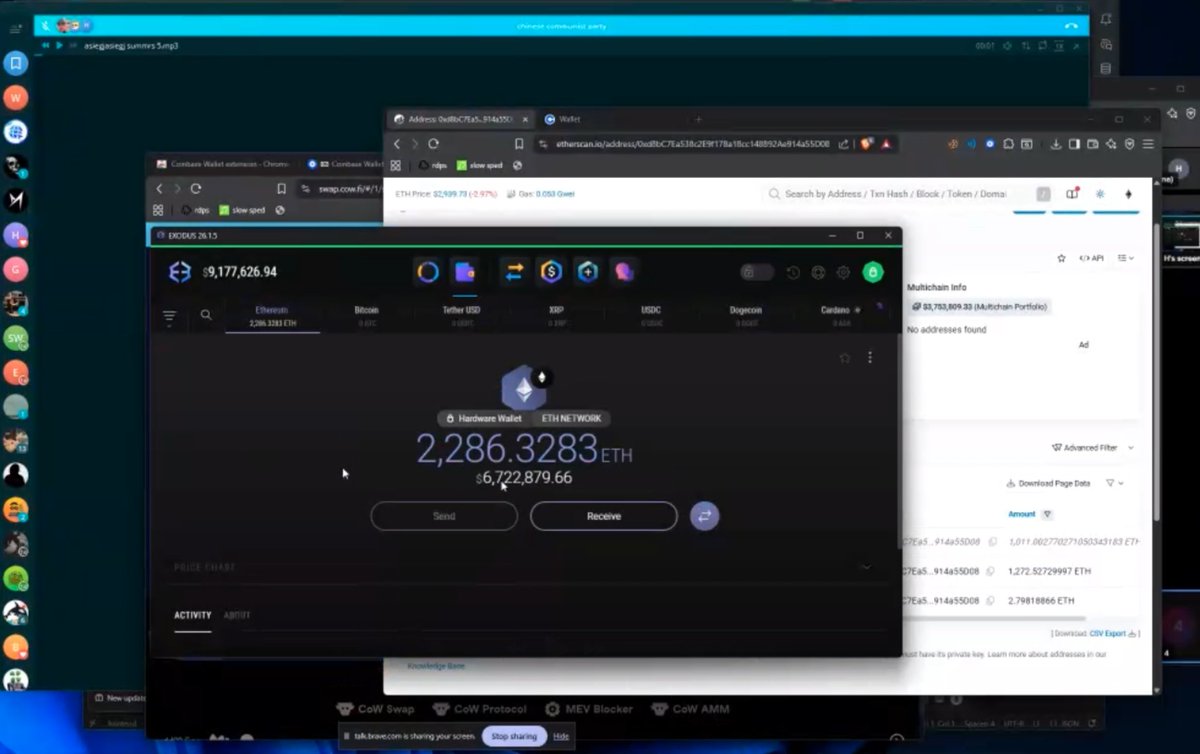
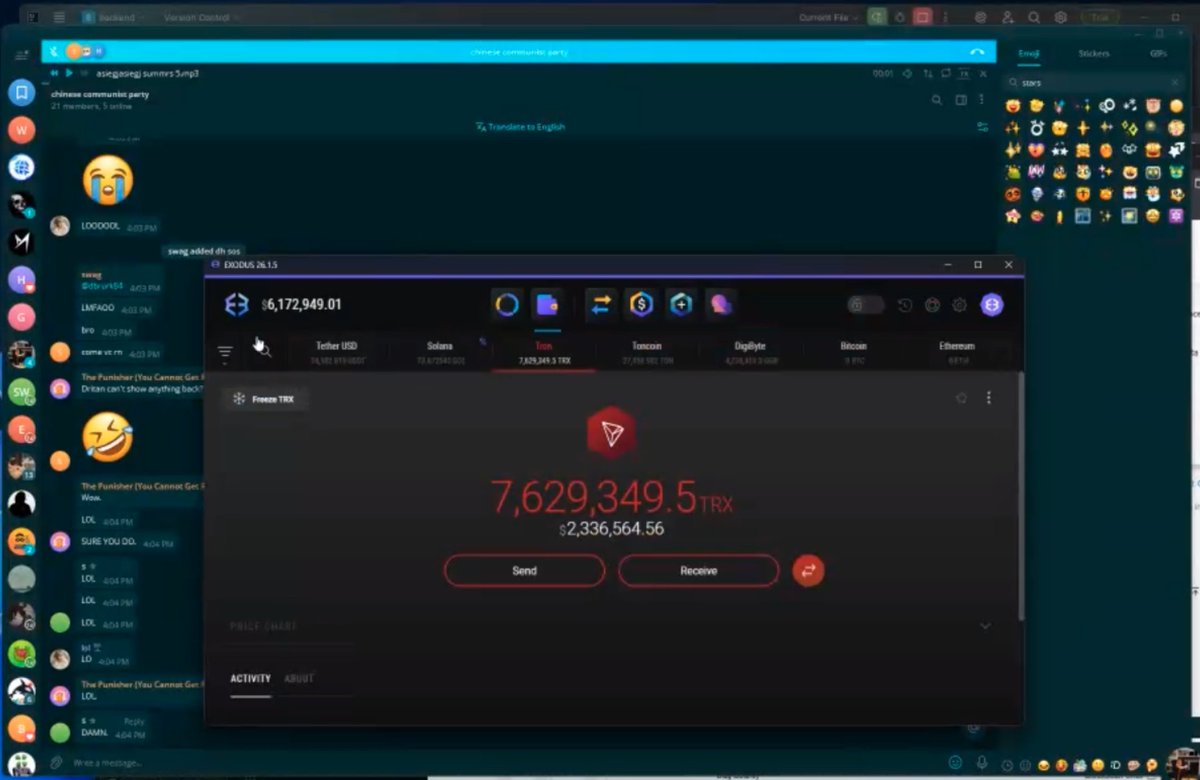
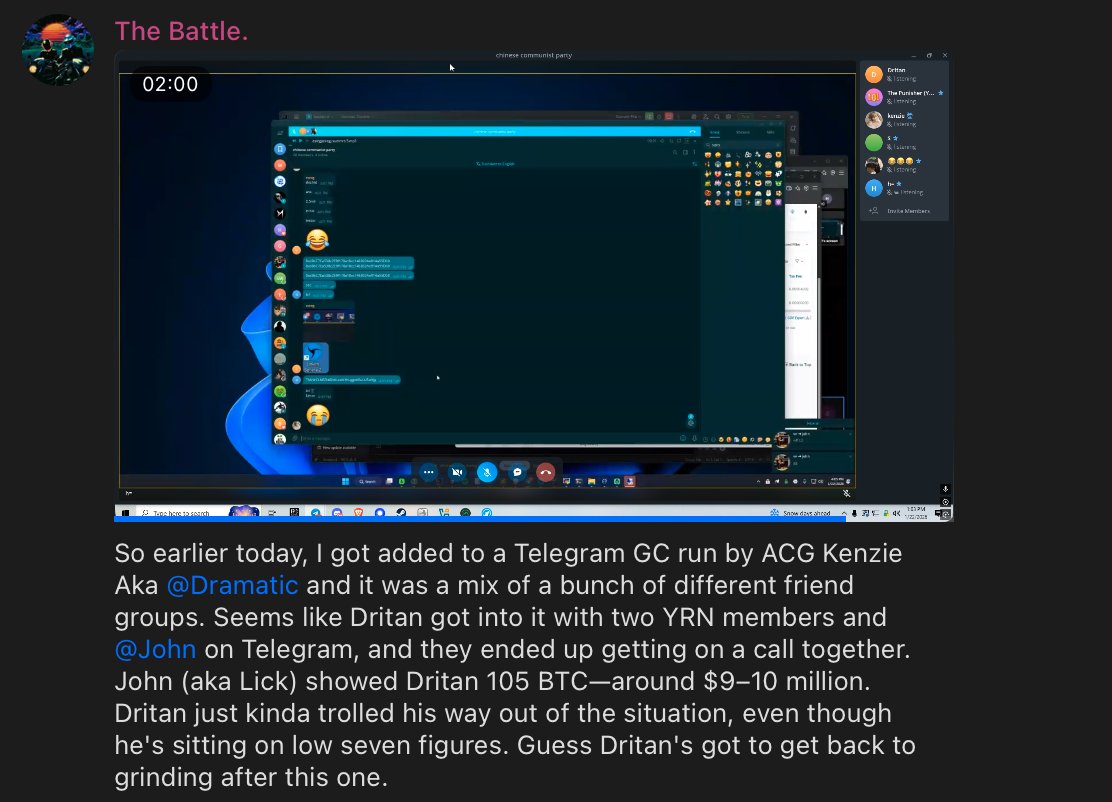
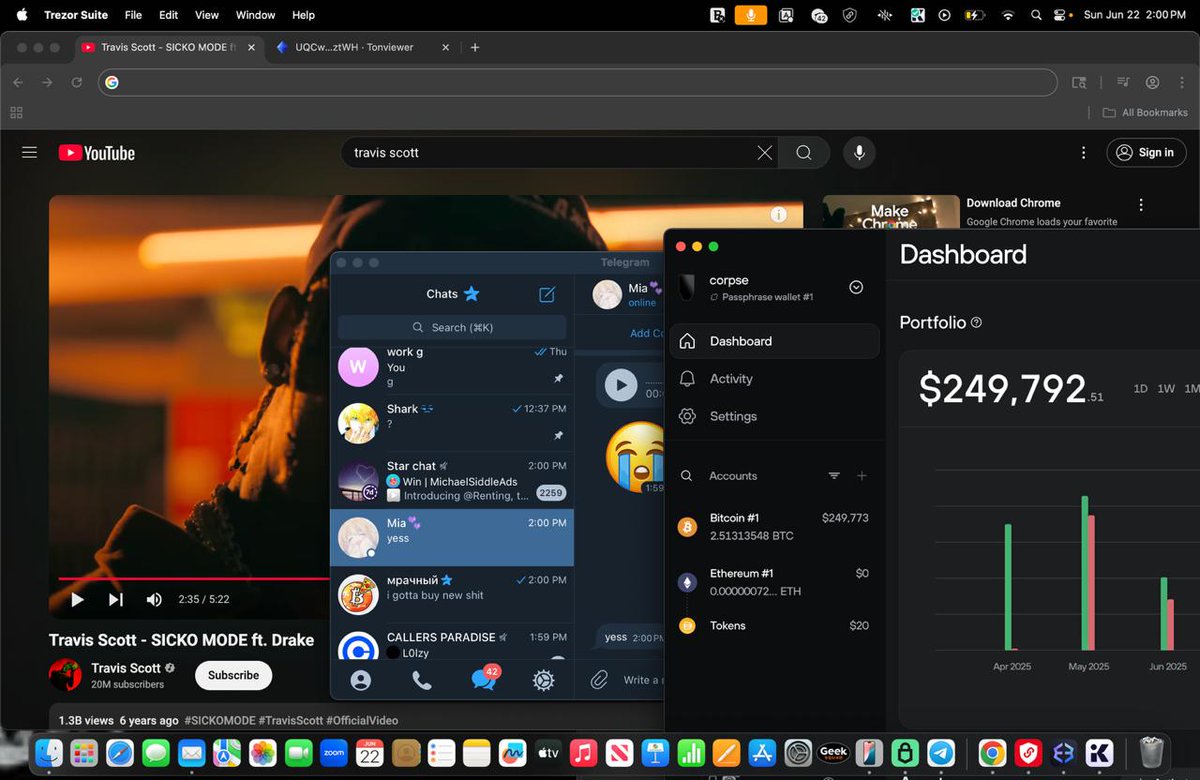
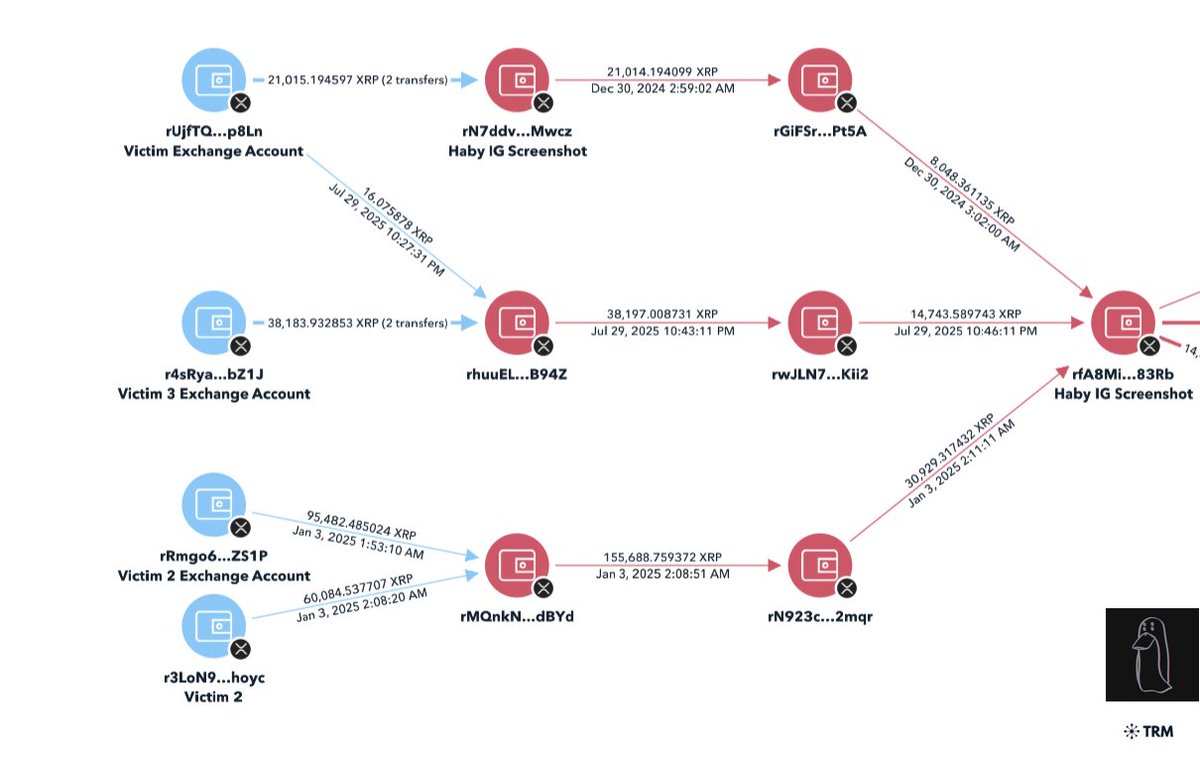
1/ So I began tracing the $230M+ WazirX hack back from the original exploiter address and was able to make some interesting observations.

https://twitter.com/WazirXIndia/status/1813843289940058446
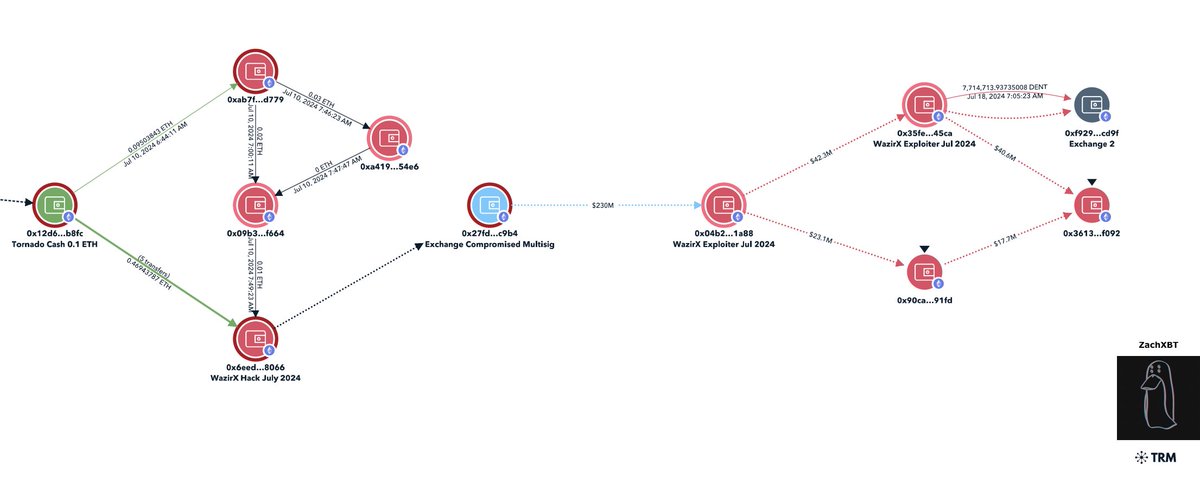
2/ The theft address I will start from is 0x6ee which was doing test transactions on July 10th from 0x09b multisig with SHIB and was funded with 6 X 0.1 ETH from Tornado.
0x6eedf92fb92dd68a270c3205e96dccc527728066
A technical breakdown of the attack by Mudit can be found below


0x6eedf92fb92dd68a270c3205e96dccc527728066
A technical breakdown of the attack by Mudit can be found below
https://twitter.com/mudit__gupta/status/1813881385800913327


3/ With the 6 X 0.1 ETH withdrawals from Tornado Cash on July 10th I was able to demix this and find 6 X 0.1 ETH matching deposits made the day before.
0xc6873ce725229099caf5ac6078f30f48ec6c7e2e
The demix is accurate as 0xc68 was also doing tests with 0x304 multisig on July 9th with SHIB.
0xc6873ce725229099caf5ac6078f30f48ec6c7e2e
The demix is accurate as 0xc68 was also doing tests with 0x304 multisig on July 9th with SHIB.

4/ 0xc68 was funded with 1 ETH from Tornado cash on July 8th at 3:03 PM UTC
0xe3b4cf64e0fc25fafb10d226984b18addc038879ed77f730abbed4737db6a5fc
The matching 1 ETH deposit was made 9 hrs before
0x87c01ca1f56ef3663651b05cd8ebcf133281c5fdd0ef1016f83a16a862c4a235
Both 0xc687 & 0xc891 transferred to each other on July 9th breaking the privacy benefits Tornado provides.
0xe3b4cf64e0fc25fafb10d226984b18addc038879ed77f730abbed4737db6a5fc
The matching 1 ETH deposit was made 9 hrs before
0x87c01ca1f56ef3663651b05cd8ebcf133281c5fdd0ef1016f83a16a862c4a235
Both 0xc687 & 0xc891 transferred to each other on July 9th breaking the privacy benefits Tornado provides.

5/ If I trace back from 0xc891 can see it was funded in two txns with 0.36 ETH and 0.66 ETH on July 8th from an exchange
0xc2fdc27f98cf02c2da2a180fa35824dc365c63795e7a7ce12ba88c1e06edd4f7
0xa62685d8a8b39920e957e0aaf56d527aec6d65bc9323d3d219e11f44e150e224
By performing a timing analysis we can see it was funded from Bitcoin
53795dd1629026c2f92a87d5cd2447736f1afc9cae71262f3af9e62a4ac83b92
ddfd189125ce88c622ec2453b2e9f2dbe5c5c0931f16e3389eac4976c757e5b9
0xc2fdc27f98cf02c2da2a180fa35824dc365c63795e7a7ce12ba88c1e06edd4f7
0xa62685d8a8b39920e957e0aaf56d527aec6d65bc9323d3d219e11f44e150e224
By performing a timing analysis we can see it was funded from Bitcoin
53795dd1629026c2f92a87d5cd2447736f1afc9cae71262f3af9e62a4ac83b92
ddfd189125ce88c622ec2453b2e9f2dbe5c5c0931f16e3389eac4976c757e5b9

6/ This is where my tracing ends as the BTC appears to come from an unknown service making it difficult to trace.
All I can say is the WazirX hack has the potential markings of a Lazarus Group attack (yet again)
Hopefully the WazirX team will be transparent with their findings.
I solved the Arkham bounty where I identified a KYC exchange deposit made by the WazirX hacker
Unfortunately this is probably not super helpful as KYC verified accounts can be easily purchased online for any exchange.
All I can say is the WazirX hack has the potential markings of a Lazarus Group attack (yet again)
Hopefully the WazirX team will be transparent with their findings.
I solved the Arkham bounty where I identified a KYC exchange deposit made by the WazirX hacker
Unfortunately this is probably not super helpful as KYC verified accounts can be easily purchased online for any exchange.
• • •
Missing some Tweet in this thread? You can try to
force a refresh