
VP Intel & Senior Technical Fellow (AI Research) @SentinelOne | Distinguished Fellow, @SAISHopkins Alperovitch | Founder @ LABScon | Buddy @ Three Buddy Problem
How to get URL link on X (Twitter) App

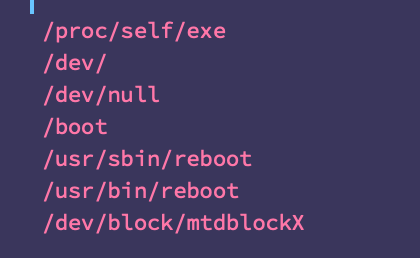
 @TomHegel For context, AcidRain was a wiper component utilized during the infamous 'Viasat hack' that took down KA-SAT Surfbeam2 modems at the start of the Russian invasion of Ukraine.
@TomHegel For context, AcidRain was a wiper component utilized during the infamous 'Viasat hack' that took down KA-SAT Surfbeam2 modems at the start of the Russian invasion of Ukraine.
 First of all, let me say I’m shocked at how unfamiliar people are with Sade. You’re breaking @MigoKed’s heart as he continues to play with musical classics for campaign namings. (Looking at you @SecurePeacock :P )
First of all, let me say I’m shocked at how unfamiliar people are with Sade. You’re breaking @MigoKed’s heart as he continues to play with musical classics for campaign namings. (Looking at you @SecurePeacock :P )



https://twitter.com/YourAnonTV/status/1497510954921254915You can read the email here. It's actually pretty funny.


https://twitter.com/threatintel/status/1496844387275390979The 'ransomware' (4dc13bb83a16d4ff9865a51b3e4d24112327c526c1392e14d56f20d6f4eaf382) is written in Go and C and has some interesting quirks and taunting–

https://twitter.com/threatintel/status/1496578746014437376Pretty small piece of code, all things considered.


https://twitter.com/IranIntl_En/status/1452944995741315079?s=20Screens on the gas pump PoS systems say 'cyberattack, 64411' in Farsi. For avid readers, this should be a throwback to the Iranian railway systems attack in July where the attackers also directed calls to 64411, the Office of Iran's Supreme Leader, Ali Khamenei' #MeteorExpress

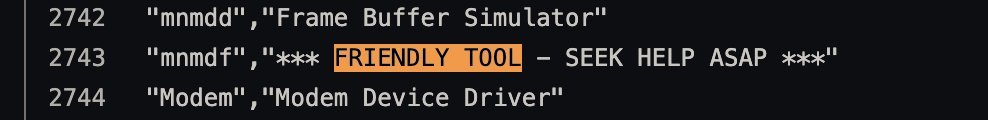
https://twitter.com/josephfcox/status/1430161392364044292I've played with Augury before. Netflow can be useful. But for the most part it's spotty, incomplete, and inconclusive. You don't turn into a SIGINT agency because you have visibility into a few hops along a path for a sliver of time. Internet routing doesn't work that way.



https://twitter.com/billmarczak/status/1416801439402262529These remarks on the limitations when inspecting iOS devices should give us pause… there’s a mistaken belief that privacy is protected by limiting checks on system integrity and correlation of anomalies. What privacy is protected in these cases? (@tim_cook @radian)

