5 this person received 2.7 ETH from Aztec
0x2b8745157bd13cb7aa76444af67e7de0bf0b288bff50886b599942a17e0e298c

8/ In March 2023 the Uranium hacker deposited 52 X 100 ETH to Tornado & this person received 52 X 100 ETH
March 6 & 14: Uranium Hacker deposits 52 X 100 ETH to Tornado
March 7 & 15: Our person withdrew huge volumes from Tornado
After they finished the Uranium hacker deposits more in May

March 6 & 14: Uranium Hacker deposits 52 X 100 ETH to Tornado
March 7 & 15: Our person withdrew huge volumes from Tornado
After they finished the Uranium hacker deposits more in May

9/ While my analysis could be incorrect I find it very suspicious that this person:
-spends 8 figures on MTG
-is overpaying for MTG
-shields identity through broker who likely does not know what Tornado is
-receives $13.2M from Tornado post OFAC while in the US
-uses WETH method to obfuscate source
-spends 8 figures on MTG
-is overpaying for MTG
-shields identity through broker who likely does not know what Tornado is
-receives $13.2M from Tornado post OFAC while in the US
-uses WETH method to obfuscate source
• • •
Missing some Tweet in this thread? You can try to
force a refresh