How to get URL link on X (Twitter) App



 Perhaps it's only looking for UDP magic packets? Not so fast. Let's look at what changed.
Perhaps it's only looking for UDP magic packets? Not so fast. Let's look at what changed.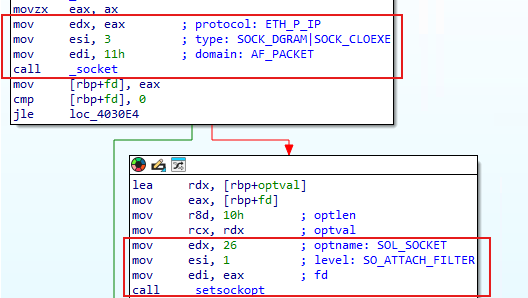

 Case in point:
Case in point: 
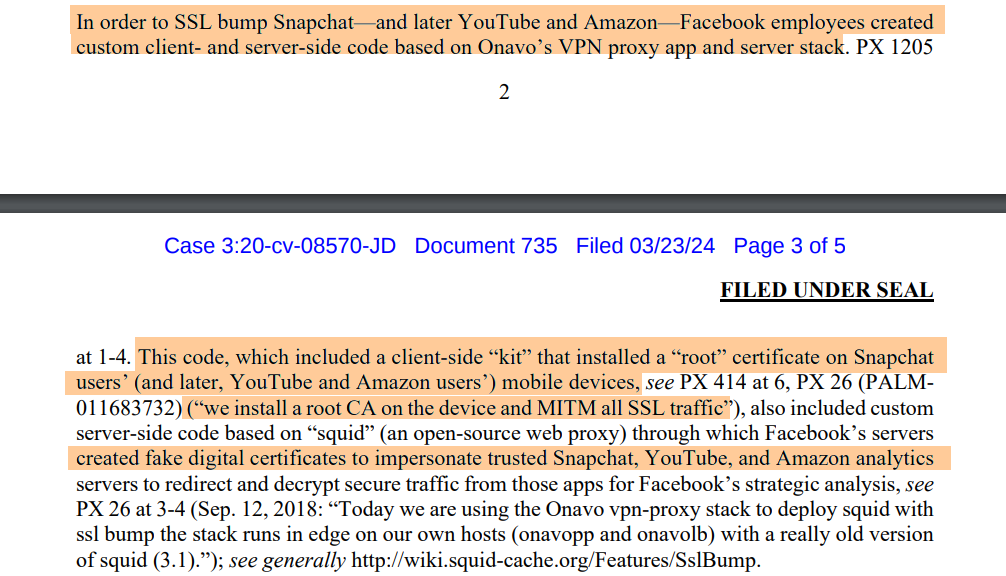
 Here Facebook acquired Onavo and had quite a good run before the spyware got pulled from app stores.
Here Facebook acquired Onavo and had quite a good run before the spyware got pulled from app stores.
 One version uploaded from 🇨🇳 has zero detections on VT. The other, uploaded from 🇮🇹 has just one detection.
One version uploaded from 🇨🇳 has zero detections on VT. The other, uploaded from 🇮🇹 has just one detection. 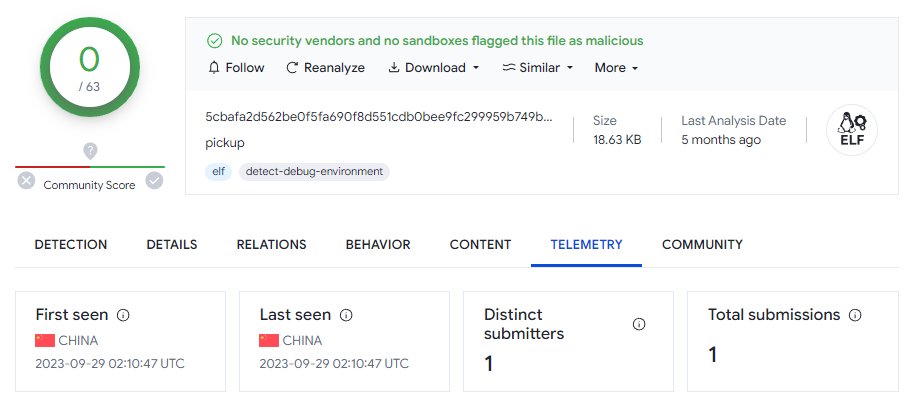


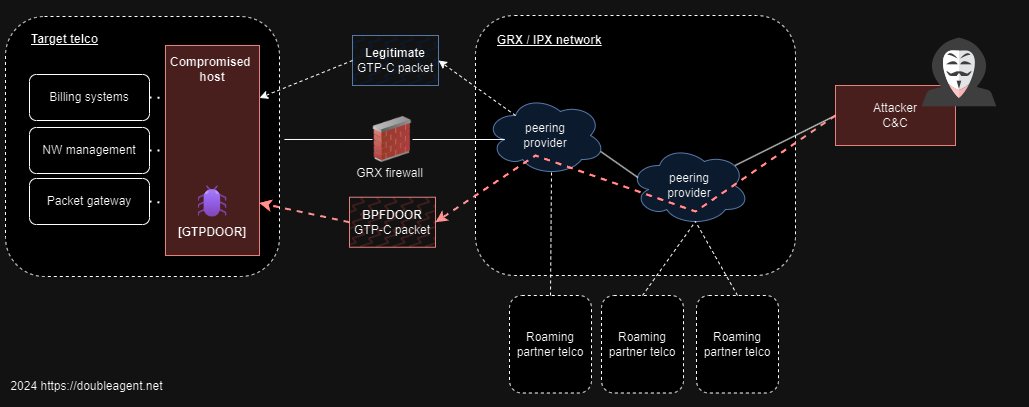
 CDRs are primarily used for postpaid billing and reporting purposes. They are generated in various network elements and consolidated in mediation systems.
CDRs are primarily used for postpaid billing and reporting purposes. They are generated in various network elements and consolidated in mediation systems. 

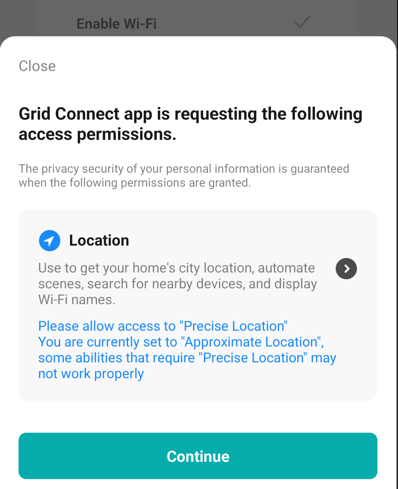
 Happy to see that the Android app has responsibly requested the minimum permissions for BLE scanning. I kind of was expecting it to request my location for this which it didn't. (2/n)
Happy to see that the Android app has responsibly requested the minimum permissions for BLE scanning. I kind of was expecting it to request my location for this which it didn't. (2/n) 

 Before we begin the investigation, a coverage map of where these devices have been found across planet earth.
Before we begin the investigation, a coverage map of where these devices have been found across planet earth. 

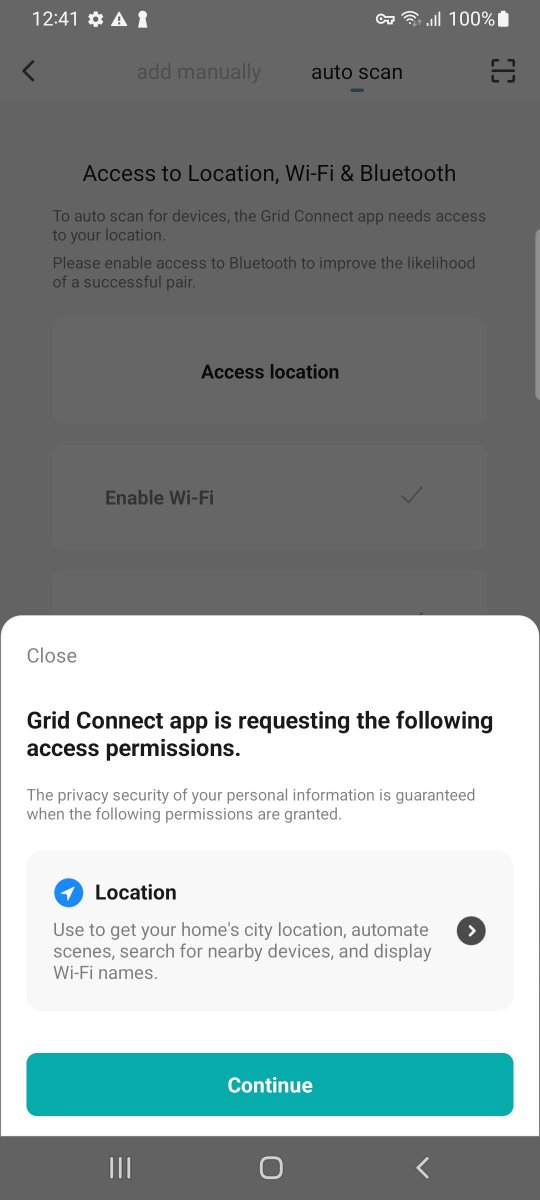
 Let's see how we can pair with the minimum amount of granted permissions.
Let's see how we can pair with the minimum amount of granted permissions. 

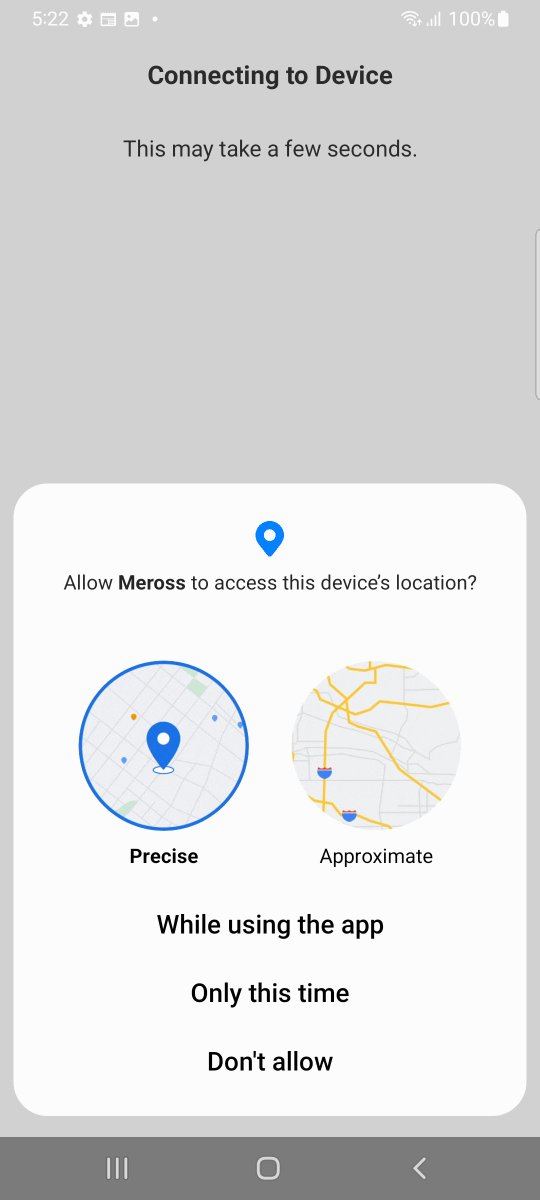

 The app has a feature where it can auto discover your BLE devices. Is locations permission needed here? It depends. From Android API SDK v31 things have improved where fine location is not needed for BLE scanning.
The app has a feature where it can auto discover your BLE devices. Is locations permission needed here? It depends. From Android API SDK v31 things have improved where fine location is not needed for BLE scanning.