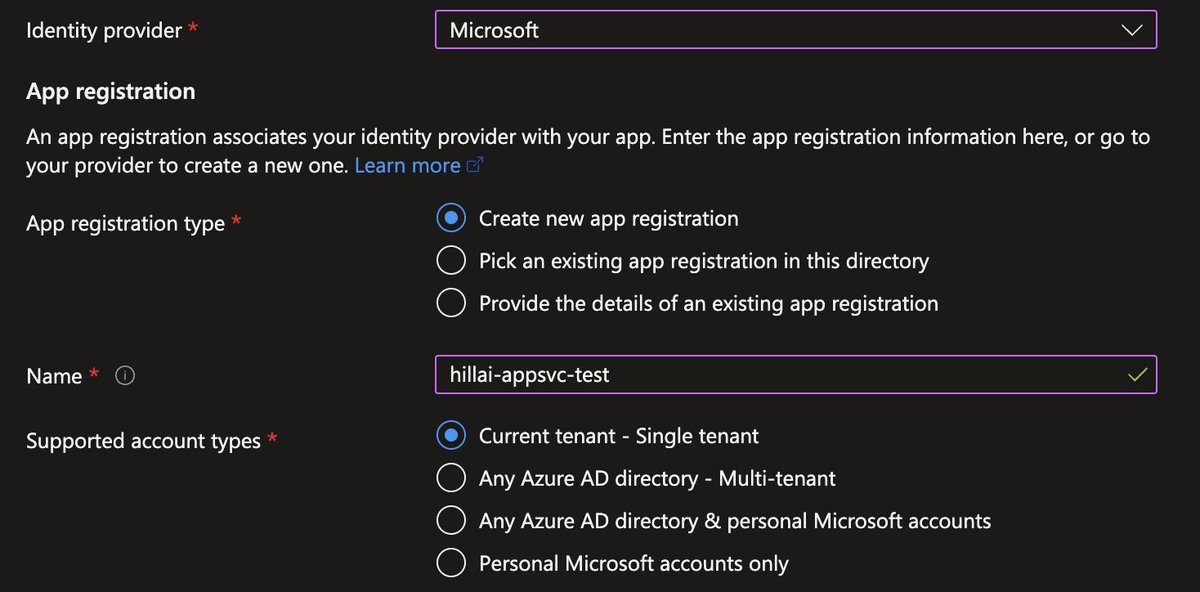
I hacked the @SAP AI platform by changing my UID to 1337.
…Yeah, really.
This led to admin permissions on several SAP systems, but also access to customers’ secrets and private AI files 👀
This is the story of #SAPwned 🧵⬇️
…Yeah, really.
This led to admin permissions on several SAP systems, but also access to customers’ secrets and private AI files 👀
This is the story of #SAPwned 🧵⬇️

SAP AI Core allowed me to run AI training procedures – but with heavy restrictions.
🚫 I couldn’t run as root
🚫 Interesting permissions were removed
🚫 Access to the internal network was blocked by an @IstioMesh firewall
So I wondered – how does this firewall actually work?
🚫 I couldn’t run as root
🚫 Interesting permissions were removed
🚫 Access to the internal network was blocked by an @IstioMesh firewall
So I wondered – how does this firewall actually work?
I started reading the traffic rules set by Istio.
All network traffic was redirected to the proxy.
Except… traffic by UID 1337? 🤨
Although I couldn’t be root, setting my UID to 1337 was still allowed. So that’s what I did.
Crazily enough… it worked! 🤯
All network traffic was redirected to the proxy.
Except… traffic by UID 1337? 🤨
Although I couldn’t be root, setting my UID to 1337 was still allowed. So that’s what I did.
Crazily enough… it worked! 🤯

With unrestricted access to SAP’s internal network, I started searching for interesting internal services.
I quickly found a Grafana Loki server, several EFS file shares, and a Helm server.
They all had one thing in common – they were fully accessible without authentication 🫠
I quickly found a Grafana Loki server, several EFS file shares, and a Helm server.
They all had one thing in common – they were fully accessible without authentication 🫠
Using this access, I gained admin permissions to:
☸️ SAP AI Core’s K8s cluster
🐳 SAP’s container registries
🐸 SAP’s Artifactory server
Allowing attackers to access:
📄 Internal logs
📁 Private customer files
🔑 Customers’ cloud secrets
And more!
☸️ SAP AI Core’s K8s cluster
🐳 SAP’s container registries
🐸 SAP’s Artifactory server
Allowing attackers to access:
📄 Internal logs
📁 Private customer files
🔑 Customers’ cloud secrets
And more!

All issues have been reported to SAP and fixed.
To read the full story with all technical details, check out our @wiz_io 1337 h4x0r blog 👇👇👇
wiz.io/blog/sapwned-s…
To read the full story with all technical details, check out our @wiz_io 1337 h4x0r blog 👇👇👇
wiz.io/blog/sapwned-s…
• • •
Missing some Tweet in this thread? You can try to
force a refresh