The ability to block Device Code Flow just became available in Microsoft Entra ID Conditional Access.
Here's a quick walkthrough of how attackers use device code flow to get access to your tenant and what you can do to protect yourself.
Here's a quick walkthrough of how attackers use device code flow to get access to your tenant and what you can do to protect yourself.
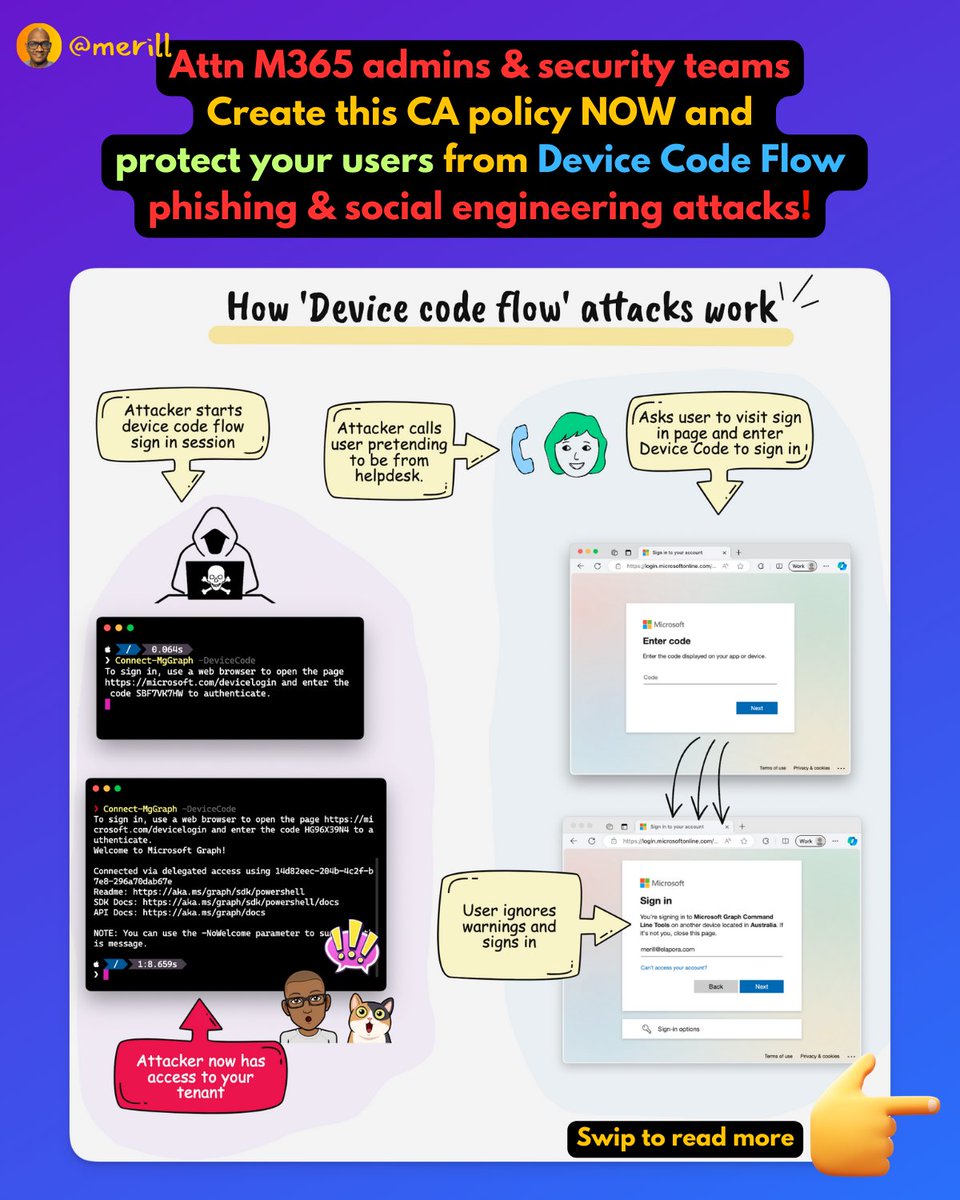
❇️ Why does device code flow exist?
Device code flow is required when signing into devices that might lack local input for eg meeting room devices or scenarios like shared devices.
Unfortunately, attackers frequently use this mechanism to target your users.
Device code flow is required when signing into devices that might lack local input for eg meeting room devices or scenarios like shared devices.
Unfortunately, attackers frequently use this mechanism to target your users.
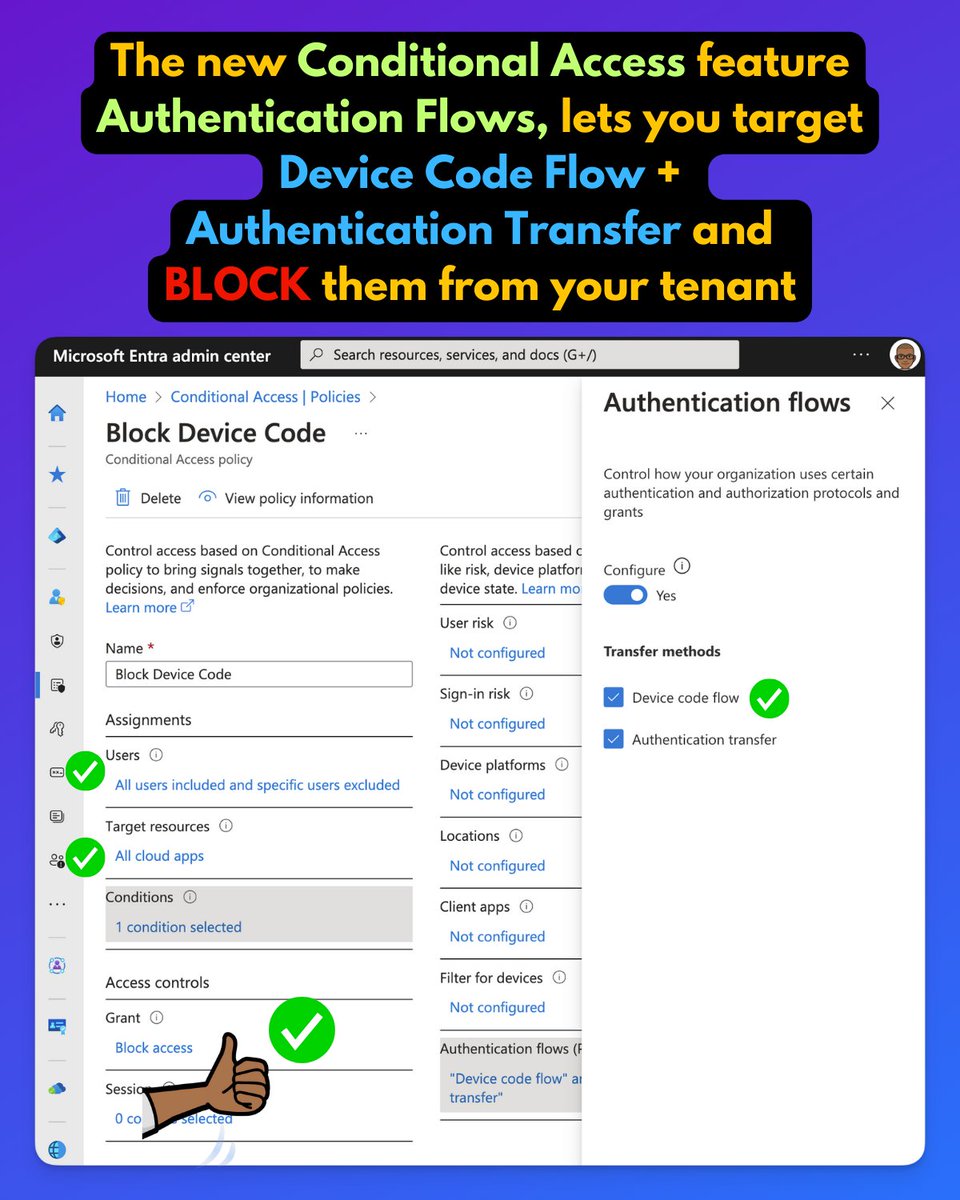
🪟 Microsoft's recommendation
Microsoft's recommendation is to block device code flow wherever possible and only allow device code flow where necessary.
Learn more
→
→
→ How-to article: learn.microsoft.com/entra/identity…
learn.microsoft.com/entra/identity…
learn.microsoft.com/entra/identity…

Microsoft's recommendation is to block device code flow wherever possible and only allow device code flow where necessary.
Learn more
→
→
→ How-to article: learn.microsoft.com/entra/identity…
learn.microsoft.com/entra/identity…
learn.microsoft.com/entra/identity…

Bookmark, like and repost if you found this useful.
Sign up to my newsletter to get this directly in your inbox. entra.news

Sign up to my newsletter to get this directly in your inbox. entra.news

Shout out to eagle eyed @rootsecdev who figured out this new CA feature before Microsoft published it. 👋
If you want to learn more don't miss this awesome blog post by @fabian_bader ⬇️
cloudbrothers.info/en/protect-use…
If you want to learn more don't miss this awesome blog post by @fabian_bader ⬇️
cloudbrothers.info/en/protect-use…
https://x.com/rootsecdev/status/1762316550378307767?s=20
• • •
Missing some Tweet in this thread? You can try to
force a refresh