It's been an interesting weekend! Eagle-eyed @TomHegel spotted what appears to be a new variant of AcidRain. Notably this sample was compiled for Linux x86 devices, we are calling it 'AcidPour'. Those of you that analyzed AcidRain will recognize some of the strings. Analysis 🧵 
@TomHegel For context, AcidRain was a wiper component utilized during the infamous 'Viasat hack' that took down KA-SAT Surfbeam2 modems at the start of the Russian invasion of Ukraine.
sentinelone.com/labs/acidrain-…
sentinelone.com/labs/acidrain-…
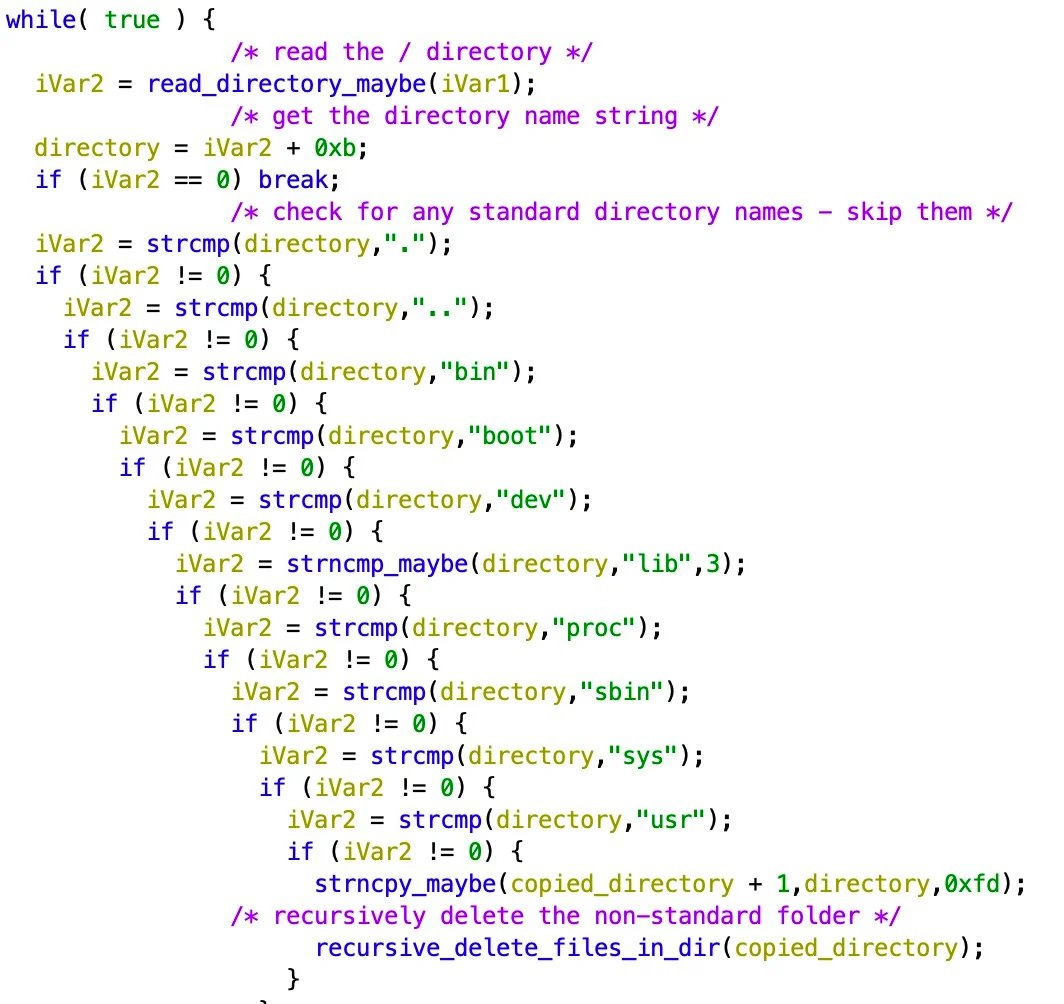
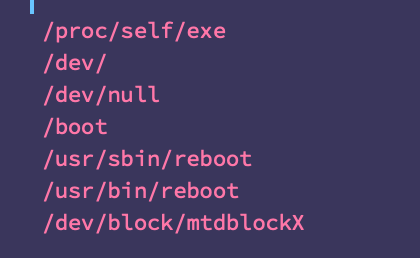
@TomHegel The original was an ELF binary compiled for MIPS. It acts as a generic and largely hamfisted wiper, iterating over common directories and device paths for most embedded linux distros.
@TomHegel Mad props to @maxpl0it for his analysis of AcidRain in a pinch/
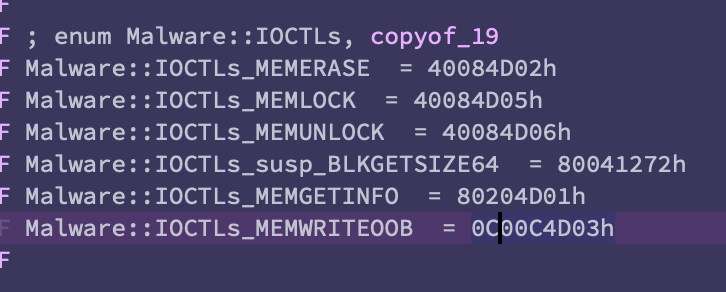
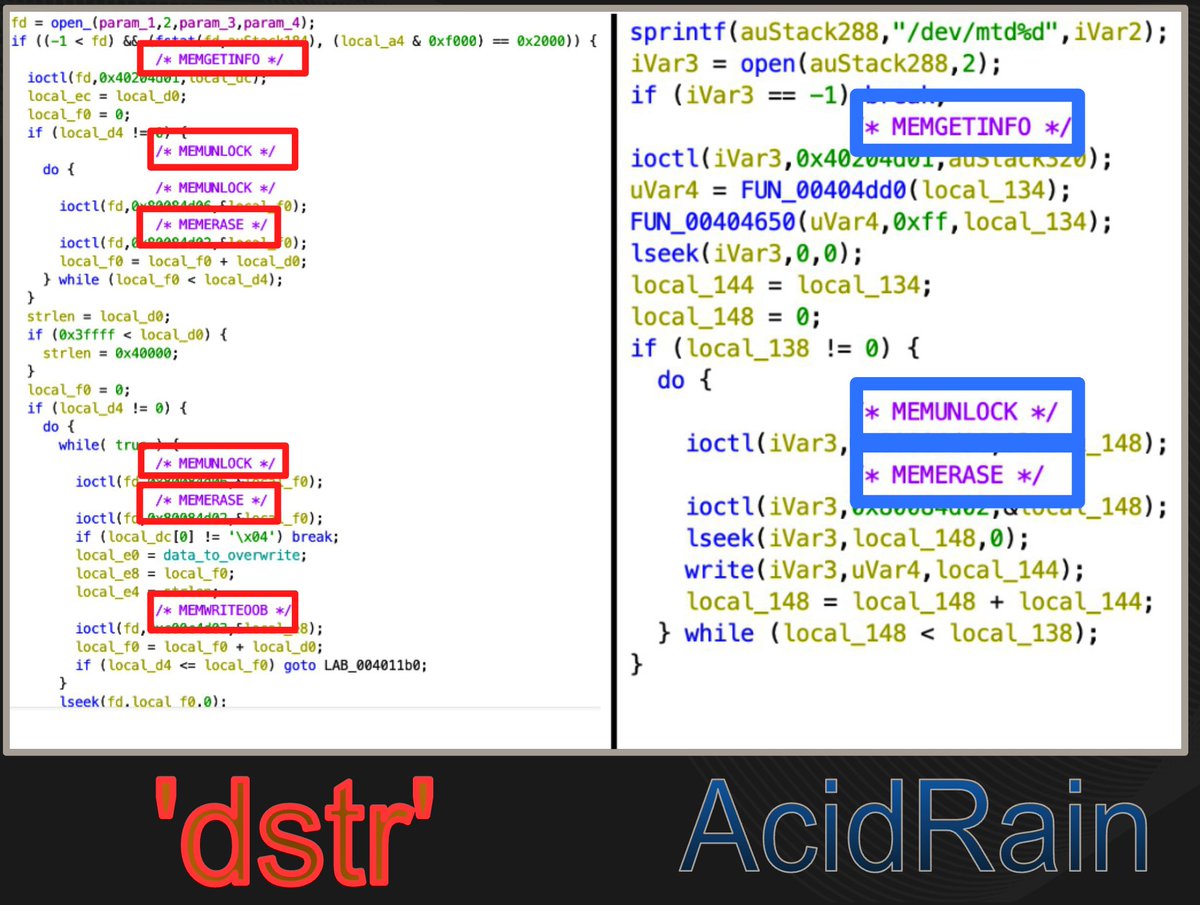
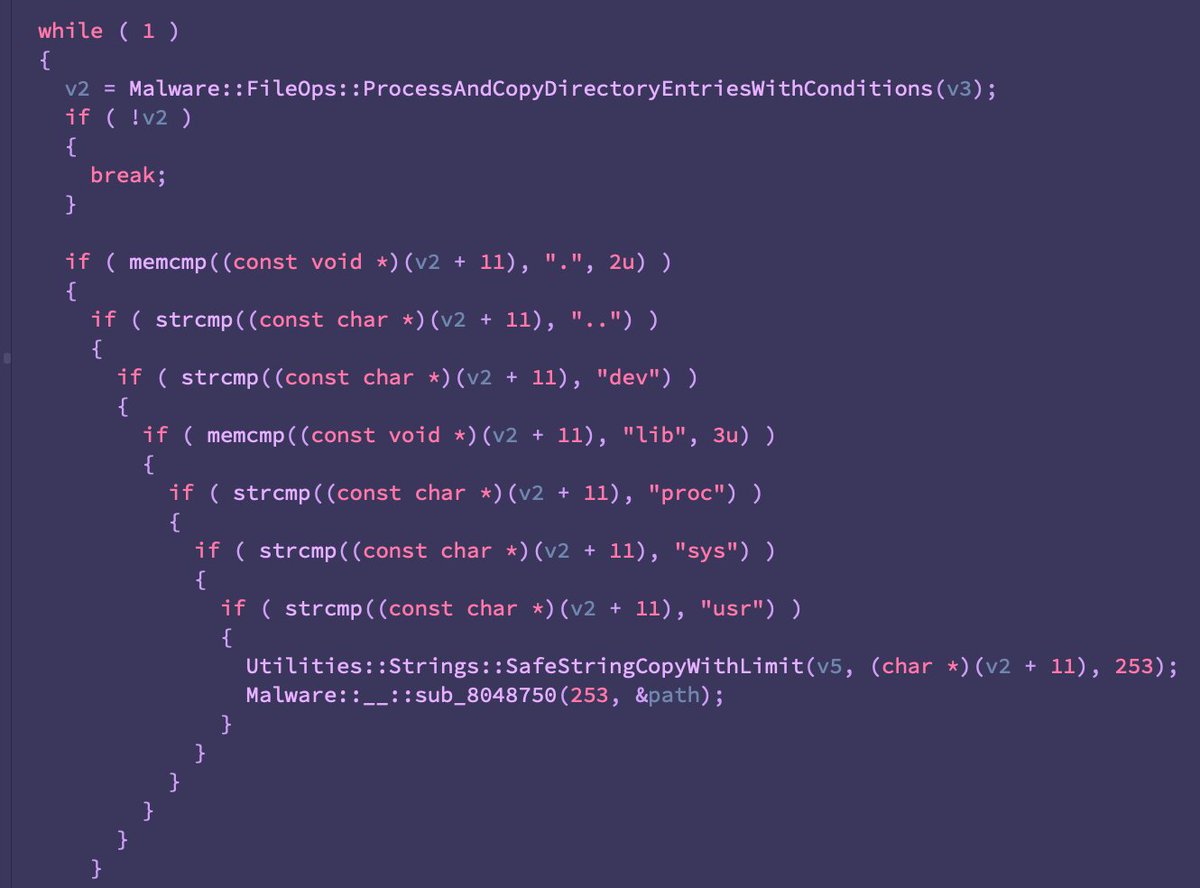
@TomHegel @maxpl0it The new variant we are calling AcidPour is an ELF binary compiled for x86 (not MIPS) and while it refers to similar devices/strings, it's a largely different codebase. Doing our best to compare across different architectures, we are looking at a rough < 30% similarity. 

For those inclined towards healthy skepticism, a few things to consider upfront:
-The initial similarities are strings that could easily be replicated by a different attacker.
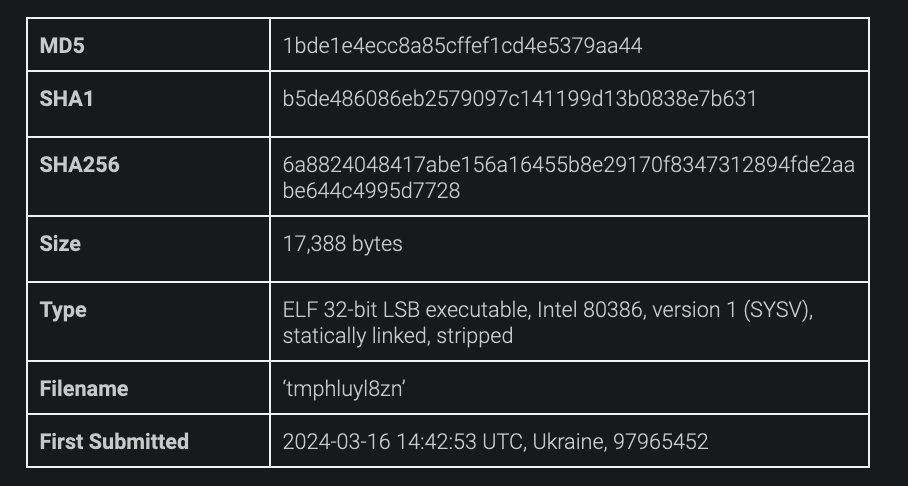
-The sample was uploaded from Ukraine on 2024-03-16 14:42:53 UTC. We have no idea about actual target.
-The initial similarities are strings that could easily be replicated by a different attacker.
-The sample was uploaded from Ukraine on 2024-03-16 14:42:53 UTC. We have no idea about actual target.
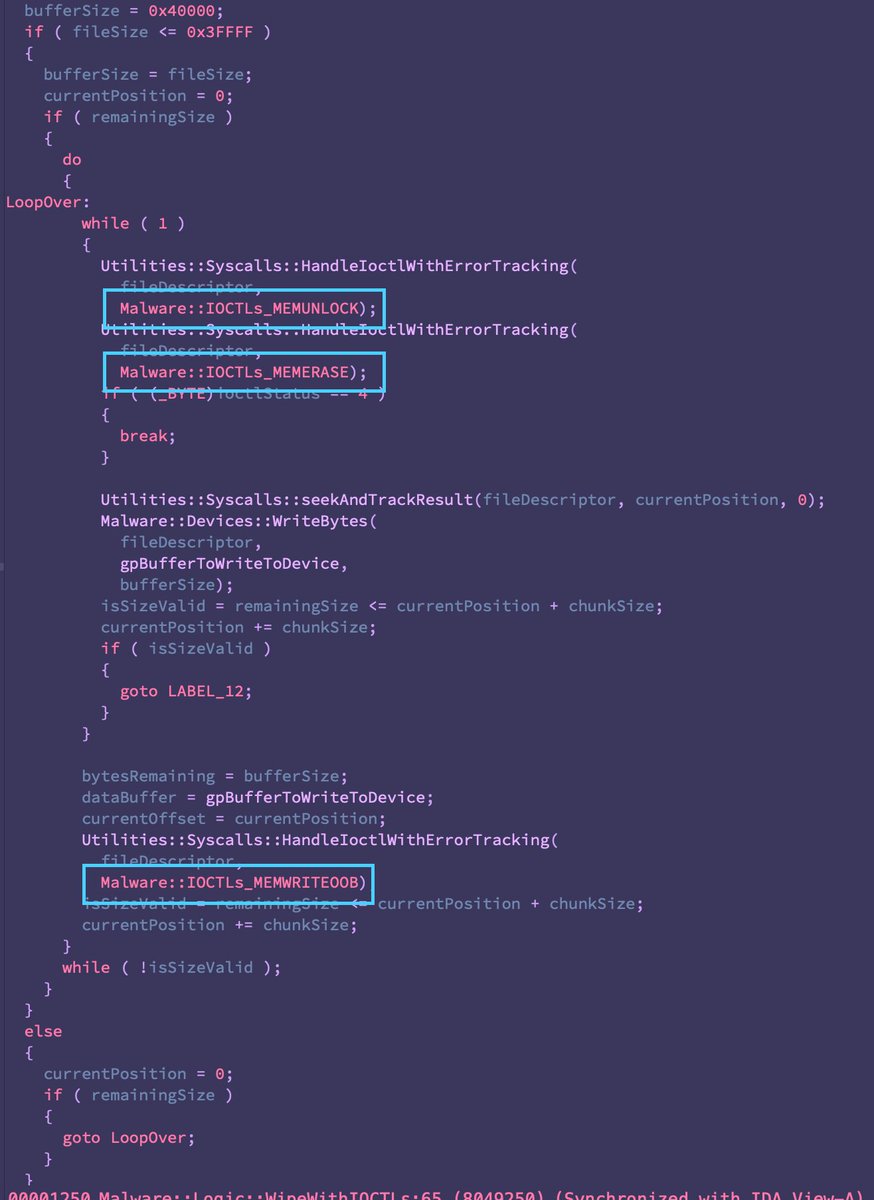
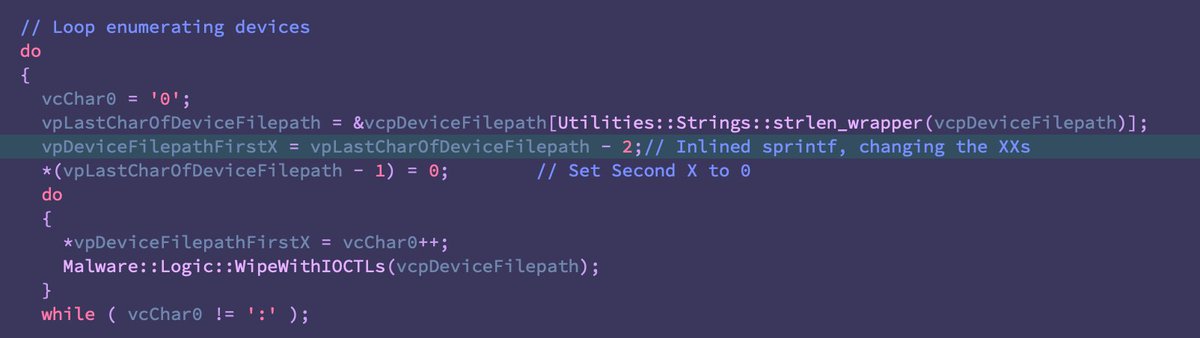
With that out of the way, the some of the additions are quite interesting, primarily the addition of ‘/dev/ubiXX’ -a reference to Unsorted Block Images (UBI) commonly used in embedded systems largely dealing with flash memory (IoT, networking devices, maybe some ICS). 
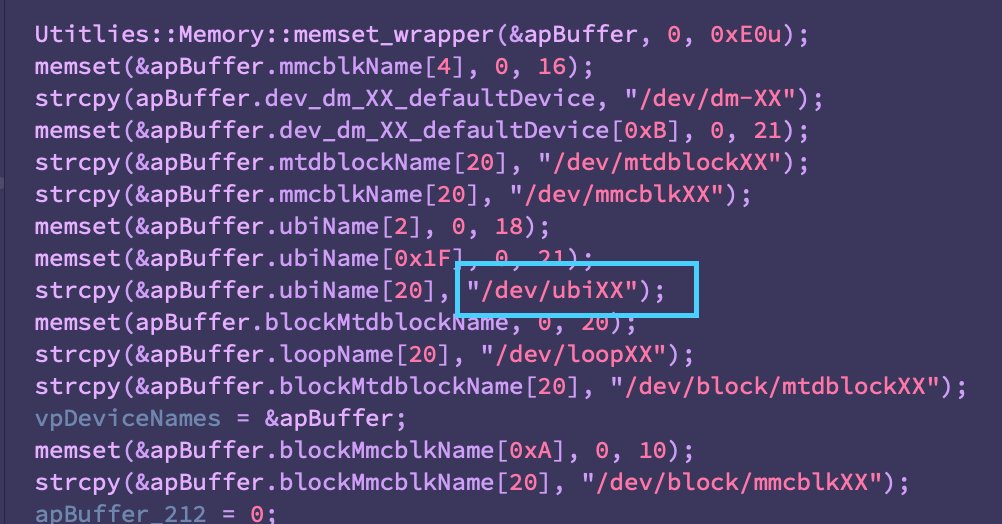
Notice also the addition of '/dev/dm-XX', virtual block devices associated with LVM -- think RAID arrays.
And now you're caught up with me, we've entered "We'll do it live!" territory (in the tradition of our OALabs friends cc: @herrcore). This is where GaboRE and I light a candle to @RolfRolles and dive into the remaining analysis. Will keep livetweeting.
On our end, the intended victim remains unidentified but we notified folks in UA on Saturday since we didn't know the possible spread of the operation.
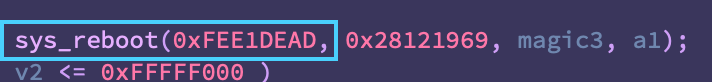
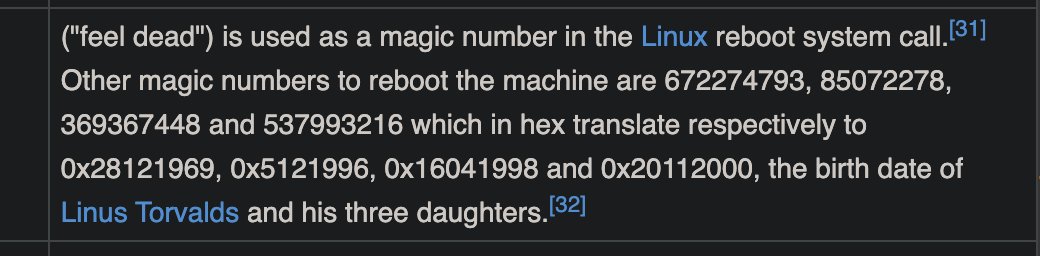
Wonder if ChatGPT is getting tired..
Analogous to AcidRain, there appears to be a different wiping logic for borking certain devices like /dev/dmXX (LVMs, likely RAIDs).
Been nerding out and not updating..
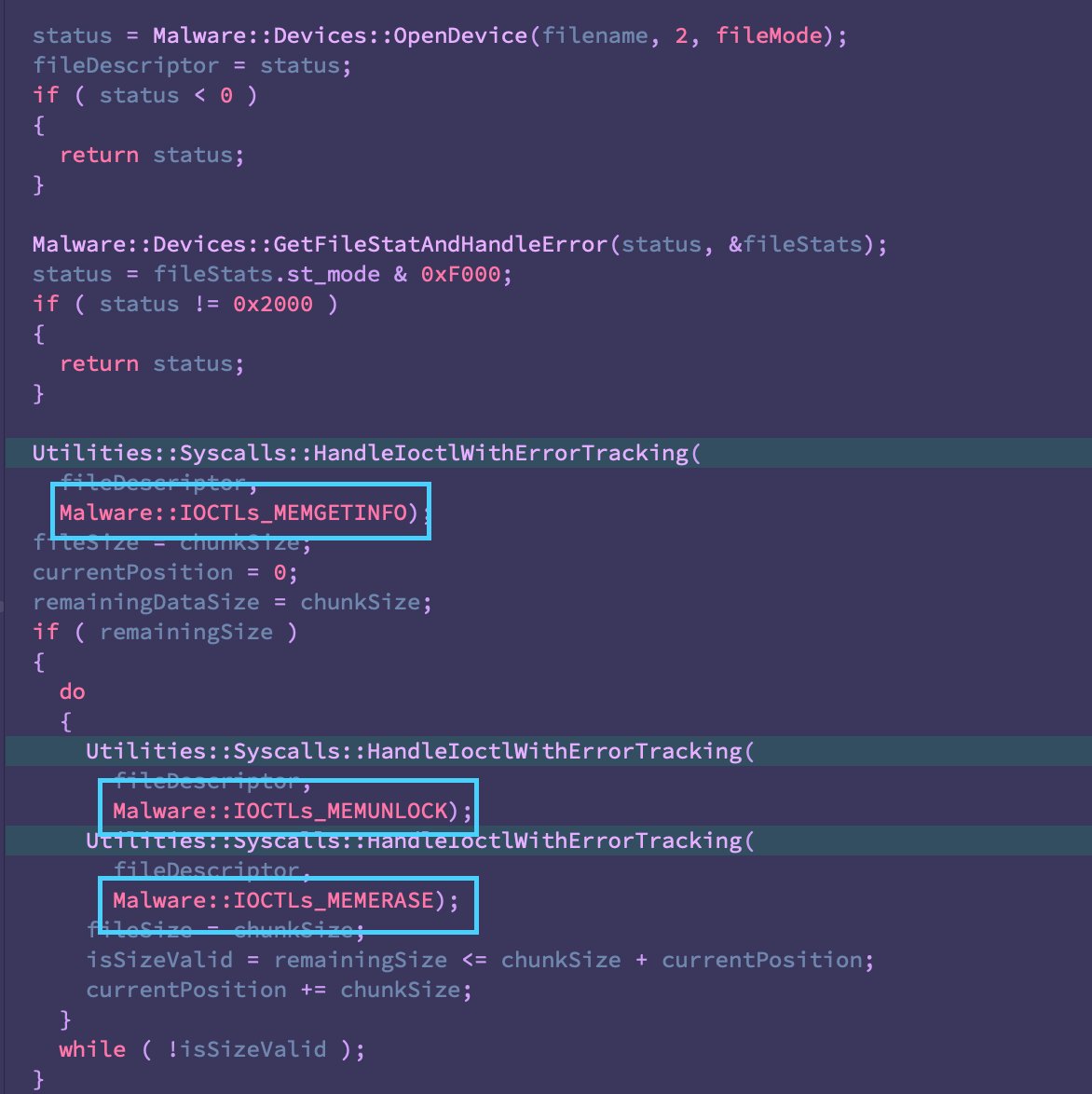
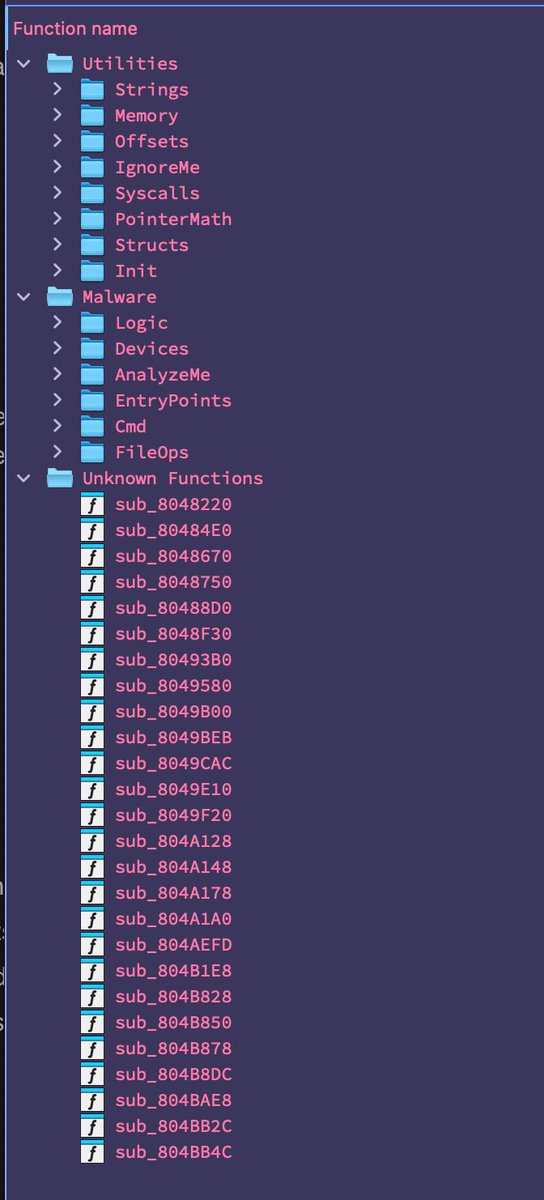
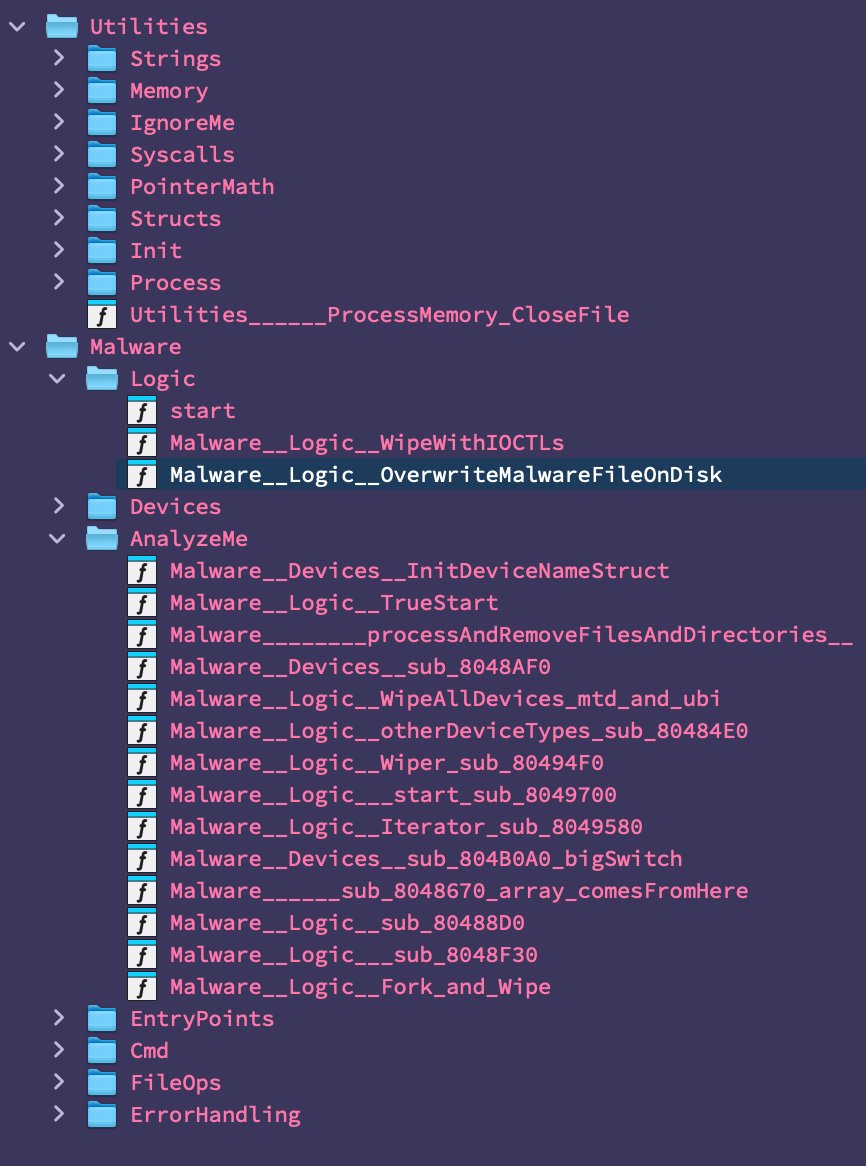
All functions labeled, now digging into the nitty gritty of the malware logic.
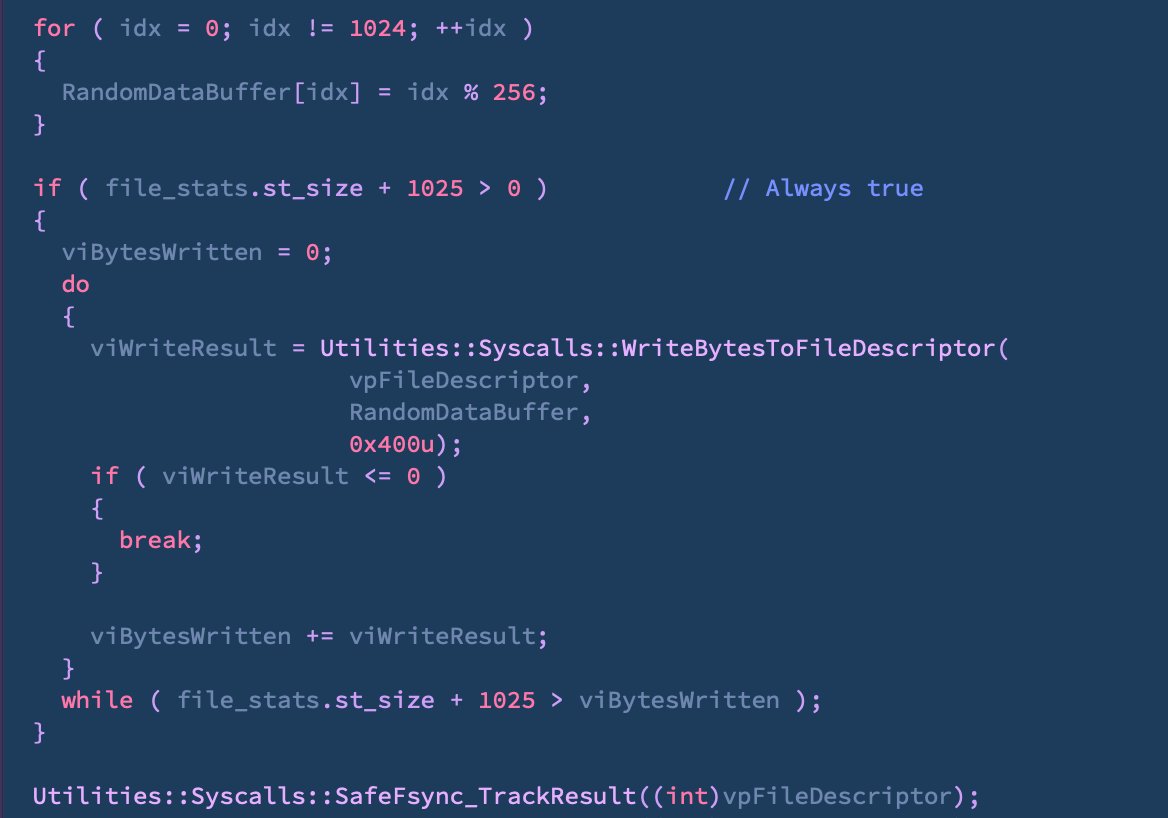
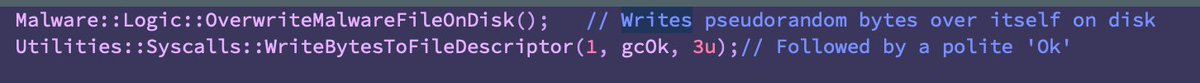
Upon execution, it overwrites itself on disk with pseudo random data, followed by a polite 'Ok'


All functions labeled, now digging into the nitty gritty of the malware logic.
Upon execution, it overwrites itself on disk with pseudo random data, followed by a polite 'Ok'
We are seeing reports this past week of disruption to Ukrainians ISPs. The involvement of AcidPour is unconfirmed but could fit the bill. 'Hacktivist' group taking credit for whatever that's worth ¯\_(ツ)_/¯
https://twitter.com/DougMadory/status/1770498150458908930
A more complete rundown of our findings is now available here:
https://twitter.com/TomHegel/status/1770824879828324573
• • •
Missing some Tweet in this thread? You can try to
force a refresh