How to get URL link on X (Twitter) App


 SAP AI Core allowed me to run AI training procedures – but with heavy restrictions.
SAP AI Core allowed me to run AI training procedures – but with heavy restrictions.
 Microsoft’s AI research team published open-source training data using “SAS tokens” – sharable links granting access to Azure Storage data.
Microsoft’s AI research team published open-source training data using “SAS tokens” – sharable links granting access to Azure Storage data.

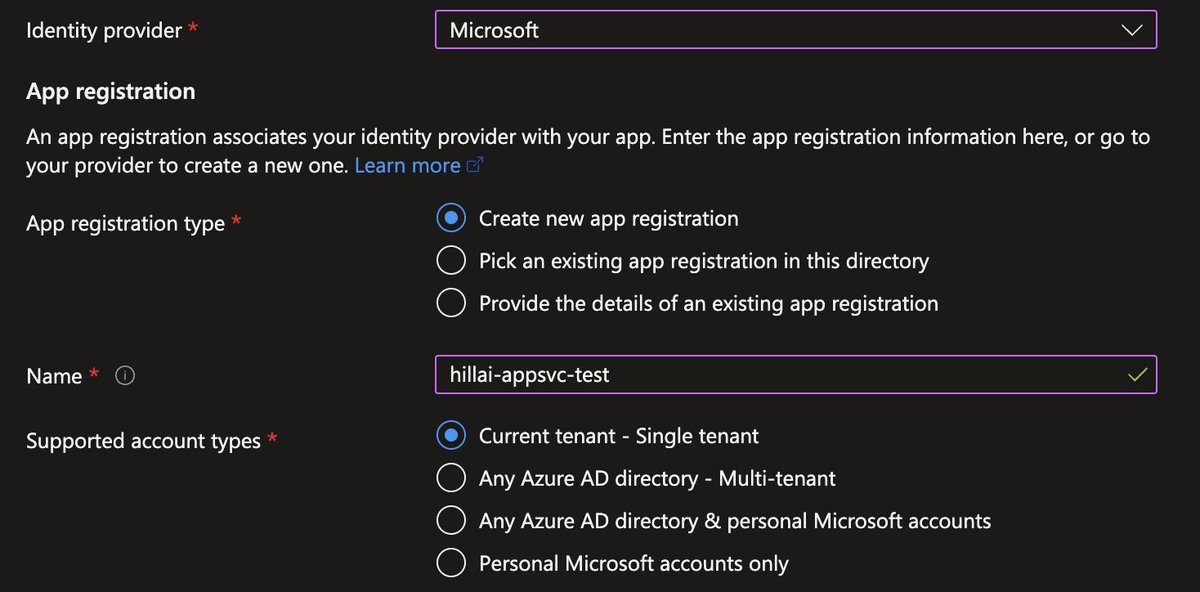
 My research started when our Research Team at @wiz_io first noticed a strange configuration in Azure. A single checkbox is all that separates an app from becoming “multi-tenant” – which by default, allows ALL USERS to log in.
My research started when our Research Team at @wiz_io first noticed a strange configuration in Azure. A single checkbox is all that separates an app from becoming “multi-tenant” – which by default, allows ALL USERS to log in.