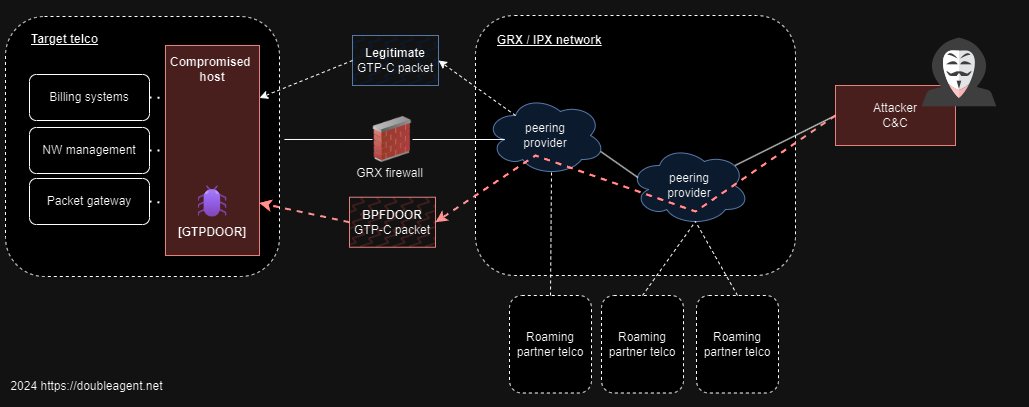
If you needed yet another reason not to trust VPN providers or proxy services...
Here Facebook partnered with a bunch of companies to have root certificates installed on people's phones so they could intercept other app's traffic.
storage.courtlistener.com/recap/gov.usco…

Here Facebook partnered with a bunch of companies to have root certificates installed on people's phones so they could intercept other app's traffic.
storage.courtlistener.com/recap/gov.usco…
Here Facebook acquired Onavo and had quite a good run before the spyware got pulled from app stores.
At a $120 million dollar price point it's clear how much value they put on having the ability to intercept user's mobile traffic.
en.wikipedia.org/wiki/Onavo

At a $120 million dollar price point it's clear how much value they put on having the ability to intercept user's mobile traffic.
en.wikipedia.org/wiki/Onavo

Checking the archived APK listing for "Onavo Protect" from 2019, likely just before it was pulled from the Play store, the description discloses some information on what they are up to, but then proceeds to gaslight the user.
apkpure.com/onavo-protect-…
apkpure.com/onavo-protect-…

I think they could only pull this off by coercing user's into installing a system-level trusted CA on the handset?
Things have improved as this is not trivial to do on Android these days - requiring a filesystem to be remounted as writable - on possible on jailbroken devices.
Things have improved as this is not trivial to do on Android these days - requiring a filesystem to be remounted as writable - on possible on jailbroken devices.
Let’s grab a copy of Facebook’s banned VPN app from 2019 and install it to see how it manages to spy on other apps on the phone.
Note how it guides me to click invasive permissions such as allowing it to appear on top of other applications. A mobile malware technique.
Note how it guides me to click invasive permissions such as allowing it to appear on top of other applications. A mobile malware technique.
Interesting, the app still manages to establish connectivity back to Facebook's servers. 😡
That said, once it's VPN tunnel comes up, all connectivity is lost on the handset - so it technically the service is down. 🥹


That said, once it's VPN tunnel comes up, all connectivity is lost on the handset - so it technically the service is down. 🥹


Back onto the permissions: red flags with requests to:
- display over other apps
- access "past+deleted app usage"
- setup a VPN connection
- make and manage phone calls
All under the pretext to "stay safer" ..
We know better right? But would say, your grandmother?
- display over other apps
- access "past+deleted app usage"
- setup a VPN connection
- make and manage phone calls
All under the pretext to "stay safer" ..
We know better right? But would say, your grandmother?

Notice that we did not see any prompt to install a user certificate - this is really required for the claims made against Facebook to be true (intercept other app's traffic).
Decompiling an earlier version of the APK and it's quite apparent the functionality is there:
Decompiling an earlier version of the APK and it's quite apparent the functionality is there:

Here we can see the file names of the certificates which get added to AndroidCAStore and also how it checks later if they were indeed added.
Fortunately this technique of using intents to install certs no longer works thanks to improvements in Android. 👌
Fortunately this technique of using intents to install certs no longer works thanks to improvements in Android. 👌

Mind you, none of this is new.. Here in Australia, last year the ACCC dished out out a net $20 million dollar fine for this shadiness.
I'm just curious on the technical mechanism the app went about spying on other apps.
accc.gov.au/media-release/…

I'm just curious on the technical mechanism the app went about spying on other apps.
accc.gov.au/media-release/…

I get the impression the Australian fine was more about harvesting usage analytics from other running apps (see: android.permission.PACKAGE_USAGE_STATS)
Did the regulators consider the MITM (wiretapping) which is central to this new antitrust lawsuit in the USA?
Did the regulators consider the MITM (wiretapping) which is central to this new antitrust lawsuit in the USA?

More assumptions related to the $20M fine:
If we dump the schema for the sqlite database "spaceship.db" we see what statistics it was collecting.
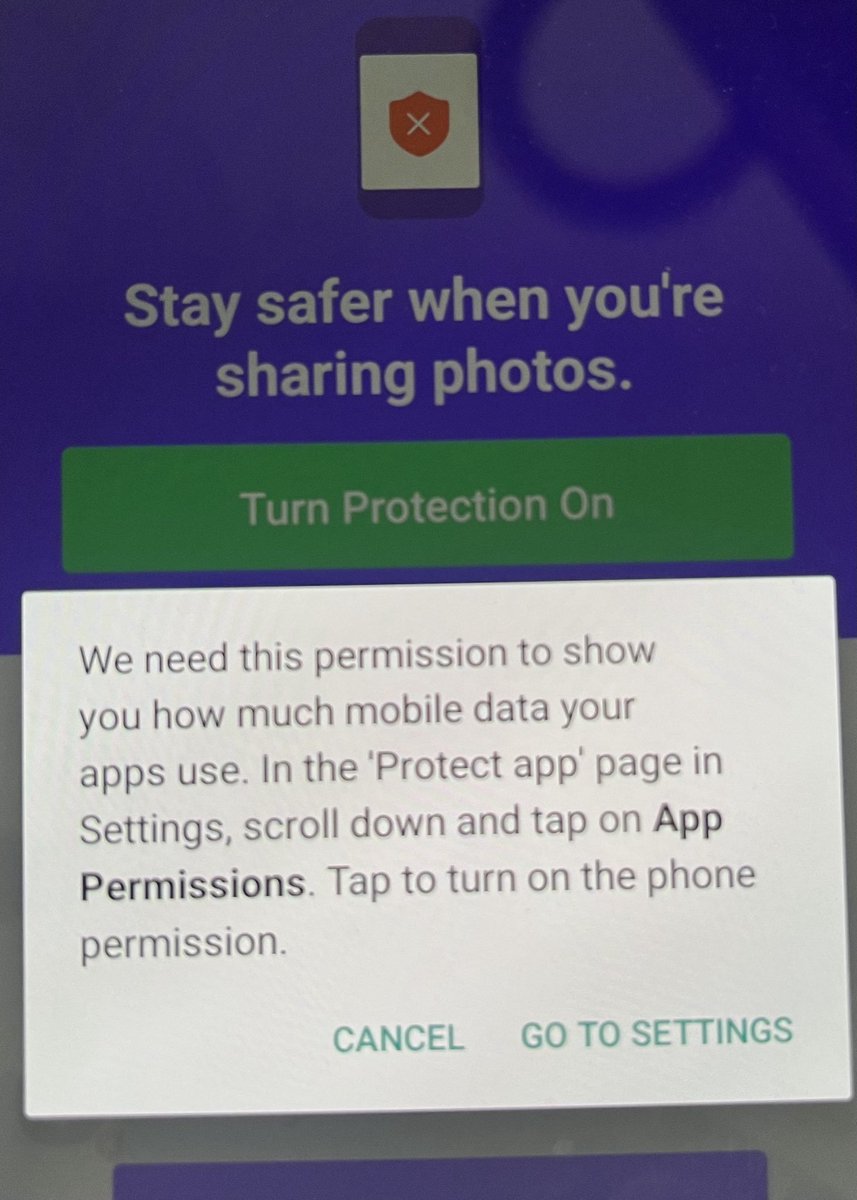
No need for fancy traffic inspection for the app get this data. Remember this popup ?


If we dump the schema for the sqlite database "spaceship.db" we see what statistics it was collecting.
No need for fancy traffic inspection for the app get this data. Remember this popup ?

So, so far we have evidence of:
- Code related to the functionality to install a certificate likely for performing MITM attacks.
- Code / internal database related to collecting other app's usage
What else can we find?
Device info (nothing special):
- Code related to the functionality to install a certificate likely for performing MITM attacks.
- Code / internal database related to collecting other app's usage
What else can we find?
Device info (nothing special):

For what acceptable reason would they wanted to obtain the mobile subscriber IMSI? This is particularly sensitive data.
This actually wouldn't work with the app's manifest file. Perhaps we are seeing older code not cleaned up.
Still, not a great look.
This actually wouldn't work with the app's manifest file. Perhaps we are seeing older code not cleaned up.
Still, not a great look.

A correction on the prior post, the Android documentation on the API doesn't state it but elsewhere says the permission READ_PHONE_STATE would have been enough to obtain the subscriber IMSI.
This Android API change was made in 2019. So IMSIs may have been collected?


This Android API change was made in 2019. So IMSIs may have been collected?


If these are accurate statistics, that's some serious telemetry Facebook were collecting from this app (10 million downloads)
appbrain.com/app/onavo-prot…

appbrain.com/app/onavo-prot…

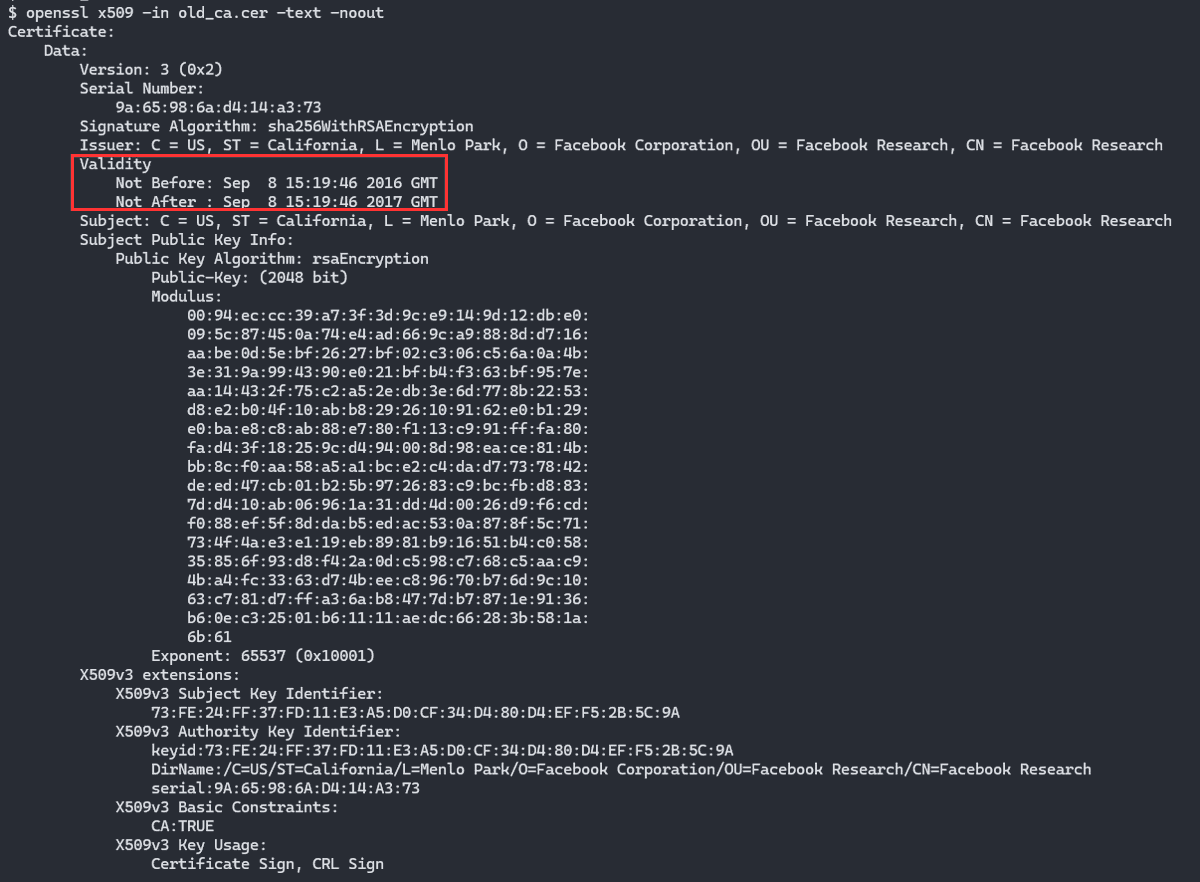
I have been able to find the certificates that were likely used for the MITM attacks.
There are two as first one only was valid for a year.
The second wouldn't remain in for long as some months after it was added in 2017, it (and offending code) then removed.
Wonder why? 🤔


There are two as first one only was valid for a year.
The second wouldn't remain in for long as some months after it was added in 2017, it (and offending code) then removed.
Wonder why? 🤔

One explanation why it was so short lived could be a targeted company figured out what was going on.
Imagine all those millions of requests originating from the same origin IPs and same client proxy certificates.
The MITM CA certs were in the app were out by Oct the 19th 2017.
Imagine all those millions of requests originating from the same origin IPs and same client proxy certificates.
The MITM CA certs were in the app were out by Oct the 19th 2017.

Finishing this thread with a disclaimer.
This is live tweeting: discovering things as we go. We don't have the full picture as of yet, there maybe inaccuracies.
No doubt more details will come to light soon enough though.
The claims are serious.
This is live tweeting: discovering things as we go. We don't have the full picture as of yet, there maybe inaccuracies.
No doubt more details will come to light soon enough though.
The claims are serious.

• • •
Missing some Tweet in this thread? You can try to
force a refresh