
Technical tweets for technical folks by Deutsche Telekom CERT, CTI, and DFIR.
#dfir #cyber #cert #cti #TelekomSecurity
How to get URL link on X (Twitter) App


 In one intrusion related to this campaign a fake IT support agent called the victim user and reported that there are "Outlook problems". The caller then tricked the victim into downloading and executing a malware binary from a provided domain. 🧵2/x
In one intrusion related to this campaign a fake IT support agent called the victim user and reported that there are "Outlook problems". The caller then tricked the victim into downloading and executing a malware binary from a provided domain. 🧵2/x


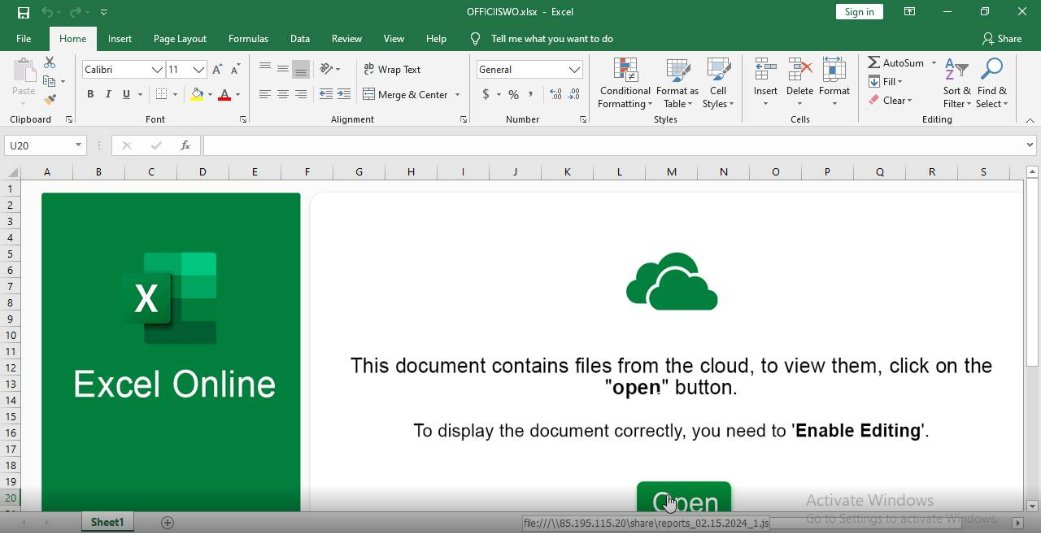
 Further inspection of the file reveals that the document contains a hyperlink 🔗 to a remote SMB share, which hosts a Javascript file that triggers the Pikabot infection chain. 🧵2/4
Further inspection of the file reveals that the document contains a hyperlink 🔗 to a remote SMB share, which hosts a Javascript file that triggers the Pikabot infection chain. 🧵2/4 









 Attached to the email is a HTML file which tries to download and execute malicious Javascript code. 🧵2/5
Attached to the email is a HTML file which tries to download and execute malicious Javascript code. 🧵2/5 