I recently found two very interesting Linux binaries uploaded to Virustotal.
I call this malware 'GTPDOOR'.
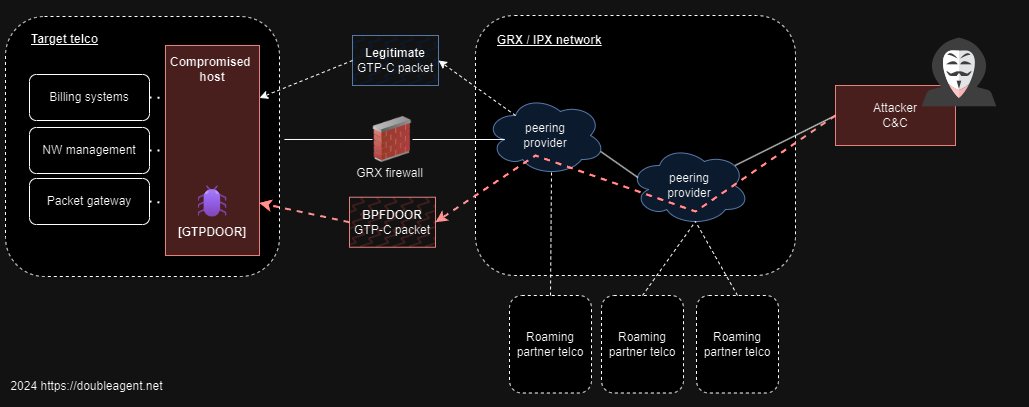
GTPDOOR is a 'magic/wakeup' packet backdoor that uses a novel C2 transport protocol: GTP (GPRS Tunnelling Protocol), silently listening on the GRX network (1/n) 🧵
I call this malware 'GTPDOOR'.
GTPDOOR is a 'magic/wakeup' packet backdoor that uses a novel C2 transport protocol: GTP (GPRS Tunnelling Protocol), silently listening on the GRX network (1/n) 🧵
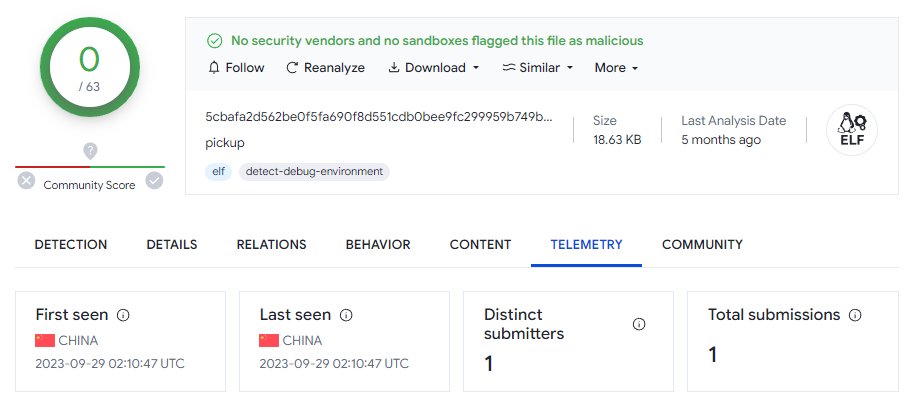
One version uploaded from 🇨🇳 has zero detections on VT. The other, uploaded from 🇮🇹 has just one detection.
These were uploaded 4 to 5 months ago.
(2/n)


These were uploaded 4 to 5 months ago.
(2/n)

As they binaries were not stripped, they contain some artifacts that give us an idea of the intended platforms they were to be run on - Very outdated Red Hat Linux machines.
Someone hasn't been keeping their systems up to date .. 🤔
(3/n))
Someone hasn't been keeping their systems up to date .. 🤔
(3/n))

When run, the first thing GTPDOOR does is process-name stomps itself - changing it's process name to "[syslog]" - disguised as syslog invoked from the kernel.
It supresses child signals and then opens a raw socket.
(4/n)
It supresses child signals and then opens a raw socket.
(4/n)

The raw socket will allow the implant to receive UDP messages that hit the network interfaces.
It then matches those with destination port of 2123. This is the 3GPP standard port for the GTP-C protocol.
It then looks for only those that are of GTP_ECHO_REQUEST.
(5/n)
It then matches those with destination port of 2123. This is the 3GPP standard port for the GTP-C protocol.
It then looks for only those that are of GTP_ECHO_REQUEST.
(5/n)

Before moving further, the message is authenticated - `idkey` must be supplied and correct. It's hardcoded, but as we will see later, it can be dynamically updated at runtime.
(6/n)
(6/n)

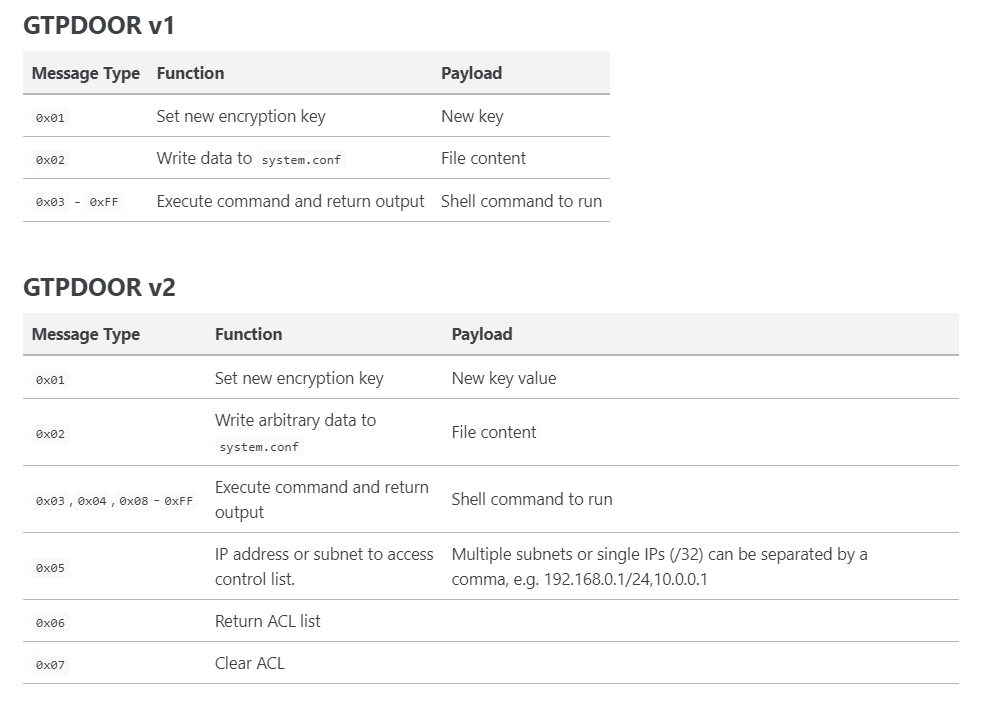
Next the message command type is read. There are different message types depending on the binary.
This is all documented in a blog post I've just whipped up.
(8/n)
doubleagent.net/telecommunicat…

This is all documented in a blog post I've just whipped up.
(8/n)
doubleagent.net/telecommunicat…
The packet format is something like this. IP/UDP/GTP/GTPDOOR.
For example, the tailing bytes (MESSAGE DATA) will contain a command to execute remotely.
Why use GTP for the C2 communications?
(9/n)
For example, the tailing bytes (MESSAGE DATA) will contain a command to execute remotely.
Why use GTP for the C2 communications?
(9/n)

This implant looks like it is designed to sit on compromised hosts that directly touch the GRX network - these are the systems that communicate to other telecommunication operator networks via the GRX.
Examples include the 2/3G: eDNS, GGSN, SGSN,STP, 4G: PGW, DRA and more (10/n)
Examples include the 2/3G: eDNS, GGSN, SGSN,STP, 4G: PGW, DRA and more (10/n)
Let's cut the chase. This is almost certain to be attributed to the threat actor UNC1954 (Mandiant) or LightBasin (CrowdStrike).
This actor has used GTP-U (traffic plane / PDP Context) for covert tunnelling.
(11/n)
mandiant.com/resources/blog…
crowdstrike.com/blog/an-analys…
This actor has used GTP-U (traffic plane / PDP Context) for covert tunnelling.
(11/n)
mandiant.com/resources/blog…
crowdstrike.com/blog/an-analys…
With this implant, the use the GTP port associated not with traffic plane (GTP-U), but control plane (GTP-C).
GRX firewalls have to allow these protocols to some of the systems described earlier, so the C2 traffic blends right in with other mobile network traffic. (12/n)
Again:
GRX firewalls have to allow these protocols to some of the systems described earlier, so the C2 traffic blends right in with other mobile network traffic. (12/n)
Again:

What makes magic / wakeup / port knocking backdoors so stealthy as they don't need to listen on any service.
These backdoors have been around since the 90s but they still are used because they are effective.
No listening services / open ports - just a process idle sitting and waiting for it's magic packet.
BPFDOOR was a recent one. It was also found in telco networks (although attributed to a different actor).
Read about that one here:
…
(13/n)sandflysecurity.com/blog/bpfdoor-a…
These backdoors have been around since the 90s but they still are used because they are effective.
No listening services / open ports - just a process idle sitting and waiting for it's magic packet.
BPFDOOR was a recent one. It was also found in telco networks (although attributed to a different actor).
Read about that one here:
…
(13/n)sandflysecurity.com/blog/bpfdoor-a…
An interesting feature in one version of GTPDOOR a second raw socket that pulls in all TCP packets off the interface to inspect.
The implant beacons out a very particular TCP message to the source IP of every TCP message - except those listed in a defined ACL. WEIRD!
(14/n)
The implant beacons out a very particular TCP message to the source IP of every TCP message - except those listed in a defined ACL. WEIRD!
(14/n)

The TCP packet it beacons out has no data / payload. Just the TCP RST/ACK flags are set.
No data? Look closely. Super stealthy.... 🕵️🕵️♀️🕵️♂️
(15/n)
No data? Look closely. Super stealthy.... 🕵️🕵️♀️🕵️♂️
(15/n)

My best guess on what's going on here is this:
You send a TCP packet to ANY port on an infected host's GRX interface address.
Any beacon reply = confirmation implant running +
TCP urgent ptr flag == 1? dst port was open
TCP urgent ptr flag == 0? dst port was closed
They are hiding a message inside a TCP header. I think I read about this first in some old hacking book from the early 2000s. Was it "Counter Hack"?
Now there are some conditions for this beacon to be sent - An ACL "deny list" needs to be set - possibly to prevent beacons hitting the target network infrastructure.
If my theory is right here, then it could be possible to scan the entire GRX to find compromised servers / telco network operators?🤔
(16/n)
You send a TCP packet to ANY port on an infected host's GRX interface address.
Any beacon reply = confirmation implant running +
TCP urgent ptr flag == 1? dst port was open
TCP urgent ptr flag == 0? dst port was closed
They are hiding a message inside a TCP header. I think I read about this first in some old hacking book from the early 2000s. Was it "Counter Hack"?
Now there are some conditions for this beacon to be sent - An ACL "deny list" needs to be set - possibly to prevent beacons hitting the target network infrastructure.
If my theory is right here, then it could be possible to scan the entire GRX to find compromised servers / telco network operators?🤔
(16/n)
Here is a tcpdump capture of the probe message sent to port 22 which is open (SSH running).,
The received beacon TCP RST/ACK message has the urgent flag set.
This actor is known for it's stealth, and this is the perfect example.
(17/n)
The received beacon TCP RST/ACK message has the urgent flag set.
This actor is known for it's stealth, and this is the perfect example.
(17/n)

I think I'll wrap this up now. A YARA rule can be found on my blog post on this backdoor for all you threat hunters.
I'm sure someone will come up with a much better one real soon.
Thanks for watching !🙏
(18/18)
doubleagent.net/telecommunicat…

I'm sure someone will come up with a much better one real soon.
Thanks for watching !🙏
(18/18)
doubleagent.net/telecommunicat…

Oh yeah, I forgot to mention, there is a memory corruption vulnerability in there.
Any guesses on how to trigger it? 😆
(19/19)
Any guesses on how to trigger it? 😆
(19/19)

• • •
Missing some Tweet in this thread? You can try to
force a refresh